
Deceptive Signatures: Advanced Techniques in BEC Attacks
The Cybereason DFIR team has observed threat actors leveraging email signatures to enhance their phishing lures. Read about their full discovery into the tactic.

Cybereason Security Research Team
Cybereason issues Threat Alerts to inform customers of emerging threats, including a recently observed DJvu variant delivered via a loader masquerading as freeware. Cybereason Threat Alerts summarize these threats and provide practical recommendations for protecting against them.
The Cybereason Security Services Team is investigating incidents that involve variants of the DJvu ransomware delivered via loader payloads masquerading as freeware or cracked software.
While this attack pattern is not new, incidents involving a DJvu variant that appends the .xaro extension to affected files and demanding ransom for a decryptor have been observed infecting systems alongside a host of various commodity loaders and infostealers. This Threat Alert will provide an overview of an attack involving this variant of DJvu, which we will call Xaro for ease of reference.
The adversary’s goal is data exfiltration, information stealing, and the encryption of files in order to garner a ransom from the victim.
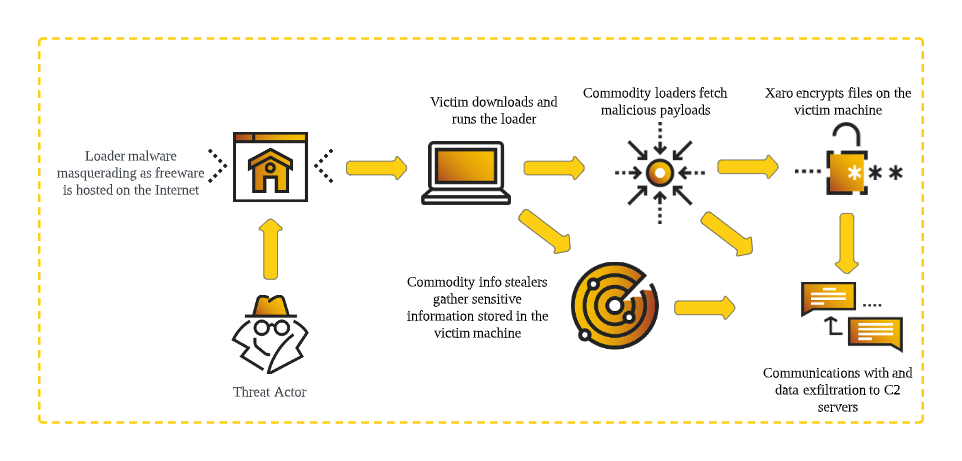 Attack flow diagram of the Xaro infection- threat actors host malicious payloads as freeware online. When the user downloads and runs the payload, a variety of malware (including the DJvu variant Xaro) is executed.
Attack flow diagram of the Xaro infection- threat actors host malicious payloads as freeware online. When the user downloads and runs the payload, a variety of malware (including the DJvu variant Xaro) is executed.
The Cybereason Defense Platform can detect and prevent post-exploitation observed in attacks using DJvu variants. Cybereason recommends the following actions:
This blog post is the summary of a full 16-page Threat Alert, which can be downloaded here.
Ralph Villanueva, Senior Security Analyst, Cybereason Global SOC
Ralph Villanueva is a Security Analyst with the Cybereason Global SOC team. He works hunting and combating emerging threats in the cybersecurity space. His interests include malware reverse engineering, digital forensics, and studying APTs. He earned his Masters in Network Security from Florida International University.
The Security Security Research Team creates and manages the core security content of Cybereason, including the detection and preventions logic of its products. The Team is leading the innovation of security defense features to detect and disrupt advanced cyberattacks. The Team is led by top-tier security researchers working with major enterprises, governments, and the military.

The Cybereason DFIR team has observed threat actors leveraging email signatures to enhance their phishing lures. Read about their full discovery into the tactic.

In December 2022, the Cybereason Incident Response (IR) team investigated an incident which involved new deployment methods of GootLoader.

The Cybereason DFIR team has observed threat actors leveraging email signatures to enhance their phishing lures. Read about their full discovery into the tactic.

In December 2022, the Cybereason Incident Response (IR) team investigated an incident which involved new deployment methods of GootLoader.
Get the latest research, expert insights, and security industry news.
Subscribe