Explore the latest trends, techniques, and procedures (TTPs) our incident response (IR) experts are actively facing with the TTP Briefing Q4 2025, a report built on frontline threat intelligence from our global incident response investigations, enriched by noteworthy detections from our SOC.
The TTP Briefing is grounded in real-world investigations led by our global IR and SOC teams across industries and geographies. As we continue the integration with LevelBlue and expand our threat intelligence to include trillions of events from SpiderLabs, this edition of our TTP Briefing primarily examines Cybereason’s findings from Q4, and compares certain trends to our findings in Q3 and H1 2025. Expect future TTP Briefing editions to include more findings from the unified LevelBlue DFIR, threat intelligence teams.
Findings from Q4 highlight that although organizations are improving detections and enabling faster response to malicious activity in their networks, threat actors are continuing to evolve their techniques to bypass controls. We’re seeing the first lines of defense are proving to be weaker to threat actors evolving tactics: MFA bypass rates are at an all time high, edge devices are being more commonly exploited, phishing tactics are evolving to bypass email security filters, and an uptick in SEO poisoning has lead to an increased downloading of Remote Access Tools (RATs). Although threat actors are not always getting through to ransomware detonation or data exfiltration, they have been gaining entry and viewing/accessing data, which can still trigger regulatory and data privacy issues.
For additional insights, join our IR experts on February 26 at 12:00 ET for a live webinar where they will unpack and dive deeper into our findings. Come armed with questions and walk away with actionable intelligence, detection priorities, and recommendations to strengthen your defenses.
Let’s explore a few key findings:
Most Common Threat Types

- Business email compromise (BEC) remained the top threat incident type, accounting for 42% of incidents.
- Ransomware was again the second most common incident type, at 28%.
- Network intrusion events not resulting in ransomware jumped from 7% in Q3 to 25% in Q4. This is in part due to organizations detecting pre-ransomware intrusions earlier, enabling faster response and less data exfiltration.
Initial Intrusion Vector (How Are They Getting In?)

Phishing remained the dominant initial intrusion vector in Q4 (52%), steadily increasing through 2025. Threat actors continue to vary their phishing tactics, catching victims off guard and gaining access to networks. One of the more unique phishing trends observed in Q4 2025 relates to calendar based phishing, where attackers send victims a calendar invite with a malicious login in the event description. These invites often slip by email filters, landing on victims calendars, appearing trustworthy and capturing credentials.
 Calendar phishing example
Calendar phishing example
Edge devices also remain a top concern, accounting for 18% of initial intrusion vectors. RDP and VPNs continue to be targeted by threat actors, leveraging weaknesses and vulnerabilities to exploit these devices.
Most Commonly Observed CVEs - Q4
|
CVE-2025-24472
|
FortiOS Authentication Bypass
|
|
CVE-2025-61882
|
Oracle
|
|
CVE-2025-40601
|
SonicWall SonicOS SSL-VPN
|
|
CVE-2024-55591
|
Fortinet FortiOS
|
|
CVE-2024-53705
|
SonicWall SonicOS SSH
|
|
CVE‑2024‑53704
|
SonicWall SonicOS SSL-VPN
|
|
CVE‑2024‑40762
|
SonicWall SonicOS SSL-VPN
|
|
CVE-2024-21762
|
Fortinet FortiOS
|
|
CVE-2023-399280
|
SonicWall SonicOS Stack-Based Buffer Overflow
|
|
CVE-2023-399279
|
SonicWall SonicOS Stack-Based Buffer Overflow
|
|
CVE-2023-399278
|
SonicWall SonicOS
|
|
CVE-2023-38277
|
SonicWall SonicOS Stack-Based Buffer Overflow
|
|
CVE-2023-39276
|
SonicWall SonicOS Stack-Based Buffer Overflow
|
|
CVE-2019-18935
|
Telerik UI
|
MFA Implementation Continues To Rise, with MFA Bypass at an All Time High

MFA Bypass over time
In Q4 we continued to see more organizations regularly implementing MFA, up to 92% from 53% in H1, and 75% in Q3. While MFA is becoming more widely implemented, we saw it being bypassed by threat actors almost every time (96%). This demonstrates that diverse phishing tactics, attackers in the middle (AiTM), and session token interceptions remain prevalent threats.
Most Targeted Industries & Company Sizes

Similarly to Q3 and H1, financial services remains the most targeted industry. This quarter, we saw an increased targeting of both Legal & Professional Services and Manufacturing, both steadily rising from Q3 and H1.
Organizations with revenue between $1M - $10M were the most frequently impacted, indicating that even small businesses still need to prioritize maturing their cyber defenses.
Tactics Across the Intrusion Path
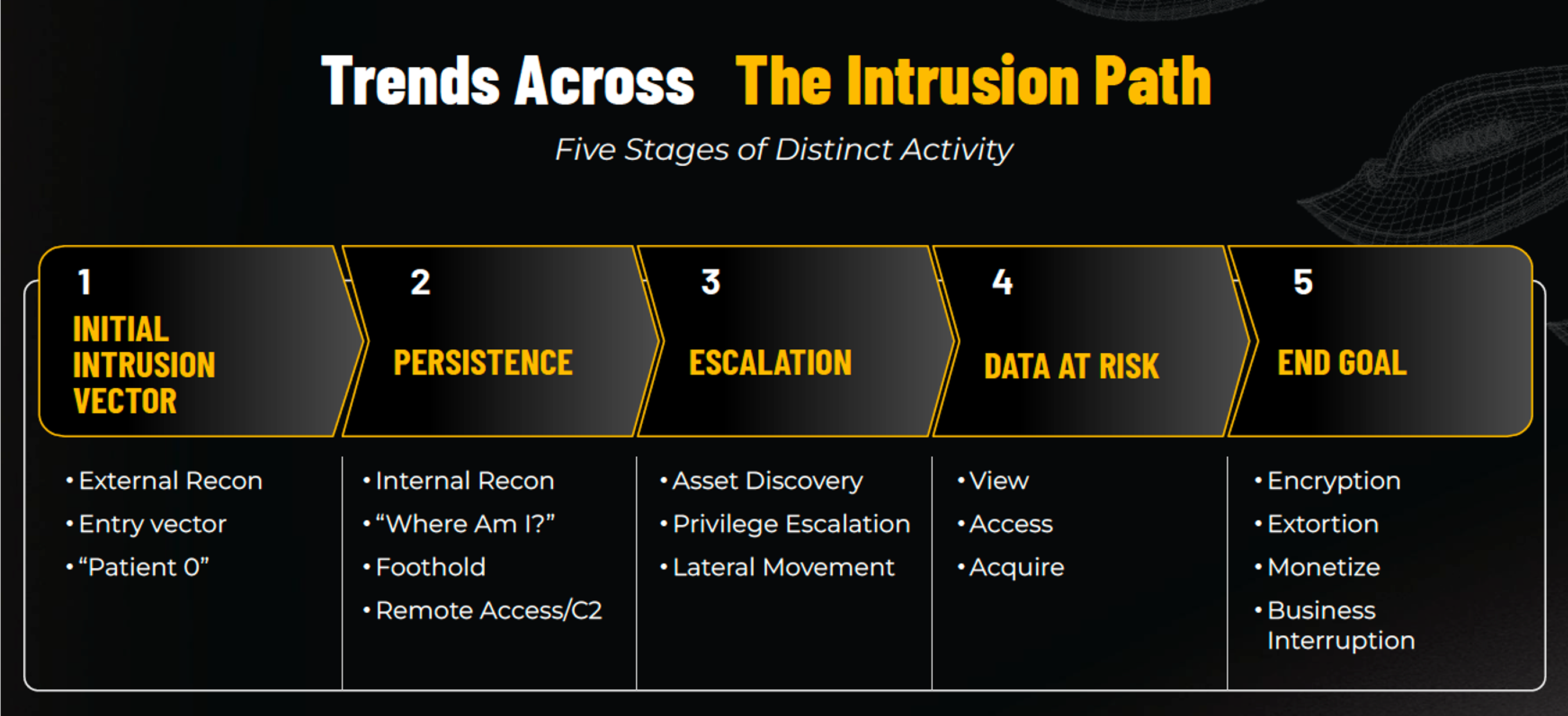
The TTP Briefing provides data across the five stages of the intrusion path, from initial intrusion to persistence and escalation techniques, to exfiltration and monetization tactics. Noteworthy findings include:
- Threat actors continue to leverage Anydesk and Netscan as the most common tools for persistence.
- Remote access tools (RATs) have increased as a method for escalation, due to more frequent SEO poisoning, leading to the inadvertent download of malicious tooling.
- While there’s been an increase in pre-ransomware attacks, threat actors are less frequently reaching the exfiltration stage. Our findings show evidence of files being viewed/accessed, but early detection helps activate response in time to avoid data exfiltration.
SEO Poisoning Increases RAT Downloads
 Increase in Remote Access Tool (RAT) usage over time
Increase in Remote Access Tool (RAT) usage over time
In Q4, we observed a sharp rise in SEO poisoning campaigns designed to trick users into downloading legitimate-looking Remote Access Tools (RATs), dramatically expanding attacker footholds inside enterprise environments. The use of RATs for privilege escalation surged from just 3% of investigations in Q3 to 60% in Q4, signalling a shift from opportunistic use to systematic deployment for persistence, credential access, and internal reconnaissance.
Once the user installs these tools, they enable broader asset discovery and lateral movement to the attacker. This is also reflected in a parallel increase in network intrusion activity, which rose from 7% in Q3 to 25% in Q4. Together, these trends indicate that threat actors are increasingly abusing trusted software and search results as an initial access vector, allowing them to blend in with legitimate IT activity while rapidly escalating privileges and expanding their reach across the network.
A Look Into Dwell Time

In the TTP Briefing, we exclude any MDR clients and measure dwell time the initial date of the compromise until our IR team is engaged. 42% of our cases had 31+ day dwell time, up from 38% in Q3, demonstrating that threat actors remain stealthy in environments, careful to stay undetected for longer periods.
One factor that can contribute to the appearance of longer dwell times relates to initial access brokers (IABs), who obtain unauthorized access and then sell that access to another threat actor group. Therefore, we often observe a latency period between initial exploitation and the new threat actor leveraging the unauthorized access. During the latency period, within the overall 31+ dwell time averages, there is commonly no active malicious activity going on in the network, but the organization has been compromised.
If you would like more information about this report, our team is available 24x7 at response@cybereason.com



.png)










.png)