When ransomware threatens to shut down your business operations, one of the most critical measures of success is the ability to detect malicious activity in real-time.
CrowdStrike users should be thinking twice right about now. After all, more than 10 percent of CrowdStrike’s detections were delayed during this year’s MITRE ATT&CK Enterprise Evaluations 2022 — the second most delayed detections of all 30 vendors tested in the MITRE evaluation.
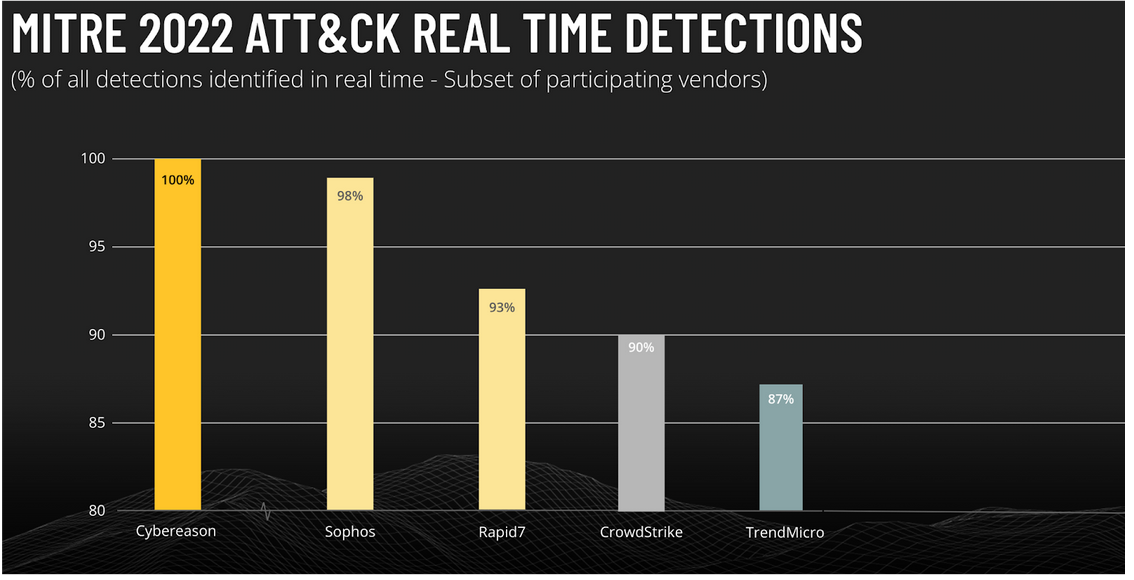
Cybereason delivered the best performance in the 4-year history of these evaluations with 100% Protection, 100% Visibility, 100% Real-Time Detections, and an industry best of 99% Analytic Coverage.
This test focused on emulating the Wizard Spider and Sandworm ransomware gangs to test the real-world performance of cyber security solutions. Cybereason demonstrated comprehensive defenses in the MITRE lab, quantifying our ability to provide absolute ransomware protection.
Solutions that miss a large portion of ransomware threats, such as CrowdStrike, are failing because they are losing the single most important contest that must be won against the ransomware gangs: The race against time.

Learn how you can leverage the MITRE ATT&CK Framework to improve your security operations
Effective ransomware protection is a race against time
Ransomware attacks occur in stages, with malicious activity often occurring weeks and even months before encryption occurs. For this reason, Cybereason approaches Ransomware attacks not as a single point-in-time event but as methodical malicious operations—or RansomOps.
When defending against these sophisticated RansomOps, the single most important factor is time. Attackers that are allowed to dwell in environments deepen their footholds and move laterally.
As they engrain themselves, they exfiltrate more and more data (to make double extortion a credible threat in the future) and stage as many machines as possible for future encryption (so they can ensure devastating business interruptions). This means effective ransomware protection must be able to uncover RansomOps, respond, and recover from ransomware threats faster than ever before.
Stopping attackers in their tracks as early in their malicious operation as possible is the most effective way to ensure that the attackers will not be able to extort organizations' desire to prevent the publication of their data or demand payment to restore the operation of critical systems.
Cybereason’s anti-ransomware approach identifies and stops ransomware activity so early in the malicious operation—and long before wide-scale encryption can occur—that the capability is referred to as Cybereason Predictive Ransomware Protection.
Many competitors, including CrowdStrike, do not have this same maniacal focus to reverse the adversary's advantage by winning this race against time:
Uncover RansomOps faster
Long before encryption occurs, ransomware attackers are consistently repeating two processes over and over again across the target environment: lateral movement and data exfiltration.
In most cases, attackers begin with a small foothold (i.e., a single machine) and must capture other machines through lateral movement to continue propagating the ransomware operation. This process of spreading throughout the environment and stealing data will continue until the ransomware attacker crosses two key thresholds:
- Enough machines have been captured to materially disrupt business operations
- Sufficient critical data has been removed from these machines to enable a double extortion scheme
Once these two dimensions are satisfied, the attackers are then ready to detonate encryption and render all the machines under their control in the environment useless.
This is when many solutions, such as CrowdStrike, spring to action and start sounding alarms. This is far too late. By now, the attackers already have your critical data, and if the prevention stack wasn’t working effectively, they’ve already brought your organization to its knees.
By comparison, Cybereason uncovers these ransomware operations in the initial weeks and months of the attack while the attacker is focused on lateral movement and data exfiltration; long before the encryption occurs. Cybereason can see this less obvious malicious activity because the Cybereason platform is designed to collect and analyze 100% of event data in real time, processing more than 23 trillion security-related events per week.
To ensure the performance of their rigid solution and to keep costs down, Crowdstrike is forced to filter out critical event telemetry—and while they try to pawn off this deficit as a "feature" by calling it Smart Filtering, eliminating critical telemetry undermines their ability to detect complex RansomOps attacks at the earliest stages.
Cybereason’s unparalleled data processing ability at scale is why Cybereason remains undefeated against ransomware.
Respond and recover from ransomware threats faster
It’s rare (at least when you’re using Cybereason) for encryption to occur; in fact, a Cybereason customer has never had their business operations materially disrupted by ransomware encryption. However, the precursor events leading up to encryption (such as lateral movement and data exfiltration) must be responded to quickly to ensure the ransomware operation is stopped in its earliest stages.
A good way to determine the efficiency of a vendor’s technology is to examine their marketing materials for their Managed Detection and Response (MDR) service. This telltale exposes how well the vendor expects their technology to work when they have their in-house experts managing the solution.
CrowdStrike asserts that a time to initial detection of 1 minute, 10 minutes to investigate, and 60 minutes to remediate is the penultimate achievement that a security organization should strive for. This objective of 1/10/60 is also what CrowdStrike aims to achieve for their MDR service.
That’s just not good enough. Cybereason MDR service provides initial detection in less than 1 minute, a time to investigate of 5 minutes, and a time to remediation of 30 minutes—1/5/30.
How is it that CrowdStrike’s MDR service objectives for investigation and remediation take twice as long as Cybereason’s? CrowdStrike relies heavily on manual human labor to operate its technology and as a result, their mean-time-to-respond enables attackers to spread through environments. As a result, their mean-time-to-respond enables attackers to spread through environments.
Even when the creators of the CrowdStrike technology closely manage the tool, their time to remediation is still too slow to win the race against time and beat the ransomware adversaries. Cybereason’s superior technology can handle many aspects of the investigation and the remediation independently of human intervention, significantly speeding up time to recovery—and, therefore, our customers’ ability to defeat ransomware.
Cybereason is undefeated against ransomware
When it comes to defending against ransomware operations (RansomOps), the most critical factor is time. Uncover RansomOps faster; Respond and recover from RansomOps faster; Be undefeated in the fight against ransomware.
Cybereason is the XDR company, partnering with Defenders to end attacks at the endpoint, in the cloud, and across the entire enterprise ecosystem. Only the AI-driven Cybereason Defense Platform provides planetary-scale data ingestion, operation-centric MalOp™ detection, and predictive response that is undefeated against modern ransomware and advanced attack techniques. Cybereason is a privately held international company headquartered in Boston with customers in more than 40 countries.







