
Cybereason Posts Best Results in History of MITRE ATT&CK Evaluations
Cybereason leads the industry in the MITRE ATT&CK Enterprise Evaluation 2022, achieving the best results ever in the history of these evaluations...

Maranda Cigna
Fresh off the press: the results of the 2023 MITRE Engenuity ATT&CK® Evaluations: Enterprise have been published, putting 30 security solutions to the test in real world scenarios that mimic the Turla threat actor.
As is customary, many vendors have been in a frenzy to cherry-pick the results and craft creative narratives and graphs that cast their offerings in the most favorable light. In contrast, Cybereason continues to take pride in allowing the raw evaluation results to tell their own unfiltered story…

This year, Cybereason set a new benchmark with perfect results in nearly every aspect of the evaluations, including:
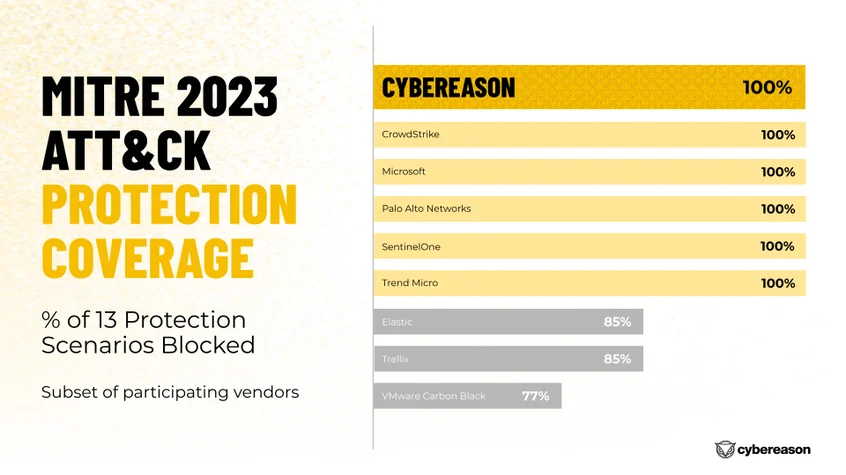
Cybereason delivered COMPLETE prevention coverage in the 2023 Enterprise Evaluation.
A security solution that can't put up a good fight against attackers ultimately sets off a chain reaction of chaos for your security team. Prevention testing figures out if your solution can stop attackers before they even get started. When it can, your security team is in for a smoother ride, since they won't be drowning in a sea of alerts.
Cybereason is the only security vendor that provides unparalleled attack protection by combining 9 independent prevention layers, ensuring that your business achieves its goals, and bad actors don’t. These prevention capabilities are designed to give security pros the tools they need to stay one step ahead of the attacker.
Cybereason uncovered 100% of the attack steps executed, with 97% Technique Detections.
To keep attackers from hiding amongst the noise, you need security tools that can instantly spot attacker behavior. That’s where detection testing comes into play, making sure that your security solution is sharp enough to uncover every move an attacker makes. Technique Detections are the pinnacle of all detections, since they reveal the exact actions an attacker takes when they are aiming for a specific goal.
Cybereason provides businesses with the earliest detection possible by uncovering subtle behavioral indicators (IOBs), rather than relying only on post-attack evidence and artifacts (IOCs). Our detection capabilities ensure that security teams can pick up on even the tiniest hints and clues during an attack.

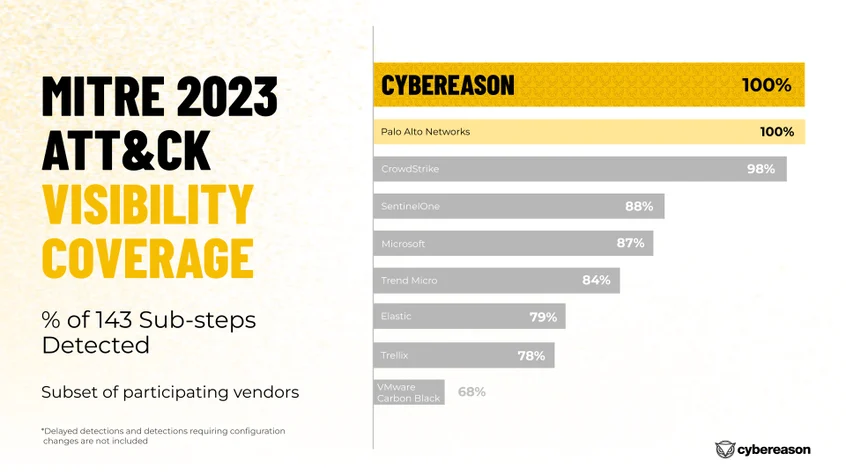
Cybereason exposed 100% of the 143 attack behaviors evaluated for both Windows and Linux.
Visibility matters, especially when dealing with threat actors like Turla. It can be a real challenge for defenders to spot and stop sophisticated attacks, which is why it’s crucial to evaluate a solution’s ability to see the complete picture - where it started, what was impacted, and the complete attack timeline.
Cybereason takes an operation-centric approach, which lets you see the entire attack from where it started right down to every device it touched. This unique capability gives defenders the power to immediately stop malicious operations rather than chasing endless alerts. Using a multi-stage visual breakdown of the attack sequence, packed with all the necessary context that shows you where it all began and who was impacted, Cybereason delivers complete visibility into attacks.
Cybereason spotted and stopped attacks immediately, experiencing ZERO delayed detections.
Delayed detections are ones that are not caught immediately, and instead require additional time and context to identify and catch. When it comes to defending against sophisticated threats, the single most important factor is time, which is why we don’t count detections that don’t occur in real time.
Cybereason provides real-time detection by leveraging all of our customers’ data, which allows us to grasp the full scale of an attack. While other solutions may become inundated with data during an attack and subsequently use data filtering, only the Cybereason MalOp Detection Engine connects all the dots in real-time, giving you a full view of ongoing events as they unfold.
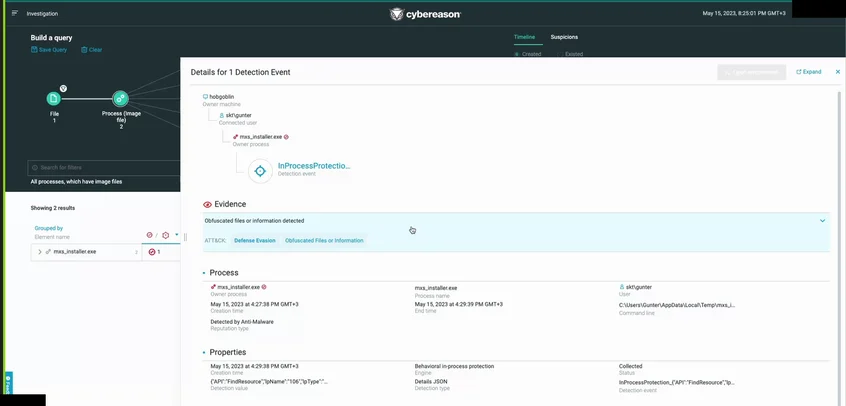
Cybereason detects obfuscated files in real time during MITRE Engenuity Evaluation: Enterprise 2023
Cybereason required ZERO configuration changes in the 2023 Enterprise Evaluation.
When a security solution misses an attack on the first try of a performance test, they have to adjust their configuration settings for another shot at stopping the attack. But in the real world, businesses don’t get a do-over. That’s why out-of-the-box capabilities are so essential - they allow teams to put their energy into critical response actions rather than spend time fiddling with their security systems. For this reason, we don’t count detections that require a configuration change.
Cybereason continuously updates and fine-tunes our detections based on intel from our broad customer and partner base. We also leverage our industry leading research team to help uncover the most complex threats across the globe. This means that customers can immediately deploy and benefit from real-time prevention and detection capabilities that stop even the most advanced cyberattacks.
Join us for a live webinar on September 28th at 4pm CEST / 3pm BST / 10am EDT to hear more about this latest round of MITRE ATT&CK Enterprise Evaluations, including:
The views and opinions expressed in this are those of Cybereason and do not necessarily reflect the views or positions of any entities they represent.

Maranda Cigna, Vice President of Product Marketing, is a cybersecurity practitioner turned product marketer with 15+ years of experience in the global security and technology businesses spanning marketing, consulting, business operations, and product development.
All Posts by Maranda Cigna
Cybereason leads the industry in the MITRE ATT&CK Enterprise Evaluation 2022, achieving the best results ever in the history of these evaluations...

MITRE is the preeminent third-party security solution evaluator. We explain the key metrics to look for in their upcoming Enterprise ATT&CK Evaluation...

Cybereason leads the industry in the MITRE ATT&CK Enterprise Evaluation 2022, achieving the best results ever in the history of these evaluations...

MITRE is the preeminent third-party security solution evaluator. We explain the key metrics to look for in their upcoming Enterprise ATT&CK Evaluation...
Get the latest research, expert insights, and security industry news.
Subscribe