In this Threat Analysis Report, Cybereason explores the fake installer, ValleyRAT

Explore the most effective trends, techniques, and procedures used by threat actors in Q4 2025, with frontline threat intelligence from our incident response experts. Read More

In this Threat Analysis Report, Cybereason explores the fake installer, ValleyRAT

DFIR expert Jamie Mamroe shares 2026 Incident Response Predictions around Identity and Cloud attacks

Cybereason achieves 100% detection, accuracy, and SOC efficiency in the 2025 MITRE ATT&CK Enterprise Evaluation.

React2Shell vulnerability, tracked as CVE-2025-55182, recently discovered in React’s Server Components, could allow for pre-authentication remote code execution.

In this Threat Analysis Report, Cybereason explores the new ransomware group, "The Gentlemen", and their latest TTPs.
.png)
In this Threat Alert, Cybereason analyzes Tycoon 2FA phishing kit, a sophisticated phishing-as-a-service platform designed to bypass two-factor authentication.
Get the latest research, expert insights, and security industry news...

A new and improved Redeemer 2.0 ransomware version was released on an underground forum and is described by the developers as a “C++ no dependency ransomware with no privacy intrusions” targeting the Windows OS with support for Windows 11 systems...

The Cybereason Defense Platform offers multi-tenancy capabilities to enable SOC teams to divide workflows based on roles...

The AI-driven Cybereason XDR Platform detects and blocks MountLocker ransomware which launched back in September 2020. Since then, the attackers have rebranded the operation as AstroLocker, XingLocker, and now in its current phase, the Quantum Locker...

Threat intelligence is transparently integrated into every aspect of the AI-driven Cybereason XDR Platform to enable Threat Hunting for behavioral TTPs...
.png)
Explore the most effective trends, techniques, and procedures used by threat actors in Q4 2025, with frontline threat intelligence from our incident response experts.
February 5, 2026 / 4 minute read

In this Threat Analysis Report, Cybereason explores the fake installer, ValleyRAT
February 3, 2026 / 16 minute read

DFIR expert Jamie Mamroe shares 2026 Incident Response Predictions around Identity and Cloud attacks
January 9, 2026 / 4 minute read

Cybereason achieves 100% detection, accuracy, and SOC efficiency in the 2025 MITRE ATT&CK Enterprise Evaluation.
December 16, 2025 / 3 minute read

React2Shell vulnerability, tracked as CVE-2025-55182, recently discovered in React’s Server Components, could allow for pre-authentication remote code execution.
December 5, 2025 / 3 minute read

In this Threat Analysis Report, Cybereason explores the new ransomware group, "The Gentlemen", and their latest TTPs.
November 18, 2025 / 8 minute read
.png)
In this Threat Alert, Cybereason analyzes Tycoon 2FA phishing kit, a sophisticated phishing-as-a-service platform designed to bypass two-factor authentication.
November 3, 2025 / 7 minute read
.png)
In this Threat Analysis Report, investigates the flow of a Tangerine Turkey campaign
October 29, 2025 / 5 minute read
.png)
Explore the most effective trends, techniques, and procedures used by threat actors in Q3 2025, with frontline threat intelligence from our incident response experts.
October 23, 2025 / 3 minute read

Email extortion campaign by threat actor group CL0P targets e-business suite users under CVE-2025-61882
October 5, 2025 / 5 minute read

Download the 11 essential cybersecurity controls to minimize attack surface, reduce incident impact, and build cyber resilience (with compliance mappings).
September 23, 2025 / 12 minute read

In this Threat Analysis Report, Cybereason analyzes an investigation into a new malicious Chrome extension campaign
September 9, 2025 / 6 minute read

Two critical vulnerabilities, tracked as CVE-2025-53770 and CVE-2025-53771, have been discovered in on-premise Microsoft SharePoint.
July 22, 2025 / 3 minute read

In this Threat Analysis Report, Cybereason investigates a recently observed BlackSuit ransomware attack and the tools and techniques the threat actors used.
July 11, 2025 / 7 minute read

In this Threat Alert, Cybereason analyzes malicious WordPress websites and the methods and tools used by threat actors to deploy the NetSupport Remote Access Tool (RAT) payload.
July 7, 2025 / 5 minute read
.png)
Gain insight into the latest attack trends, techniques, and procedures we’re facing in the 1st edition of our TTP Briefing, built on frontline threat intel from our global IR investigations and notable detections from our SOC.
June 29, 2025 / 2 minute read

In this Threat Alert, Cybereason explores the rise of Qilin amidst a turbulent realignment of the ransomware landscape.
June 17, 2025 / 12 minute read

Analysis of new Rhadamanthys infostealer campaign in Europe and malware breakdown
May 21, 2025 / 11 minute read

In this Threat Alert, Cybereason identifies a malware infection exhibiting similarities to a previous Genesis Market campaign.
May 21, 2025 / 7 minute read

A critical, unauthenticated remote code execution vulnerability, tracked as CVE-2025-32433, have been discovered in Erlang/OTP's SSH implementation.
April 20, 2025 / 8 minute read

In this Threat Analysis report, Cybereason investigates the evolution of LummaStealer and its hidden secrets
April 11, 2025 / 18 minute read

With data breach-related class actions on rise, lawsuits have become a major risk vector. Cybereason, we offer a full suite of expert services to support defendants in class action litigation.
April 10, 2025 / 3 minute read

In this Threat Analysis report, Cybereason investigates the PlayBoy Locker, the new Ransomware-as-a-Service, and how to defend against it.
March 25, 2025 / 5 minute read

AI is changing the landscape of detection methodology. In order to stay ahead of adversaries, Greg Day breaks down how cybersecurity vendors need leverage AI within their threat detection, prevention & response.
March 17, 2025 / 5 minute read

Introducing the Security Configuration Snapshot, an innovative enhancement to traditional BEC investigations, helping to minimize impact of incidents.
March 11, 2025 / 4 minute read

Three zero-day vulnerabilities, tracked as CVE-2025-22224, CVE-2025-22225, and CVE-2025-22226 have been discovered in nearly all VMware products.
March 5, 2025 / 3 minute read

The Cybereason DFIR team has observed threat actors leveraging email signatures to enhance their phishing lures. Read about their full discovery into the tactic.
February 25, 2025 / 3 minute read

Introducing the Security Configuration Snapshot, an innovative enhancement to traditional BEC investigations, helping to minimize impact of incidents.
February 18, 2025 / 3 minute read

From the perspective of an RSA committee member, Greg Day shares key trends that appeared in the RSA 2025 talk submissions
January 29, 2025 / 4 minute read

In this Threat Analysis report, Cybereason investigates the the Phorpiex botnet that delivers LockBit Black Ransomware (aka LockBit 3.0).
January 28, 2025 / 9 minute read

A critical vulnerability, tracked as CVE-2025-23006, has been discovered in SonicWall SMA 1000 Series.
January 24, 2025 / 2 minute read

Dominic Rinaldi provides his take on the 2024 MITRE ATT&CK® Enterprise Evaluation and its validation of the value of the Cybereason MalOp Technology in the world of modern cyber defense.
January 23, 2025 / 5 minute read

Greg Day provides his take on the 2024 MITRE ATT&CK® Enterprise Evaluation and the importance of "Out-of-the-Box" Detection Coverage for Endpoint Security Solutions.
December 31, 2024 / 5 minute read

A zero-day vulnerability, tracked as CVE-2024-55956, has been discovered in 3 Cleo products and is being exploited by CL0P ransomware group, leading to potential data theft
December 17, 2024 / 3 minute read

In this Threat Analysis report, Cybereason investigates the rising activity of the malware LummaStealer.
December 17, 2024 / 14 minute read

In the 2024 MITRE ATT&CK® Enterprise Evaluation, Cybereason demonstrated why out-of-the-box detection coverage and operational efficiency matter more than ever.
December 16, 2024 / 3 minute read

At pace, gather enough evidence to understand what was occurring, the first goal being to contain the threat and minimize its impact on the business.
December 11, 2024 / 3 minute read

In this Threat Analysis report, Cybereason investigates incidents relating to the Andromeda backdoor and a new cluster of C2 servers.
December 3, 2024 / 8 minute read

what should your own cybersecurity staff do in-house and what should be taken as an outcome based service?
November 8, 2024 / 5 minute read

In this high-stakes game of cat and mouse, the use of artificial intelligence (AI) has emerged as a powerful tool in the fight against cyber threats.
October 24, 2024 / 4 minute read

Scientology spies were trained in all covert operations techniques: surveillance, recruiting agents, infiltrating enemy lines, and blackmail. However, a suspicious librarian and a determined FBI agent brought the largest single spy operation in US government history to an end.
October 23, 2024 /

In this Threat Analysis report, Cybereason investigates the Ransomware-as-a-Service (RaaS) known as Beast and how to defend against it through the Cybereason Defense Platform.
October 18, 2024 / 5 minute read

In this report, Cybereason confirms the ties between Cuckoo Spear and APT10 Intrusion Set by tying multiple incidents together and disclosing new information about this group’s new arsenal and techniques.
October 4, 2024 / 13 minute read

In this blog post, we will take a deep dive into the risks of alert fatigue in the context of cyber attacks and security breaches and introduce how the Cybereason Defense Platform can help mitigate these risks.
October 3, 2024 / 5 minute read

In 1963, the FDA raided the headquarters of a budding new and esoteric religion - The Church of Scientology. In response to this and similar incidents to come, the church's founder - an eccentric science fiction author named L. Ron Hubbard - would go on to lead the single largest known government infiltration operation in United States history.
October 1, 2024 /

Should businesses prioritize cloud-based or on-premise cybersecurity solutions, or are CIOs being influenced by a variety of strategic factors and opting for a hybrid approach?
September 18, 2024 / 7 minute read

On Dec. 5, 2016, two senior Russian Intelligence officers and two civilians were arrested and accused of treason. A few weeks later, when Western journalists were finally able to speak with the men’s lawyers, they learned that the case was based on events that were, oddly enough, already widely known. This made the arrests even more peculiar.
September 17, 2024 /

In this report, Cybereason confirms the ties between Cuckoo Spear and APT10 Intrusion Set by tying multiple incidents together and disclosing new information about this group’s new arsenal and techniques.
September 13, 2024 / 11 minute read

Many organizations today will tell you they have a next-generation Security Operations Centre (SoC). But should we continue to optimize, or do we actually need to evolve and change some of the fundamental principles of the next generation SoC?
September 11, 2024 / 5 minute read

SNAP - better known as food stamps - goes back to the Great Depression. The physical stamps were replaced with EBT cards in the 1990s, but since these cards are without the secure EMV chip technology, enterprising criminals found innovative ways to drain funds meant for low-income families.
September 5, 2024 /

Nicole Kotsianas, an investigator with K2 Intelligence, made it her personal mission to hunt down the Hollywood Con Queen, who cruelly tormented her victims and shattered their dreams. Nicole's efforts bore unexpected fruits, when she discovered that the Con Queen was actually… a man.
August 27, 2024 /

In 2015, two aspiring script writers flew to Indonesia to meet with executives of a large Chinese film corporation. It was a trap: the Hollywood Con Queen not only coned them out of tens of thousands of dollars, she also cruelly ruined their friendship. Two years later, a corporate investigator working for a big shot Hollywood producer, made a discovery that put her on the trail of this master of deceit.
August 14, 2024 /

Some CISOs I know work on a premise that for every one new technology deployed, two should be removed. I wonder if we tried to apply a similar principle to the operational aspects of cybersecurity, how far we could progress.
August 1, 2024 / 5 minute read

Discover how George Lasry, a modern codebreaker, uncovered the secrets of Mary, Queen of Scots, hidden in the French National Library for over 400 years. This episode delves into the painstaking process and the historical impact of decoding these ancient messages, revealing the hidden motives and desperate actions of a doomed queen.
July 31, 2024 /

In this blog, you learn about a highly sophisticated, well-funded, and strategically motivated nation-state cybersecurity threat called cuckoo spear.
July 25, 2024 / 4 minute read

Why did people write malware in the pre-internet days? Back then, there was no way to make money by writing malware. So why write them in the first place? The lack of a financial motivation meant that virus authors had a plethora of other motives - and this diverse mix of motives had, as we shall hear, an interesting effect on the design and style of viruses created at that period.
July 15, 2024 /

In this Threat Analysis report, Cybereason Security Services investigates HardBit Ransomware version 4.0, a new version observed in the wild.
July 10, 2024 / 14 minute read

Section 230 is the pivotal law that has enabled the rise of social media -while sparking heated debates over its implications. In this episode, we're charting the history of Section 230, from early landmark legal battles, to modern controversies, and exploring its complexities and the proposed changes that could redefine online speech and platform responsibility.
June 26, 2024 /

In this Threat Analysis report, Cybereason Security Services investigate the rising activity of the malware GootLoader. GootLoader is a malware loader known to abuse JavaScript to download post-exploitation malware/tools and persist within the infected machine.
June 25, 2024 / 11 minute read

In 2016, Joe Sullivan, former CISO of Facebook, was at the peak of his career. As Uber's new CISO, he and his team had just successfully prevented data from a recent breach from leaking to the internet. But less than a year later, Sullivan was unexpectedly fired from Uber, and three years later, the US Department of Justice announced criminal charges against him. So, what happened at Uber?
June 11, 2024 /

This supply chain attack targets to compromise the integrity of Secure Shell (SSH) - a cryptographic network protocol used to operate systems using remote command execution over an unsecured network.
May 29, 2024 / 7 minute read

In this episode of ML, we're exploring the history of the well-known Nigerian Prince scam, also known as 419 or advanced fee scam, from its roots in a Parisian prison during the French Revolution, to the economic and social reason why this particular scam became so popular with African youth. Also, will AI make such scams more dangerous - or, counter intuitively, go against the interests of scammers?
May 28, 2024 /

Dive into the world of open-source intelligence (OSINT) in this episode, where we uncover how ordinary citizens use publicly available data to unravel some of the most complex global mysteries. From tracking conflicts in real-time to exposing the truth behind high-profile incidents like the downing of Malaysia Airlines flight MH17, discover how OSINT is revolutionizing the field of investigative journalism and transforming how we perceive and verify information.
May 17, 2024 /

In this Threat Analysis Report, Cybereason’s Security Research Team explores the security implications, vulnerabilities, and potential mitigation strategies surrounding Hidden VNC (hVNC) and Hidden RDP (hRDP).
May 6, 2024 / 9 minute read

A few weeks ago we had a listener’s meetup in New York, and as part of that meetup, I gave a talk in which I discussed how Malicious Life came to be - a story that goes back to my days as a ship's captain in the Israeli Navy - and then about how me and Nate craft the stories that you hear every other week. That last part, I hope, might also be beneficial to those of you, our listeners, who find themselves giving talks about technically complex ideas, cyber-related or not. The storytelling ideas and techniques I laid out in the talk are universal, and you’ll find them in blockbuster movies as well as podcast episodes.
May 1, 2024 /

In the waning years of the 20th century, amid growing anxieties about the turn of the millennium, one man, Robert Bemer, observed the unfolding drama from his remote home on King Possum Lake. A revered figure in computing, Bemer had early on flagged a significant, looming issue known as the Y2K bug, which threatened to disrupt global systems as calendars rolled over to the year 2000. This episode delves into Bemer's life during this critical period, exploring his predictions, the ensuing global frenzy to avert disaster, and the disparate views on whether the billions spent in prevention were justified or merely a response to a misunderstood threat.
April 23, 2024 /

In the 1950s and 60s - even leading into the 1990s - the cost of storage was so high, that using a 2-digit field for dates in a software instead of 4-digits could save an organization between $1.2-$2 Million dollars per GB of data. From this perspective, programming computers in the 1950s to record four-digit years would’ve been outright malpractice. But 40 years later, this shortcut became a ticking time bomb which one man, computer scientist Bob Bemer, was trying to diffuse before it was too late.
April 1, 2024 /

Cybereason SDR delivers a comprehensive cybersecurity solution that converges EPP, detection and response (EDR and XDR), SIEM, and Observability into an unified cybersecurity service portal.
March 25, 2024 / 2 minute read

AnyDesk, one of the world’s leading providers of Remote Management and Monitoring (RMM) software, confirmed they had identified a compromise of production systems.
March 22, 2024 / 3 minute read

The 2008 Russo-Georgian War marked a turning point: the first time cyberattacks were used alongside traditional warfare. But what happens when the attackers aren't soldiers, but ordinary citizens? This episode delves into the ethical and legal implications of civilian participation in cyberwarfare, examining real-world examples from Ukraine and beyond.
March 19, 2024 /

In this Threat Analysis Report, Cybereason Security Services examines an incident on a Linux server, which saw malicious shell (bash) executions from a Java process running Apache ActiveMQ.
March 13, 2024 / 10 minute read

Cybereason On-Prem delivers all the state-of-the-art features and capabilities of modern EDR tools while allowing organizations to maintain control over their security infrastructure within their own premises
March 6, 2024 / 3 minute read

In this Threat Analysis Report, Cybereason Security Services dives into the Python Infostealer, delivered via GitHub and GitLab, that ultimately exfiltrates credentials via Telegram Bot API or other well known platforms.
March 5, 2024 / 9 minute read

In 1991, Kevin Mitnick was bouncing back from what was probably the lowest point of his life. He began to rebuild his life: he started working out and lost a hundred pounds, and most importantly - he was finally on the path towards ditching his self-destructive obsession of hacking.
March 1, 2024 /

Many of our customers choose Cybereason On-Prem to simplify their data and critical infrastructure compliance with the flexibility to deploy in on-prem server rooms, private data centers or private cloud environments.
February 20, 2024 / 2 minute read

For Kevin Mitnick - perhaps the greatest social engineer who ever lived - hacking was an obsession: even though it ruined his marriage, landed him in scary correction facilities and almost cost him his sanity in solitary confinement, Mitnick wasn't able to shake the disease that compelled him to keep breaking into more and more communication systems.
February 19, 2024 /

Learn how to detect and prevent a new attack vector being exploited in low-burn, low-cost campaigns using compromised YouTube accounts to spread malware.
February 12, 2024 / 12 minute read

Cybereason issues Threat Alerts to inform customers of emerging impacting threats, including critical vulnerabilities such as the Ivanti Connect Secure VPN Zero-Day exploitation. Cybereason Threat Alerts summarize these threats and provide practical recommendations for protecting against them.
February 6, 2024 / 9 minute read

Right now, hundreds of thousands of people in the southern African country of Namibia are faced with a choice. At the end of next month, their phone service is going to be shut off permanently: to prevent that from happening, they’ll have to give up their data privacy. As a result, nearly two million Namibian citizens are facing a data privacy problem which may haunt them for years to come - and hundreds of thousands more are set to join them, or else they’ll lose their phone service for good. All of which raises the question: was making everybody register their SIM cards a good idea in the first place?
February 5, 2024 /

The execution of DarkGate Loader ultimately leads to execution of post-exploitation tools such as Cobalt Strike and Meterpreter. This Threat Alert provides an overview of an attack involving DarkGate Loader.
January 29, 2024 / 2 minute read

In 2008, The 12 million PCs strong Mariposa Botnet infected almost half of Fortune 100 company - but the three men who ran it were basically script kiddies who didn't even knew how to code.
January 22, 2024 /

I had the huge privilege of being on the program committee for the RSA Conference 2024, reviewing the always popular track: Hackers and Threats, which were a great indicator of the challenges we should expect to see in the coming year.
January 16, 2024 / 3 minute read

Valdimir Levin is often presented as "the first online bank robber," and appeares on many lists of the "Top 10 Greatest Hackers." But a few veteran Russian hackers cliam that Levin's infamous hack had been mangled by the journlists who wrote about it. What's the truth behind the 1994 $10.7 million Citibank hack?…
January 9, 2024 /

About a year ago, six academics from Ruhr University Bochum and the CISPA Helmholtz Center for Information Security set out to survey engineers and developers on the subject of satellite cybersecurity. But most of these engineers were very reluctant to share any details about their satellites and their security aspects. Why were satellite engineers so reticent to talk about cybersecurity? What was so secretive, so wrong with it, that they didn’t feel they could answer even general questions, anonymously? Because let’s be clear: if there’s something wrong with the security of satellites, that’d be a serious problem.
December 27, 2023 /

Cybereason issues Threat Alerts to inform customers of emerging threats, including critical vulnerabilities such as CitrixBleed. Cybereason Threat Alerts summarize these threats and provide practical recommendations for protecting against them.
December 18, 2023 / 3 minute read

When investigators discovered in 1996 that US military networks were being extensively hacked, they didn't realize they were witnessing the birth of what would become Russia's formidable Turla APT espionage group. We uncover the 20-year metamorphosis of this original group of hackers into one of the most sophisticated and dangerous state-sponsored threats that's still active today.
December 11, 2023 /

In August 2021, a port in Houston, Texas, was attacked. Over the following months, a series of attacks occurred in various locations, reminiscent of a serial killer's pattern. Targets included telecommunications companies, government agencies, power plants, and water treatment facilities. How did Volt Typhoon manage to evade authorities and analysts for such an extended period?
November 28, 2023 /

The Cybereason Security Services Team is investigating incidents that involve variants of the DJvu ransomware delivered via loader payloads masquerading as freeware or cracked software.
November 28, 2023 / 2 minute read

In the last six to nine months, I don’t think I’ve been at any cybersecurity meeting where Generative AI was not a key topic. As such, it’s no great surprise that generative AI has a strong influence on my predictions for 2024!
November 27, 2023 / 4 minute read

Cybereason issues Threat Alerts to inform customers of emerging impacting threats, including new ransomware actors such as the emergent group INC Ransom. Cybereason Threat Alerts summarize these threats and provide practical recommendations for protecting against them.
November 20, 2023 / 3 minute read

By the time Forbidden Stories published its “Pegasus Project” in 2021, NSO was already knee deep in what was probably the worst PR disaster ever suffered by a cybersecurity company - and then, in November 2021, came the fateful blow: the US Dept. of Commerce added NSO to its “Entity List.” Is NSO to blame for its troubles? Could the company have acted differently to prevent its downfall?
November 13, 2023 /

NSO Group, creator of the infamous Pegasus spyware, is widely regarded as a vile, immoral company: a sort of 21st century soldier of fortune, a mercenary in the service of corrupt and evil regimes. Yet among its many clients are many liberal democracies, including the US, Germany, the Netherlands and Spain, to name but a few. So, is NSO really as evil as many think it is?
October 30, 2023 /

It's not surprising that in the last couple of months the requests of “are you EU Network Information Security Directive (NISD) v2 compliant?” are starting to come in. What would seem like a simple GRC yes no question is in fact complex.
October 25, 2023 / 3 minute read

To support cyber defenders to achieve tangible business benefits and deliver effective security outcomes, Cybereason has developed a comprehensive Extended Detection & Response (XDR) Buyer’s Guide.
October 24, 2023 / 1 minute read

Exploring the hard work that goes into keeping pace with the ever evolving and increasingly complex threats as well as the challenge of ensuring endpoints are secure against them.
October 23, 2023 / 3 minute read

The FBI explicitly advises companies against paying ransomware attackers - but itself payed 4.4 million dollars worth of Bitcoin after the Colonial Pipeline attack. So, should you listen to what the experts say, or follow what they occasionally do? It’s complicated, but we can model this problem.
October 17, 2023 /

In this Threat Analysis report, Cybereason investigates and explores various techniques for abusing the Windows Shortcut file format.
October 6, 2023 / 3 minute read

In the vast landscape of STEM, women constitute a mere 28% of the workforce. Yet, when we zoom into the realm of cybersecurity, the number dwindles even further to a startling 20 to 24 percent. What are the underlying reasons behind this disparity?
October 2, 2023 /

In 1981, during the G7 Summit in Quebec, French president Francois Mitterand handed President Raegan a top secret collection of documents, called Farewell Dossier. The information found in the dossier allowed the US to devise a cunning plan - the very first supply chain attack, if you will - to bring a firey end to one of largest industrial espionage campaigns in history.
September 20, 2023 /

Fresh off the press: the results of the 2023 MITRE Engenuity ATT&CK® Evaluations for Enterprise have been published and Cybereason set a new benchmark with perfect scores in nearly every aspect of the evaluations.
September 20, 2023 / 3 minute read

How do we secure the Private Infrastructure Protection (PIP) space? By providing virtualized containers, allowing customers to re-use their own hardware and making it easier to add in new capabilities as the cyber security world evolves.
September 13, 2023 / 4 minute read

Much of the cybersecurity software in use today utilizes AI, especially things like spam filters and network traffic monitors. But will all those tools be enough to stop the proliferation of malware that will come from generative AI-driven cyber attacks? The potential of AI to disrupt cyberspace is far greater than any solutions we’ve come up with thus far, which is why some researchers are looking beyond the traditional answers, towards more aggressive measures.
September 4, 2023 /

Every so often, the entire landscape of cybersecurity shifts, all at once: The latest seismic shift in the field occurred just last year. So in this episode of Malicious Life we’re going to take a look into the future of cybersecurity: at how generative AI like ChatGPT will change cyberspace, through the eyes of five research teams breaking ground in the field. We’ll start off simple, and gradually build to increasingly more complex, more futuristic examples of how this technology might well turn against us, forcing us to solve problems we’d never considered before. – check it out...
August 22, 2023 /

LockBit 2.0 ransomware attackers are constantly evolving and making detection, investigation, and prevention more complex by disabling EDR and other security products and deleting the evidence to stifle forensics attempts...
August 21, 2023 / 4 minute read
This integration is a significant development in the Cybereason & Sysdig partnership. By combining our strengths, we aim to create a solution that will help customers better protect their complete cloud risk.
August 9, 2023 / 2 minute read

On the face of it, there's an obvious economic incentive for both vendors and security researchers to collaborate on disclosing vulnerabilities safely and privately. Yet bug bounty programs have gained prominence only in the past decade or so, and even today only a relatively small portion of vendors have such programs at place. Why is that? – check it out...
August 8, 2023 /

The constant battle between those who wish to encrypt data and those who wish to break these ciphers has made modern encryption schemes extremely powerful. Subsequently, the tools and methods to break them became equivalently sophisticated. Yet, could it be that someone in the 15th century created a cipher that even today’s most brilliant codebreakers and most sophisticated and advanced tools - cannot break?...
July 25, 2023 /

In 2019, Roman Seleznev, a 34 years-old Russian national, was sentenced to 27 years in prison: A sentence that’d make any criminal quiver. Seleznev's deeds had a horrendous effect on the 2.9 million individuals whose credit cards he stole and sold to cyber criminals for identity theft and financial crimes. On one hand, it’s hard to imagine any nonviolent computer crime worth 27 years in prison. But then what is an appropriate sentence for such a man as Seleznev? – check it out...
July 10, 2023 /
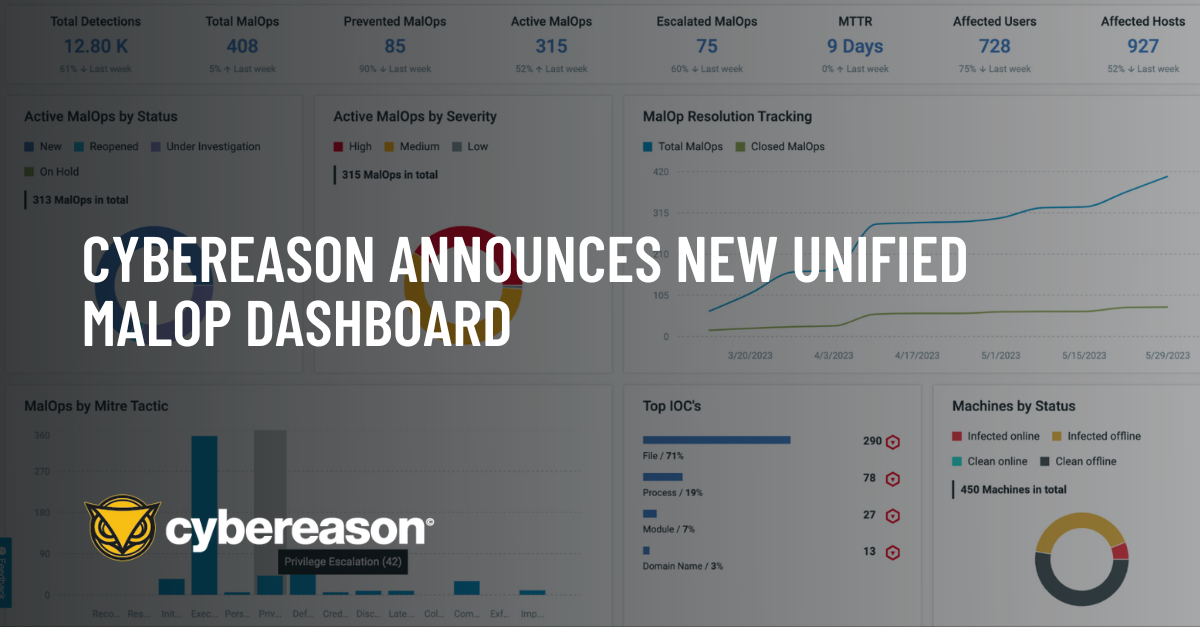
To help SOC teams stay ahead of the curve, Cybereason introduced a unified dashboard designed to provide additional insights into emerging threats, operational metrics and provide insights to continuously improve SOC processes and procedures.
July 7, 2023 / 2 minute read

"We made a mistake and Sony paid a terrible price.” A terrible price indeed: an arrogant and ill-advised decision to include a rootkit in its music CDs cost Sony BMG a lot of money - and painted it as a self-centered, self-serving company that cares more about its bottom line than its customers. Why did Sony BMG make such a poor decision? – check it out...
June 27, 2023 /

Can XDR bring value to your security team? In this post, we delve into three crucial questions that can help determine if XDR can be a shining knight on your cyber battlefield.
June 21, 2023 / 2 minute read

"What makes ad fraud so successful, and so prevalent, and why can’t we stop it? The answer isn’t technical at all. It’s not hard to understand. But it’s a harsh reality that many people are simply not willing to face. – check it out...
June 9, 2023 /

Right now, a man named Aleksandr Zhukov is sitting in jail for one of the most financially ruinous schemes ever invented for the internet. Zhukov is guilty. He was caught and convicted under a mountain of evidence against him. Except the deeper you look into it, the deeper the well goes. In this episode, we’ll learn how Aleksandr Zhukov defrauded some of the biggest American corporations for millions of dollars. And we’ll ask the question that hardly anyone else is willing to acknowledge: Was this clever, successful, guilty cybercriminal merely a fall guy for everybody else playing his twisted game?. – check it out...
May 30, 2023 /

The numbers can’t be any clearer: a DDoS attack costs less than a hundred dollars, while the price tag for mitigating it might reach tens if not hundreds of thousands of dollars. A single well crafted phishing email can easily circumvent cyber defenses which cost millions of dollars to set up. How can we change the extreame cost asymmetry between attackers and defenders in cyberspace?. – check it out...
May 15, 2023 /

Cybereason XDR eliminates data fragmentation by ingesting all relevant security data from all security controls into a single data platform.
May 3, 2023 / 2 minute read

We’ve all experienced the creepiness of modern data trafficking, but that kind of daily annoyance is the surface of a much bigger issue: Big Tech companies such as Amazon & Microsoft are lobbying policymakers to veto laws that harm their business, and often hide their lobbying behind industry coalitions or organizations with names that are vague and seemingly harmless. Will current and future privacy laws actually protect your information, or will they protect the companies collecting your information? – check it out...
May 1, 2023 /

Cybereason has a long history of leveraging AI and Machine Learning models to classify malicious operations (MalOp™) and malware with a high level of accuracy.
May 1, 2023 / 2 minute read

Cybereason announces Unified Threat Hunting and Investigation, a significant development in its approach to storing long-term hunting data.
April 26, 2023 / 2 minute read

Don’t miss the immersive Cybereason digital experience and live demos at booth N-5457 in the North Expo Hall.
April 18, 2023 / 2 minute read

Disruptions to the world’s internet cables happen more often than you think: Whether it be ship anchors or animals or saboteurs, cut a few wires in the right places and at nearly the speed of light you can disrupt or shut off the internet for broad populations of people at a time. It is an immense power that runs through these lines -- a power that can be sabotaged or, in the right hands, weaponized. – check it out...
April 17, 2023 /

In the midst of 35,000 exhilarated spectators eagerly chanting the time-honored countdown to kick off the 2018 Pyeongchang Winter Olympics, a sinister malware crept through the games' network, threatening to disrupt the highly-anticipated event. The obvious question in everyone’s minds was - who was responsible for the attack? Who was vile enough to launch such a potentially destructive attack against an event which, more than anything, symbolizes peace and global cooperation? – check it out...
April 3, 2023 /

Cybereason detects and prevents the ongoing 3CXDesktopApp supply chain attack.
March 31, 2023 / 2 minute read

On May 23rd, 1989, Karl Koch - a 23 years old West German hacker who worked for the KGB - took a drive, from which he would never return: Nine days later his charred remains were found by the police in a remote forest. Was Koch assasinated by the US or the Sovient Union, or is there another, more 'mystical' explanation for his death? – check it out...
March 20, 2023 /

Investing in technology can give companies a false sense of security when it comes to ransomware. Here are 5 steps to more effective ransomware response.
March 15, 2023 / 3 minute read

Ransomware directly impacts the investment decisions organizations make to modernize their Security Operations Centers, according to a Cybereason study.
March 14, 2023 / 1 minute read

Where other vendors fail to support on-premises deployments, Cybereason is globally minded, and we address the need for secure Private Infrastructure.
March 9, 2023 / 2 minute read

Four decades ago, three quarters would’ve gone a lot further than they do today. With that kind of loose change you could’ve picked up some milk from the grocery store, or over half a gallon of gas, or a bus ticket. But that doesn’t explain why, on one fateful day in 1986, a systems administrator at the Lawrence Berkeley National Laboratory in California made such an issue over 75 missing cents. – check it out...
March 8, 2023 /

We are at an inflection point in U.S. National Cybersecurity strategy. The strategy’s high-level objectives are laudable, but largely unachievable.
March 8, 2023 / 2 minute read

Cybereason’s Variant Payload Prevention employs a new proprietary algorithm for fuzzy similarity called Binary Similarity Analysis (BSA).
March 3, 2023 / 6 minute read

In this B-Side episode, our Senior Producer Nate Nelson interviewed Dr. Bilyana Lilly - CISSP, a leader in cybersecurity and information warfare with over fifteen years of managerial, technical, and research experience, and author of "Russian Information Warfare" - about the Russian use of instant messaging and social media platforms such as Telegram and Twitter in their war efforts. Dr. Lilly discusses who they are targeting and the real-world impact their propaganda has on various populations. – check it out...
February 28, 2023 /

Cybereason is excited and honored to be positioned as a “Leader” in the recently released 2022 Gartner Magic Quadrant for Endpoint Protection Platforms.
February 28, 2023 / 2 minute read

The increasing stress of leading and working in a Security Operations Center (SOC) will lead to a wave of resignations in the next two years.
February 23, 2023 / 2 minute read

In the early 1970's, US intelligence pointed at the possibility that the Russians have laid an underwater communication cable between two important naval bases in the Far East. The dangerous mission of installing a listening device on that cable was given to the navy most secretive and unusual submarine. – check it out...
February 20, 2023 /

In December 2022, the Cybereason Incident Response (IR) team investigated an incident which involved new deployment methods of GootLoader.
February 14, 2023 / 5 minute read

We are already seeing ransomware that scans for cloud-based collaboration points. And while you may think the risks are the same, that's not the case.
February 14, 2023 / 4 minute read

What happens when an NFT marketplace goes under, and disappears? You would imagine that the users’ NFTs are perfectly safe: after all, the blockchain itself is still there, right? But that’s not how things work in the real world.
February 13, 2023 /

New Cybereason features and capabilities include improvements to prevention, data collection, investigation, and management capabilities.
February 6, 2023 / 4 minute read

Financial markets make good targets for criminals - after all, that's where the big money is. Surprisingly, many of these criminals are not your run-of-the-mill black hat hacker, but brokers registered with the SEC: genuine finance industry professionals – check it out...
February 6, 2023 /

If SIM swap stories ever make the news, almost uniformly, they focus on people who lost a lot of money. But SIM swaps also take a psychological toll...
January 31, 2023 /

Nate Nelson speaks with Rich Murray, who leads the FBI’s North Texas Cyber unit, about how the Federal Bureau of Investigations dealt with dealt with another attack by REvil
January 24, 2023 /

Spamhaus's decision to add Cyberbunker to its list of Spam sources led the Stophaus coalition to initiate a DDoS attack later dubbed “The attack that almost broke the Internet.”
January 20, 2023 /

If you’re a security practitioner wondering where to start your XDR journey, here’s a look at the fundamental building blocks of a successful XDR strategy.
January 19, 2023 / 3 minute read

Threat Research: Sliver C2 gets more and more traction from Threat Actors, often seen as an alternative from Cobalt Striker.
January 19, 2023 / 20 minute read

This year's submissions to the RSA Conference have broadened the diversity of ideas and introduced new concepts.
January 17, 2023 / 2 minute read

Sven Kamphuis and Herman Johan Xennt are quite dissimilar... and in 1996, their unlikely partnership coalesced around a mutual deep hatred towards authority...
January 11, 2023 /

Recently, IcedID, also known as BokBot, has been used more as a dropper for other malware families and as a tool for initial access brokers.
January 10, 2023 / 9 minute read

Cybereason has developed a comprehensive guide to MITRE ATT&CK to help your organization drive more consistent and effective defenses against attacks.
January 9, 2023 / 1 minute read

2011 was a pivotal year for Netflix: the now hugely successful company was then in the midst of a formidable transformation, changing from a mail-based DVD rental service to the modern streaming service that it is today
January 3, 2023 /

Dr. Fred Cohen not only introduced the name ‘computer virus’, a term invented by his mentor, Leonard Adelman, but was also the first to analyze computer viruses in a rigorous mathematical way...
December 19, 2022 /

Royal ransomware has become one of the most prolific ransomware groups in 2022. Read our threat analysis to learn how Royal ransomware operations work, how they evade anti-ransomware defenses, and how you can outsmart them.
December 14, 2022 / 7 minute read

With Cybereason Managed Detection and Response (MDR), the Olist security team shortened their triage and remediation times to less than 30 minutes.
December 13, 2022 / 1 minute read

How does it feel to live for years with a virtual target mark on your back?… Malicious Life discusses the story of Thamar Gindin.
December 13, 2022 /

Paying a ransom is the worst possible strategy for addressing ransomware attacks.
December 12, 2022 / 2 minute read

Nobody likes cheaters, especially in video games. That's why EA and other publishers are implementing kernel-mode anti-cheat software in their games. Yet some people warn that installing such kernel-level systems is extremely dangerous. In this episode of Malicious Life, we examine why.
December 8, 2022 /

Current approaches to fighting ransomware in healthcare don't seem to be working. We've got a prescription for what healthcare CISOs can do differently.
December 7, 2022 / 2 minute read

Learn how threat actors are embedding malicious binaries and scripts in legitimate Microsoft Windows Installation (.msi) files to take over machines they're targeting with elevated privileges. Find out how to detect this sophisticated attack technique.
December 5, 2022 / 16 minute read

The FBI and CISA issued a joint advisory on Cuba ransomware actors. The advisory is the latest in the government’s #StopRansomware campaign.
December 2, 2022 / 2 minute read

Cybereason VP and EMEA Field CISO Greg Day anticipates 2023 will bring more cloud credential attacks, increased use of deepfakes in blended attacks, attacks between smart devices, and more.
December 1, 2022 / 3 minute read

When it was founded in 2011, Norse Corp. had everything going for it, but the startup blew up in smoke less than six years later. Malicious Life explores what went so horribly wrong.
November 29, 2022 /

An Australian white hat hacker demonstrated how easily hackers can take over farming equipment and the risks this creates for global food supplies.
November 28, 2022 /

Find out how the Russian Business Network, a once legitimate ISP, became the largest player in the Russian cybercrime world and a key component of Putin's attacks on democracy and misinformation campaigns in this episode of the Malicious Life podcast.
November 25, 2022 /

Find out what cybersecurity professionals can learn from MMA wrestlers and Chess Grand Champions about peak performance in this episode of Malicious Life, featuring Chris Cochran and Ron Eddings, the co-founders of Hacker Valley Media.
November 24, 2022 /
This threat alert describes an aggressive new attack campaign operated by the Black Basta ransomware group. The fast-moving campaign is targeting U.S. companies, and in many cases, is causing serious damage to their IT infrastructures.
November 23, 2022 / 11 minute read

Information security executives explain how media companies can be hacked and why we, as consumers, should care in this Malicious Life BSide podcast.
November 22, 2022 /

One day in 2008, Michael Daugherty got a call from cybersecurity company TiVera, saying private medical data of some 9000 LabMD patients had been discovered online. When Michael refused to pay for TiVersa's hefty "consultation fee", a ten-year legal battle began that led to the demise of LabMD, but also cost the FTC dearly.
November 18, 2022 /

Traditional Monday through Friday staffing models are out of step with cyber threats and leave companies vulnerable on weekends and holidays, according to the results of a recent survey from Cybereason.
November 16, 2022 / 5 minute read

Cybereason NGAV combines 9 independent yet complimentary prevention layers ensuring that your business achieves its goals and bad actors don’t.
November 14, 2022 / 15 minute read

Cybereason has released a series of enhancements in the Machine Timeline feature (formerly known as Process Timeline) to improve investigation workflows.
November 1, 2022 / 2 minute read

This Threat Analysis Report explores widely used DLL Side-Loading attack techniques, outlines how threat actors leverage these techniques, describes how to reproduce an attack, and reports on how defenders can detect and prevent these attacks...
October 26, 2022 / 13 minute read

The Tidal Platform makes it efficient to research adversary techniques using MITRE ATT&CK, and now Cybereason has joined the Tidal Product Registry to deliver a visual view of our out-of-the-box detection capabilities...
October 19, 2022 / 2 minute read

Financial markets make good targets for criminals - after all, that's where the big money is. Surprisingly, many of these criminals are not your run-of-the-mill black hat hacker, but brokers registered with the SEC: genuine finance industry professionals – check it out...
October 18, 2022 /

The potential impact from cyberattacks can be very far reaching–not just for the compromised Telcos, but also for their vast customer base whose data is also at risk...
October 18, 2022 / 3 minute read

IOBs describe the subtle chains of malicious activity derived from correlating enriched telemetry from across all network assets - but unlike backward-looking IOCs, IOBs offer a proactive means to leverage real-time telemetry to identify attack activity earlier, and they offer more longevity value than IOCs...
October 12, 2022 / 4 minute read

NGAV can work to prevent the early stages of a ransomware attack that precede the delivery of the ransomware payload, and offers further protection by also assuring that payload is not detonated on the target machine in the case where the first stages of the attack were not detected...
October 11, 2022 / 4 minute read

Rachel Tobac is a hacker and CEO of SocialProof Security, where she helps people and companies keep their data safe by training and pentesting them on social engineering threats like Vishing and the many psychological tricks attackers employ to hack people – check it out...
October 11, 2022 /

CISOs and CSOs are already on the hook and are the first ones to take the fall for breaches regardless of whether they fought for additional investments in people, processes, and technology. But what about accountability for the C-Suite and BOD?
October 6, 2022 / 1 minute read

Here are Cybereason's 10 Ways to Make Your Security Operations More Efficient and Effective...
October 6, 2022 / 4 minute read

Container Escape is considered the 'Holy Grail' of the container attack world - it allows an attacker to escape from a container to the underlying host, and by doing so the attacker can move laterally to other containers from the host or perform actions on the host itself...
October 5, 2022 / 9 minute read

The key to early detection of advanced operations such as the SolarWinds attacks is in leveraging Indicators of Behavior (IOBs) to level-up to a more efficient and effective Operation-Centric approach to detecting the whole of an attack as opposed to responding to individual, uncorrelated alerts...
October 5, 2022 / 4 minute read

In this edition of the Blue Team Chronicles, we assess the capabilities of eslogger, a new built-in macOS tool, and show how defenders can use this tool to better understand malicious activities on macOS and build new detection approaches...
October 4, 2022 / 8 minute read

Some stock traders are willing to go to great lengths to get information before anyone else, even hacking into trading technologies to gain an unfair advantage and make a fortune along the way–check it out...
October 4, 2022 /

The Cybereason GSOC Managed Detection and Response (MDR) Team is investigating incidents that involve exploitation of the critical Microsoft Exchange vulnerabilities (CVE-2022–41040 and CVE-2022–41082) dubbed ProxyNotShell after finding them being exploited in the wild...
October 3, 2022 / 5 minute read

Cybereason has released a new white paper, Eliminate Alert Fatigue: A Guide to More Efficient and Effective SOC Teams...
October 3, 2022 / 1 minute read

The Malicious Life Podcast Team is excited to announce that we won the This Week in Tech Technology Category honor at the 17th Annual People's Choice Podcast Awards...
October 3, 2022 / 1 minute read

In this webinar, Cybereason CSO Sam Curry is joined by Cody Queen to dig into the data from the Ransomware: The True Cost to Business 2022 report and how to quantify the true cost to business of ransomware attacks and what cybersecurity leaders can do to mitigate against them...
September 30, 2022 / 1 minute read

Authentication is one of the main elements of a cloud application, as it provides the ability to control access to your application. Need to pick an authentication solution and don't know where to start? This write-up will guide you in choosing an authentication solution that will suit your needs...
September 29, 2022 / 5 minute read

Join us on October 13th to hear from-the-field tips on how to create world-class efficiencies, including ways to find efficiencies within your tech stack, tips on how to recruit and manage a successful team, practical tips any team can take to reduce event burden, how the Cybereason Defense Platform can create a 10x boost in efficiencies and more...
September 29, 2022 / 1 minute read

As their name implies, LulzSec was known for trolling their victims:, and while their childish behavior might have fooled some people into thinking that LulzSec was harmless, the story you’re about to hear will show they were anything but – check it out...
September 28, 2022 /

This paper details the Operation-Centric approach and how it can foster earlier detections based on Indicators of Behavior that empowers security operations to dynamically adapt and predictively respond more swiftly than attackers can modify their tactics to circumvent defenses...
September 27, 2022 / 1 minute read

Attacks on organizations that originate from third-party partners and service providers are expected to rise in the coming years as attackers look for weak links in software supply chains in an effort to “attack one to attack all..."
September 27, 2022 / 4 minute read

The release of Cybereason Private Infrastructure Protection v. 21.2 includes security hardening improvements, new features and improvements to existing features...
September 26, 2022 / 3 minute read

Traditional antivirus tools from legacy vendors spot the easy stuff but struggle to prevent novel threats from causing damage. That is why Cybereason is announcing its latest prevention technologies to detect and block all threats from commodity malware to the never before seen...
September 22, 2022 / 1 minute read

AI-driven XDR solution unifies telemetry analysis to optimize efficacy, improves operational efficiency at scale, and eliminates detection blind spots by generating deeply contextual correlations from endpoints, identity management, workspaces, application suites, the cloud and more...
September 21, 2022 / 3 minute read

In this webinar we will hear from Cybereason CTO and co-founder Yonatan Striem-Amit about how threats are changing; Tim Amey, Field CTO about how Cybereason prevention layers stop malware in its tracks; and Cody Queen, Product Marketing Manager share the latest prevention tools developed by Cybereason to stop the most novel attack techniques...
September 21, 2022 / 1 minute read

The report showcases best practices that Council members have used to align business executives around a common understanding of cyber risk and also explores a potentially controversial solution to the business-cybersecurity alignment gap: cybersecurity accountability regulation...
September 20, 2022 / 2 minute read

You cannot defend against RansomOps in traditional ways because it’s not a traditional threat, and a focus on detecting the ransomware executable alone is risky because that is the tail-end of a longer attack sequence, where the adversary already has unfettered access to your network...
September 20, 2022 / 4 minute read

The worst of the COVID-19 pandemic may be behind us, but its impact on the global cybersecurity workforce will force many enterprises to consider Managed Detection and Response (MDR) services...
September 20, 2022 / 2 minute read

The US government says that Kim Schmitz, better known as Kim DotCom, is the leader of a file sharing crime ring. He sees himself as an internet freedom fighter: a fugitive on the run from vindictive overly-powerful governments. Can King Kimble escape the wrath of the USA? Check it out...
September 19, 2022 /

When ransomware threatens to shut down your business, the most critical measures of success is the ability to detect malicious activity in real time...
September 15, 2022 / 4 minute read

Cybereason GSOC team analysts have analyzed a specific technique that abuses Notepad++ plugins to evade security mechanisms, achieve persistence and deploy backdoors on targeted machines...
September 14, 2022 / 4 minute read