
Enriching Raw Telemetry with the Cybereason Historical Data Lake
The Cybereason Historical Data Lake ingests all available telemetry collected for analysis for two primary use cases: Historical Threat Hunting and Deep Investigation...
Paul Stamp
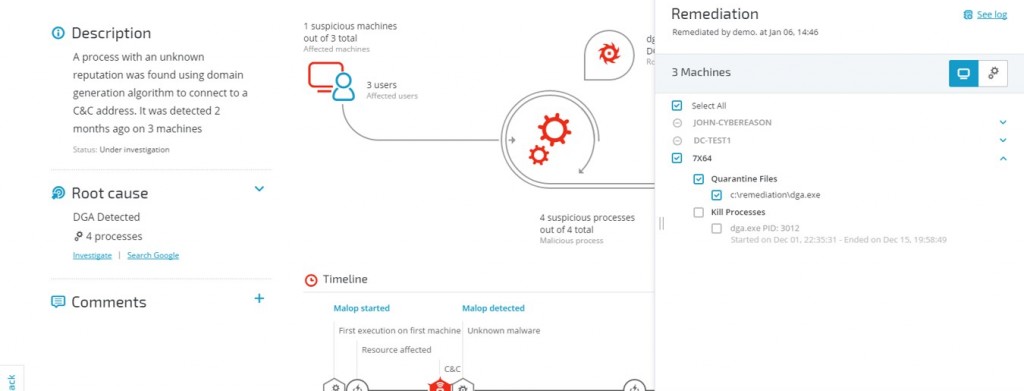
In a recent blog post, Gartner’s Anton Chuvakin wrote about “Using EDR for Remediation?” He defines remediation as “putting it the way it was.” NIST, in its Incident Handling Guide, goes into a little more detail - defining remediation as containment, eradication and recovery.
In reality, remediation is not simple at all, and remediation goes way beyond what any one tool can do. For remediation, there is no “one size fits all”, and as Chuvakin stated, full automation is probably not a good approach for remediation, as any attack would have its own effect and require a different response.
There are several steps in remediation. You need to:
Our recent release of Cybereason Guided Remediation streamlines and automates remediation processes where and when possible. Our latest release helps:
This is just the first step Cybereason is taking to help you remediate a cyberattack. We are currently developing additional capabilities to streamline the process of incident response and enable effective remediation of advanced threats. This includes new features that will enhance an organization's capabilities to contain, eradicate and recover from an attack.
Paul Stamp is the Director of Product Marketing at Cybereason.
Paul is the former Director of Product Marketing at Cybereason.

The Cybereason Historical Data Lake ingests all available telemetry collected for analysis for two primary use cases: Historical Threat Hunting and Deep Investigation...

Cybereason announces Unified Threat Hunting and Investigation, a significant development in its approach to storing long-term hunting data.

The Cybereason Historical Data Lake ingests all available telemetry collected for analysis for two primary use cases: Historical Threat Hunting and Deep Investigation...

Cybereason announces Unified Threat Hunting and Investigation, a significant development in its approach to storing long-term hunting data.
Get the latest research, expert insights, and security industry news.
Subscribe