
Cybereason MDR: Fast, Efficient, Effective
The MalOp Severity Score and Extended Response enable threat detection in less than 1 minute, triage in less than 5 minutes, and remediation in less than 30 minutes. ..

Dan Verton
Attempts to develop robust enterprise incident response (IR) processes continue to be hampered by three main challenges: The increasing volume of cybersecurity incidents, a continued shortage of skilled cybersecurity talent, and a dizzying array of disconnected security tools.
The skyrocketing number of security alerts (measured in the hundreds or thousands per day) has forced many Security Operations Centers (SOCs) to ignore a significant number of alerts, creating massive gaps in visibility and detection. Making matters worse, security teams remain understaffed and lacking in experience, and are struggling to collect and analyze data from dozens of siloed security tools.
This month, Cybereason and IBM are launching a joint solution that combines Cybereason’s industry-leading Endpoint Detection and Response (EDR) with IBM’s Managed Security Services (MSS) and Managed Detection and Response (MDR) to address these challenges and significantly improve incident response delivery, triage, and remediation processes.
For most SOCs, the ability to respond to a cybersecurity incident depends on the quality of the alerts produced across their security stack. The higher the quality and context of the initial alert, the faster the team can investigate and respond.
However, most monitoring technologies often produce low-quality alert signals—it isn’t clear what’s happening, if it’s important, and what to do about it. The problem has been compounded by the fact that most organizations have tried to overcome this challenge by adding more security tools to their tech stack. The results have been predictable: out-of-control tool sprawl and continuous integration complexities that make it more difficult to collect the necessary telemetry data and get the answers needed fast enough.
Cybereason EDR leverages AI and machine learning to process the data amassed from endpoint events and identify patterns in incidents and processes that could indicate an active threat. Not only does the AI-enabled analysis help detect and contain threats before damage occurs, but it's also critical in highlighting the remediation techniques necessary to prevent future, similar intrusions.
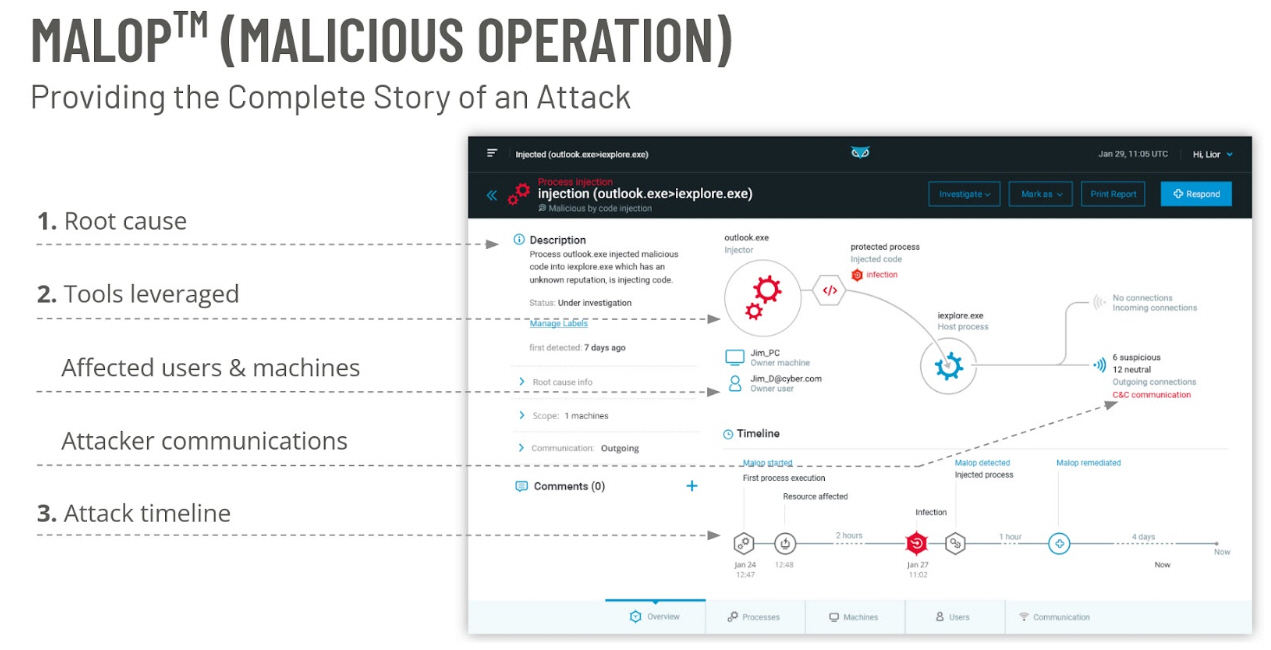
Whereas competing solutions require complex integrations with dozens or hundreds of security tools to gather necessary telemetry, Cybereason ingests and correlates all of this data using the MalOp™ (malicious operation) detection engine to identify malicious behaviors with extremely high confidence levels.
A MalOp is a collection of related suspicious activities that are highly likely to be part of a security incident. Every MalOp has a number of related suspicions and evidence, which are listed in the MalOp details. When evidence and/or suspicions reflect a confirmed pattern of malicious behavior, the Cybereason platform deems the activity a MalOp.
Cybereason EDR investigates each and every event across all endpoint devices. Behavioral analytics question these events (up to 80 million per second - more than any other EDR platform on the market) in real-time:
It is this AI-driven contextualization that gives Cybereason its predictive capability to help analysts understand the full attack story and know what the attacker is likely to do next—all while ensuring they are focused on only the most important things taking place on their network.
From an enterprise IR perspective, Cybereason centralizes response and remediation capabilities from within the platform. Each MalOp offers automated or guided one-click response actions that increase analyst effectiveness, improve accuracy, and ultimately bring a 10X improvement to mean-time-to-respond (MTTR).
Organizations that engage the Cybereason-IBM partnership get the advantage of the industry’s top-performing platform in the MITRE ATT&CK Enterprise Evaluations 2022 combined with the world’s largest enterprise security provider operating 7 follow-the-sun security operations centers (SOCs).
IBM Security Managed Detection and Response is part of the industry’s broadest portfolio of solutions that manage the full threat management lifecycle with turnkey support for leading endpoint and network security technologies, eliminating vendor lock-in.
IBM Security X-Force threat intelligence and incident response teams combine organic threat intelligence with AI-powered automation to help improve SOC productivity, reduce attack dwell time, and rapidly respond to threats 24x7. IBM Security Managed Detection and Response finds threats more consistently than static indicators of compromise (IOC) by leveraging IBM's proprietary tactics, techniques, and procedures (TTP) threat hunt library and the MITRE ATT&CK framework.
Not only does Cybereason map directly to the ATT&CK framework, but the Cybereason platform out-performed the industry in the MITRE ATT&CK Enterprise Evaluation 2022. This year’s results speak for themselves:
The evaluation took the technology from 30 participating vendors and pitted it against real-world simulations of two notorious ransomware and data destruction gangs, Wizard Spider and Sandworm. Cybereason demonstrated comprehensive and exhaustive defense against these sophisticated ransomware operations. Improving our platform through the MITRE ATT&CK evaluations directly translates to helping our customers remain undefeated against ransomware and other critical threats.
Cybereason is dedicated to teaming with Defenders to end attacks across the enterprise to anywhere the battle is taking place. Contact us today to learn how your organization can benefit from an operation-centric approach through the AI-driven Cybereason XDR Platform.
Dan Verton is Director of Content Marketing at Cybereason. Dan has 30 years of experience as a former intelligence officer and journalist. He is the 2003 first-place recipient of the Jesse H. Neal National Business Journalism Award for Best News Reporting – the nation’s highest award for tech trade journalism and is the author of the groundbreaking work, Black Ice: The Invisible Threat of Cyber-Terrorism (McGraw-Hill, 2003). He most recently served as an intelligence advisor and co-author of a nationwide TSA anti-terrorism awareness training program.
All Posts by Dan Verton
The MalOp Severity Score and Extended Response enable threat detection in less than 1 minute, triage in less than 5 minutes, and remediation in less than 30 minutes. ..

To sustain the fight against a decentralized global enemy in cyberspace, the modern SOC must engage in a change management experiment to become more agile.

The MalOp Severity Score and Extended Response enable threat detection in less than 1 minute, triage in less than 5 minutes, and remediation in less than 30 minutes. ..

To sustain the fight against a decentralized global enemy in cyberspace, the modern SOC must engage in a change management experiment to become more agile.
Get the latest research, expert insights, and security industry news.
Subscribe