Evolving threats. New responses.
How organizations are adapting to a new breed of cybersecurity threats in a surprising way.
Read moreNew
State of the art endpoint security to prevent, detect, and respond to the most sophisticated attacks in private, offline, and air-gapped networks.
Proven Technology
Privacy & Regulation
Transparent Pricing
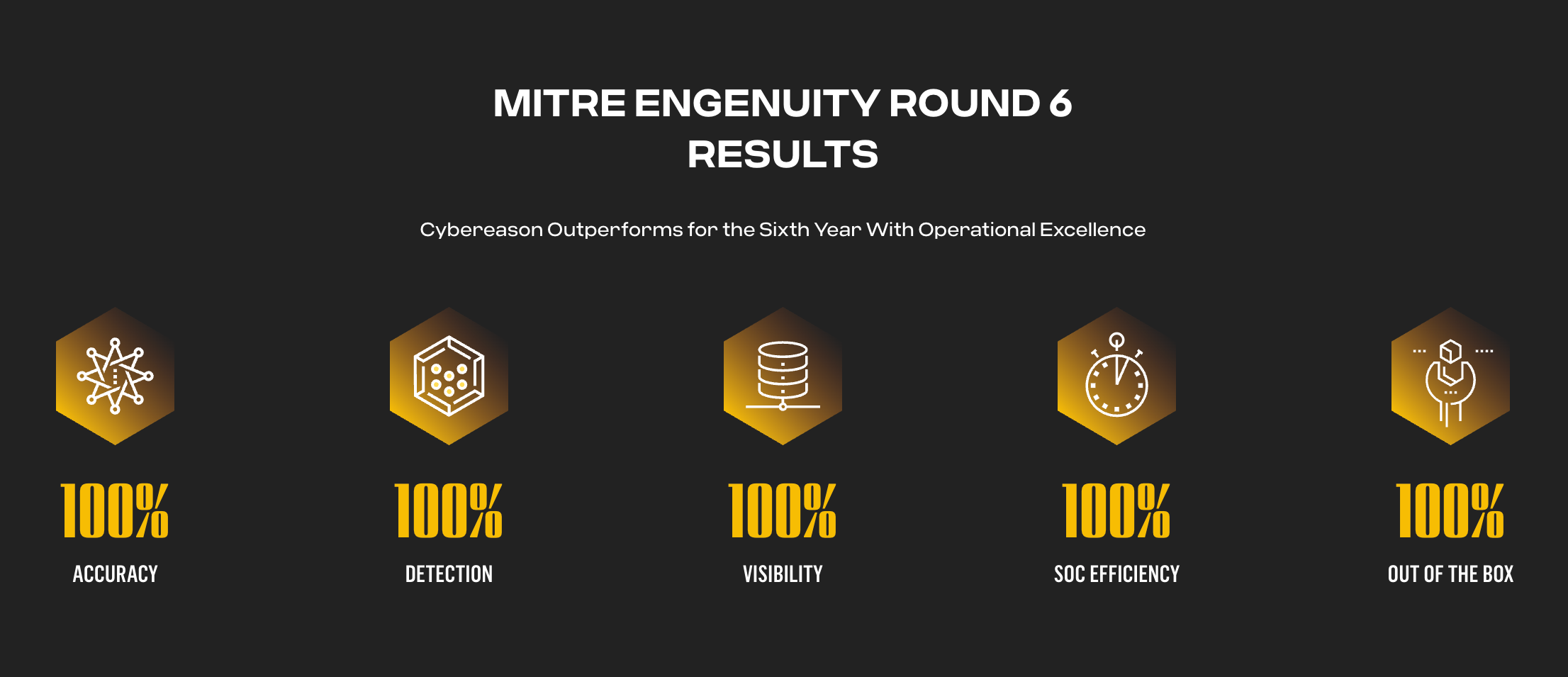
As top performer in the latest MITRE ATT&CK Evaluations, our customers know Cybereason On-Prem provides the best defense for hard to protect, off-line and private networks.

Cybereason On-Prem makes it easier to meet increasing pressure from industry standard agencies and regulators restricting the use of public cloud whilst providing better protection against the latest threat actors and improving security operational efficiencies.

Transparent and flexible pricing to meet your organization's unique needs. With one, three, and five year pricing packages, Cybereason On-Prem can be deployed within networks of any size.
On-Prem vs. Cloud
Regulatory Compliance
Architectural Use-Cases
On-Prem vs. Cloud
Regulatory Compliance
Architectural Use-Cases
Evolving threats. New responses.
How organizations are adapting to a new breed of cybersecurity threats in a surprising way.
Read more
Ensuring safety in today’s regulatory climate
How critical industries are addressing regulatory requirements.
Read more
Protection without compromise for critical systems
Industry needs state-of-the-art solutions for maximum uptime.
Read more

1.
2.
3.
Small Package
Up to 1,000 Endpoint
$150,000
Billed annually for 1 year
Medium Package
Up to 5,000 Endpoint
$690,000
Billed annually for 1 year
Large Package
Up to 10,000 Endpoint
$1,300,000
Billed annually for 1 year
Need more coverage?
Speak to a Cybereason expert.
Need more coverage?
Speak to a Cybereason expert.
Small Package
Up to 1,000 Endpoints
$99,000
Billed annually for 3 years
Medium Package
Up to 5,000 Endpoints
$462,500
Billed annually for 3 years
Large Package
Up to 10,000 Endpoints
$855,000
Billed annually for 3 years
Need more coverage?
Speak to a Cybereason expert.
Need more coverage?
Speak to a Cybereason expert.
Small Package
Up to 1,000 Endpoints
$88,500
Billed annually for 5 years
Medium Package
Up to 5,000 Endpoints
$408,000
Billed annually for 5 years
Large Package
Up to 10,000 Endpoints
$755,000
Billed annually for 5 years
Need more coverage?
Speak to a Cybereason expert.
Need more coverage?
Speak to a Cybereason expert.
Small Package
Up to 1,000 Endpoint
$90,000
Billed annually for 1 year
Medium Package
Up to 5,000 Endpoint
$450,000
Billed annually for 1 year
Large Package
Up to 10,000 Endpoint
$900,000
Billed annually for 1 year
Need more coverage?
Speak to a Cybereason expert.
Need more coverage?
Speak to a Cybereason expert.
Small Package
Up to 1,000 Endpoint
$81,000
Billed annually for 3 years
Medium Package
Up to 5,000 Endpoint
$382,500
Billed annually for 3 years
Large Package
Up to 10,000 Endpoint
$720,000
Billed annually for 3 years
Need more coverage?
Speak to a Cybereason expert.
Need more coverage?
Speak to a Cybereason expert.
Small Package
Up to 1,000 Endpoint
$76,500
Billed annually for 5years
Medium Package
Up to 5,000 Endpoint
$360,000
Billed annually for 5years
Large Package
Up to 10,000 Endpoint
$675,000
Billed annually for 5years
Need more coverage?
Speak to a Cybereason expert.
Need more coverage?
Speak to a Cybereason expert.
Cybereason Appliance-based Solution
Cybereason On-Prem is available combined with a purpose-built appliance through strategic hardware partners. The Cybereason On-Prem appliance based solution includes Cybereason On-Prem software pre-provisioned and supports the latest workstations, servers, or legacy systems. Your appliances can be deployed anywhere - off-site private data centers or on-premises server rooms - you choose.
Cybereason On-Prem Virtual Appliance
The Cybereason On-Prem virtual solution can be installed anywhere, and supports the latest workstations, servers, or legacy systems. Take advantage of existing on-premises and datacenter hardware, or deploy in private cloud infrastructure - you choose.
Get in touch with a Cybereason expert
First, tell us about you
← Choose another plan
Pricing Estimate
Service Type
On-PremApplication
Plan Size
Term Length
Annual Cost
Total Cost
By clicking the submit button, you are considered to have agreed to Cybereason’s Privacy Notice
Watch an attack simulation
See the many opportunities an attacker has to advance the operation, and the ways a defender can break the kill chain and end the attack before crown jewels are compromised.
Watch Now

It's not surprising that in the last couple of months the requests of “are you EU Network Information Security Directive (NIS) v2 compliant?” are starting to come in. What would seem like a simple GRC yes no question is in fact complex.
Read More
How do we secure Private Infrastructure? By providing virtualized containers, allowing customers to re-use their own hardware and making it easier to add in new capabilities as the cyber security world evolves.
Read More
Many of our customers choose Cybereason On-Prem to simplify their data and critical infrastructure compliance with the flexibility to deploy in on-prem server rooms, private data centers or private cloud environments.
Read MoreINFOGRAPHIC
Read this infographic to better understand how Cybereason consolidates alerts, generates high-fidelity detections and implements the right amount of automation to make teams maximally effective.
Download The MalOp™ InfographicDATA SHEET
Cybereason On-Prem brings state of the art endpoint security to prevent, detect, and respond to even the most sophisticated attacks in private, offline, and air-gapped networks.
Read the Data Sheet