Explore the latest trends, techniques, and procedures (TTPs) our incident response (IR) experts are actively facing with the TTP Briefing Q3 2025, a report built on frontline threat intelligence from our global incident response investigations, enriched by noteworthy detections from our SOC.
The TTP Briefing is grounded in real-world investigations led by Cybereason’s IR and SOC teams across industries and geographies. This edition of our TTP Briefing examines our data from Q3, and compares certain trends to our findings in H1 2025.
Findings from Q3 highlight that the gap between organizations’ cybersecurity and the techniques used by threat actors has not diminished. We’re seeing even higher rates of successful multi-factor authentication (MFA) bypass and vulnerability exploitation, a growing number of insider threat cases, and the adoption of detection evasion tactics previously used only by advanced threat actors becoming the norm. Continuing to refine your cybersecurity posture is key to staying resilient against these types of threats, and our 11 Essential Cybersecurity Controls can help organizations focus efforts on what matters most.
Watch the Full TTP Briefing Session Recording:
Let’s explore a few key findings:
Most Common Threat Types
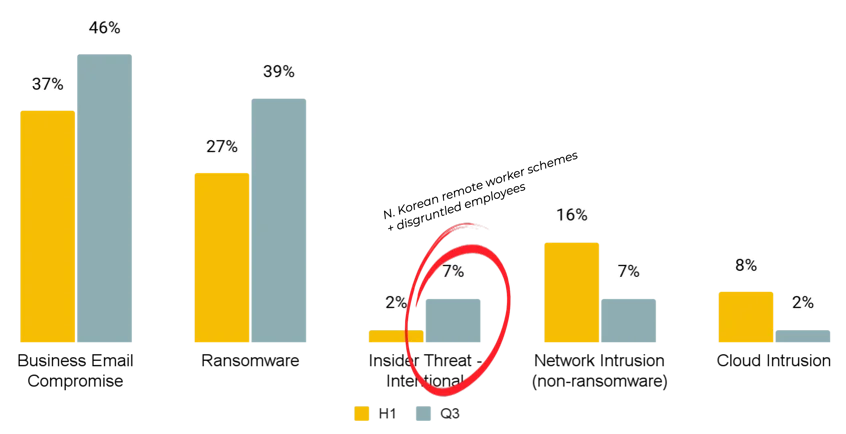
- Business email compromise (BEC) remained the top threat incident type, accounting for 46% of incidents, up from 37% in H1.
- Ransomware was again the second most common incident type, at 39%.
- Insider threats jumped from 2% in H1 to 7% in Q3. This is in part due to increased activity around North Korean remote worker schemes, and disgruntled employees absconding proprietary data.
Initial Intrusion Vector (How Are They Getting In?)
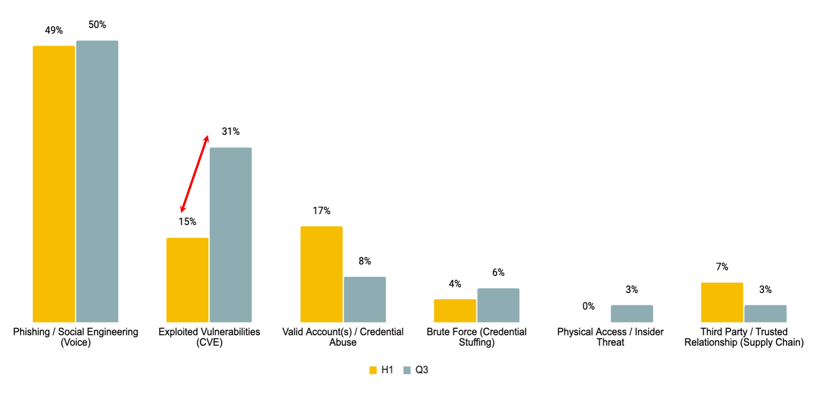
Phishing remained the dominant initial intrusion vector in Q3 (50%), consistent with H1. Surprisingly, exploited vulnerabilities (CVE) jumped up to the second position (31%), and more than doubled from H1 (15%). This is largely due to an increase in CVEs with CVSS scores greater than 9.5 and highlights the importance for organizations to strengthen their vulnerability patching and management programs.
Most Commonly Observed CVEs - Q3
|
CVE-2025-53770
|
On-Premises Microsoft SharePoint Server
|
|
CVE-2025-30406
|
Gladinet CentreStack
|
|
CVE-2025-24477
|
Fortinet FortiOS
|
|
CVE-2024-53704
|
SonicWall SonicOS SSL-VPN
|
|
CVE-2024-40766
|
SonicWall SonicOS
|
|
CVE‑2024‑23113
|
Fortinet FortiOS
|
|
CVE‑2024‑21762
|
Fortinet FortiOS
|
|
CVE-2023-5970
|
SonicWall SMA100 SSL-VPN
|
|
CVE-2023-44221
|
SonicWall SonicOS SSL-VPN
|
|
CVE-2023-27997
|
Fortinet FortiOS
|
|
CVE-2022-2915
|
SonicWall SMA100
|
|
CVE-2022-1703
|
SonicWall SMA100 SSL-VPN
|
Deep Dive into CVE-2024-40766: SonicWall SonicOS Vuln
During Q3, Akira was observed gaining unauthorized access to SonicWall devices through previously harvested user credentials obtained through exploitation of CVE-2024-40766. Many affected SonicWalls were previously compromised before being patched. Even on devices that were patched, if administrators did not also reset all SSL VPN credentials, threat actors have been able to leverage previously stolen information to gain access. Some attacks were assessed as having involved credentials that were migrated from older SonicWall devices and never reset.
MFA Implementation Continues To Rise, But So Do Bypass Techniques
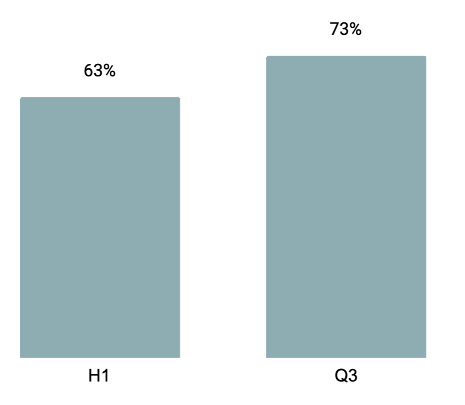
Between H1 and Q3, we saw more organizations regularly implementing MFA, up to 75% from 53%. While MFA is becoming more widely implemented, we saw an increase in it being bypassed (73%). This demonstrates that phishing kits, attackers in the middle (AiTM), and session token interceptions remain prevalent threats. Implementing a phishing-resistant form of MFA (such as passkeys) can better protect against these types of attacks.
Most Targeted Industries & Company Sizes
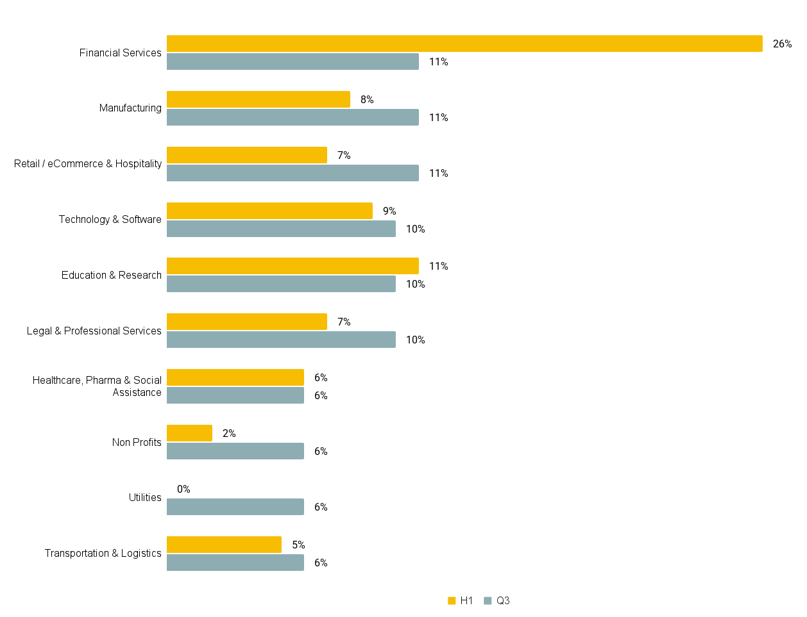
Similarly to H1, financial services remains a commonly targeted industry. But this quarter, we saw a more even distribution of attacks across sectors, with financial services, manufacturing, and retail/eCommerce & Hospitality all tying for the top spot at 11%.
Organizations with revenue between $1M - $10M were the most frequently impacted, indicating that even small businesses need to focus on maturing their cyber defenses.
Tactics Across the Intrusion Path
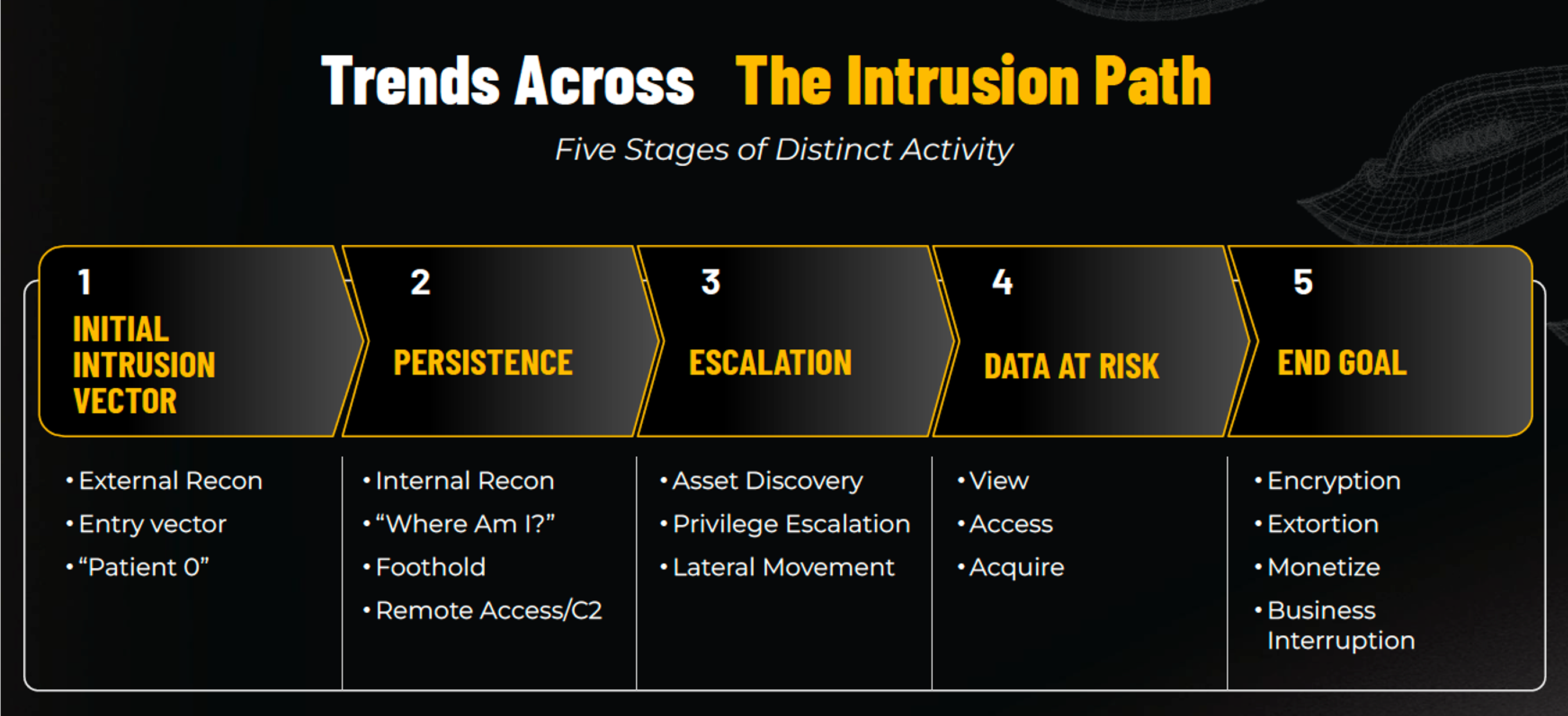
The TTP Briefing provides data across the five stages of the intrusion path, from initial intrusion to persistence and escalation techniques, to exfiltration and monetization tactics. Noteworthy findings include:
- Threat actors are continuing to leverage a myriad of tools to obtain persistence, including Anydesk and Netscan, but also increasingly leveraging newer tools such as impacket and pinggy.
- Credential stealers remain a common method for escalating privileges, leveraging tools like Mimikatz and DCSync.
- Threat actors continue to focus their efforts on data exfiltration, using tools like WinRar and WinSCP.
Threat Actors Are Increasingly Living-Off-the-Land, Hindering Detection
We observed living-off-the-land binaries (LOLBINs) usage in 17% of investigations in Q3, up from 13% in H1 2025. These trusted, built-in system tools let attackers more easily blend in with legitimate activity, evade detection, and carry out attacks without deploying malware. This is raising stakes for defenders, who must now strengthen their behavioral monitoring and contextual analysis for hunting and detecting attacks, leveraging modern EDR and SIEM platforms.
A Look Into Dwell Time
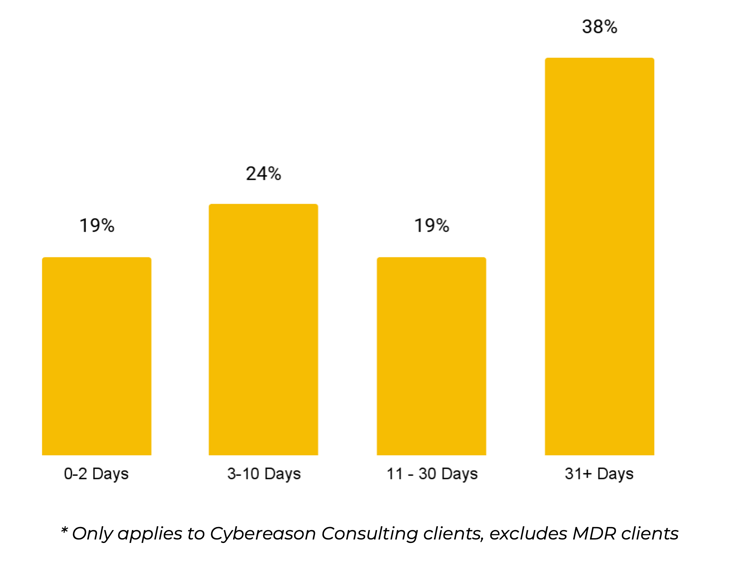
In the TTP Briefing, we excluded any MDR clients and measured dwell time as the initial date of the compromise until our IR team was engaged. 38% of our cases had 31+ day dwell time, down from 45% in H1. While this is still not ideal, we are seeing a slight improvement in response time.
One factor that can contribute to the appearance of longer dwell times relates to initial access brokers (IABs), who obtain unauthorized access and then sell that access to another threat actor group. Therefore, we often observe a latency period between initial exploitation and the new threat actor leveraging the unauthorized access. During the latency period, within the overall 31+ dwell time averages, there is commonly no active malicious activity going on in the network, but the organization has been compromised.
Reducing dwell time can be addressed with a proper incident response plan, streamlining the time between detection and DFIR vendor engagement. In addition, there are a number of cybersecurity controls you can implement that can reduce the likelihood, dwell time, and impact of an incident.
If you would like more information about this report, our team is available 24x7 at response@cybereason.com



.png)







.png)