
Beware of the Messengers, Exploiting ActiveMQ Vulnerability
In this Threat Analysis Report, Cybereason Security Services examines an incident on a Linux server, which saw malicious shell (bash) executions from a Java process running Apache ActiveMQ.

Cybereason Security Services Team
Cybereason issues Threat Alerts to inform customers of emerging impacting threats, including critical vulnerabilities. Cybereason Threat Alerts summarize these threats and provide practical recommendations for protecting against them.
Cybereason Security Services is investigating incidents that involve the abuse of AnyDesk code signing certificates.
AnyDesk, one of the world’s leading providers of Remote Management and Monitoring (RMM) software, released a public statement on February 2nd 2024, confirming they had identified a compromise of production systems. As such, they initiated incident response and as part of remediation efforts, had revoked all of their security-related certificates and issued new ones.
Following the initial public statement made by AnyDesk, media reports have suggested that attackers were able to steal proprietary source code and AnyDesk’s private code signing certificate during the attack. There is no indication of a supply chain incident at the time of this article’s publication.
Code signing abuse involves leveraging the trust associated with a code signing certificate to distribute malware by deceiving users into believing that malicious code has originated from a trusted source. Indeed, this is a common practice to help malware evade detection that solely rely on digital signature to identify trusted software. According to data shared by VirusTotal, between 2021 and 2022, amongst the million signed malicious samples uploaded to the platform, 87% of them were holding a valid signature when submitted.
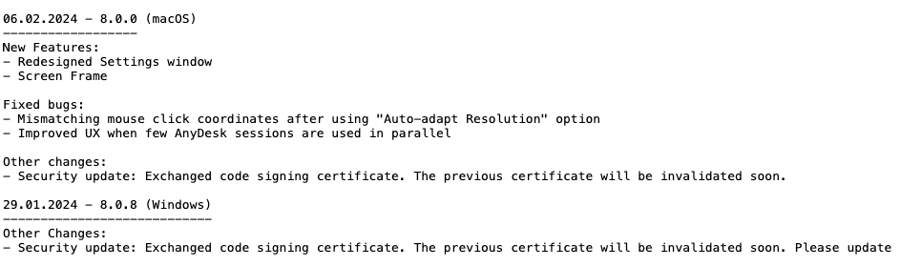
Extract From AnyDesk Changelog.txt Showing The Security Update And Code Signing Certificate Exchange
In this case malware could be distributed, purporting to be a legitimate AnyDesk application.
Open source intelligence indicates that the stolen AnyDesk code signing certificate is already being abused to digitally sign malware.
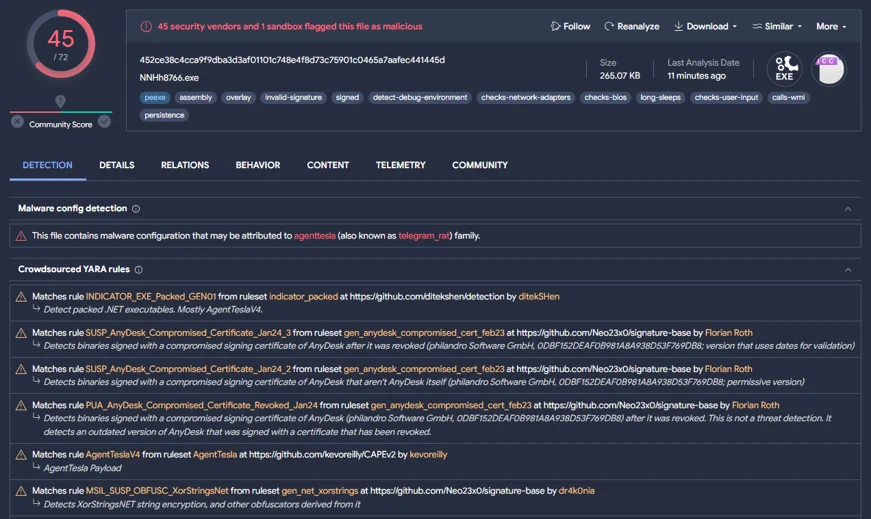
Virustotal Sample Appearing To Show Information Stealing Malware Signed With A Compromised AnyDesk Signing Certificate
Cybereason Security Services teams are proactively hunting for signs of AnyDesk certificate abuse across customer environments.
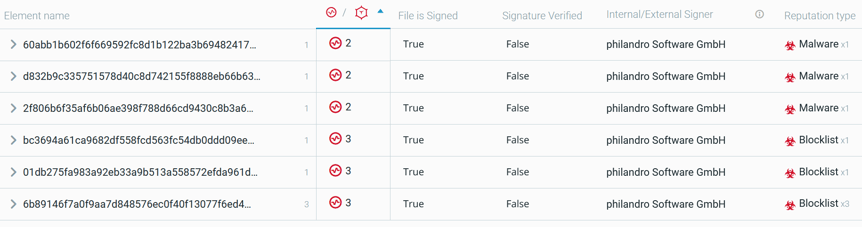
Malware Signed With A Compromised AnyDesk Signing Certificate
AnyDesk has prompted their customers to update their software with the newest version published on January 29th 2024, containing the new code signing certificate. They have also forced password reset on the AnyDesk portal due to indication of stolen credentials.
Below are the characteristics of compromised AnyDesk version:
Threat actors are using the stolen certificate to sign malicious binaries. Over 500 samples of Agent Tesla - signed with the compromised certificate - have been publicly uploaded to VirusTotal since June 2022.
So far, Cybereason has primarily observed Trojans being signed with this certificate. A trojan is a piece of malware that misleads users of its true intent by disguising itself as a standard program, that can then be used to download and execute additional malware as well as exfiltrate data from the network of its victim. In these particular cases, they appeared to be linked to the threat Agent Tesla, a Remote Access Trojan (RAT) .
At this point, there is no clear evidence that these binaries were signed following AnyDesk’s breach.
The Cybereason Defense Platform detects and prevents the execution of malware signed with the leaked certificate through the Cybereason Next Generation Antivirus (NGAV) module - Signature-based Antimalware.
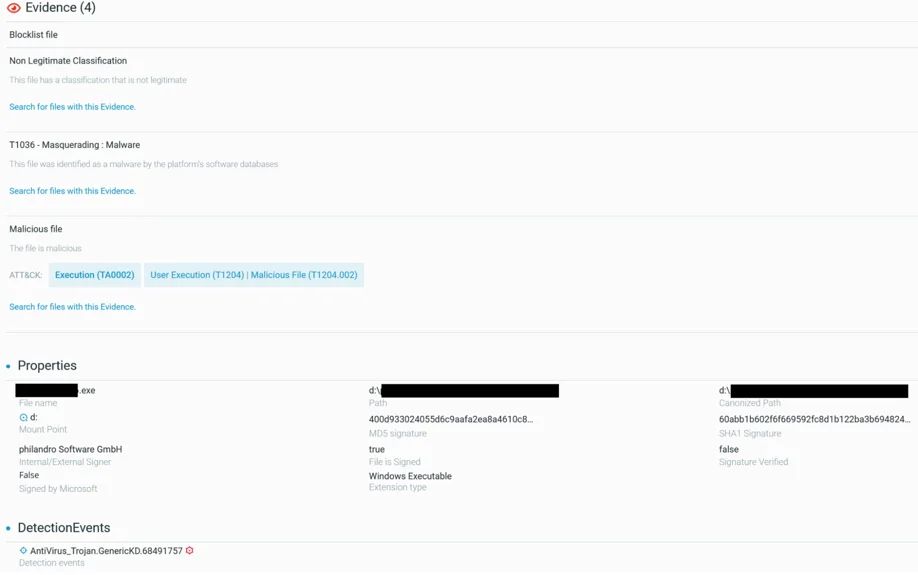
File Element View Showing Evidence Mapped To MITRE ATT&CK And Detection Signature For The Anti-Malware Engine On A Signed Malware File
. In addition, Cybereason recommends the following actions:
Cybereason is dedicated to teaming with Defenders to end cyber attacks from endpoints to the enterprise to everywhere. Learn more about Cybereason XDR powered by Google Chronicle, check out our Extended Detection and Response (XDR) Toolkit, or schedule a demo today to learn how your organization can benefit from an operation-centric approach to security.
Elena Odier, Security Operations Analyst at Cybereason
 Elena Odier is a GSOC Analyst with the Cybereason Global SOC team. She is involved in MalOp Investigation and Threat Hunting.
Elena Odier is a GSOC Analyst with the Cybereason Global SOC team. She is involved in MalOp Investigation and Threat Hunting.
Previously, Elena worked in incident response at ANSSI (French National Agency for the Security of Information Systems).
Darren Singh, Security Operations Analyst at Cybereason
 Darren is a Senior GSOC Analyst with the Cybereason Global SOC Team. He is involved in Malware Analysis, Threat Hunting and Extended Detection and Response (XDR). Darren holds a Bachelor of Engineering in Digital Security, Forensics and Ethical Hacking with first class honors.
Darren is a Senior GSOC Analyst with the Cybereason Global SOC Team. He is involved in Malware Analysis, Threat Hunting and Extended Detection and Response (XDR). Darren holds a Bachelor of Engineering in Digital Security, Forensics and Ethical Hacking with first class honors.
He has experience working in information security teams in public and private sector organizations including the financial services industry.


In this Threat Analysis Report, Cybereason Security Services examines an incident on a Linux server, which saw malicious shell (bash) executions from a Java process running Apache ActiveMQ.

React2Shell vulnerability, tracked as CVE-2025-55182, recently discovered in React’s Server Components, could allow for pre-authentication remote code execution.

In this Threat Analysis Report, Cybereason Security Services examines an incident on a Linux server, which saw malicious shell (bash) executions from a Java process running Apache ActiveMQ.

React2Shell vulnerability, tracked as CVE-2025-55182, recently discovered in React’s Server Components, could allow for pre-authentication remote code execution.
Get the latest research, expert insights, and security industry news.
Subscribe