Cybereason issues Threat Alerts to inform customers of emerging threats, including critical vulnerabilities such as CitrixBleed. Cybereason Threat Alerts summarize these threats and provide practical recommendations for protecting against them.
What is CitrixBleed?
The Cybereason Security Services team is investigating incidents that involve the exploitation of a critical vulnerability which exists in NetScaler ADC (previously Citrix ADC) and Citrix Gateways (VPN virtual server, ICA proxy, CVPN, or RDP proxy). The vulnerability, known as CitrixBleed, is tracked as CVE-2023-4966 and has a critical CVSS Score of 9.4.
This vulnerability allows attackers to send a large HTTP GET request to the ADC/Gateway, resulting in a buffer overread error. If the exploit is successful, the memory adjacent to buffer overflow is leaked. The memory can contain anything including user passwords, session tokens etc. The threat actor can extract sensitive information (passwords, sessions tokens) from the leaked memory. The post exploitation techniques and the attack model depends upon the extracted user account/session permission and scope of access.
This memory can also include users’ MFA-authenticated session information. The information can then be used to hijack the user’s session and act as a known user. CitrixBleed enables attackers to bypass MFA and password authentication, allowing the attacker to evade defenses to exploit the environment in the context of a legitimate user.
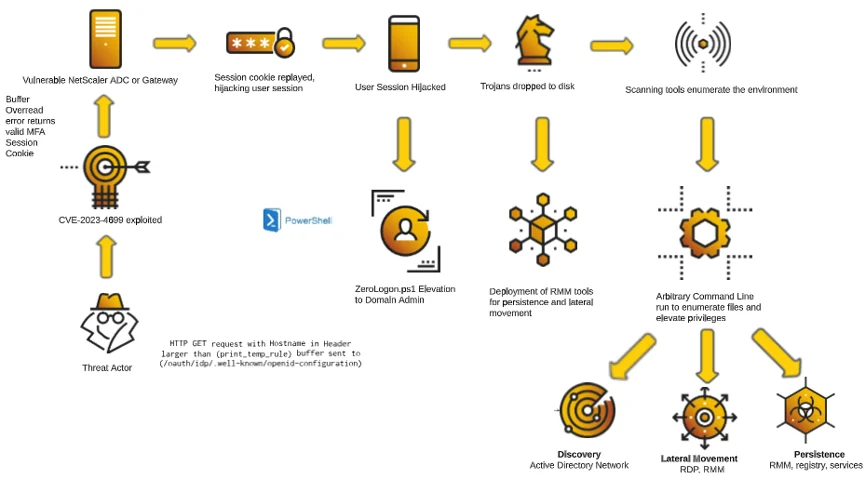 CitrixBleed Exploitation Pattern
CitrixBleed Exploitation Pattern
KEY OBSERVATIONS
This section describes the key observations made following the investigation of incidents which started due to the CitrixBleed vulnerability:
- Initial Access - Session Hijacking: Valid user sessions from unknown IP addresses, internal or external.
- Credential Access: User credentials were dumped from the browsers (Firefox, Chrome, Internet Explorer). Attackers may try to extract passwords from multiple targets.
- Reconnaissance: The attacker will target the servers that implement the NetScaler Gateway Authentication process. Attackers scan the environment to enumerate network targets. Powershell is used to find all text, PDF, Word documents, and Excel files written to disk in the past 30 days. Windows Management Instrumentation (WMI) is leveraged to search for any connected storage. Actors use nltest and dnsdump to query Active Directory domains.
- Lateral Movement: Attackers use Network share (net use) and built-in utility pushd to install RMM tools in other servers.
- Exfiltration: After installing RMM tools, the attackers can export sensitive data from company cloud storage to threat actor-controlled cloud storage.
- Privilege Escalation - NTDS.DIT Retrieved From Domain Controllers: Zero-Logon.ps1 is executed from a raw Github attempting to elevate privileges to Domain Administrator (in the observed case this was blocked by the Cybereason Defense Platform). Actors then take steps to extract the NTDS.DIT from the Domain Controller.
- Deployment Of Multiple RMM Tools: Threat actors make use of multiple RMM tools such as AnyDesk, Atera, Splashtop, and ConnectWise.
- Deployment Of Tedy & Boigy Trojan Variants: Execution of an unsigned .dll and an unsigned .exe, which did not match public malware and threat intelligence signatures, were recognized by Cybereason’s Variant Payload Protection capability.
- Post-exploitation Activities Detected By Cybereason: The Cybereason Defense Platform is capable of detecting these types of lateral movement and exploitation activities.
CYBEREASON RECOMMENDATIONS
The Cybereason Defense Platform can detect and prevent CitrixBleed post-exploitations. Cybereason recommends the following actions:
- Customers should immediately implement patching of affected Citrix versions in conjunction with manufacturer provided updates and the associated CISA advisory.
- Monitor the environment for:
- Unapproved Remote Monitoring and Management (RMM) tools
- Unknown .dlls communicating with unknown/unauthorized destinations
- User sessions from unapproved IP addresses.
- Reset all active NetScaler sessions following update, as the vulnerable sessions still persist after patching, per above Citrix recommendation.
- Perform periodic log reviews of NetScaler ADC and NetScaler Gateway Appliance logs (syslog and ns.log).
- Employ Web Application Firewalls (WAF) and HTTP/S recording in your network appliances and monitor for SSL VPN connections with a mismatched Client IP and Source IP, indicative of session hijacking. When a session is brokered between an endpoint and a NetScaler ADC/Gateway, Citrix’s Virtual Delivery Agent (VDA) records information regarding the users’ initial session IP address in the NetScaler’s registry. In the event an attacker hijacks the session, there will be a difference between the logged, initial session IP and the attacker’s hijacked session IP. External IPs from unauthorized geolocations could indicate possible malicious activity.
- Examine Host/IP connections in your NetScaler’s registry:
-
\Policies\Citrix\<session #>\Evidence\ClientName
-
\Policies\Citrix\<session #>\Evidence\ClientIP
- \Policies\Citrix\<session #>\Evidence\BrokeringUserSid
- \WOW6432Node\Policies\Citrix\<session #>\Events\LastUpdate
- \WOW6432Node\Policies\Citrix\<session #>\Evidence\ClientName
-
Ensure Cybereason’s Variant Payload Prevention and Behavioral Execution Prevention features are enabled per policy.
- Hunt proactively using the Investigation screen in the Cybereason Defense Platform and the queries in the Hunting Queries section to search for assets that have potentially been exploited. Based on the search results, take further remediation actions, such as isolating the infected machines and deleting the payload files.
- Add relevant Indicators of Compromise (available in the Threat Alert report) to the custom reputation with “Block & Prevent”.
DOWNLOAD THE FULL THREAT ALERT
This blog post is the summary of a full 21-page Threat Alert, which can be downloaded here.
ABOUT THE RESEARCHERS
 Scott Shaulis, Security Analyst, Cybereason Global SOC
Scott Shaulis, Security Analyst, Cybereason Global SOC
Scott Shaulis is a Security Analyst with the Cybereason Global SOC team. He is involved with active MalOp Investigation, Threat Hunting, Malware Analysis, and remediation. Scott holds an Associate's of Applied Science in Information Systems and is currently pursuing a Bachelors in Software Development.
 Hema Loganathan, Security Analyst, Cybereason Global SOC
Hema Loganathan, Security Analyst, Cybereason Global SOC
Hema Loganathan is a Security Analyst with the Cybereason Global SOC team. She is involved in Malop Investigation, Malware Analysis, Reverse Engineering and Threat Hunting. Hema has a Master of Science degree in Information Systems.





 Scott Shaulis, Security Analyst, Cybereason Global SOC
Scott Shaulis, Security Analyst, Cybereason Global SOC Hema Loganathan, Security Analyst, Cybereason Global SOC
Hema Loganathan, Security Analyst, Cybereason Global SOC
