Threat
Hunting
The Cybereason Defense Platform empowers defenders to proactively hunt out the adversary and uncover even the most complex attacks.
WHY CYBEREASON THREAT HUNTING?
Uncover Unknown Attacks
Search for evidence and suspicions tied with MalOps to identify unknown attacks and minimize damage or business disruption.
Level Up Your Analyst Skills
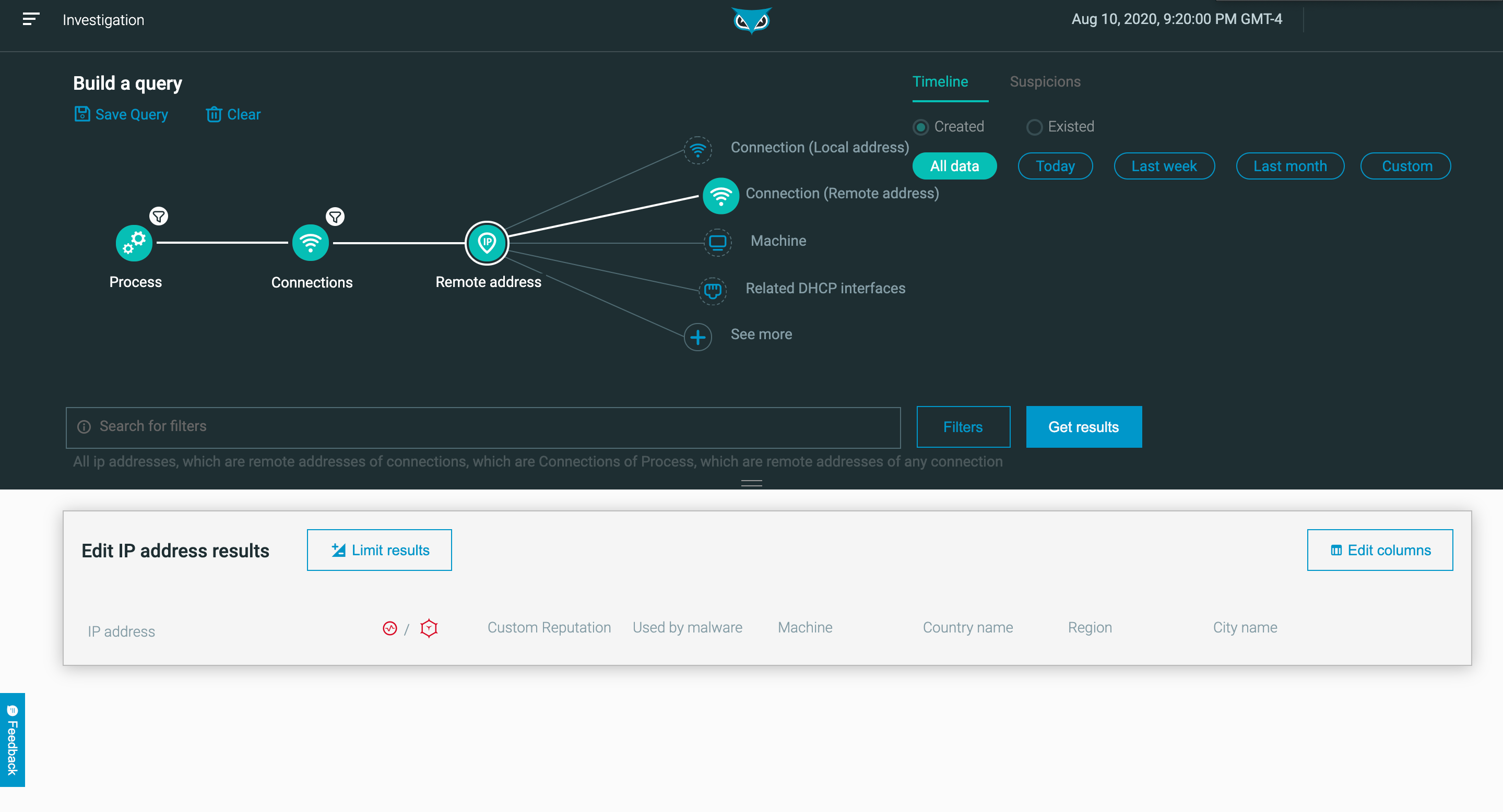
Easily pivot between events and conduct investigations without crafting complex queries. As a result, Level 1 and 2 analysts can perform with Level 3 proficiency.
Evolve Your Threat Hunting
Defenders can leverage custom detection rules and define new logic for triggering MalOps based on lessons learned from successful hunts.
THREAT HUNTING Capabilities
Proactive Threat Defense
Threat hunting allows security teams to identify attacks sooner and minimize the likelihood of business disruption. The Cybereason Defense Platform is the nexus of threat intelligence and contextual correlations required for in-depth threat hunting to expose the most complex attacks and ensure a proactive security posture.
Research-Driven Insight
The Cybereason Nocturnus Team constantly evaluates new methodologies to uncover new Indicators of Compromise (IOCs) and key Indicators of Behavior (IOBs), the more subtle signs of an attack derived from across the whole of your network. Cybereason is committed to providing superior threat hunting capabilities to empower defenders to stay one step ahead of attackers and reverse the adversary advantage.
Industry Validation
See why Cybereason is the solution of choice for future-ready prevention, detection and response.
Customer Highlight: Olist
With over 1,100 employees and 2,100 endpoints, Olist needed to gain visibility into their attack surface, and staff to investigate and respond to incidents. Learn how a combination of the Cybereason Defense Platform and MDR services increased visibility and led to security performance improvements.
Read NowHighest MITRE ATT&CK Score in History
Cybereason received the highest scores in history from MITRE ATT&CK Evaluations, scoring 100% in prevention tests, 100% in real-time detection coverage, and was the only vendor to deliver 100% visibility across all operating systems.
Read the Report