MITRE’s Adversarial Tactics, Techniques, and Common Knowledge (MITRE ATT&CK) is a model and knowledge base of adversary behavior. It catalogs the attack lifecycle of different adversaries and the platforms they choose to target, all based on real-world observations. ATT&CK is not a static framework, and is updated quarterly with new adversaries, tactics, techniques, and other information supplied by security vendors and organizations around the world.
Since its public release, MITRE ATT&CK has become a staple of the endpoint security space. As of this writing, ATT&CK has built a community for sharing techniques, a yearly conference called ATT&CKCon, adversary emulation plans, evaluations for security vendors, and various tools to interface with ATT&CK.
In our paper on Five Steps to Enhance SecOps with MITRE ATT&CK, we explain how to use two of MITRE ATT&CK’s most important components to develop a continuously improving defense.
What are Tactics, Techniques, and Procedures?
Long before their use in cybersecurity, tactics, techniques, and procedures (TTPs) were used to describe military operations within the United States Department of Defense. Like much military terminology, TTPs are aptly used in cybersecurity, as they describe the processes and profile of a specific adversary.
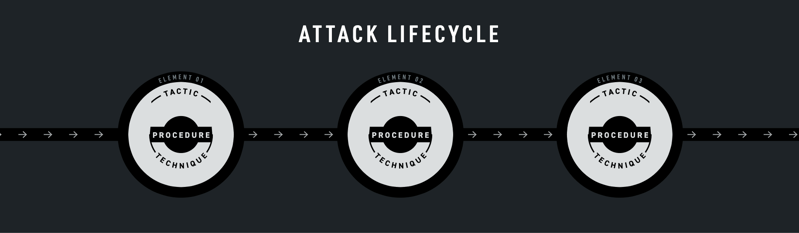
Figure 1: A representation of how techniques, tactics, and procedures can be represented as part of the attack lifecycle.
Tactic: A tactic is a high-level description of part of the attack lifecycle with limited details on how the adversary explicitly carries out an activity. For example, MITRE ATT&CK lists twelve different enterprise tactics attackers may use across their attack lifecycle, like initial access (TA0001), persistence (TA0003), command and control (TA0011), and exfiltration (TA0010).
Technique: A technique is the middle ground between high-level considerations of tactics and specific details of procedures. Within each tactic are a list of techniques that adversaries may use to accomplish the goal of the tactic. For example, some MITRE ATT&CK techniques can be used for initial access (TA0001), including a drive-by compromise (T1189), spearphishing via service (T1194), or a supply chain compromise (T1195).
Procedure: A procedure is the specific details of how an adversary carries out a technique to achieve a tactic. For example, MITRE ATT&CK lists how APT19 (G0073) uses a watering hole attack to perform a drive-by compromise (T1189) and gain initial access (TA0001) of forbes.com in 2014.
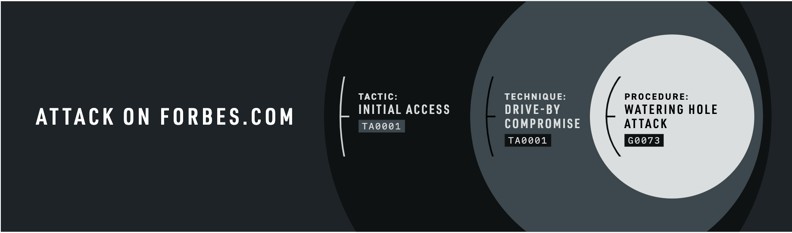
Figure 2: A representation of how techniques, tactics, and procedures for APT19’s attack on forbes.com can be represented.
TTPs give vendors, analysts, and everyone in between a common vocabulary around which to consistently communicate methods of an attack.
Diving Deeper into THE MITRE ATT&CK LIFECYCLE
Choosing the Right Targets
MITRE ATT&CK has threat intelligence on almost eighty different adversaries, from the techniques they use to the industries they target. To get the most out of your AEP, prioritize simulating adversaries you are most likely to face in real life.
For example, a healthcare organization may model an adversary like Deep Panda (MITRE ATT&CK ID G0009), since they are well-known for targeting healthcare companies like Anthem. This same thinking can be applied to all the adversary groups across industries.
Table 1: Example adversaries and the industries they target.
To make things easier, you can search for an industry within the MITRE ATT&CK website and immediately see which adversaries are known to target it.
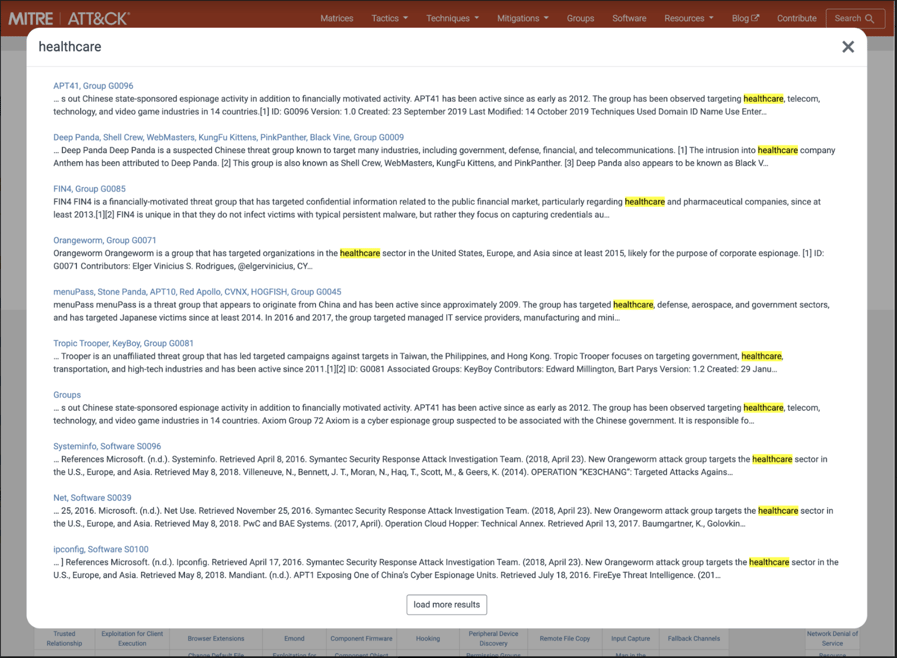
Figure 3: Searching the MITRE ATT&CK website for adversary groups known to target healthcare companies.
To learn more about the MITRE ATT&CK Framework in our 101 series.








