
Cybereason Announces Unified Threat Hunting and Investigation
Cybereason announces Unified Threat Hunting and Investigation, a significant development in its approach to storing long-term hunting data.

Paul Bottomley
Regardless of whether you are performing Threat Hunting across your most recent dataset or your long-term historical datasets, an important dimension to your data is the enrichment and contextualization process.
Contextual data provides the Threat Hunter (“hunter”) with additional data points and a more complete picture of the activity, allowing them to make more informed decisions about whether the activity should be investigated further or disregarded.
The Cybereason Historical Data Lake, which logs all telemetry collected by our endpoint sensors, has two main use cases:
As of version 21.2.160, Historical Data Lake enriches raw telemetry from the endpoint sensors with our industry-leading MalOpTM (malicious operation) detection engine. This feature provides the hunter with invaluable context as to whether activity (results from their search) was detected as malicious in real-time by the Cybereason XDR Platform.
Given one of the goals of Threat Hunting is to surface threats that have evaded existing detection and prevention controls, this contextual data provides the hunter with enhanced focus. During historical hunting, the hunter may want to investigate results that have matched their search, yet were not detected as malicious (i.e. did not generate a MalOp) by the Cybereason XDR Platform at the time of the event.
In this scenario, the hunter may not want to waste valuable cycles investigating activity that has already been detected as malicious (and potentially remediated); they want to uncover new attacker activity, therefore their focus is on the results that are being reported as benign.
When performing Deep Investigation, however, the hunter may want to examine a machine or specific set of machines that have returned results identified as malicious (i.e. generated a MalOp) by the Cybereason XDR Platform at the time of the event. In this scenario, the hunter may want to use the identified malicious activity as a pivot point, establish a timeline of events, and uncover additional IOCs surrounding this pivot.
Bringing this to life, a typical hunting example and workflow may be as follows:
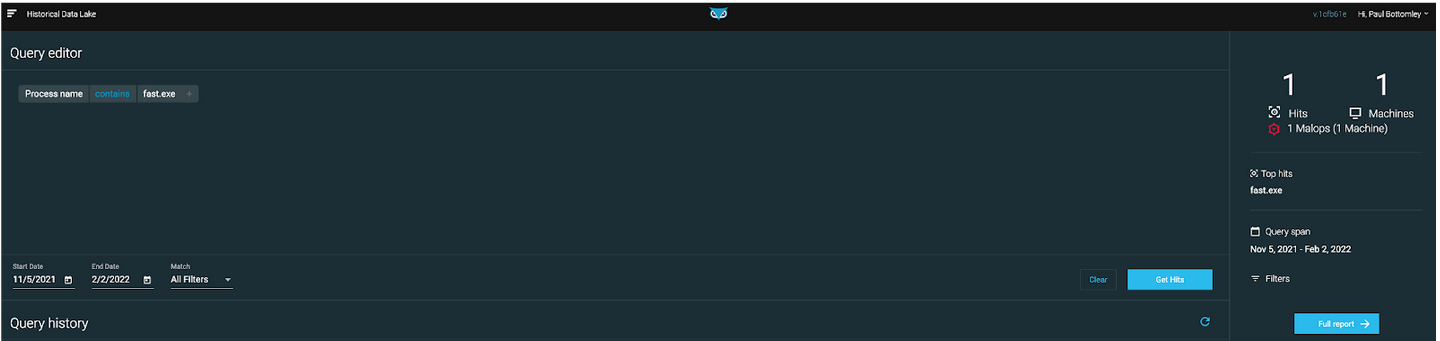 Figure 1: Hunter performing a simple process name search
Figure 1: Hunter performing a simple process name search
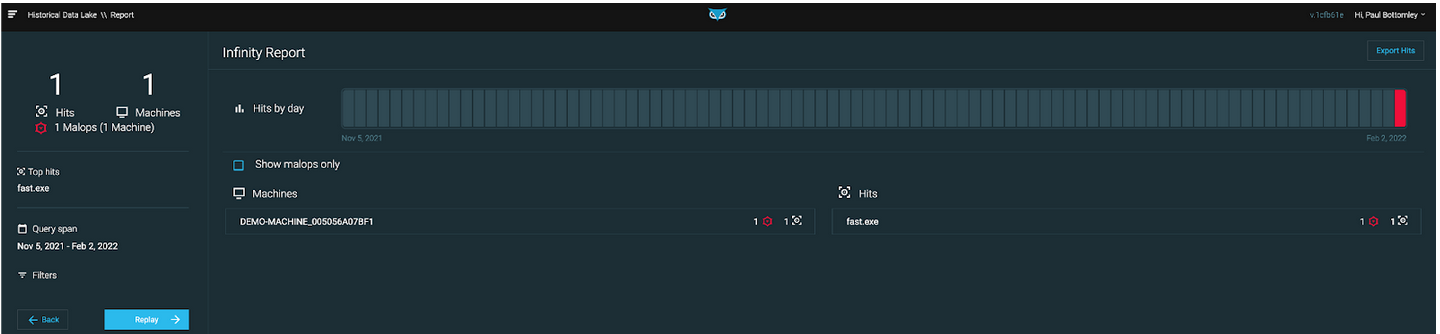 Figure 2: Result on one machine associated with a MalOp
Figure 2: Result on one machine associated with a MalOp
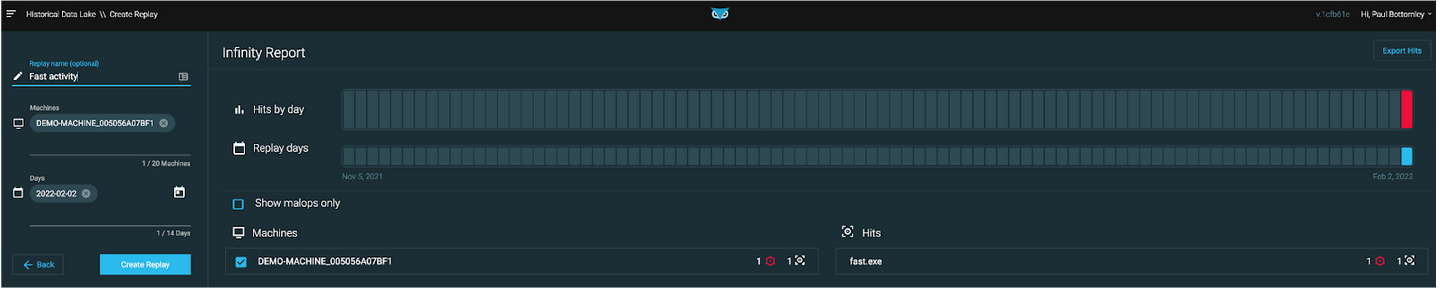 Figure 3: Hunter creating a ‘Replay’ to investigate the machine in greater depth
Figure 3: Hunter creating a ‘Replay’ to investigate the machine in greater depth
Cybereason is dedicated to teaming with defenders to end cyber attacks from endpoints to the enterprise to everywhere. Learn more about Historical Data Lake here or schedule a demo today to learn how your organization can benefit from extended data retention and investigation.

Paul is the Senior Product Manager for Threat Hunting and joined Cybereason in September 2021. Paul has over 10 years experience developing Threat Hunting products and services to global customers, which involved helping them surface attacker activity and cyber risk in their IT networks.
All Posts by Paul Bottomley
Cybereason announces Unified Threat Hunting and Investigation, a significant development in its approach to storing long-term hunting data.
.png)
The Cybereason Process Timeline view provides threat hunters with a unified timeline of events and full visibility of activity that happened on the endpoint...

Cybereason announces Unified Threat Hunting and Investigation, a significant development in its approach to storing long-term hunting data.
.png)
The Cybereason Process Timeline view provides threat hunters with a unified timeline of events and full visibility of activity that happened on the endpoint...
Get the latest research, expert insights, and security industry news.
Subscribe