With over 1,100 employees and 2,100 endpoints, Olist needed to gain visibility into their attack surface, and staff to investigate and respond to incidents. Learn how a combination of the Cybereason Defense Platform and MDR services increased visibility and led to security performance improvements.
Read NowThreat
Intelligence
Evolve faster than the adversary with actionable threat intelligence to detect and end complex threats.
WHY CYBEREASON THREAT INTELLIGENCE?
World-Class Research
Benefit from the unparalleled expertise of our elite Nocturnus Security Research Team, who provide best-in-class intelligence and 24 x 7 support.
Real-Time Intelligence
Proprietary and third-party threat intelligence is continuously aggregated and infused into the Cybereason Defense Platform in real-time.
Actionable Intel To End Attacks
Move beyond simple alerts with Indicators of Compromise (IOCs) and Behavior (IOBs) that correlate all attack activity across your network.
Key Capabilities
RESEARCH-DRIVEN INSIGHT
The Cybereason Nocturnus Team has brought the world’s brightest threat intelligence analysts and malware reverse engineers who work around the clock from our Global SOCs in the U.S., Israel and Japan to uncover emerging threats and ensure the delivery of actionable threat intelligence to defend the endpoint, the enterprise, and everywhere the battle is being waged by defenders.
Cybereason is Dedicated to the Defenders
Learn more about Cybereason’s commitment to reversing the adversary advantage by empowering defenders with the ingenuity and technology to end cyber attacks.
Related Resources
Cybereason received the highest scores in history from MITRE ATT&CK Evaluations, scoring 100% in prevention tests, 100% in real-time detection coverage, and was the only vendor to deliver 100% visibility across all operating systems.
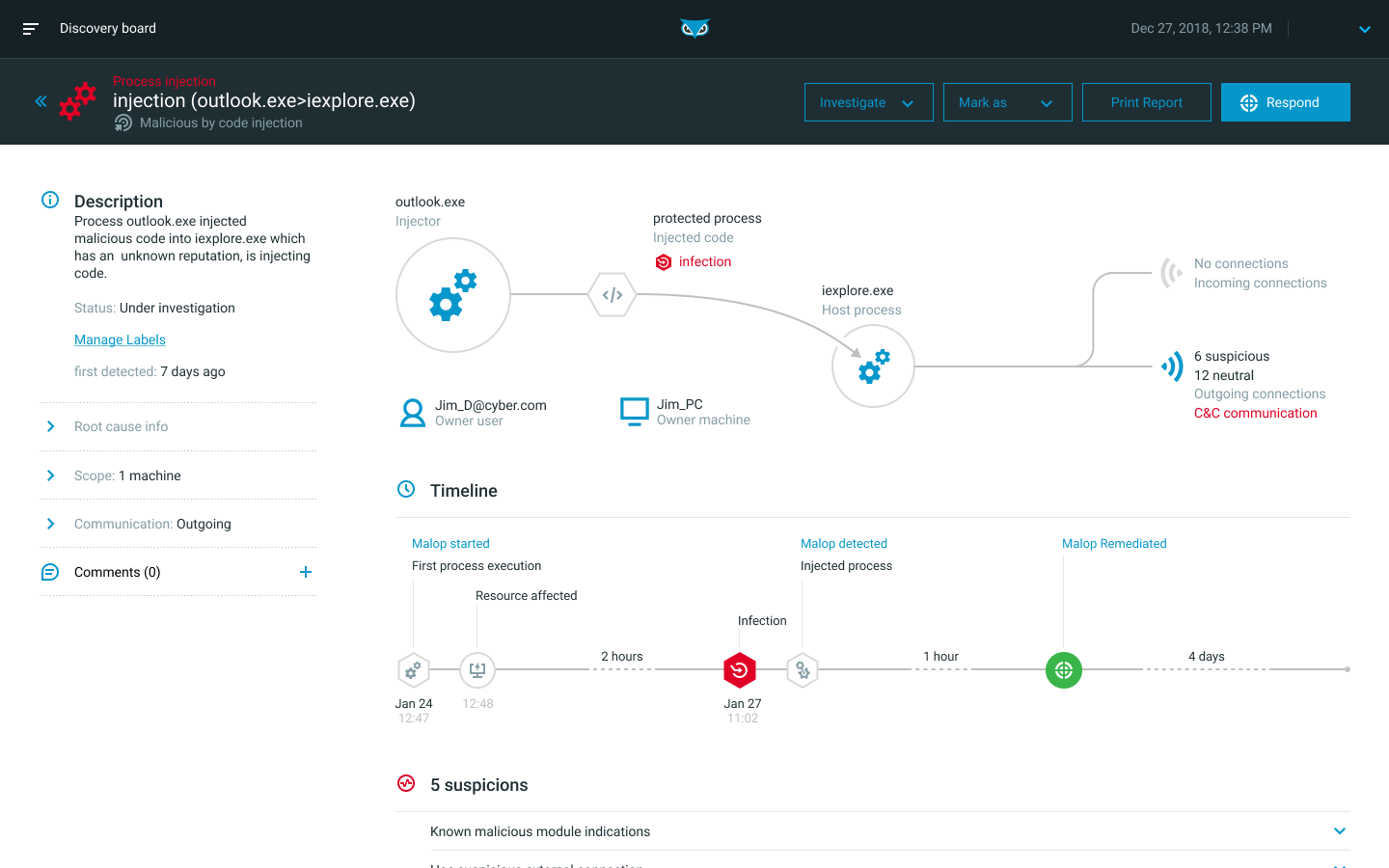
Read the ResultsCybereason makes sense of complex data relationships and behaviors to stitch together the separate components of an attack, including all users, devices, identities, and network connections into an operation-centric view we call The MalOp™.
Learn More








