Cybereason is constantly innovating to ensure that our customers can achieve the utmost efficacy and efficiency in their security programs. The latest release of the Cybereason Defense Platform is packed with enhancements, including improvements to query results, sensor management, updated workflows, and expanded support for Linux. Customers can read the complete release notes on The Nest.
For this post, we’ll focus on the recent improvements in the areas of investigation, enhanced protection, and infrastructure management.
INVESTIGATION
Find key artifacts faster with an improved live file search screen experience
We have improved the experience of executing file search operations:
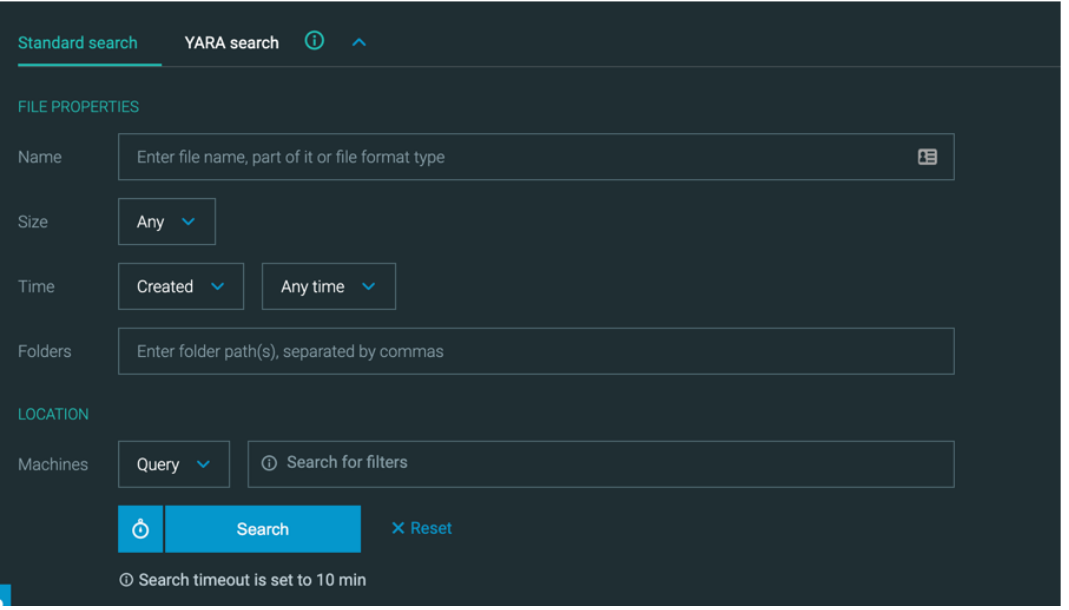
Now, you can select from a standard search based on search filters, or a YARA rule-based search.
In addition, you have the option to select different types of dynamic filters to help you search for the correct machines:
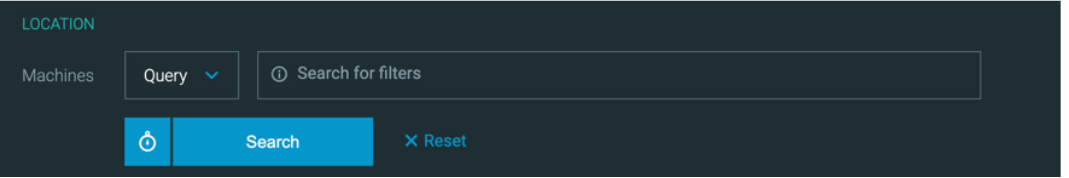
Learn more about Cybereason DFIR capabilities here.
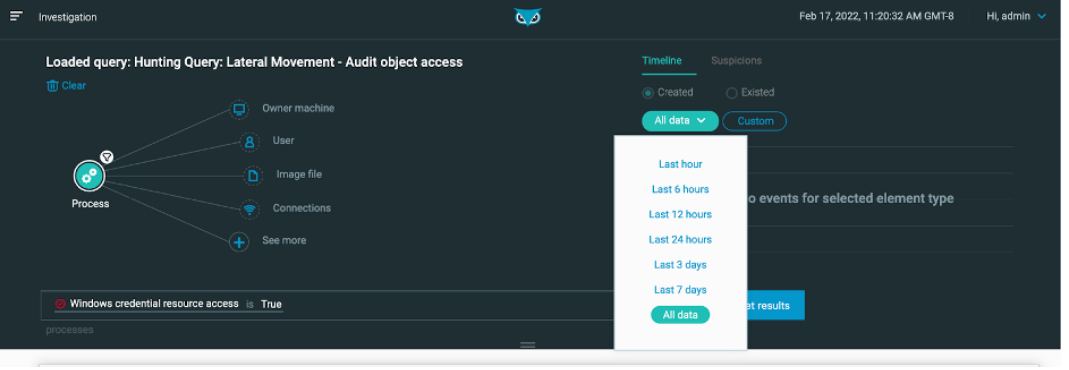
See more granular results with investigation query result enhancements
From the Investigation screen, you can select a timeframe within which to apply your query. Options include the last hour, 6 hours, 12 hours, or 24 hours, the last 3 or 7 days, or all data. The default value is 24 hours:
In addition, you can also now customize a specific number of results in a page of query results:
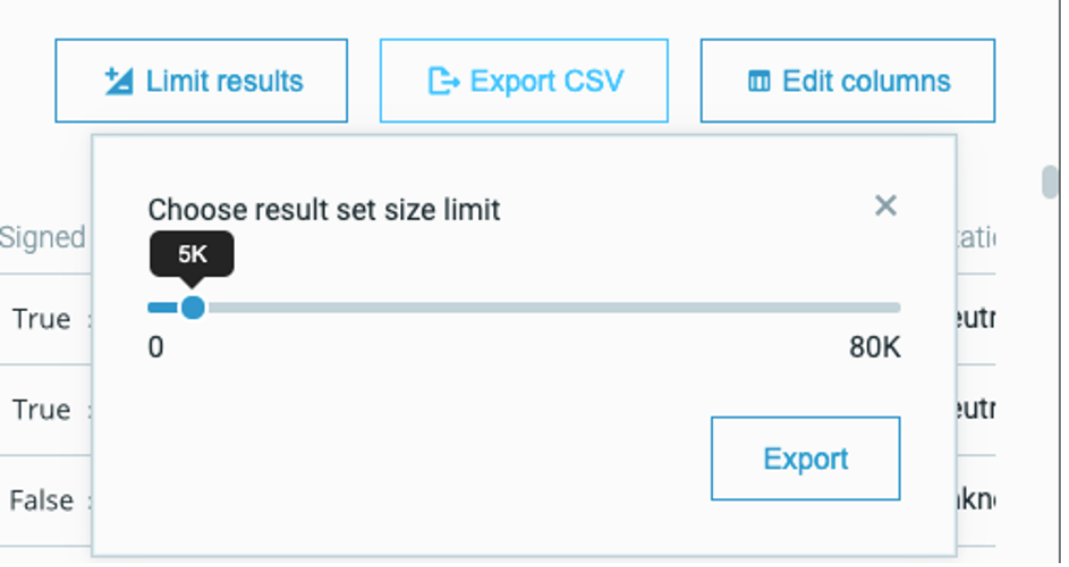
Learn more about Cybereason Threat Hunting here.
ENHANCED PROTECTION
Uncover malicious activity occurring in containers at runtime with Cloud Workload Protection
The Cybereason Cloud Workload Protection (CWP) offering protects workloads and containers at runtime wherever they reside or move across the infrastructure. This cloud-native solution extends powerful sensors across the environment, providing the most effective threat detection and prevention available.
Two new sensors have been developed that can be deployed on a Docker host or Kubernetes clusters. These sensors collect security data that is correlated with all other data collected by Cybereason and is displayed across the Cybereason Defense platform:
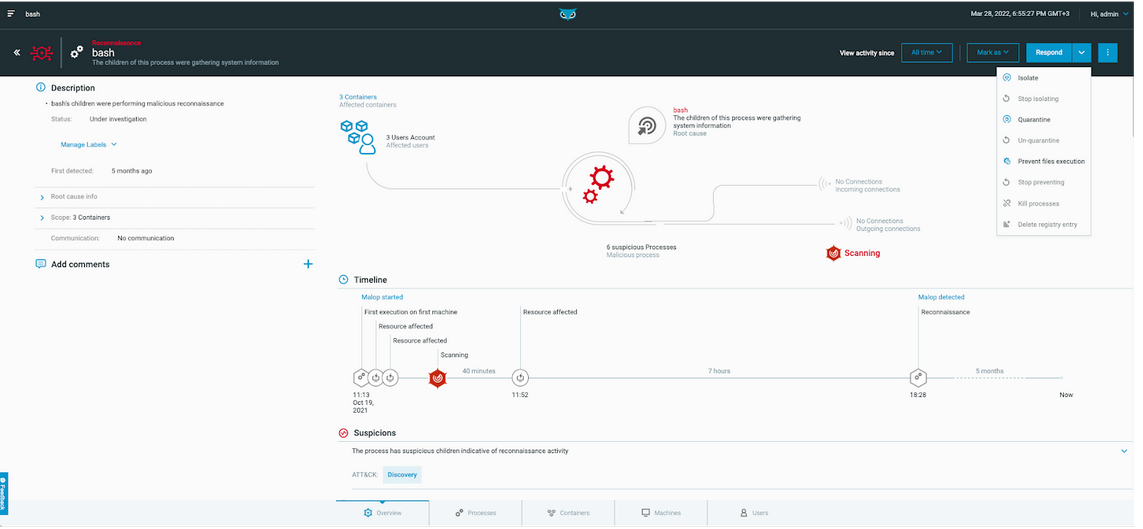
Learn more about Cybereason Cloud Workload Protection here.
Leverage the intelligence of sophisticated EDR detections to improve preventative efficacy
Behavioral Execution Prevention (BEP) allows organizations to detect and prevent malicious execution of processes based on the process behavior. Behavioral Execution Prevention uses intricate research data leveraged by the Cybereason EDR solution to identify anomalies in processes, image names, metadata, command line commands, or the process hierarchy.
When used in the Behavioral Execution Prevention technology this data provides inline prevention on the endpoint, significantly shortening response time. Learn more about Behavioral Execution Prevention here.
INFRASTRUCTURE MANAGEMENT
Increase alarm accuracy with the new custom reputation screen
We made significant enhancements to the custom reputations screen. Now users can add, edit or remove reputations from the private lists directly within the console, and can also edit the lists or search for file types based on wide-ranging criteria.
Custom reputations are a great way to keep false positive detections low but also ensure you are detecting what needs to be detected, specific to your environment:
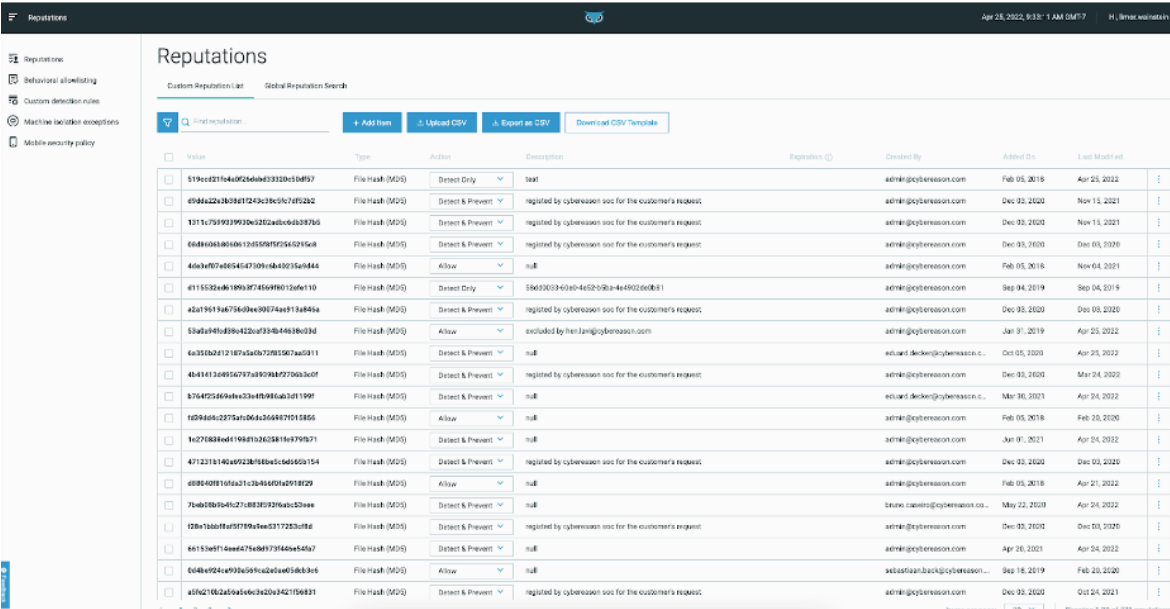
Learn more about achieving faster, more accurate response with Cybereason Threat Intelligence here.
Adjust protections to best leverage the configuration of your unique environment with fileless mode protection module selection
When you configure the Fileless protection settings in a sensor policy, you can choose to leverage .NET, AMSI, or both, based on the needs of your organization:
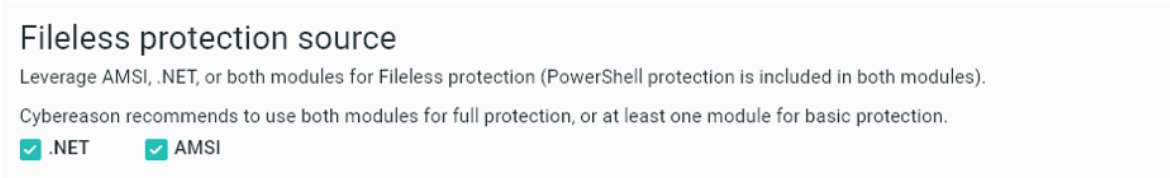
Learn more about defending against fileless malware here.
Improve endpoint resiliency with enhanced sensor tampering protection
Enhanced sensor tampering protects sensor processes and files against unauthorized or malicious modifications or kill attempts.
Sensor tampering protection provides enhanced protection to the Cybereason processes running on Windows endpoints. With sensor tampering protection, Cybereason protects its processes and files against unauthorized or malicious modifications or kill attempts.
In addition, sensor tampering protection protects the sensor from end-users terminating the process and inadvertently exposing the endpoint machine to potential attacks.
Ease deployment processes with sensor installer packages for sensor groups
When using sensor groups you can download a sensor installation package pre-configured to add sensors to a specific group to streamline your deployment process.
Learn more about the deployment process here.
Decrease maintenance tasks with the improved sensor update process
We improved the sensor upgrade process to enable you to perform sensor updates with increased efficiency.
The sensor now checks for an updated sensor package every few hours. If an updated package is found, the package is downloaded but not installed. After an administrator triggers a sensor upgrade action the sensor is able to install the pre-downloaded package.
With these improvements, you can update up to 1,000 sensors each hour—all without degrading network performance.
Decrease the Linux attack surface with expanded feature support
We expanded support of platform features to supported Linux operating systems, including:
- Device control for MTP and USB devices
- Personal firewall control
- Remote Shell
- NGAV Support for On-file access scans
- NGAV Automatic exclusion of known or safe processes on the machine
Learn more about Cybereason NGAV here.
New OS Support
We added support for the following operating systems/platforms:
- Windows 10 21H2
- MacOS 12 (Monterey)
- Amazon Linux 2
- Debian 10
A full list of supported operating systems is available for customers in the Nest.
Cybereason is dedicated to teaming with defenders to end attacks on the endpoint, across the enterprise, to everywhere the battle is taking place. Learn more about AI-Driven Cybereason XDR here or schedule a demo today to learn how your organization can benefit from an operation-centric approach to security.












