Threat Intelligence is a process of enriching detections with contextual clues from data that provides a clearer understanding of the threat. If there isn’t a direct hit of a detection rule and specific processes are suspicious rather than outright malicious, threat intelligence can un-muddy the waters to provide a clearer picture.
Threat intelligence most often comes in feeds built from historical knowledge on certain types of processes, IP addresses, domains, and other telemetry sources that are flagged as unusual or harmful. Unknown processes that are potentially malicious can be identified through sandboxing and other forms of analysis to determine a maliciousness score. This scoring system can help teams triage detections appropriately, respond to the most severe threats first and foremost, and work backward to less severe issues.
For every process that runs in an organization’s environment, Cybereason must determine if the file is malicious or benign and, if malicious, what type of malware it is. How does Cybereason reach this conclusion?
Cybereason Threat Intelligence
Nocturnus Research and Global SOC Teams
Cybereason has brought the world’s brightest minds from the military, government intelligence, and enterprise security to uncover emerging global threats through our Nocturnus team. Nocturnus discoveries and insights are injected directly into the Cybereason Defense Platform for up-to-the-minute threat intelligence.
We apply proprietary file hash classification from our Global SOC and Nocturnus teams, who use artificial intelligence and machine learning models to classify malicious operations (MalOps™) with a high level of accuracy. In addition, a proprietary classification process is applied for third-party information.
Common IOC Formats, including YARA, STIX/TAXII, and YAML
YARA rules are a way of identifying malware or other threats by searching for common characteristics. Analysts can ingest YARA rules to search for specific IOCs (indicators of compromise) as new intelligence becomes available through various sources.
Similarly, STIX / TAXII is a standardized language that describes threat information. Analysts can also ingest STIX/TAXII threat intelligence to search for IOCs, create enrichment, and other YAML formatted reputations.
MITRE ATT&CK
MITRE ATT&CK is an industry-standard knowledge base of adversarial tactics, techniques, and procedures. ATT&CK tracks and catalogs what an adversary attempts to execute from a tactical perspective.
Whenever a MITRE ATT&CK detection rule is violated, accompanying threat intelligence is provided in-platform so that infosec analysts quickly know what took place, why that matters, and how to respond accordingly.
Cybereason recently posted the best performance results in the history of the MITRE evaluations - learn more about the superior protection against advanced threats delivered by Cybereason based on the latest round of MITRE testing.
Threat Intelligence powered by Binary Similarity Analysis
Sandboxing can be difficult and often slows threat investigations. Cybereason offers a more nimble approach to inspecting unknown binaries without the drawbacks of a sandbox but creates the same outcome of enrichment and intelligence.
Teams can drop zero-day binaries into our portal and within seconds understand maliciousness scores, which malware family a specific binary is related to, whether or not a threat has been obfuscated, and a host of other factors that create the necessary context for response and recovery.
Custom Reputations
The Cybereason Defense Platform enables users to maintain customizable private reputation lists called allowlists and blocklists.
Teams can associate response actions to any file, hash, process, IP address, or domain tracked in the reputation list. If a given behavior is malicious, analysts can program an immediate blocking action and the firing of a detection (MalOp) within the platform.
Equally valuable is the ability to mark benign behaviors as safe and add those behaviors or hashes to an allowlist that ensures a detection will not fire for a standard but seemingly suspicious process. This level of customization is necessary because every organization has specific security needs, and some legitimate programs exhibit behaviors that resemble those of malicious tools:
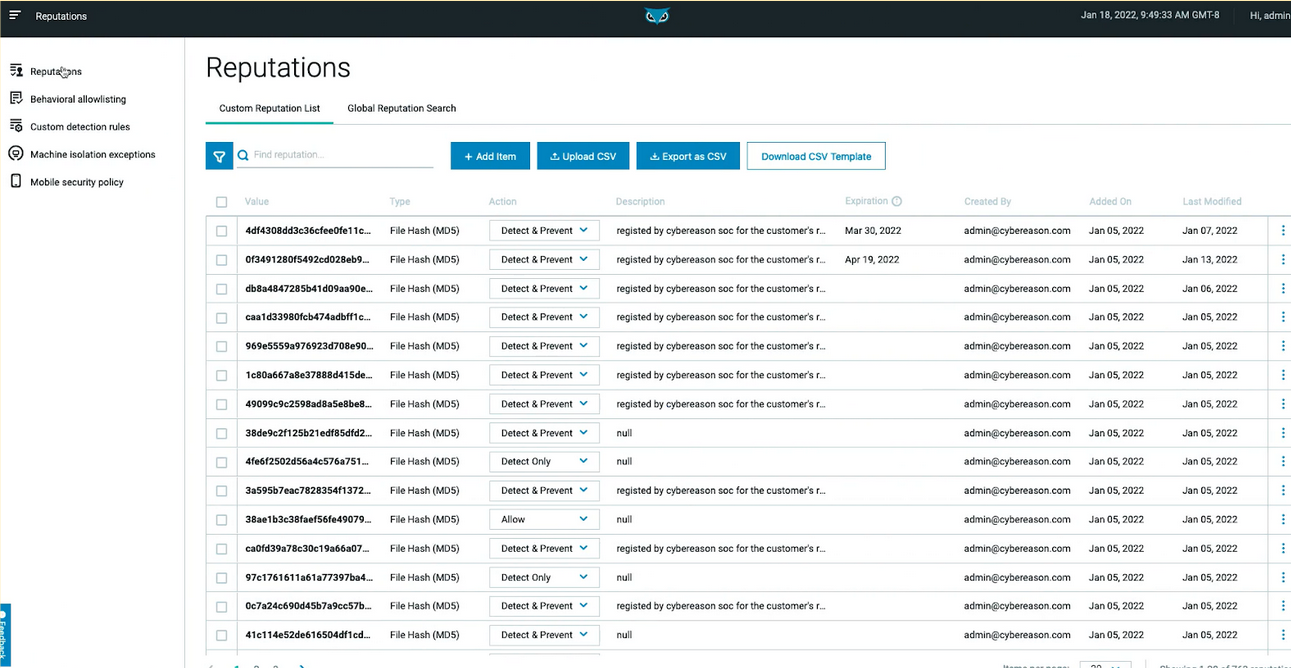 Cybereason's new Reputations UI view.
Cybereason's new Reputations UI view.
We’ve recently enhanced this interface, as seen above. Now users can add, edit or remove reputations from the private lists directly within the console and edit the lists or search for file types based on wide-ranging criteria.
Custom reputations are a great way to keep false positive detections low and ensure you detect what needs to be detected, specific to your environment.
Leveraging third-party feeds
Flexibility is king for a top-tier EDR solution in today’s marketplace, and many organizations rely on multiple external threat intelligence feeds to enrich their detections. Cybereason integrates external threat intelligence feeds directly into our console, with out-of-the-box integrations with standard tools, including:
- VirusTotal
- ReversingLabs
- ThreatConnect
- Threat Quotient
- VMRay
- Polarity
- + many others on demand via RESTful API architecture
Sandboxing is a common technique to understand unknown threats and provide additional enrichment and contextualization. Tools like VMRay can be used to detonate unknown executables, observe their behaviors, and provide threat scoring and intelligence directly through the Cybereason console.
However, different threat feeds from third-party providers often do not agree on which IOCs are malicious or unknown. This conflicting information makes it difficult to determine the maliciousness of a threat and take action quickly.
Cybereason aggregates multiple threat feeds and cross-examines those feeds against machine learning analysis to rank the various threat feeds based on their historical accuracy for particular types of threats from numerous adversary groups. This enables Cybereason to determine the correct threat intelligence source to respond quickly and precisely, simplifying the investigation and response process.
Cybereason has created a statistical machine learning algorithm trained over large data sets and analyst feedback. The algorithm provides scoring to the information contained in threat intel reports, enabling our threat intelligence to reach a confident classification, even in cases where there is disagreement among vendors.
The ML algorithm includes a set of complex calculations that:
- Assess the accuracy of previous classifications.
- Address the strengths and weaknesses of specific vendors.
- Perform sophisticated analysis of text tokens within the report to understand the meaning behind each vendor’s verdict string. For example, if the report text includes the string ‘Bad Rabbit,’ this increases the likelihood that the file will be classified as Ransomware.
- Use additional metadata from intel reports apart from vendor verdicts.
If you are interested in learning more about this product and its capabilities, request a demo today. Cybereason is dedicated to teaming with defenders to end attacks on the endpoint, across the enterprise, to everywhere the battle is taking place.




 Cybereason's new Reputations UI view.
Cybereason's new Reputations UI view.
