Security Posture Assessment
An in-depth assessment of your organization’s current security tools, policies and procedures
Security Posture Assessment
The Cybereason Posture Assessment is designed to help organizations understand their current Cybersecurity maturity level and provide insight into their ability to prevent, detect and respond to advanced threats. Customized for each customer, the Cybereason Services Team will work with you to evaluate your current security tools, map the entire attack surface and inventory existing networks and endpoints.
Legacy Security Tools and Procedures
Legacy security tools, resources and procedures can leave an organization wondering if they are capable of preventing, detecting and responding to today’s advanced threats. A Posture Assessment will evaluate an organization’s current tools and help identify gaps that could leave an organization vulnerable to an attack.
New Security Team
Resources and security staff are hard to find, and can be difficult to maintain. A Posture Assessment is a great tool that will help new security members or teams understand their organization’s current threat landscape and what vulnerabilities exist.
Limited Time and Resources
Limited time and resources are common obstacles to creating and maintaining a robust security program. A Cybereason Posture Assessment will evaluate an organization’s existing set of tools, policies and procedures, and deliver actionable recommendations on how to harden your network security and prevent an attack.
Customer Outcomes
Why Cybereason Services
The Cybereason Defense Platform provides threat hunters with the tools and visibility needed to quickly detect, respond to, and remediate threats across the entire network.
Cybereason’s Nocturnus threat intelligence team delivers deep insights on the tools, techniques, and procedures of threat actors from around the world. This robust library of intelligence helps Cybereason Incident Responders identify, predict, and prevent the spread of an attack.
The Cybereason IR Team is comprised of threat hunters and security experts with decades of experience from some of the most respected organizations within both public and private sectors. A dedicated incident responder will be with you every step of the way from deployment through remediation.
Leveraging robust tools such as EDR, Forensics-as-Code, FaC and DFIR, Cybereason’s threat hunters deliver fast and efficient incident response that quickly restores back to business.
Additional Resources
Data Sheet
Posture Assessment Data Sheet
Evaluate your existing security posture
Read the Data SheetData Sheet
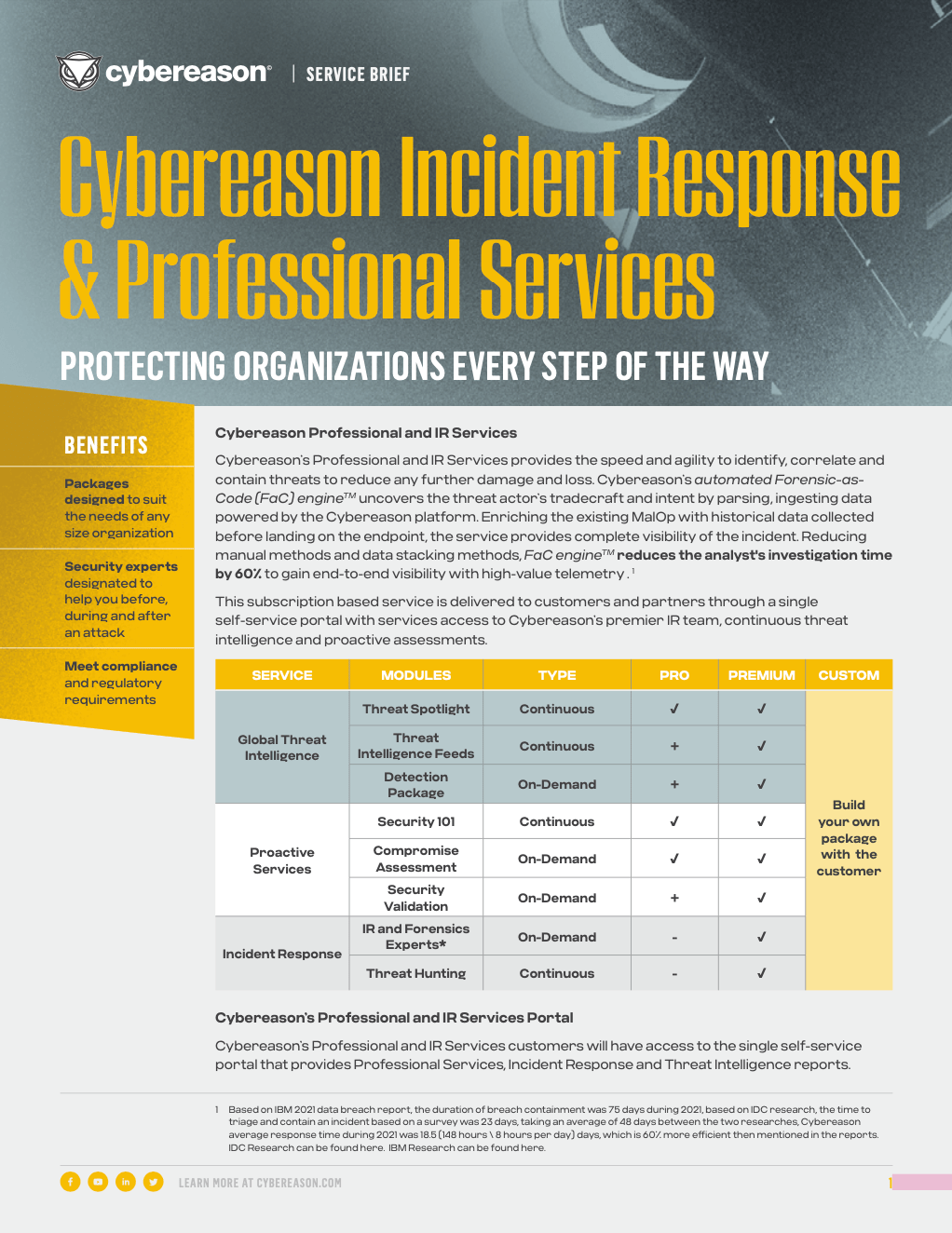
Cybereason IR & Professional Services
Learn more about Cybereason IR & Pro Services Bundles and Cybereason’s unlimited IR.
Read the Data Sheet