A skyrocketing number of alerts, limited security talent, and millions of new malware strains daily have made security a seemingly insurmountable task. Though MITRE ATT&CK gives a good basis of knowledge and input, it’s important to expand your inputs to other areas to give you a more complete and timely perspective.
Simply buying another security tool doesn’t make it easier. Adversary groups are constantly evolving, putting pressure on security teams to anticipate adversary advancements in smarter and more human ways.
Read The Whitepaper
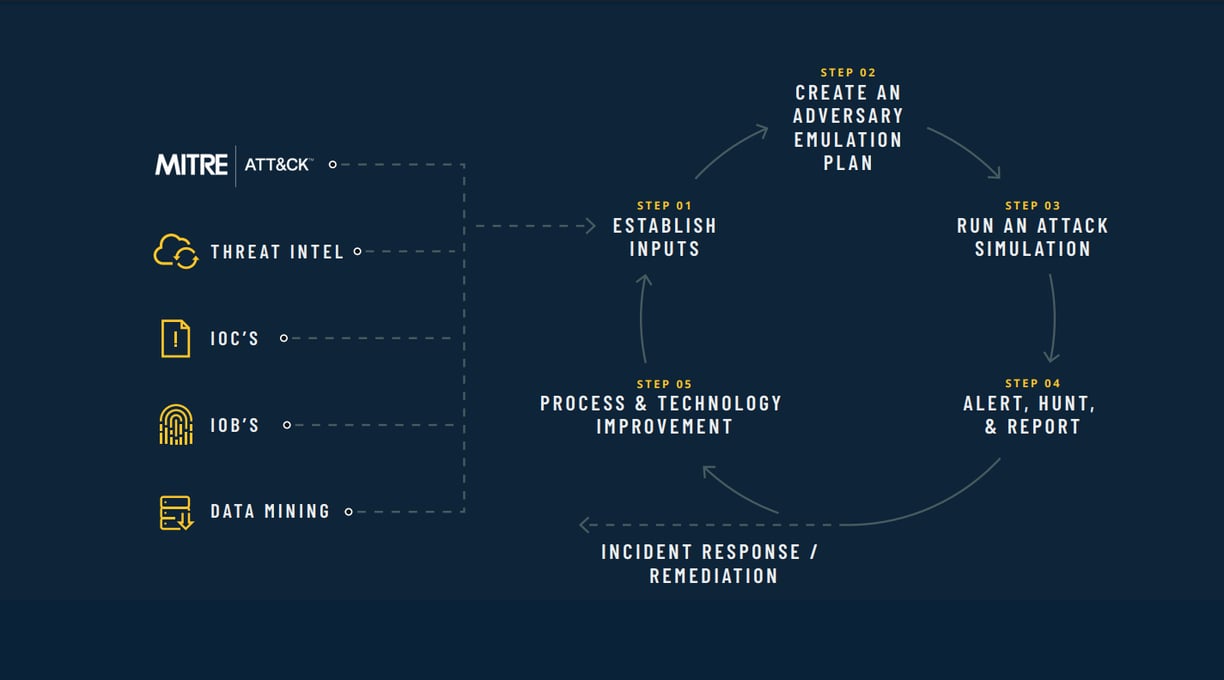
This white paper establishes a process that empowers SecOps to improve iteratively over time by leveraging their existing talent and tools. Implementing MITRE ATT&CK takes five simple steps that easily integrate with any security strategy:
- Step 1: Establish Inputs
- Step 2: Create an Adversary Emulation Plan
- Step 3: Run an Attack Simulation
- Step 4: Alert, Hunt, and Report
- Step 5: Process and Technology Improvement
With these five steps, you can continuously tune your security strategy and leverage the connection between techniques, tactics, and procedures, adversary emulation plans, and real-world adversary groups. Use these steps to align your blue and red teams around a common goal: securing your environment against real adversaries.
RESOURCES:






