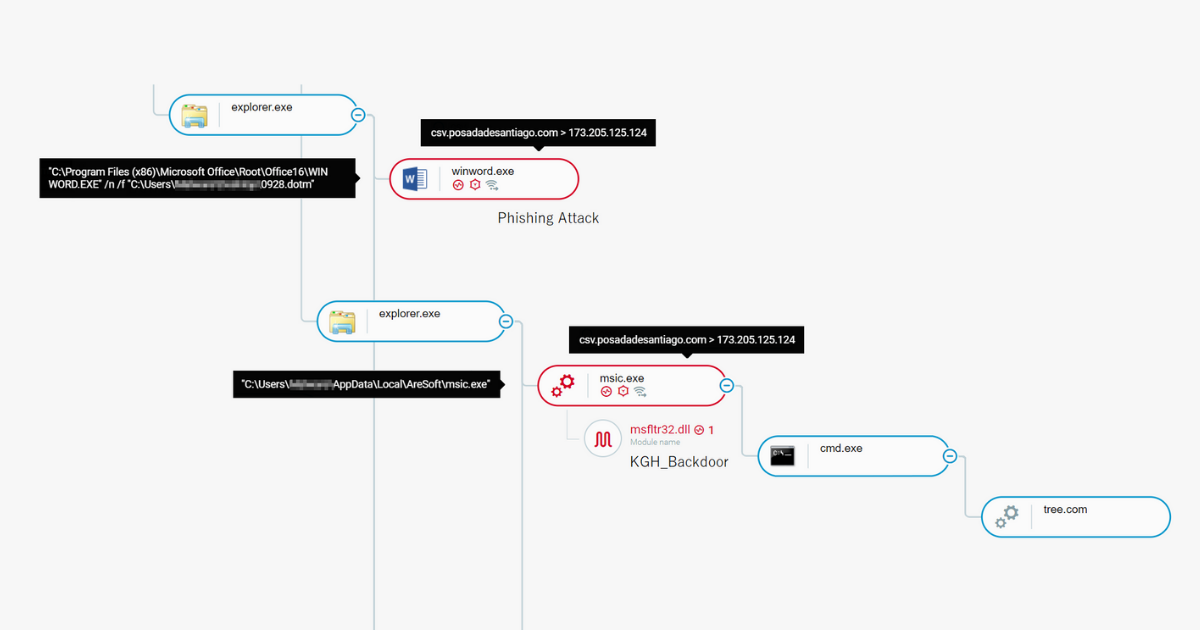
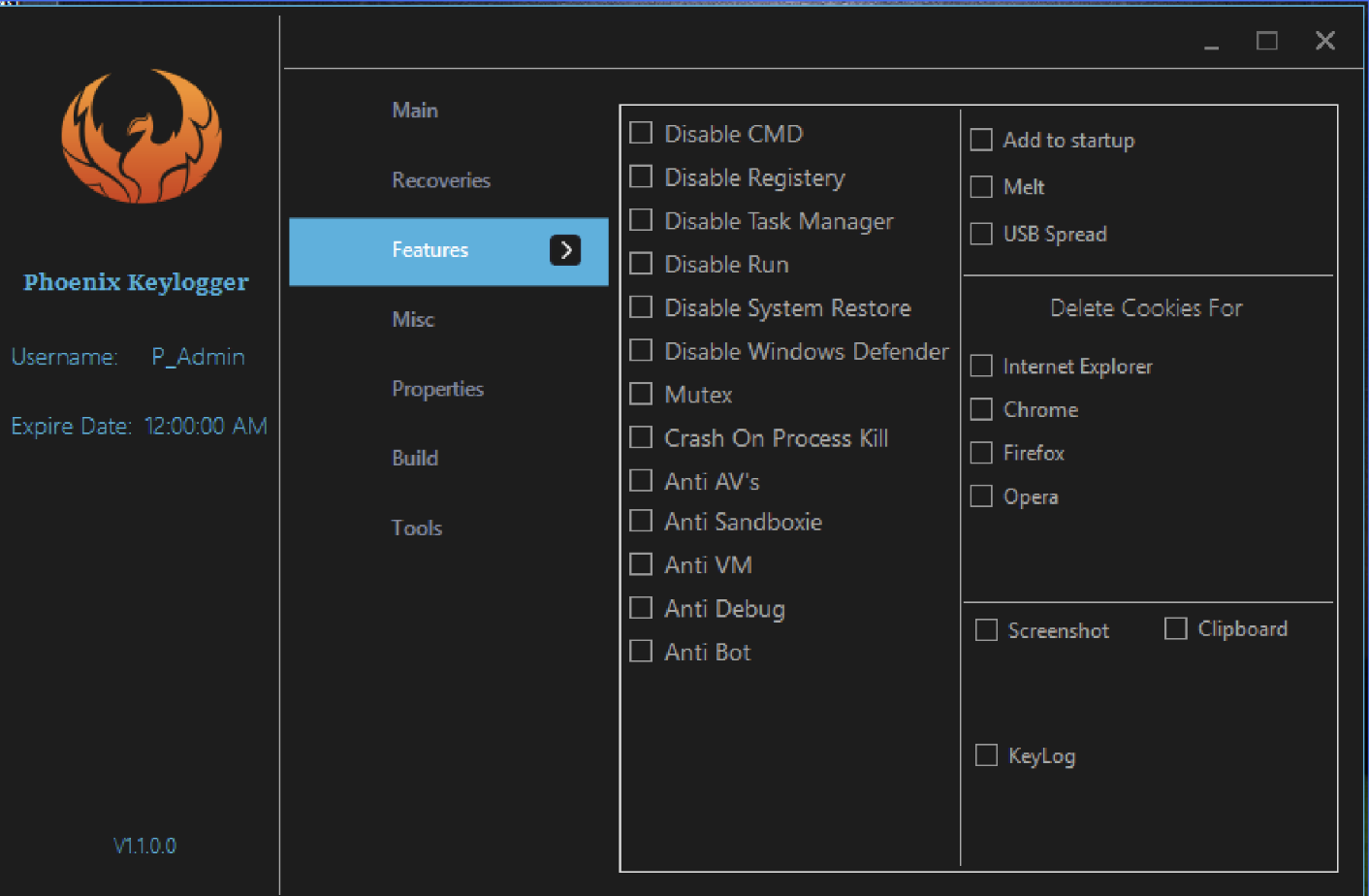
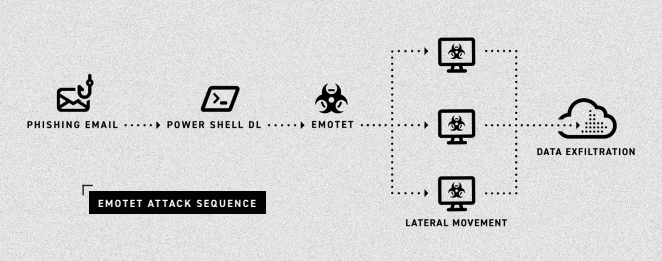
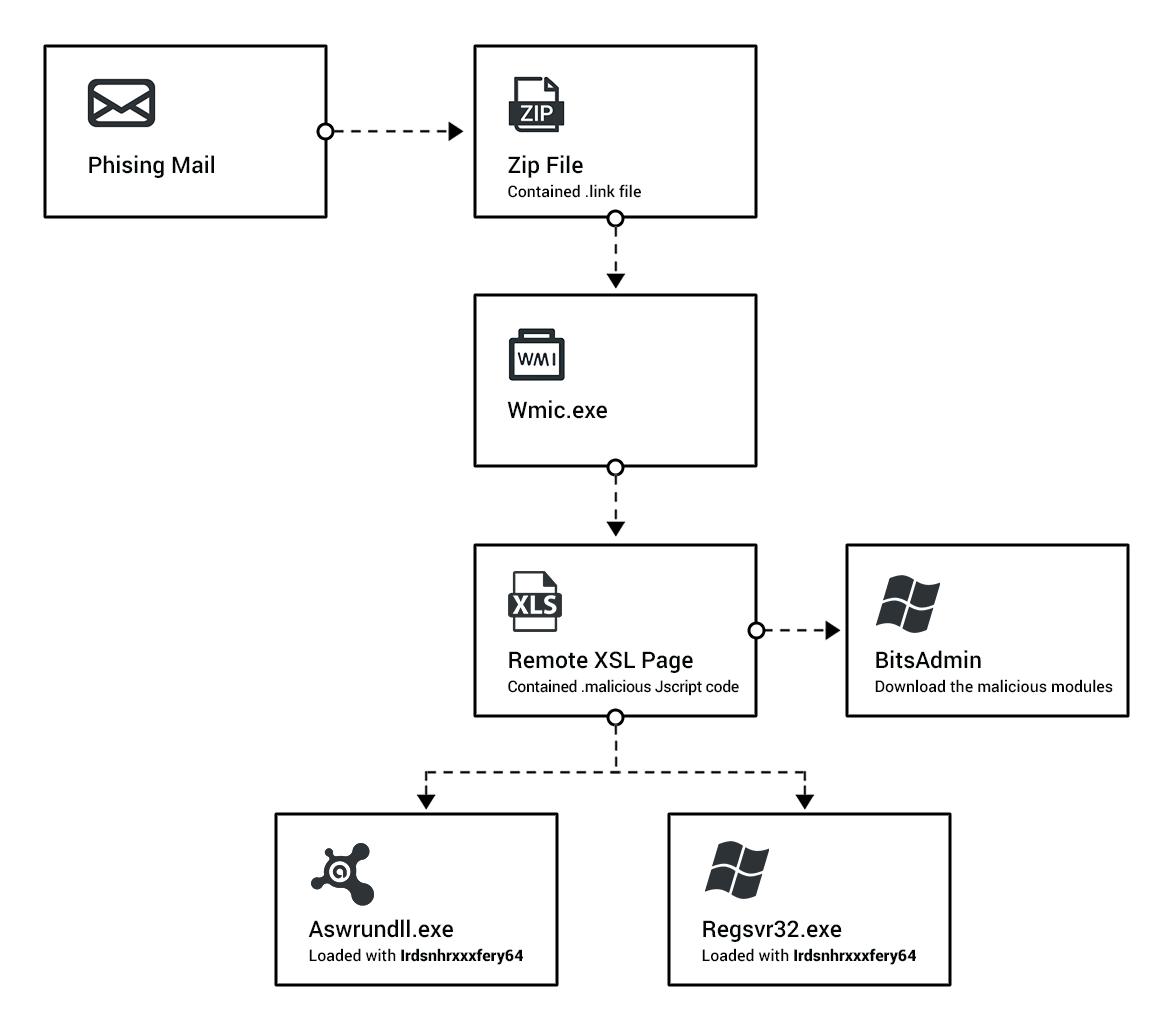
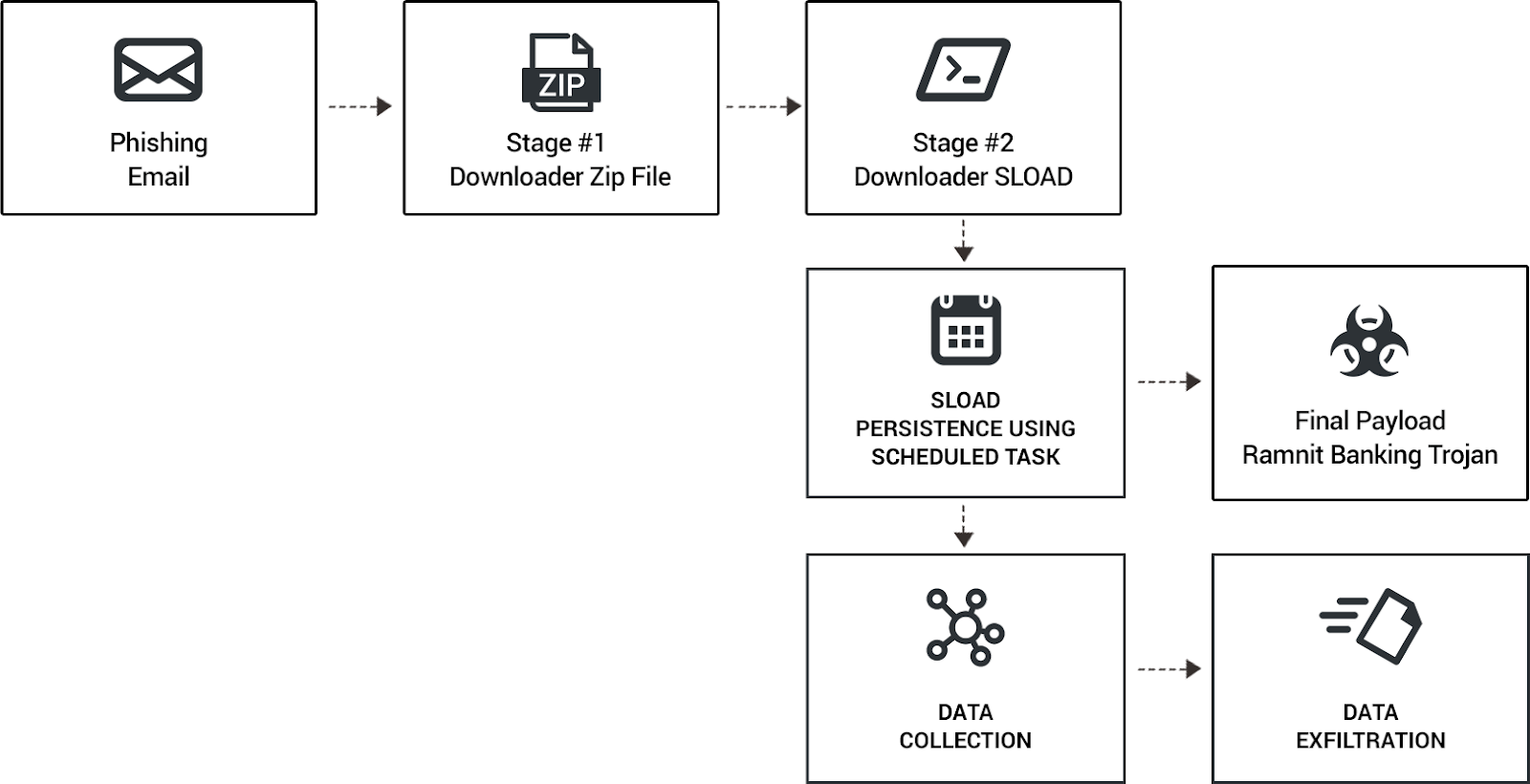
In just two months, Black Basta has added nearly 50 victims to their list, making them one of the more prominent ransomware gangs. The attackers infiltrate and move laterally throughout the network in a fully-developed RansomOps attack. The Cybereason Nocturnus Team assesses the threat level as HIGH SEVERITY given the destructive potential of the attacks...
June 24, 2022 / 6 minute read