Get the Important Details about Cybereason Mobile Threat Defense
Cybereason delivers a comprehensive mobile security solution that protects users as they access enterprise data on corporate-owned and Bring Your Own (BYO) devices.
Read the Data SheetWith Cybereason MTD, defenders can protect users accessing data through corporate-owned & BYOD from advanced mobile attacks.
Cybereason MTD is uniquely placed in the market to leverage machine learning to provide real-time, on-device detection against both known and unknown threats.
With ‘Zero-Touch' Deployment, provisioning is simplified for rapid visibility of iOS, Android and Chromebook mobile devices, ensuring protection from modern-day security threats and mitigating associated vulnerabilities.
MTD enables users to work on any device in any location safely, protecting the organizations infrastructure whilst users’ personal data and identities.
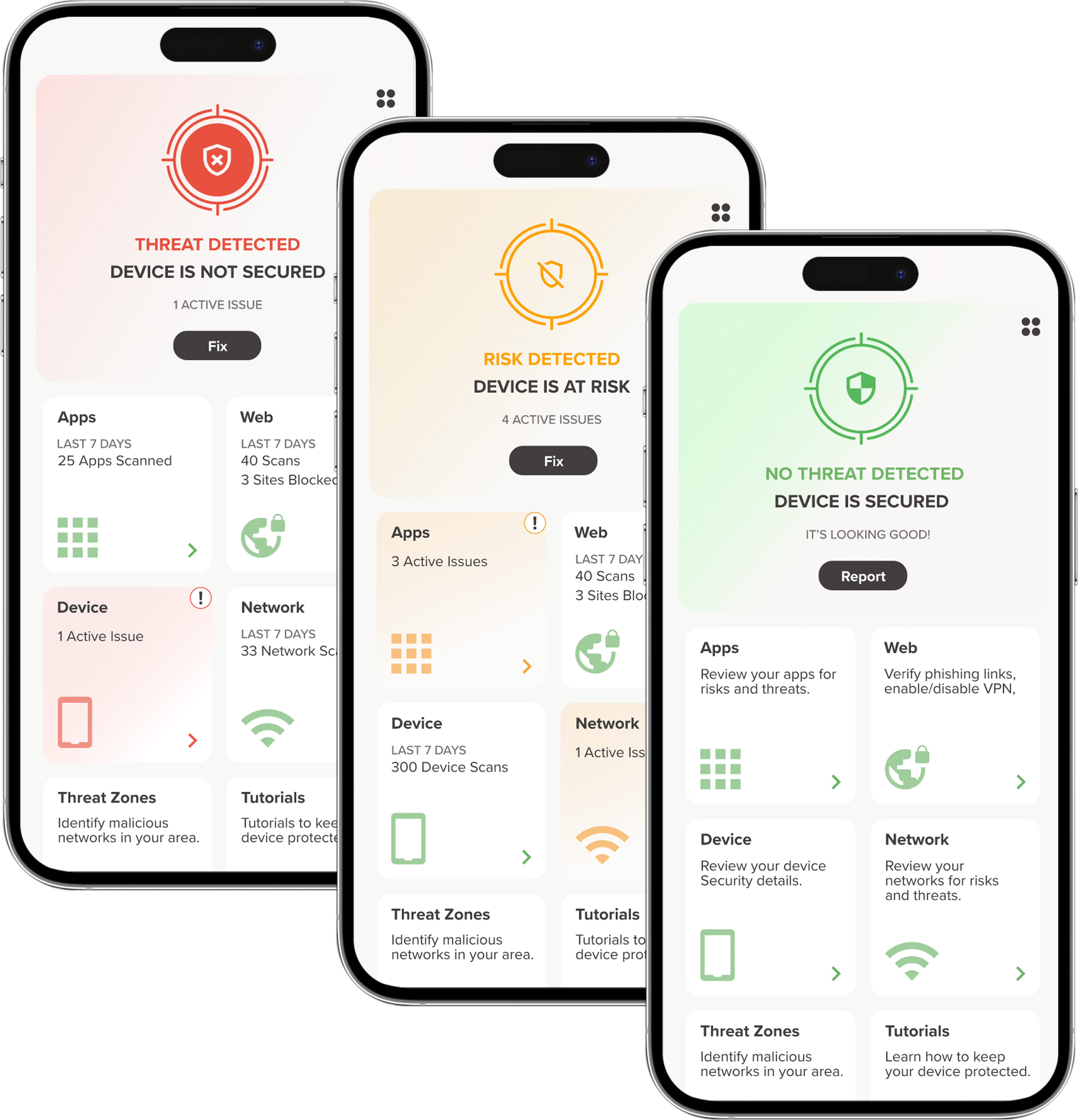
With Mobile devices now making up 75% of all devices accessing corporate data and systems, attackers are shifting their focus to target your users and their mobile devices. Organizations need to have the similar visibility, protection, detection and response capabilities as they do on their traditional endpoints for mobile devices.
As a technology, mobile threat defense is uniquely placed in the market to leverage machine learning to provide real-time, on-device protection against both known and unknown threats.
Cybereason MTD detects known and unknown threats by analyzing the behavior of a mobile device and can accurately identify mobile system deviations, applications that behave as malware, anomalous network traffic, and advanced phishing attacks. It’s the only solution that can simultaneously integrate with multiple MDMs/EMM seamlessly, essential when transitioning solutions.
Data Sheet
Cybereason delivers a comprehensive mobile security solution that protects users as they access enterprise data on corporate-owned and Bring Your Own (BYO) devices.
Read the Data SheetRegister to learn more about the latest mobile threats and how Cybereason’s mobile offering provides real-time, on-device protection against both known and unknown threats.