Security Operations Centers (SOCs) are the first line of defense for businesses when responding to cyber attacks. But with SOC teams struggling to find skilled resources coupled with the increasing volume and sophistication of attacks, Defenders must have a well-defined incident response workflow.
The Cybereason Defense Platform offers multi-tenancy capabilities to enable SOC teams to divide workflows based on roles:
The Cybereason Defense Platform offers multi-tenancy capabilities to enable SOC teams to divide workflows based on roles:
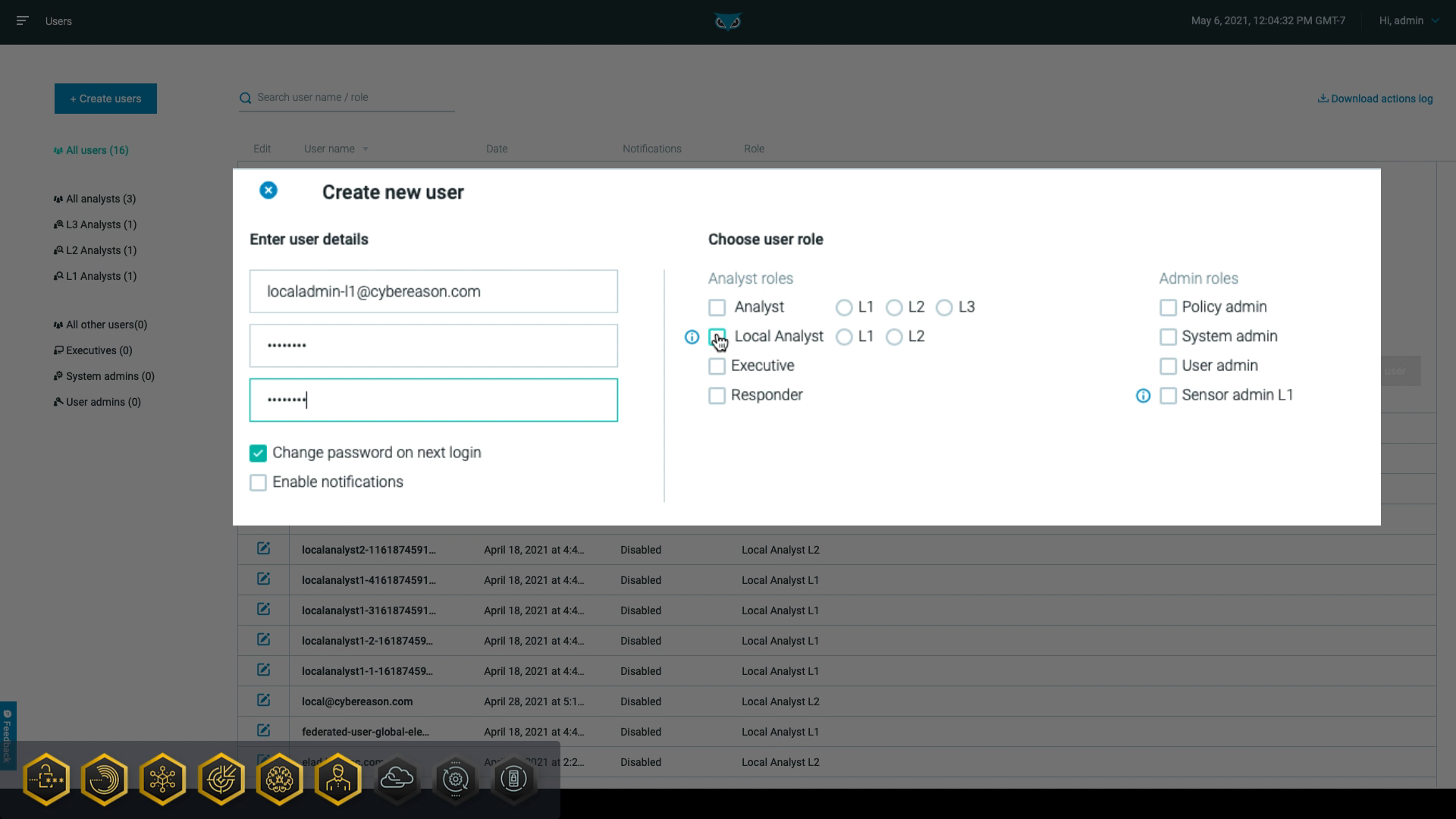
Cybereason provides multiple roles to which you can assign users, making it easy to limit specific tasks to certain users. For example, level one (L1) analysts can use the MalOp™ (malicious operation) management screen to quickly escalate more severe threats to higher level analysts, who have permission to investigate further and respond to the threats.
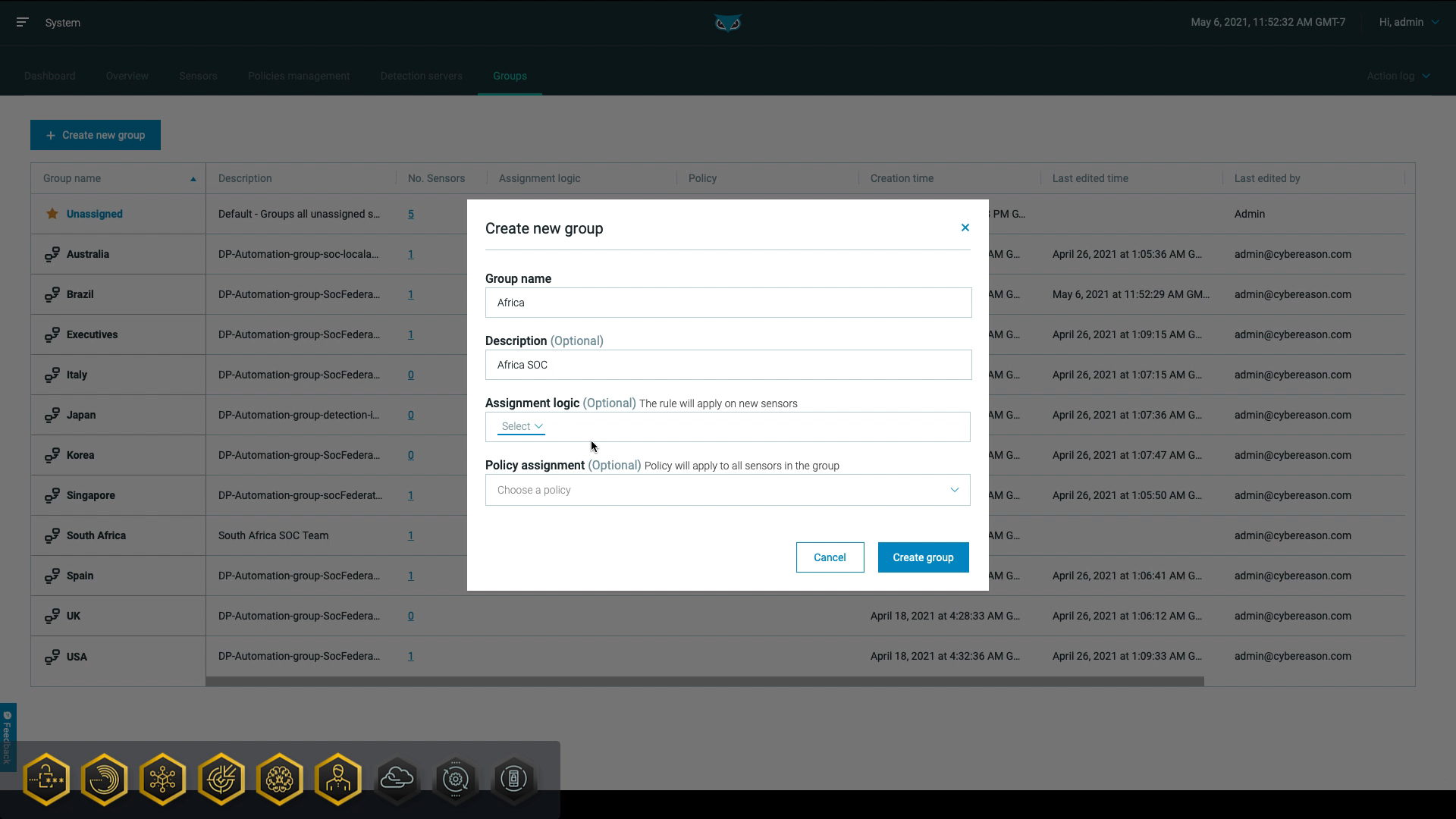
In addition, the Cybereason subtenant capability allows for role-based access to sensor data and administration tasks. First, system administrators create groups representing subtenants and assign sensors to these groups:
Then, as seen in the following graphic, the user administrators can set the user admin L1, user role, or the local analyst role and specify which subtenants the user should have access to:
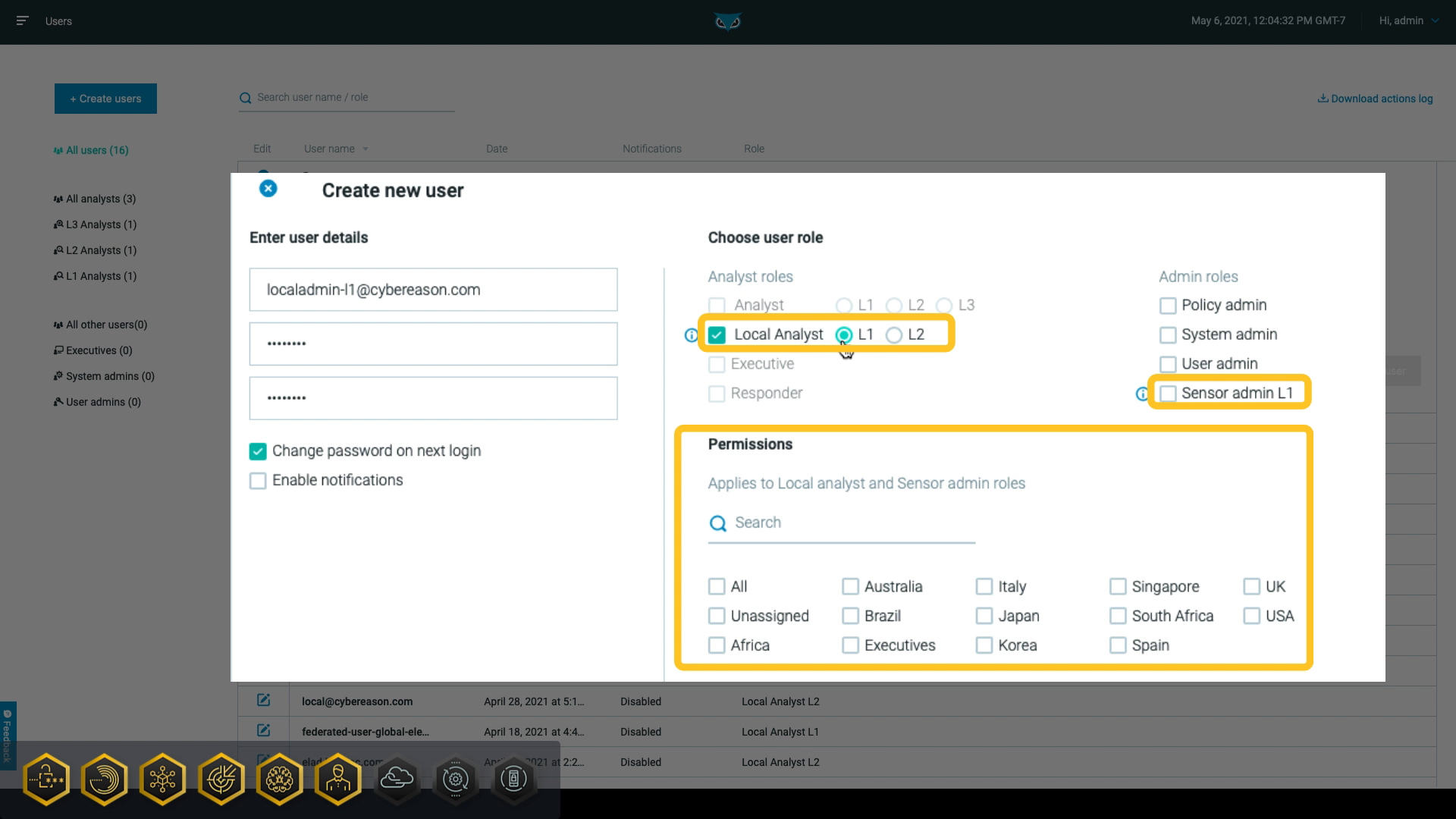
Sensor admin L1 users can perform limited sensor administration tasks related to sensors in their subtenant. Similarly, local analysts can view and interact with data and MalOps associated with machines in their subtenant.
This allows both sensor administrators and local analysts to focus on machines and MalOps in their federated environment while removing information that is not relevant to them:
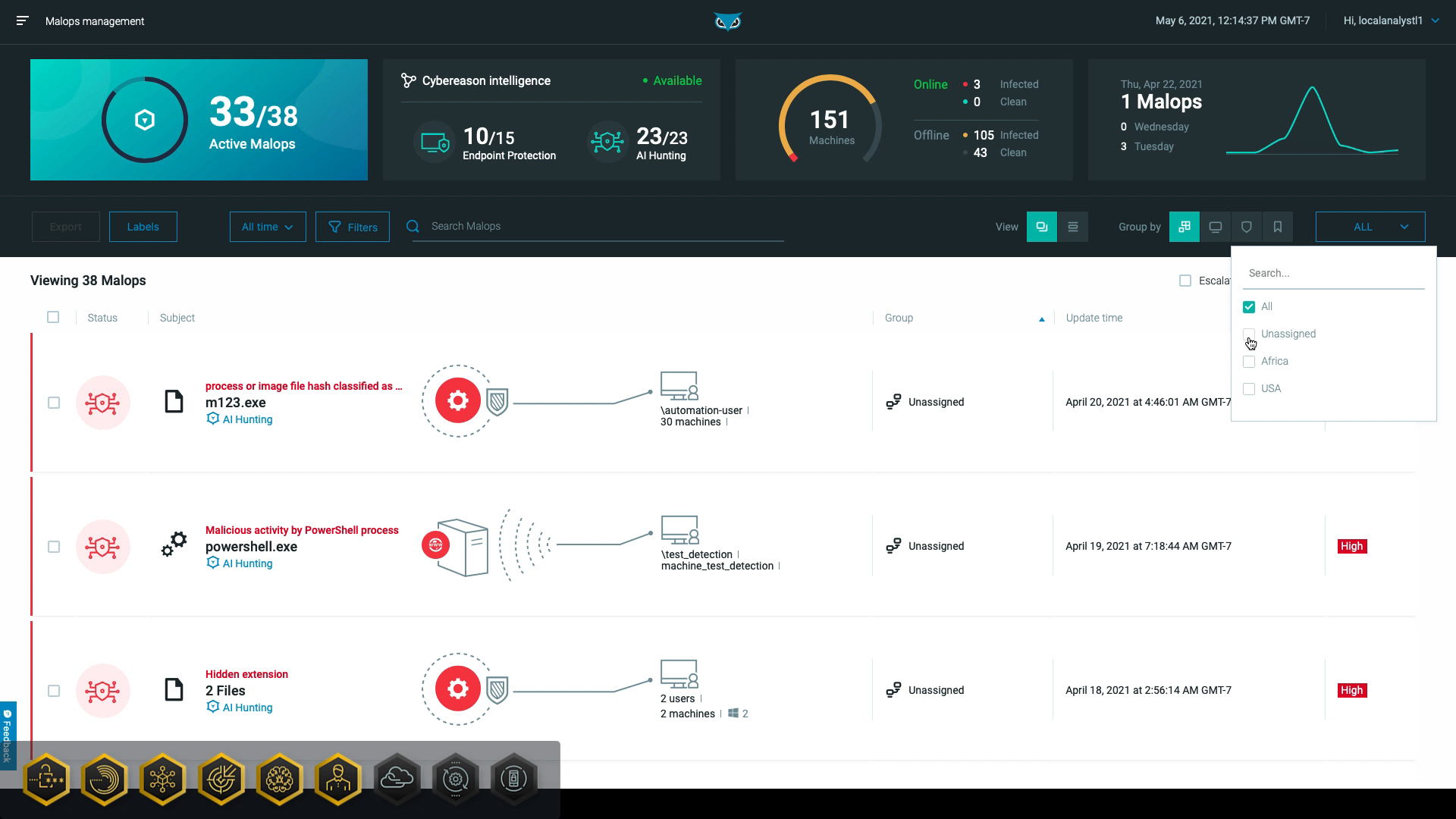
Multi-tenancy also gives higher-level administrators the ability to view overarching information across the federated organization, such as their entire MSSP practice or centralized slack.
Cybereason is dedicated to teaming with defenders to end attacks on the endpoint, across the enterprise, to everywhere the battle is taking place. Learn more about AI-Driven Cybereason XDR here or schedule a demo today to learn how your organization can benefit from an operation-centric approach to security.









