The enterprise perimeter today is more distributed than ever, and securing it requires a strong understanding of the adversary and the evolving attack landscape. Since our founding in 2012, Cybereason has proven effective in stopping the most advanced attacks, and we continue to push the boundaries of innovation in our mission to enable organizations to remain secure in the face of evolving threats.
As a result of this success, we field a large number of inbound requests from organizations interested in switching from outmoded, reactive, legacy approaches to endpoint security that contribute to a poor defense posture, excessive alert fatigue, and disproportionate resource consumption.
If you are still using Symantec, you’re most likely tired of the complex workflows, the gaps in detection, and a resource-heavy solution that inhibits workflows and productivity. If so, it’s time to level up to a better solution that’s leading the industry.
Why Cybereason?
The Cybereason Defense Platform is purpose-built to protect organizations from the world’s most advanced attacks with a single agent, a single console, a single UI, and a dedicated, worldwide team committed to protecting all enterprise devices, including mobile and IoT.
The Cybereason Defense Platform offers unparalleled prevention, detection, investigation, and remediation across operating systems (Windows, macOS, Linux) and on all endpoints (workstations, laptops, iOS and Android devices) whether they are inside or outside the firewall, fixed or mobile, corporate or employee owned.
Cybereason Prevention - Next-Generation Antivirus (NGAV) & Controls
Cybereason Prevention gives you complete protection against modern threats—from traditional malware, advanced, and fileless to ransomware prevention. Cybereason Prevention also incorporates Endpoint Controls to allow your organization to apply an additional layer of security while enforcing security policies and addressing compliance concerns.
Core to the Cybereason Prevention is its ability to prevent access and execution by known malicious files in conjunction with behavioral-based prevention techniques, which instantly block unknown malware, including malicious .NET and PowerShell execution and ransomware. Cybereason Prevention’s NGAV also includes built-in response capabilities such as file exclusions, application control, machine isolation, and more. The Cybereason machine learning algorithms analyze both behavioral and static attributes of processes and files—blocking the execution of fileless attacks, new malware variants, and never-before-seen threats instantly.

How to Switch from Symantec to Cybereason
To leverage Cybereason prevention, install Cybereason by following these three simple steps:
- Install the Cybereason sensor and create an initial policy
- Create a prevention policy
- Uninstall Symantec and assign the prevention policy to the sensor
Step 1: Create an initial policy and install the Cybereason sensor
You can easily configure sensor policies from the Cybereason UI’s Policies Management screen.

Sensor policies
Before you install the Cybereason sensor, Cybereason sets up an initial sensor policy that you can easily assign to your Cybereason sensor when you install it in the next step.
This policy includes the Anti-Malware feature with the Signatures mode set to Off.
It is also possible to configure this policy to use the Artificial Intelligence analysis feature, which uses advanced machine learning models to determine the likelihood that a file is malicious. This offers immediate protection against new strains of malware, which are not typically detected by traditional antivirus tools.

Anti-Malware disabled
Save & Publish your policy.
At this stage, your organization also sets exclusions in the Symantec antivirus to allow installation of the Cybereason sensor process.
Install the sensor
From the Cybereason UI, you can easily download the sensor installer file across operating systems:

Cybereason sensor download
Install the Cybereason sensor by running the Cybereason installer file:

Cybereason installer
Alternatively, you can run the installer file in the command line using a software distribution tool. You must have administrative privileges to run this command.
After installation, a Cybereason icon appears on the end user’s system tray, and desktop notifications appear when malware is prevented.

Cybereason system tray icon and notifications
You can also choose to hide the icon or notifications by editing the endpoint UI settings in the sensor policy.
You can now assign the initial policy you set up in step a. (see Create an initial policy) to your sensor using the Set Policy option on the System > Sensors screen.

Set policy
Step 2: Create a prevention policy
At this stage, you prepare for the uninstallation of Symantec by setting up a system policy which sets the Anti-Malware feature to Prevent. You do not yet assign this policy to your sensor - this will be done simultaneously to uninstalling Symantec.
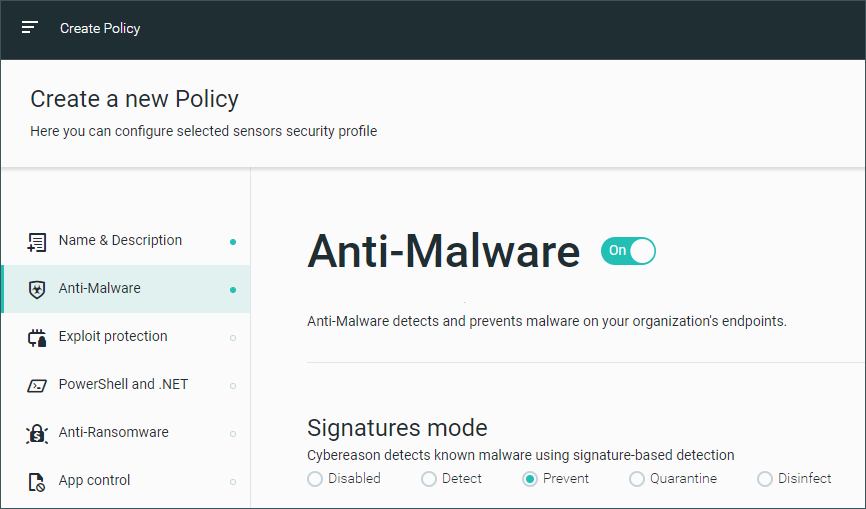
Step 3: Uninstall Symantec
Your organization’s system administrator will typically remove Symantec from multiple endpoints at once using a relevant tool or script, depending on the operating system. You can also remove Symantec from a single endpoint: for example, on Windows 10 under Apps & Features, you should be able to search for the Symantec application and uninstall it.
To ensure that the endpoints are fully protected throughout the uninstallation process, you immediately assign your prevention policy to the sensors on the endpoints from which Symantec was removed (you previously set up this policy in Step 2: Create a prevention policy).
Assign the policy to your organization’s sensors (as you did in step 1 when you installed the sensor).
You can also add prevention features to leverage Cybereason’s multi-layered prevention approach, including endpoint controls, phishing protection, fileless protection, and exploit protection.
Conclusion
Cybereason Prevention offers multi-layered protection via NGAV and Endpoint Controls with minimal impact on performance or needed IT resources - and without needing to deploy multiple agents. As demonstrated above, deploying Cybereason Prevention is simple, allowing your organizations to protect itself and start preventing attacks the same day.
Learn more about making the switch.
Quick Review: Cybereason vs. Symantec
|
Feature/Offering
|
Symantec
|
Cybereason
|
|
Unified ADMIN & Security console for Cybereason Preventions (NGAV & Endpoint Controls) and EDR
|
x
|
✓
|
|
Deployment (cloud, virtual private cloud, on-prem, air-gapped)
|
Multiple agents
|
Single agent
|
|
Fileless prevention
|
x
|
✓
|
|
Automated threat detection and response
|
x
|
✓
|
|
Managed hunting services
|
x
|
✓
|
|
One-click remediation
|
x
|
✓
|
|
Behavioral ransomware protection
|
x
|
✓
|
|
NSS Labs Advanced Endpoint Protection Certified
|
x
|
✓
|
|
AV Comparatives Business Security Certified
|
x
|
✓
|





