Despite spending millions of dollars on cybersecurity tools over the past few years, most organizations still can’t detect or respond to cyber attacks in a reasonable timeframe. According to Verizon's 2021 Data Breach Investigations Report (DBIR), 60% of incidents were discovered within days. However, in 20% of attacks, it took months or longer before organizations realized a breach had occurred.
And that’s just the beginning of the problem.
When an attacker gains initial access to your network, the clock starts ticking. Advanced threat actors have shortened the amount of time it takes them to shift from initial compromise to lateral movement and compromise of other high-value systems and data from several hours just a few years ago to, in some cases, less than 20 minutes today.
For most teams, an organization’s ability to respond to a cybersecurity incident depends on the quality of the alerts produced across their security stack. The higher the quality and context of the initial alert, the faster the team can investigate and respond.
Monitoring technologies often produce low-quality alert signals—it isn’t clear what’s happening, if it’s important, and what to do about it. The problem has been compounded by the fact that most organizations have tried to overcome this challenge by adding more security tools to their tech stack. The results have been predictable: out-of-control tool sprawl and continuous integration complexities.
AI-driven Cybereason XDR comes with native response capabilities that eliminate having to work with IT to take incident response actions. Guided and automated response capabilities further empower analysts and reduce errors.
Let’s break down Cybereason XDR’s operation-centric approach and how it enables analysts of all skill levels to quickly understand an attack without crafting complicated queries, and pivot directly from an investigation to remediation for a 10X improvement in response times.
The Spear Phishing Office 365 Pivot
This attack starts with Microsoft 365 but quickly traverses through different applications, assets, and data silos across the customer’s environment. In the below example, we see Microsoft 365 identified as the root cause of the attack. A malicious attachment has been sent to multiple email addresses/recipients.
One of the 21 recipients, Sivan Omer, has opened the file, which gives the attacker remote access to her endpoint. Cybereason XDR, with its multi-dimensional correlation, is able to pull in other behaviors related to Sivan, including relevant domain, identity, and network access:
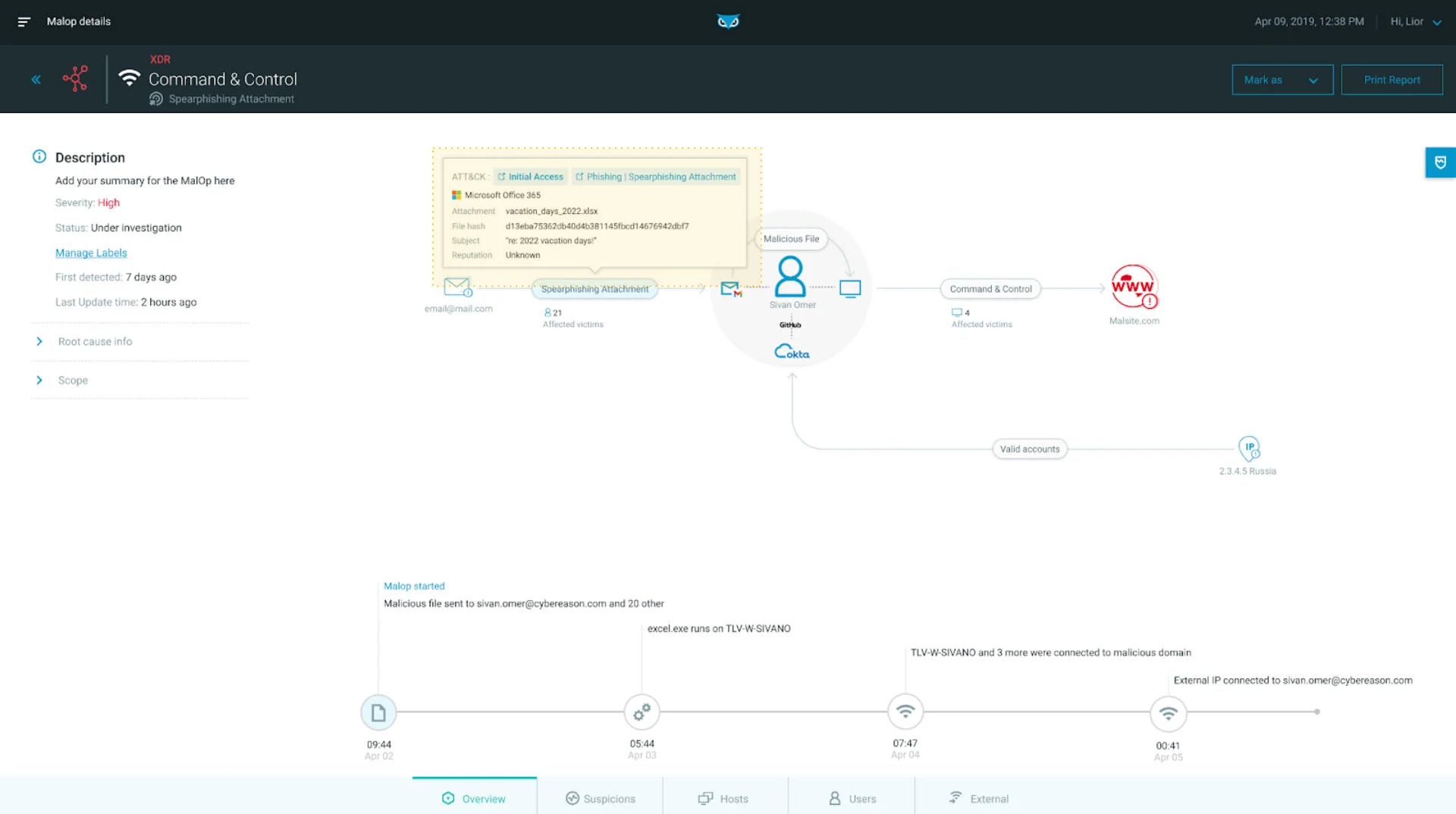
Spear Phishing Office 365 as seen in the Cybereason XDR Platform
The grey circle in the middle of the MalOp highlights the correlation map established by Cybereason XDR across Sivan Omer’s email account, her identity, and her endpoint. Microsoft 365 has been identified as the root cause of the attack. A malicious attachment has been sent to multiple email addresses/recipients.
As we can see in the below screenshot, her compromised endpoint is now engaging with a host in South Korea through an outbound C2. This is identified by Fortinet Firewall, correlated with broader data sources, and surfaced here to help analysts understand the full scope of the attack:
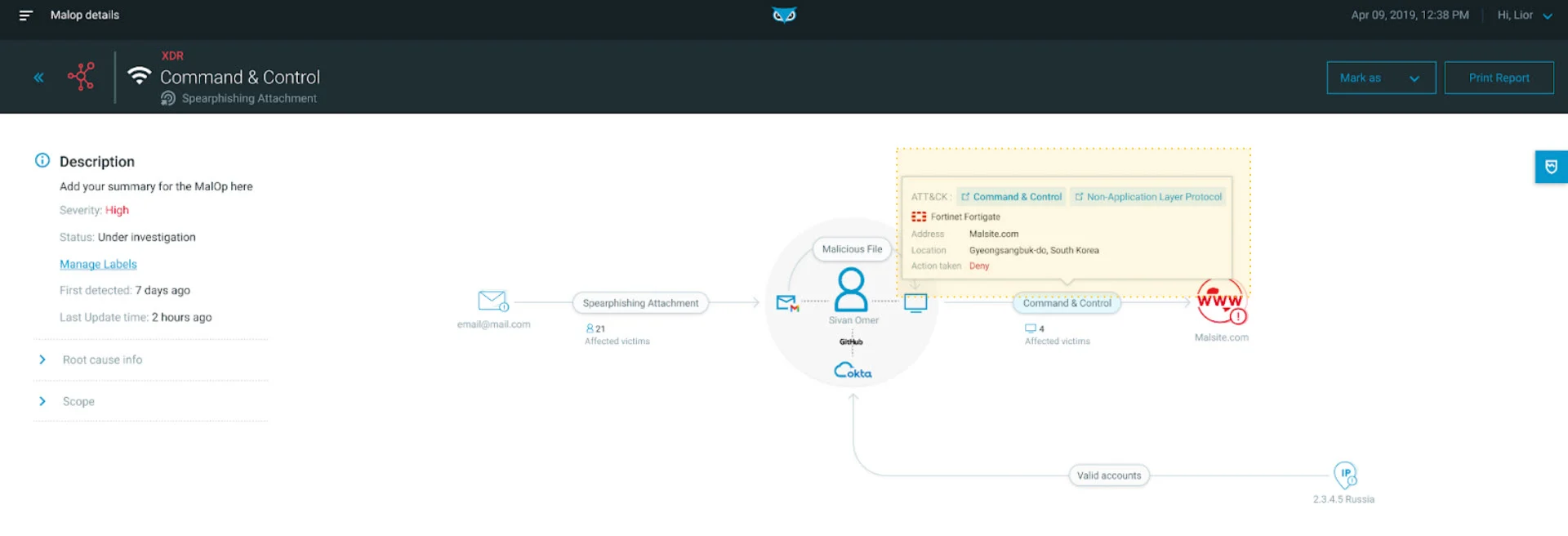
Telemetry correlations as seen in the Cybereason XDR Platform
“In a pre-XDR world, the Defenders would have to go and piece that story together. This is an insanely complex task that oftentimes can only be achieved by L3 analysts when we actually allocate enough time and attention to the pieces of the puzzle,” said Striem-Amit. “Oftentimes this won't happen in the real world.”
In addition to Cybereason XDR shows the analyst the true extent of the problem (i.e. there are 21 other recipients of the spear phish), Cybereason XDR (screenshot below) provides insights into what is happening across endpoints. This includes suspicious and malicious techniques mapped to MITRE ATT&CK, deeper threat hunting, and other affected machines:
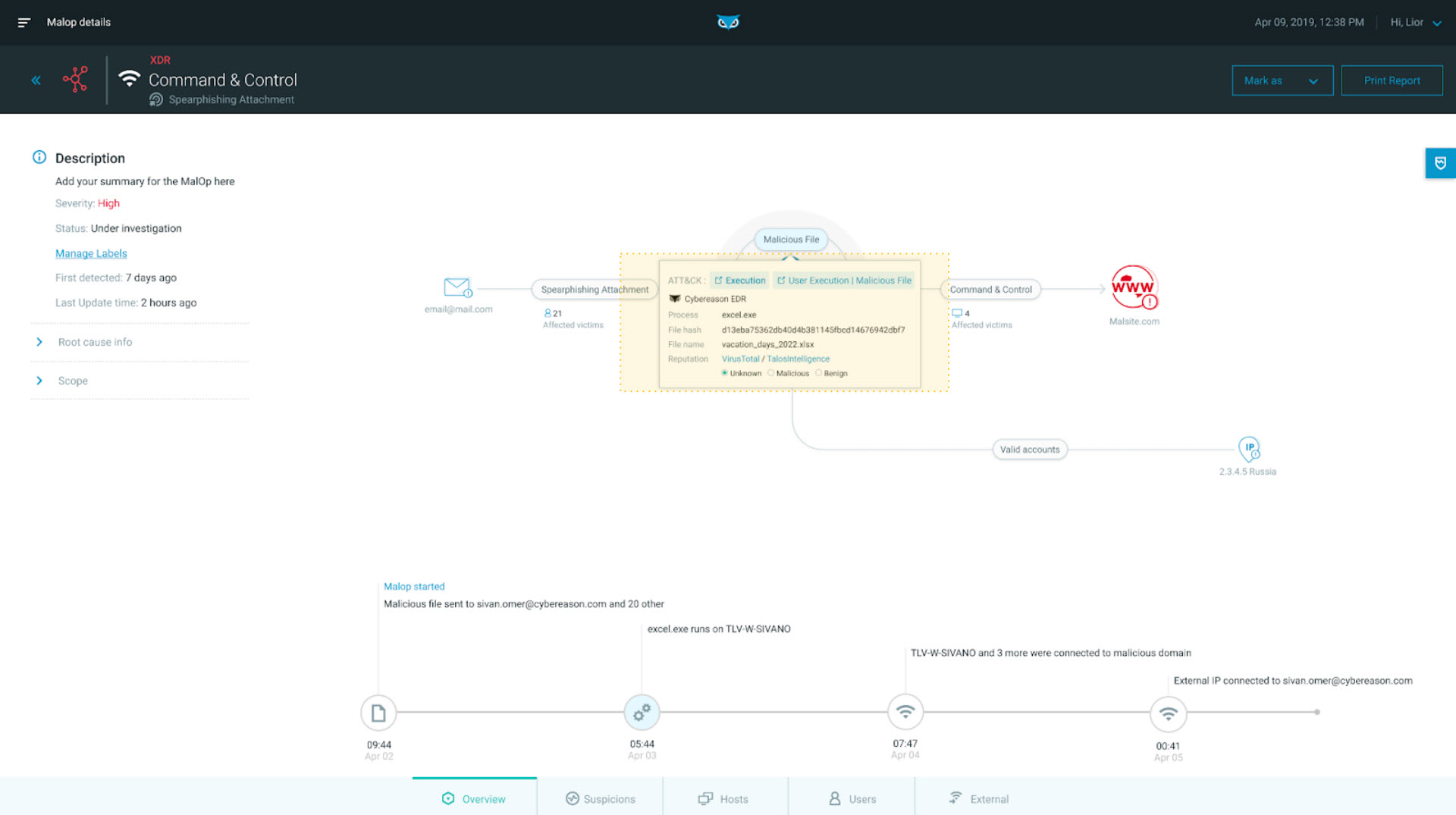
Correlations across assets as seen in the Cybereason XDR Platform
If there are any matches to threat intelligence sources, that is presented in the MalOp. The analyst can easily click on the source of the threat intelligence to get file reputation details on that hash and mark their findings.
A focus area for Cybereason XDR is centralizing response and remediation capabilities from within the platform. Each MalOp offers automated or guided one-click response actions that upskill analysts, improve accuracy, and ultimately bring a 10X improvement to mean time to respond (MTTR).
In the below screenshot, we see options to control and respond to the malicious attachment coming in from Microsoft Office 365:
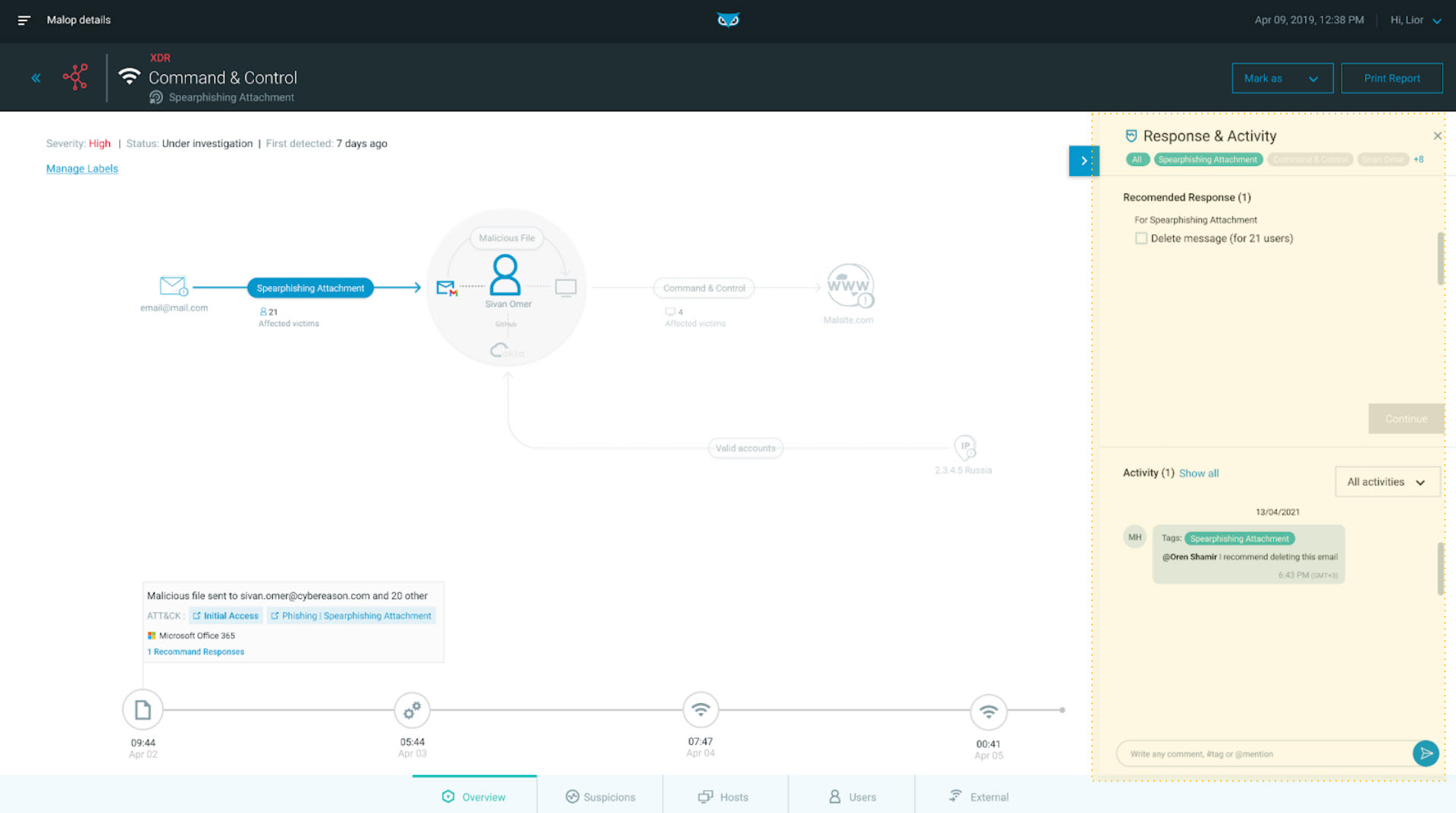
Response options as seen in the Cybereason XDR Platform
At the file level, we are able to deploy another set of response actions relevant to the malicious attachment:
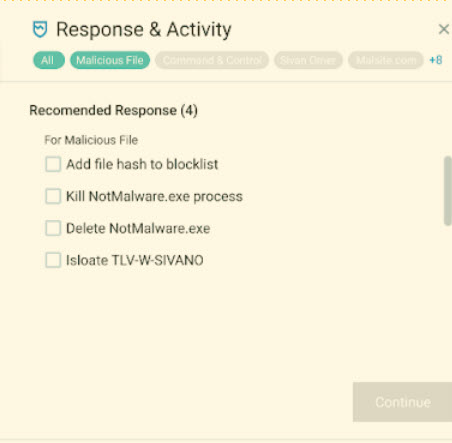
Lastly, the outbound network impact threat is neutralized with inline response actions:
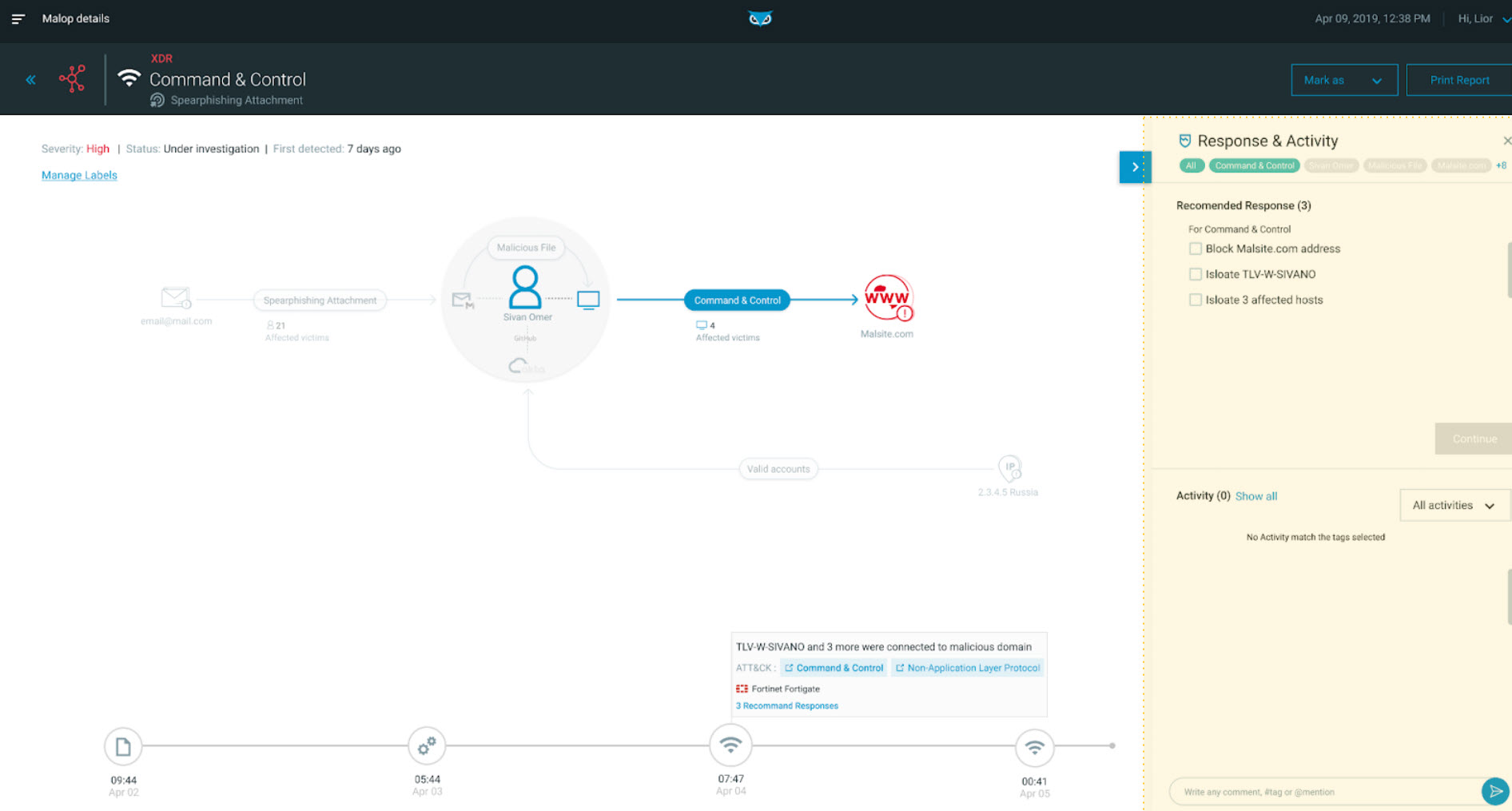
Remediation as seen in the Cybereason XDR Platform
Cybereason XDR moves an organization’s security posture from simply automating repetitive security tasks to a state of “detect, understand, and anticipate.” With direct integrations to meaningful security data across your environment, Cybereason XDR helps you predict areas of future risk so you can get ahead of your most probable security threats.
Cybereason is dedicated to teaming with Defenders to end cyber attacks from endpoints to the enterprise to everywhere. If you're a Cybereason customer, contact Customer Success to learn more about Cybereason XDR. If you're just starting your XDR journey, check out our XDR Toolkit, and schedule a demo to learn how your organization can benefit from an operation-centric approach to security.











