ENDPOINT DETECTION
AND RESPONSE (EDR)
With Cybereason EDR, defenders can stop chasing alerts and instead end malicious operations before they take hold.
Why Cybereason Endpoint Detection and Response (EDR)?
Unmatched, Unlimited Visibility
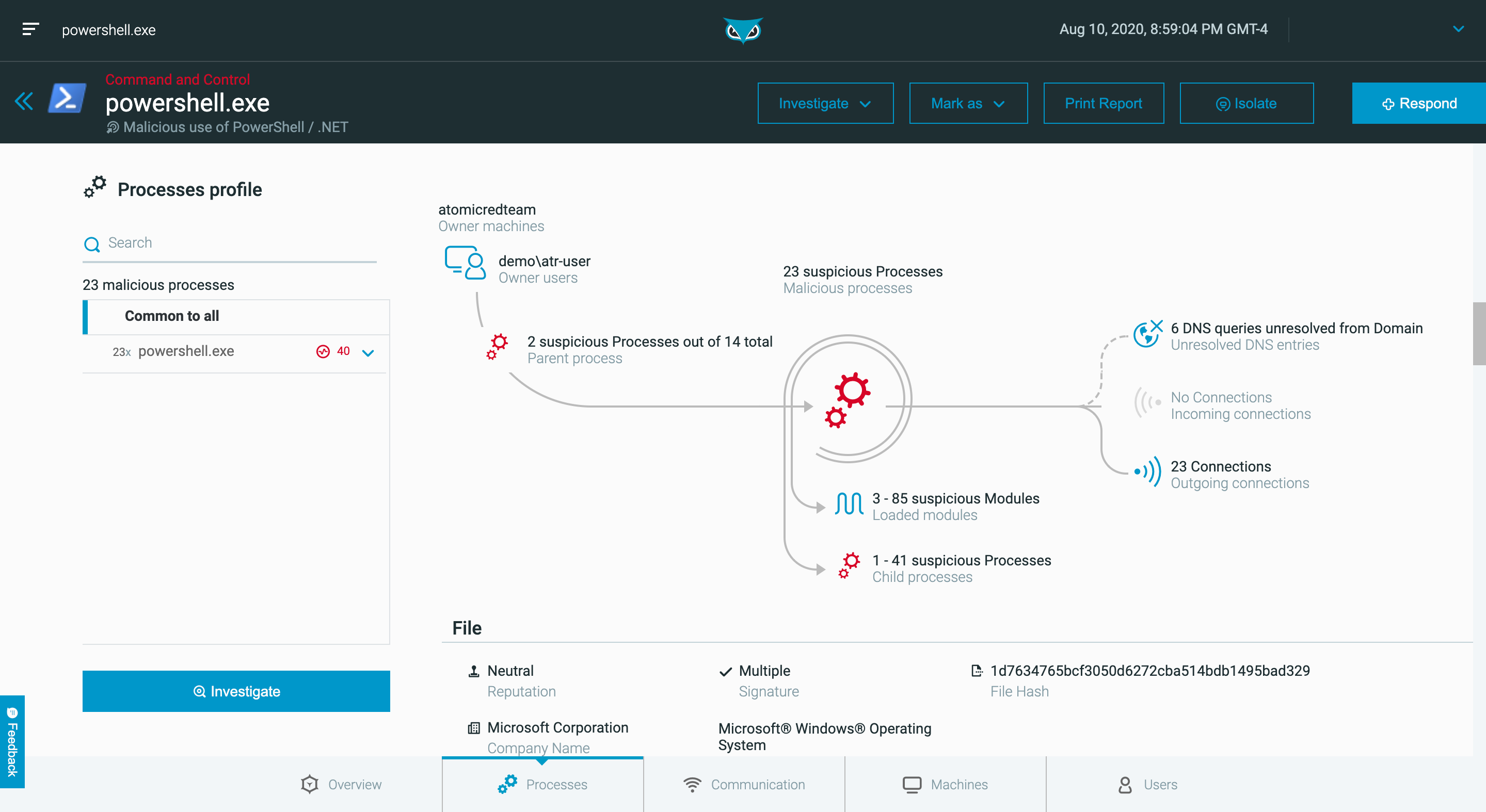
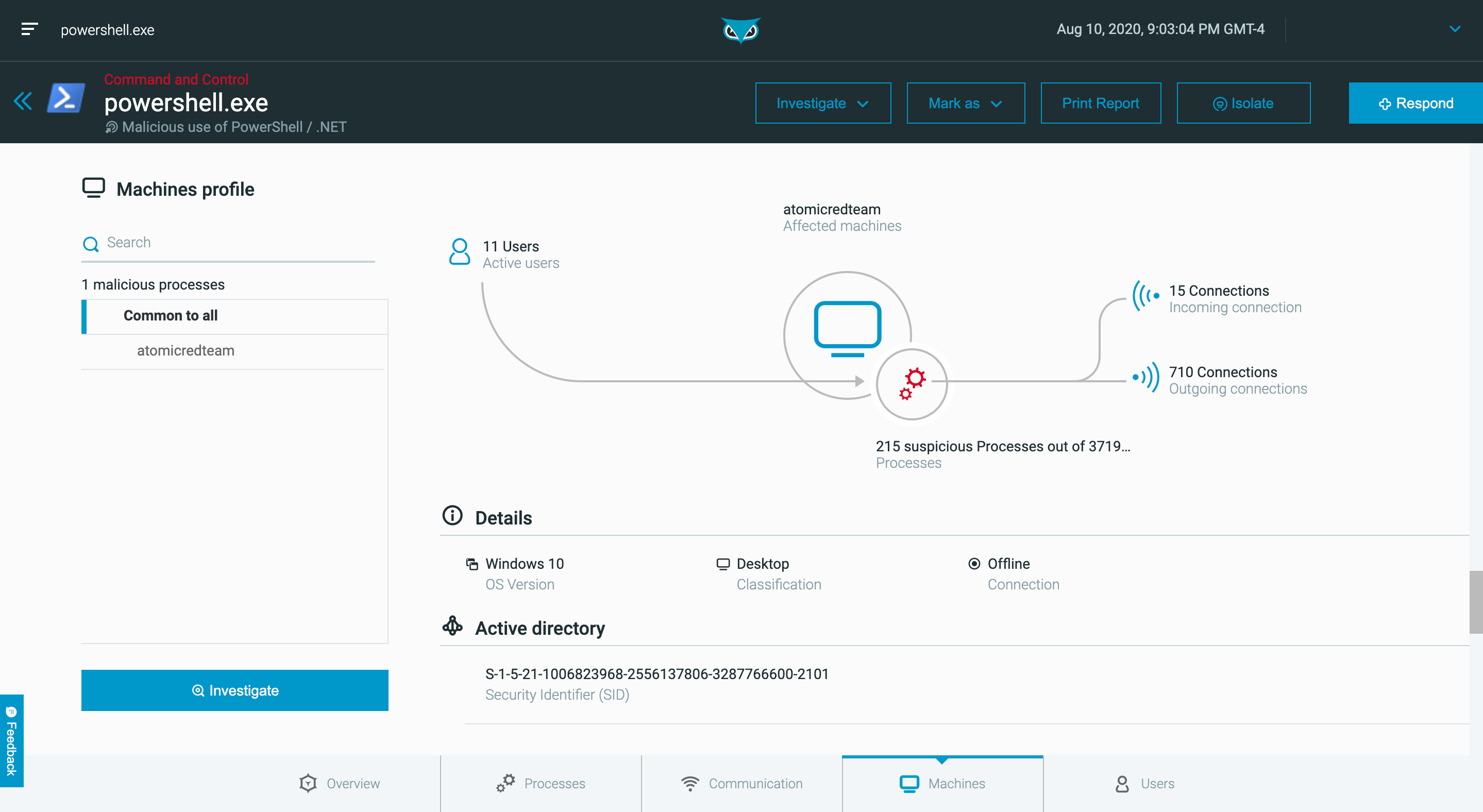
Get the complete story of a MalOp™ (malicious operation) from start to finish with contextualized and correlated insights that detect and end sophisticated attacks.
Security Team Force Multiplier
Maximize your valuable Security Operations Center resources with a 1:200,000 analyst-to-endpoint ratio that allows Level 1 and 2 analysts to perform at Level 3 proficiency.
Remediate in Seconds
Instantly remediate by killing processes, quarantining files, removing persistence mechanisms, preventing file execution and isolating machines, all with a single click.
EDR Tools and Features
Threat Intelligence
Many different threat feeds often do not agree with each other on which IOCs are malicious or unknown. This conflicting information makes it difficult to quickly determine the maliciousness of a threat and take action.
Cybereason Threat Intelligence aggregates multiple threat feeds and cross-examines those feeds against machine learning analysis to rank the various threat feeds based on their historical accuracy for particular types of threats from various adversary groups. This enables Cybereason to determine the correct threat intelligence source to respond quickly and with precision, which simplifies the investigation and response process.
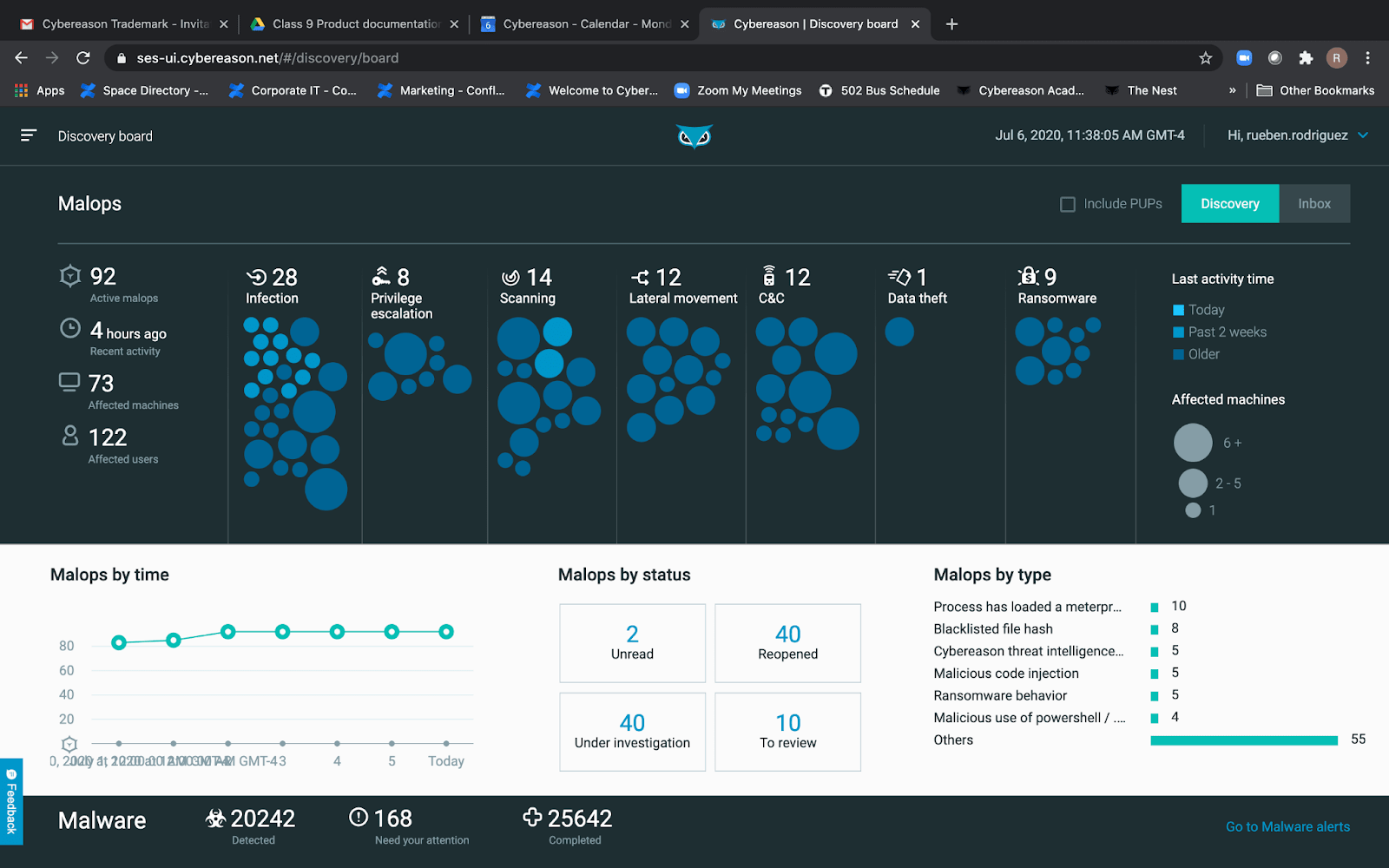
Instant Remediation
Analysts of all skill levels can quickly dig into the details of an attack without crafting complicated queries, then easily pivot directly from investigating to remediating affected devices by executing a full suite of remediation actions from machine isolation and process killing to removing persistence mechanisms - all from within an intuitive point and click interface.
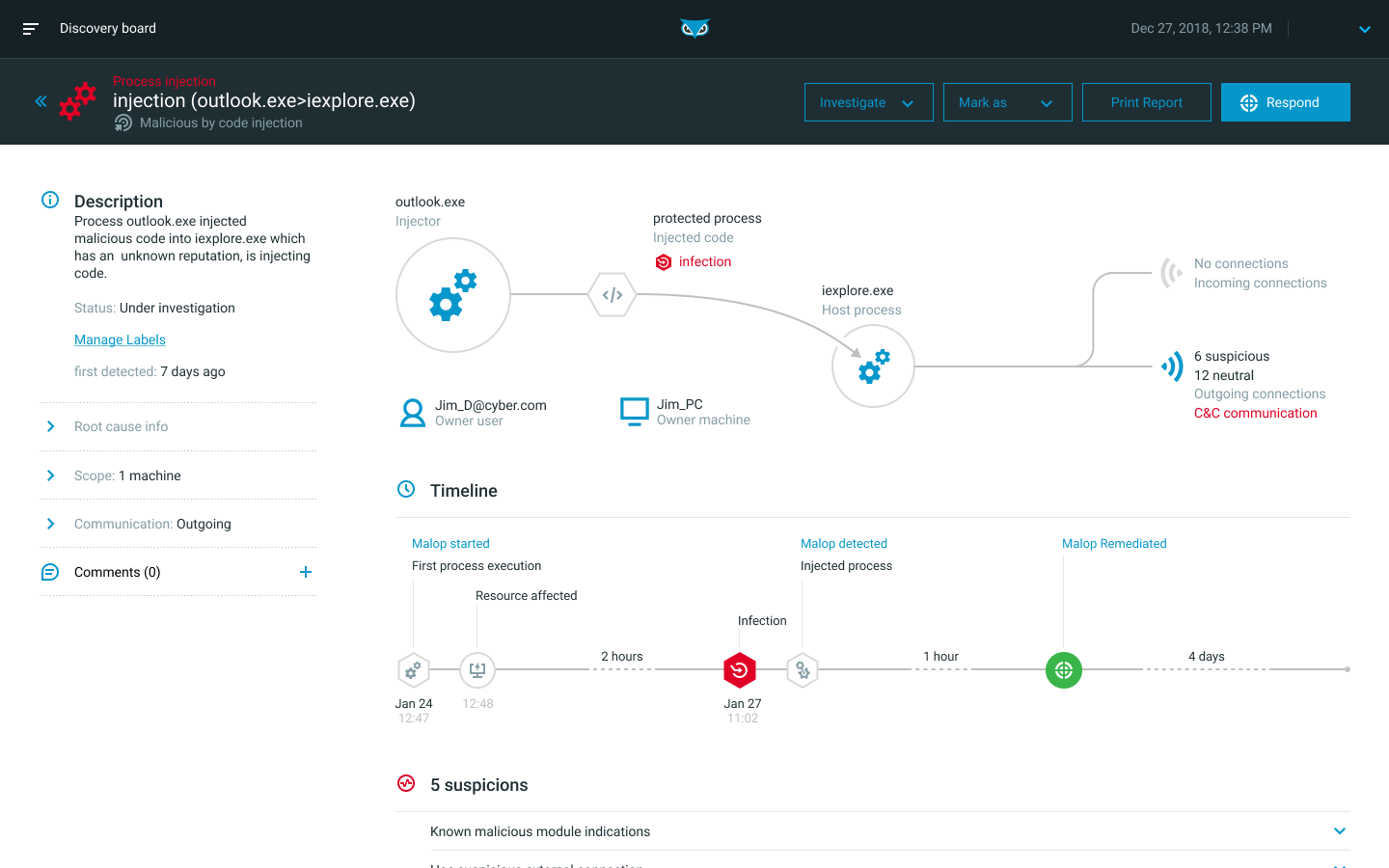
Detection Speed and Accuracy
Cybereason EDR can identify threats quickly with a high degree of accuracy using behavioral analysis that leverages cross-machine correlations and enriched data from across all endpoints in real-time, and the Cybereason cross-machine correlation engine drives an impressive 1:200,000 analyst-to-endpoint ratio, significantly reducing the workload for security teams.
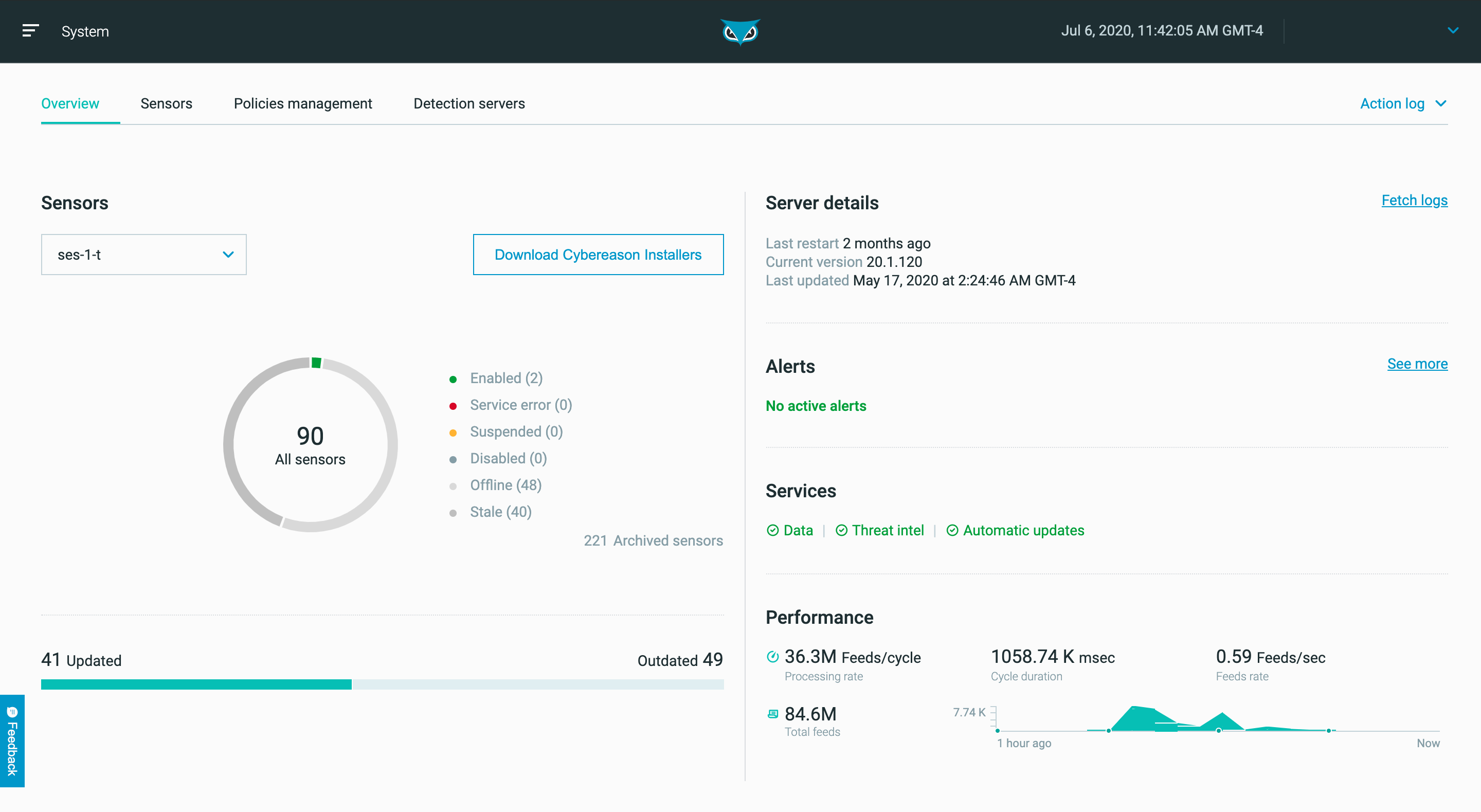
ML-Powered Detection and Correlation of Malicious Behaviors
The Cybereason Defense Platform’s AI surfaces advanced threats by detecting subtle indicators of behavior. Certain malicious behaviors are only identifiable after analyzing enterprise-wide data sets against machine learning. Monitoring via a machine-by-machine basis only can overlook nuanced adversaries whose activity can only be detected when the environment as a whole is analyzed and cross-examined against machine learning.
Once a threat is convicted of being malicious, Defenders need to know the context and other correlated events to deconstruct the entire operation. Cybereason EDR implements machine-learning based deduction to find other artifacts of the operation that are connected to the initial event and compose an automated timeline for rapid response.
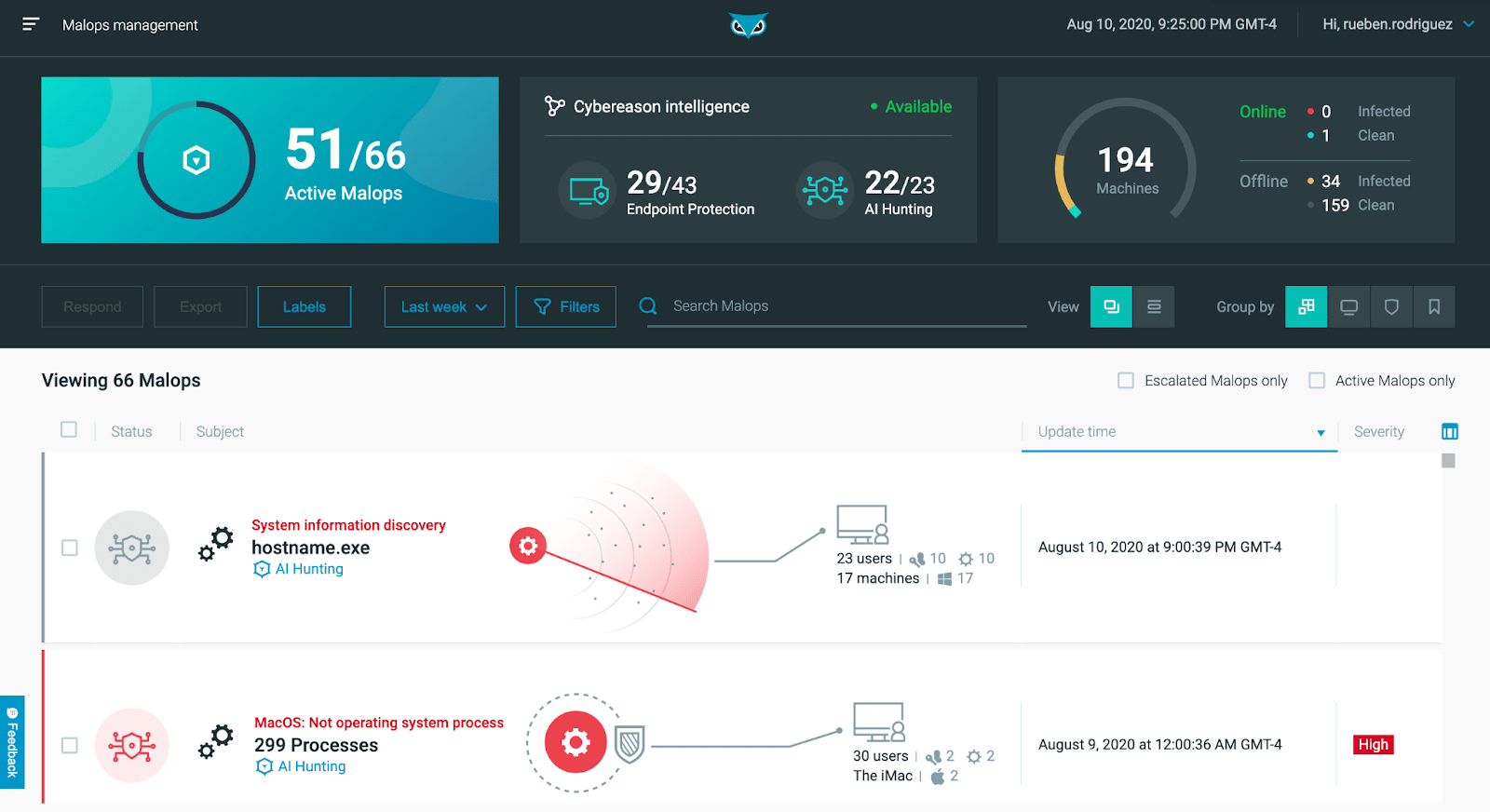
Proven Efficacy
Cybereason EDR earned the highest product score for the “current offering” category in the 2020 Forrester Wave for Enterprise Detection and Response, and the MITRE ATT&CK evaluations highlight the superior proficiency of Cybereason EDR in quickly detecting and correlating threats to instantly deliver the complete story of an attack as an easy to interpret, interactive visual representation.
Research-Driven Insight
The Cybereason Nocturnus Team evaluates new methodologies to sharpen our prevention, detection and response strategies, uncovering both Indicators of Compromise (IOCs) and key Indicators of Behavior (IOBs), the more subtle signs of an attack derived from across the whole of your network. Whether on premises, mobile or in the cloud, Cybereason is the defender’s choice to reverse the adversary advantage.
What is EDR?
What is the meaning of EDR?
EDR is an array of modern, integrated endpoint security tools that detect, contain, investigate, and eliminate invasive cybersecurity threats high in the cyber kill chain.
Read EDR Fundamentals for more
What are the benefits of EDR?
EDR provides better visibility inside an organization's systems by monitoring all the events on all endpoints. EDR uses AI and machine learning to process the data amassed from endpoint events and identify patterns in incidents and processes that could indicate an active threat.
Read EDR Fundamentals for more
EDR Solution Validation
See why Cybereason is the solution of choice for future-ready prevention, detection and response:
Customer Highlight: Olist
With over 1,100 employees and 2,100 endpoints, Olist needed to gain visibility into their attack surface, and staff to investigate and respond to incidents. Learn how a combination of the Cybereason Defense Platform and MDR services increased visibility and led to security performance improvements.
Read NowTop MITRE ATT&CK Performance Scores
Download the results summary to see why Cybereason is the only security vendor that provides unparalleled attack protection by combining 9 independent prevention layers, ensuring that your business achieves its goals, and bad actors don’t.
Read MoreData Sheet
Get the Important Details about Cybereason EDR
Cybereason EDR eliminates ransomware and other malware threats, prevents fileless and in-memory attacks, shortens investigations with correlated threat intelligence via an intuitive UI and automated or single click remediation across all devices with a single lightweight agent.
Read the Data SheetCase Study
Cybereason Endpoint Detection & Response Reviewed by a Real User
"Cybereason absolutely enables us to mitigate and isolate on the fly. Our managed detection response telemetry has dropped dramatically since we began using it."
Read the Case Study
