The foundation of the antivirus industry was built in the 1980s, with companies like McAfee and Avast releasing their first antivirus products. At that time, the terms “malware” and “computer virus” were just being born. Over the course of the next forty years, attackers would develop malware into the broad mix of crude and sophisticated software we see today. Now, there are over 1000M new malware samples classified every year.
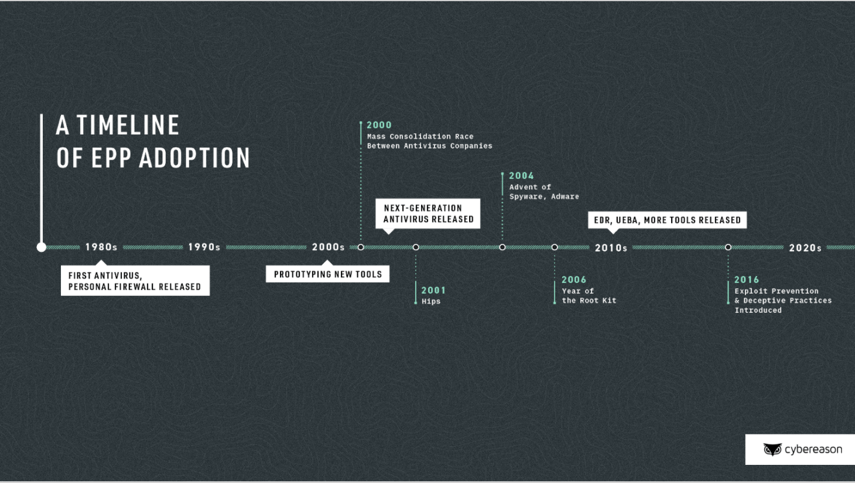
From targeted cyber espionage campaigns, to RATs relying on social engineering tactics, to fileless malware attacks, malicious payloads continually adapt as technology -- especially security tools -- fight to keep up. Ransomware and fileless malware are two of the most common and concerning types of malware legacy antivirus can’t stand up against.
- Ransomware, unlike other malware, traditionally doesn’t try to hide itself. It quickly encrypts as much data as possible, often causing damage immediately and requiring a ransom to receive files back. There’s also a shift to multistage ransomware, which lingers in the environment, exfiltrating as much valuable data as possible before detonating the ransomware.
- Fileless malware, which relies on native operating system tools like .NET, WMI, and PowerShell to perform malicious activities under the cover of normal operations. This method is made to evade legacy antivirus.
What is NGAV and why is it more effective than traditional antivirus?
Next-generation antivirus combines traditional antivirus with behavioral-based prevention to prevent more evasive threats than legacy antivirus alone. Just like antivirus, NGAV is continuously updated with the latest threat intel. It scans in the background, comparing these indicators to the files and directories on computer platforms, and labels any suspicious matches. The software then prevents these programs from running and automatically either quarantines or removes them.
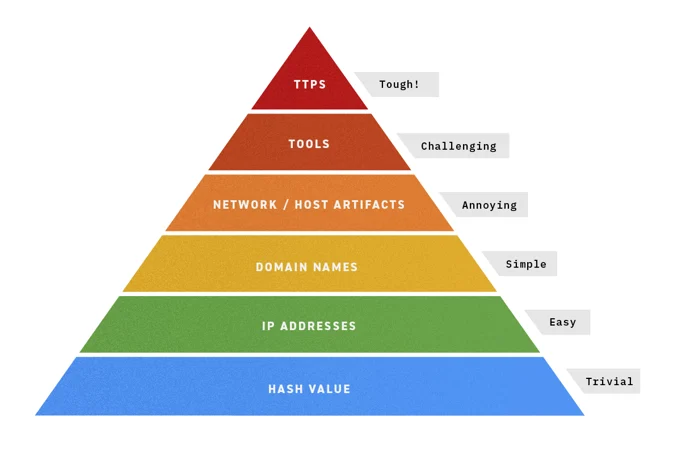
Pyramid of pain by David J Bianco - TTPs are toughest to defend against.
This isn’t enough, however, for modern-day attacks that are as well-coordinated as many legitimate business operations. For threats like fileless malware,IOCs are either not present or may change based on the environment, which puts antivirus dramatically behind the curve.
NGAV, in contrast, relies on a combination of antivirus, behavioral analysis, and machine learning to address these threats. By focusing on commonalities across tactics, techniques, and procedures (TTPs), NGAV gives a behavior-based approach that can more accurately single out the attackers from the legitimate users.
Machine learning is critical to NGAV’s anti-ransomware and anti-fileless-malware capabilities, going beyond known bad URLs and attachments to address unknown attacks. In short, NGAV is able to catch more than traditional antivirus.
How to assess NGAV solutions
Ultimately, assessing NGAV goes beyond the vendor’s messaging and into the real-world where it can be tested by your team or by a reputable organization. Consider things like:
- How well it evaluates suspicious behavior
- How well it performs against a set of advanced threats
NGAVs are limited when they take a conventional blocklisting/allowlisting approach without incorporating that behavioral-based prevention aspect. Tools like WMI and PowerShell are heavily used by IT admins, and can’t be blocklisted; allowlisting “good” PowerShell activity, meanwhile, can be time-consuming. This is why it’s so important for NGAV to leverage machine learning for behavioral-based prevention.
Performance against advanced threats: what’s next for NGAV
Our research shows that malware techniques rarely exist in silos. Instead, they’re often combined: for instance, a malicious macro is delivered through email, then uses a legitimate tool like PowerShell to download a malicious payload like ransomware.
That’s why an NGAV that aligns to the MITRE ATT&CK framework can be especially valuable. By incorporating the MITRE ATT&CK knowledge base, NGAV is set up to more effectively be used in conjunction with an endpoint detection and response tool.
NGAV should be able to protect as many of an organization’s endpoints as possible, whether it is laptops, desktops, workstations, or mobile devices.
Using NGAV and EDR Together
NGAV is the front line of defense, that can handle commodity malware. Where you need EDR is for more advanced kinds of malicious activity - all the things that make it past NGAV. NGAV focuses on preventing threats on individual endpoints; EDR collects data from every endpoint, feeding known bad back to NGAV to improve its prevention.
The combination of NGAV with EDR, as well as other items, is an endpoint protection platform (EPP). EPPs are a unified approach to enterprise security that gives layers of proactive defense.
To learn more about how and where EPP fits within an overall security strategy and addresses risk, watch our on-demand webinar Cutting Through the EPP Noise: A Future Proof Strategy.
For a glimpse of what modern ransomware looks like and how they're evading legacy prevention solutions, check out our ransomware decoded whitepaper.









