WHY COMPANIES CHOOSE CYBEREASON

NEVER BE HELD TO RANSOM

Undefeated in the fight against ransomware
Cybereason deception technology and lightning-fast threat analysis has been protecting customers from every major attack, making us undefeated in the fight against ransomware.
Passable protection isn't enough
Microsoft security offerings often leave customers susceptible to data encryption and double extortion from ransomware attacks. Exploitation of Microsoft products are responsible for more than half of all ransomware attacks.
NEVER GO IT ALONE
Elite experts and around the clock protection
Managed services provide a needed reprieve for overburdened security teams or organizations that don't have resources. Cybereason has the industry-renowned experts necessary to provide exceptional services including MDR and IR.
Lack the expertise for managed services
If you go with Microsoft, you’re banking on their ability to build and scale a brand new MDR service, and, you’ll need another vendor to provide IR services in the event that you need support recovering from an incident.
STILL IN PRODUCTION BECAUSE IT'S CRITICAL
Broad legacy systems coverage and deployment options
Critical legacy systems are unavoidable. On-premises systems are a reality for modern organizations. Cybereason includes coverage for legacy systems at no additional charge and deployment options from air-gapped to the cloud.
Expensive or impossible to secure datacenter and legacy systems
Microsoft is forcing server workloads to Azure and demands the latest Windows version on endpoints. Server security is an add-on license, legacy systems are unsupported or impose an upcharge, and on-premises deployment is impossible.
CONSOLE FATIGUE LEADS TO LOWER PRODUCTIVITY
Reduce time to detect and respond by 93%
Increase efficiency and productivity with simplified platform management and accelerated triage. Companies that switched to Cybereason reduced management tasks by 75%, and in MITRE ATT&CK tests, we detected 98% of threats with no config changes, and had zero delays.
Cumbersome consoles waste your time
Correlating the details of an attack is manual and requires switching between multiple consoles. Microsoft requires constant tuning; in MITRE ATT&CK tests configuration changes were required for detection in 12% of the tests.
NOISE MEANS MISSED THREATS
An operation-centric approach leaves attackers nowhere to hide
The Cybereason operation-centric approach is enriched with intuitive historical threat hunting to form a holistic view of an attack; cutting the noise, providing actionable insights, and uncovering today’s most sophisticated attackers.
Microsoft misses subtle signals and quiet malicious activity
Microsoft requires manual correlation of events across multiple consoles to form the complete picture of an attack. Attackers hide in the noise created by the deluge of unactionable alerts resulting from this piecemeal approach.
EFFECTIVE SECURITY REQUIRES FOCUS
Dedicated to you, The Defenders
Reversing the advantage that adversaries have in cyber security is the sole focus of Cybereason. Led by the world renowned research organization Nocturnus, every aspect of the company drives to the future where the defenders rein.
Too big to succeed
A surge of adversaries running rampant through vulnerabilities native to the Microsoft ecosystem is a direct result of a lack of focus, with countless attacks attributed to Microsoft’s laissez-faire attitude towards security.
NEVER BE HELD TO RANSOM
Undefeated in the fight against ransomware
Cybereason deception technology and lightning-fast threat analysis has been protecting customers from every major attack, making us undefeated in the fight against ransomware.
Passable protection isn't enough
Microsoft security offerings often leave customers susceptible to data encryption and double extortion from ransomware attacks. Exploitation of Microsoft products are responsible for more than half of all ransomware attacks.
NEVER GO IT ALONE
Elite experts and around the clock protection
Managed services provide a needed reprieve for overburdened security teams or organizations that don't have resources. Cybereason has the industry-renowned experts necessary to provide exceptional services including MDR and IR.
Lack the expertise for managed services
If you go with Microsoft, you’re banking on their ability to build and scale a brand new MDR service, and, you’ll need another vendor to provide IR services in the event that you need support recovering from an incident.
STILL IN PRODUCTION BECAUSE IT'S CRITICAL
Broad legacy systems coverage and deployment options
Critical legacy systems are unavoidable. On-premises systems are a reality for modern organizations. Cybereason includes coverage for legacy systems at no additional charge and deployment options from air-gapped to the cloud.
Expensive or impossible to secure datacenter and legacy systems
Microsoft is forcing server workloads to Azure and demands the latest Windows version on endpoints. Server security is an add-on license, legacy systems are unsupported or impose an upcharge, and on-premises deployment is impossible.
CONSOLE FATIGUE LEADS TO LOWER PRODUCTIVITY
Reduce time to detect and respond by 93%
Increase efficiency and productivity with simplified platform management and accelerated triage. Companies that switched to Cybereason reduced management tasks by 75%, and in MITRE ATT&CK tests, we detected 98% of threats with no config changes, and had zero delays.
Cumbersome consoles waste your time
Correlating the details of an attack is manual and requires switching between multiple consoles. Microsoft requires constant tuning; in MITRE ATT&CK tests configuration changes were required for detection in 12% of the tests.
NOISE MEANS MISSED THREATS
An operation-centric approach leaves attackers nowhere to hide
The Cybereason operation-centric approach is enriched with intuitive historical threat hunting to form a holistic view of an attack; cutting the noise, providing actionable insights, and uncovering today’s most sophisticated attackers.
Microsoft misses subtle signals and quiet malicious activity
Microsoft requires manual correlation of events across multiple consoles to form the complete picture of an attack. Attackers hide in the noise created by the deluge of unactionable alerts resulting from this piecemeal approach.
EFFECTIVE SECURITY REQUIRES FOCUS
Dedicated to you, The Defenders
Reversing the advantage that adversaries have in cyber security is the sole focus of Cybereason. Led by the world renowned research organization Nocturnus, every aspect of the company drives to the future where the defenders rein.
Too big to succeed
A surge of adversaries running rampant through vulnerabilities native to the Microsoft ecosystem is a direct result of a lack of focus, with countless attacks attributed to Microsoft’s laissez-faire attitude towards security.
THE MALOP™ DIFFERENCE
Cybereason is operation-centric instead of alert-centric. We instantly deliver fully contextualized and correlated insights into any MalOp, detailing the full attack story from root cause to impacted users and devices, significantly reducing investigation/remediation periods.
What Industry Analysts Are Saying

Highest MITRE ATT&CK Score in History
Download the results summary to see why Cybereason is the only security vendor that provides unparalleled attack protection by combining 9 independent prevention layers, ensuring that your business achieves its goals, and bad actors don’t.
Read the Results
Customer Highlight: Olist
With over 1,100 employees and 2,100 endpoints, Olist needed to gain visibility into their attack surface, and staff to investigate and respond to incidents. Learn how a combination of the Cybereason Defense Platform and MDR services increased visibility and led to security performance improvements.
Read Now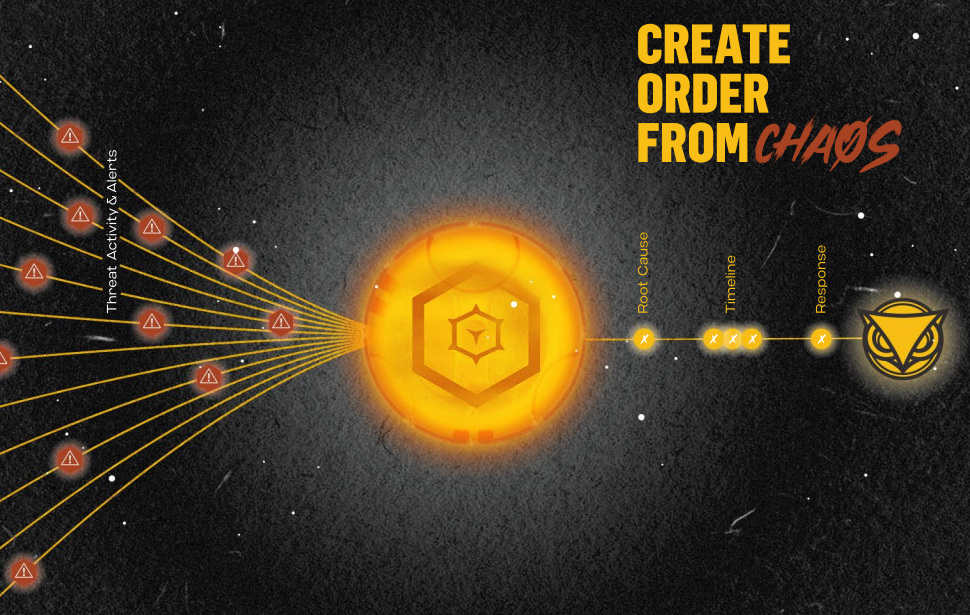
The MalOp Explained
Cybereason makes sense of complex data relationships and behaviors to stitch together the separate components of an attack, including all users, devices, identities, and network connections into an operation-centric view we call The MalOp™.
Learn MoreThe Best Defend the Best
Cybereason vs. the Competition
Defenders choose Cybereason solutions time and time again. Check out how we stack up against some of the other tools out there today.
SentinelOne's Protection Holds You Back
SentinelOne’s ransomware “rollback” approach relies on remediation after your data has been stolen and the damage or ransomware is done.
Cybereason vs. CrowdStrike
Automatically end malicious operations using artificial intelligence versus chasing alerts that require manual triage.







