Cybereason issues Threat Alerts to inform customers of emerging impacting threats, including recently observed DarkGate Loader. Cybereason Threat Alerts summarize these threats and provide practical recommendations for protecting against them.
WHAT'S HAPPENING?
Cybereason Security Services is investigating incidents that involve DarkGate Loader, a modular loader delivered via phishing email and responsible for deploying post-exploitation payloads.
Threat Actors deploy DarkGate Loader as an AutoIt script, which contains an encrypted payload. The AutoIt script decrypts and injects the payload into different processes. The execution of DarkGate Loader ultimately leads to execution of post-exploitation tools such as Cobalt Strike and Meterpreter. This Threat Alert provides an overview of an attack involving DarkGate Loader.
Impact
The purpose of DarkGate Loader is to deploy post-exploitation tools while evading detection.
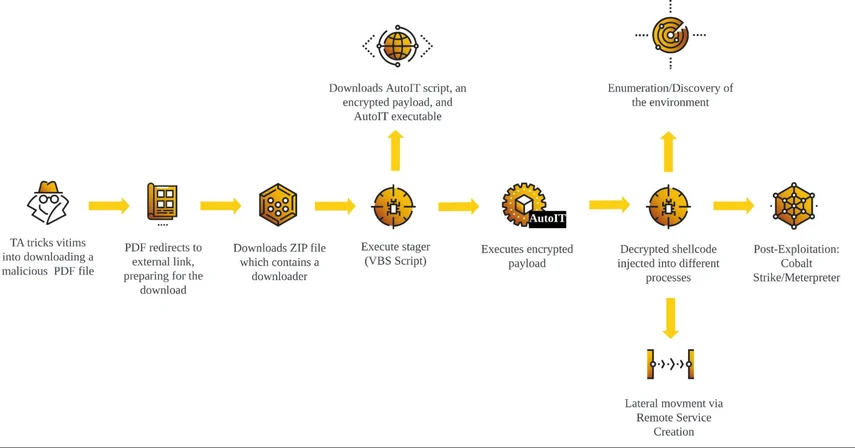 DarkGate Loader Attack Flow Diagram
DarkGate Loader Attack Flow Diagram
KEY OBSERVATIONS
- Infection chain via PDF: Threat Actor tricks victims into downloading malicious PDF files, which leads to execution of malicious VBS script.
- DarkGate loader delivered in AutoIt script format: DarkGate Loader is within the AutoIt script in the form of an encrypted payload. AutoIt decrypts the encrypted payload during the runtime and injects itself to remote processes.
- Fast paced delivery of post-exploitation: Observed DarkGate Loader incident delivered post-exploitation tools such as Meterpreter and Cobalt Strike within 6 hours after DarkGate Loader execution. The deployment of post-exploitation tools also includes Lateral Movement to critical infrastructure, leading to greater impact across organizations.
- Post-exploitation activities detected by Cybereason: Cybereason Defense Platform generates detections upon exploitation.
CYBEREASON RECOMMENDATIONS
The Cybereason Defense Platform can detect and prevent DarkGate infections and post-exploitation behaviors. Cybereason recommends the following actions:
- Enable Application Control to block the execution of malicious files.
- Enable Variant Payload Prevention with prevent mode on Cybereason Behavioral execution prevention.
- To hunt proactively, use the Investigation screen in the Cybereason Defense Platform and the queries in the Hunting Queries section to search for assets that have potentially been exploited. Based on the search results, take further remediation actions, such as isolating the infected machines and deleting the payload file.
- Add the aforementioned IoCs to the custom reputation with “Block & Prevent”
DOWNLOAD THE FULL THREAT ALERT
This blog post is the summary of a full 16-page Threat Alert, which can be downloaded here.
About The Researchers

Derrick Masters, Principal Security Analyst, Cybereason Global SOC
Derrick Masters is a Senior Security Analyst with the Cybereason Global SOC team. He is involved with threat hunting and purple teaming. Derrick's professional certifications include GCFA, GCDA, GPEN, GPYC, and GSEC.
 Hema Loganathan, Security Analyst, Cybereason Global SOC
Hema Loganathan, Security Analyst, Cybereason Global SOC
Hema Loganathan is a Security Analyst with the Cybereason Global SOC team. She is involved in Malop Investigation, Malware Analysis, Reverse Engineering and Threat Hunting. Hema has a Master of science degree in Information Systems.
 Ralph Villanueva, Senior Security Analyst, Cybereason Global SOC
Ralph Villanueva, Senior Security Analyst, Cybereason Global SOC
Ralph Villanueva is a Security Analyst with the Cybereason Global SOC team. He works hunting and combating emerging threats in the cybersecurity space. His interests include malware reverse engineering, digital forensics, and studying APTs. He earned his Masters in Network Security from Florida International University.
 Kotaro Ogino, Principal Security Analyst, Cybereason Global SOC
Kotaro Ogino, Principal Security Analyst, Cybereason Global SOC
Kotaro Ogino is a Principal Security Analyst with the Cybereason Global SOC team. He is involved in threat hunting and Extended Detection and Response (XDR). Kotaro has a bachelor of science degree in information and computer science.
 Uma Shukla, Senior Security Analyst, Cybereason Global SOC
Uma Shukla, Senior Security Analyst, Cybereason Global SOC
Uma is a Senior Security Analyst with the Cybereason Global SOC team. He is involved in threat hunting, making use cases on emerging threats and exploits. He has experience working as Incident Response Consultant, Application and Vulnerability management and holds multiple certifications like ECIH, CYSA+, BTL1, BTJA, QRadar Security Professional.






 Hema Loganathan, Security Analyst, Cybereason Global SOC
Hema Loganathan, Security Analyst, Cybereason Global SOC Ralph Villanueva, Senior Security Analyst, Cybereason Global SOC
Ralph Villanueva, Senior Security Analyst, Cybereason Global SOC Kotaro Ogino, Principal Security Analyst, Cybereason Global SOC
Kotaro Ogino, Principal Security Analyst, Cybereason Global SOC Uma Shukla, Senior Security Analyst, Cybereason Global SOC
Uma Shukla, Senior Security Analyst, Cybereason Global SOC
