If you want to build and maintain a heatmap of your organization’s detection coverage, it requires a mixture of art, science, and actionable transparency from your security vendors. Today, the MITRE ATT&CK Framework has become the de-facto language for how we communicate, analyze, and attribute adversary activity.
However, mobilizing the powerful framework into a living strategy against cyber threats comes with several challenges.
Common hurdles include understanding:
- What is my range of detection coverage across security products?
- Are we able to validate these results ourselves or via published testing (e.g. ATT&CK evaluation data)?
- What are the types of threats we should prioritize as an organization?
Leveraging the Tidal Platform Heatmap
To help Defenders with these challenges, we have partnered with Tidal Cyber, an exciting firm focused on helping security teams achieve the benefits of threat-informed defense in a practical and sustainable way.

The Tidal Platform, which launched in August, makes it efficient to research adversary techniques using MITRE ATT&CK and easy to determine what to do about techniques you may not have defenses against. Cybereason has joined the Tidal Product Registry, which presents a visual view of our out-of-the-box detection capabilities.
With a complimentary registration to Tidal Community Edition, you can explore:
- Cybereason EDR and Cybereason NGAV prevention, detection and response,
- Cybereason XDR detections across Workspace, Identity, Cloud, and Network data sources
- Compare this heatmap to infamous threat actors ranging from Carbanak to Turla.
Sign up for a Tidal account and explore the platform here…
EXPLORE
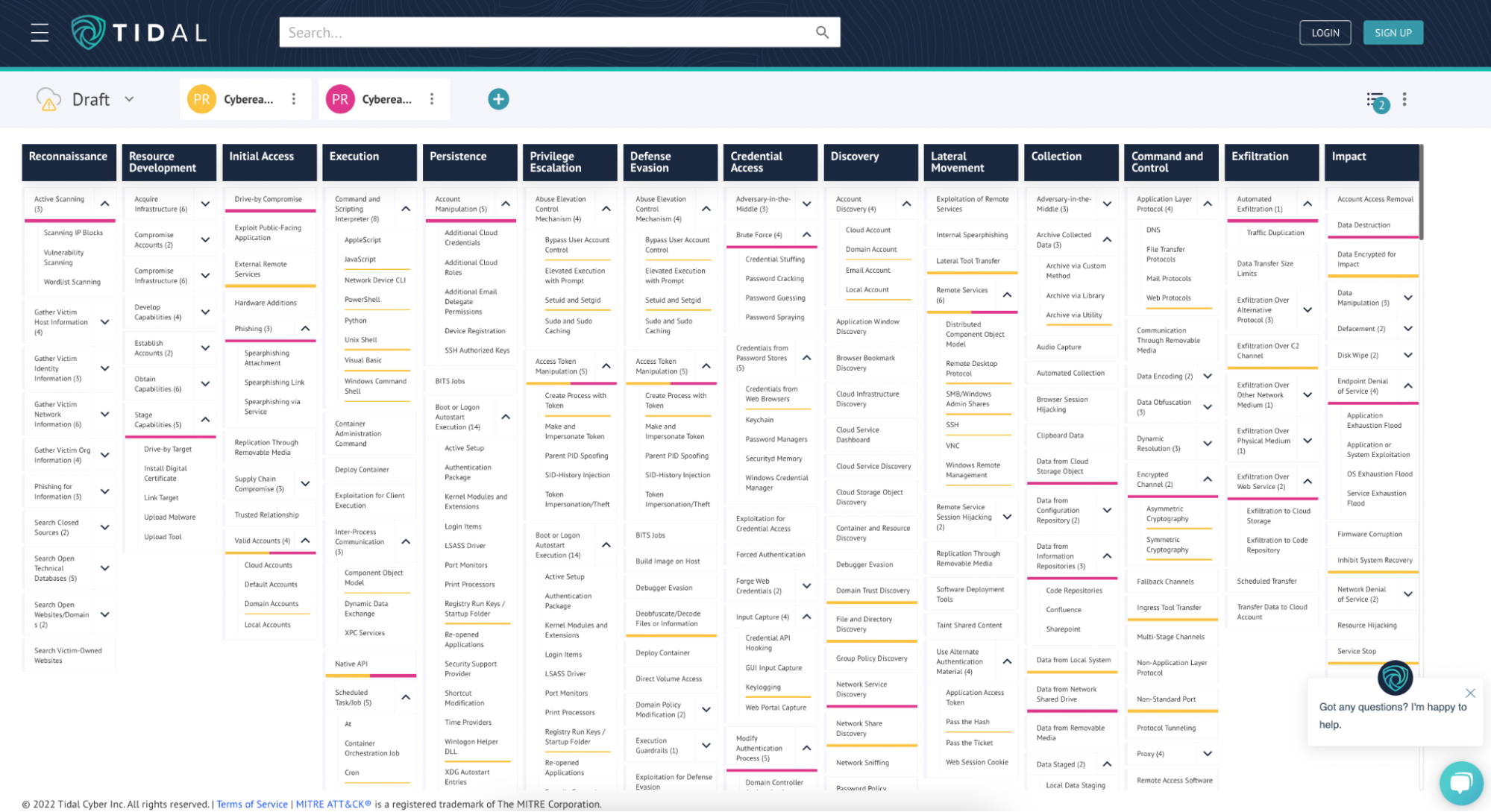
Where Did the Data Come From?
Our core differentiator at Cybereason is our Operation-Centric approach. Instead of generating and surfacing individual alerts, we present a visual of the entire MalOp™ (malicious operation) from root cause across every impacted asset and user.
All of our MalOps and Suspicious Events are mapped to the MITRE ATT&CK Framework, making it easier to understand the context behind the technique, threat hunt, and pivot across data searching for behaviors.
When sharing our detections library with Tidal, we drew from all four rounds of the MITRE ATT&CK Evaluations – including our 100% prevention scores across Round 3 and 4. That is represented in the “EDR & NGAV layer” of the heatmap. Then with Cybereason XDR, we’re able to show our analytics for common IT and security technologies like Office 365, Google Workspace, Azure Active Directory, Okta, and more.
Operationalizing MITRE ATT&CK
Whether you’re evaluating EDR, XDR or a Managed Detection and Response (MDR) partner, it’s increasingly important to know a vendor’s range of detection capabilities, whether it requires configuration or tuning, and what can be accomplished from a prevention or response perspective.
In the below video I am joined by Frank Duff, Tidal CIO, and Israel Barak, Cybereason CISO, for a fireside chat on the rich and ever-evolving story behind MITRE ATT&CK, how customers are maturing use of the framework, and how detections will evolve in an XDR world:
We’re very excited to launch our partnership with Tidal Cyber: check out their Community Edition and let us know how you’re mobilizing MITRE ATT&CK to track and report on your threat detection strategy.







