
Responding to Multi-Endpoint Threats with XDR
The Cybereason XDR Platform provides a unified view of your endpoints, allowing analysts to quickly remediate complex threats across multiple machines...

Dan Verton
When is an endpoint attack just an endpoint attack? In today’s world of advanced persistent threats and ransomware, an attack that stops at the endpoint is now a rare event.
That’s why it’s critical for security teams to be able to see the entire attack story, from root cause to likely next steps, and its impact across the complete enterprise environment. This is not possible with competing solutions on the market today.
For patchwork solutions masquerading as XDR platforms, subtle indicators of behavior and compromise—on and beyond the endpoint—are surfaced as multiple alerts that security teams must chase down and investigate across multiple consoles.
AI-driven Cybereason XDR is the industry’s first unified XDR solution that is operation-centric, predictive, and underpinned by guided and automated response capabilities. Let’s take a look at two very common attacks that defenders deal with every day to illustrate the benefit of Cybereason’s operation-centric approach: A 10X productivity boost from unified investigations.
Our story starts with an endpoint attack leveraging MimiKatz to harvest credentials. While MimiKatz is traditionally used to steal Windows account logins and passwords, attackers are also hunting for email, cloud, and other credentials to gain expanded access and get to sensitive data:
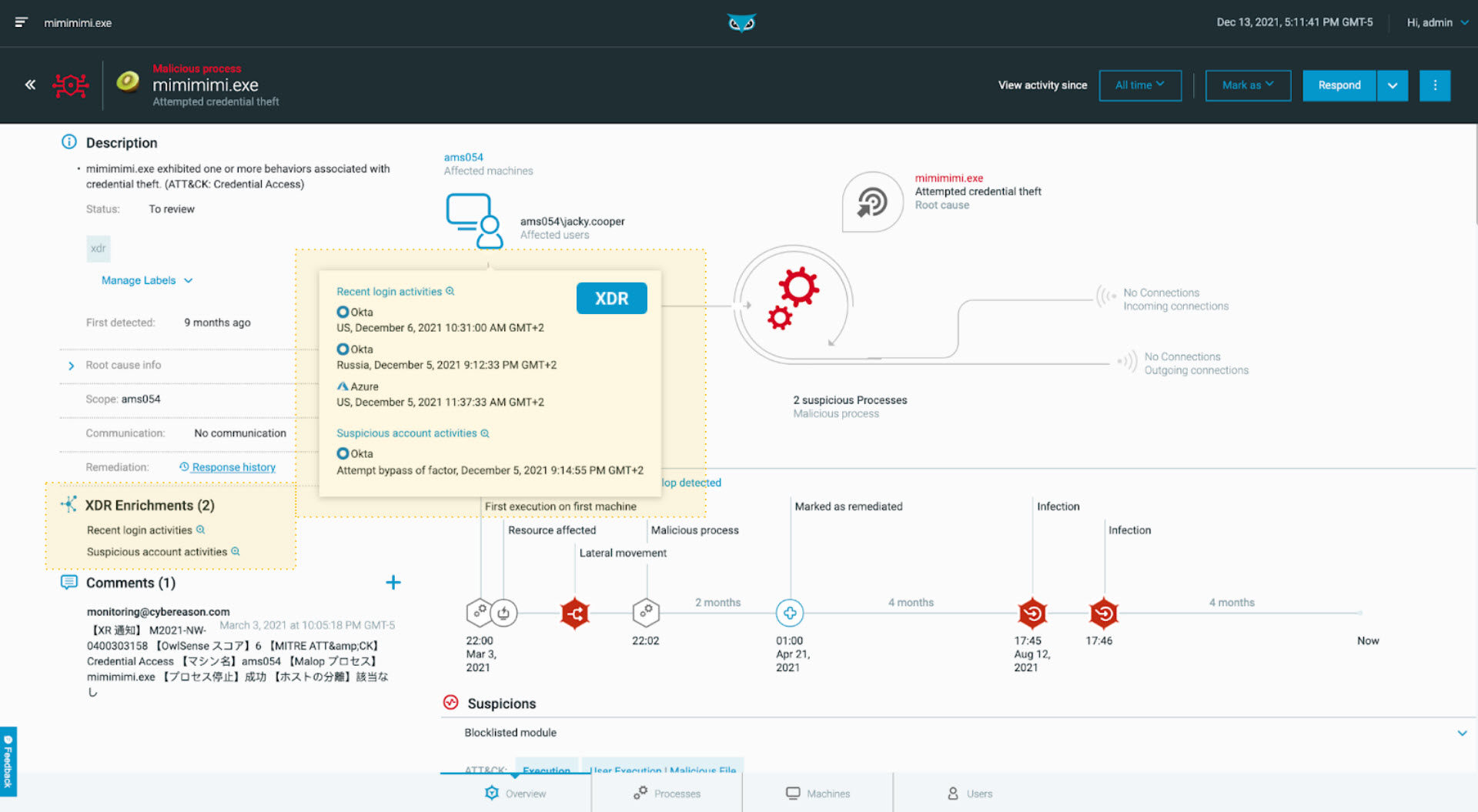 Cybereason MalOp showing the asset/user: ams054/jacky.cooper being targeted for credential theft
Cybereason MalOp showing the asset/user: ams054/jacky.cooper being targeted for credential theft
Cybereason XDR’s integration with Okta helps Defenders immediately understand a broader context—specifically where and when Jacky authenticated with her broader identity. Under “Suspicious account activities”, we see that Okta detected a potential attempt to bypass multi-factor authentication (MFA), which further helps analysts corroborate the malicious activity and stitch the larger story together.
"There's correlation through Okta, for example, and other events relating to the same user. What the system is saying is there is something here worthwhile to look at," said Yonatan Striem-Amit, Cybereason CTO and Co-Founder, during a presentation on the future of detection and response at DefenderCon.
Cybereason XDR enables defenders to explore across endpoint data, workspace and identity, network, and cloud events in one cohesive story fabric. From the MalOp, one click brings you to Investigations, where you can visualize the exact query used to retrieve this information:
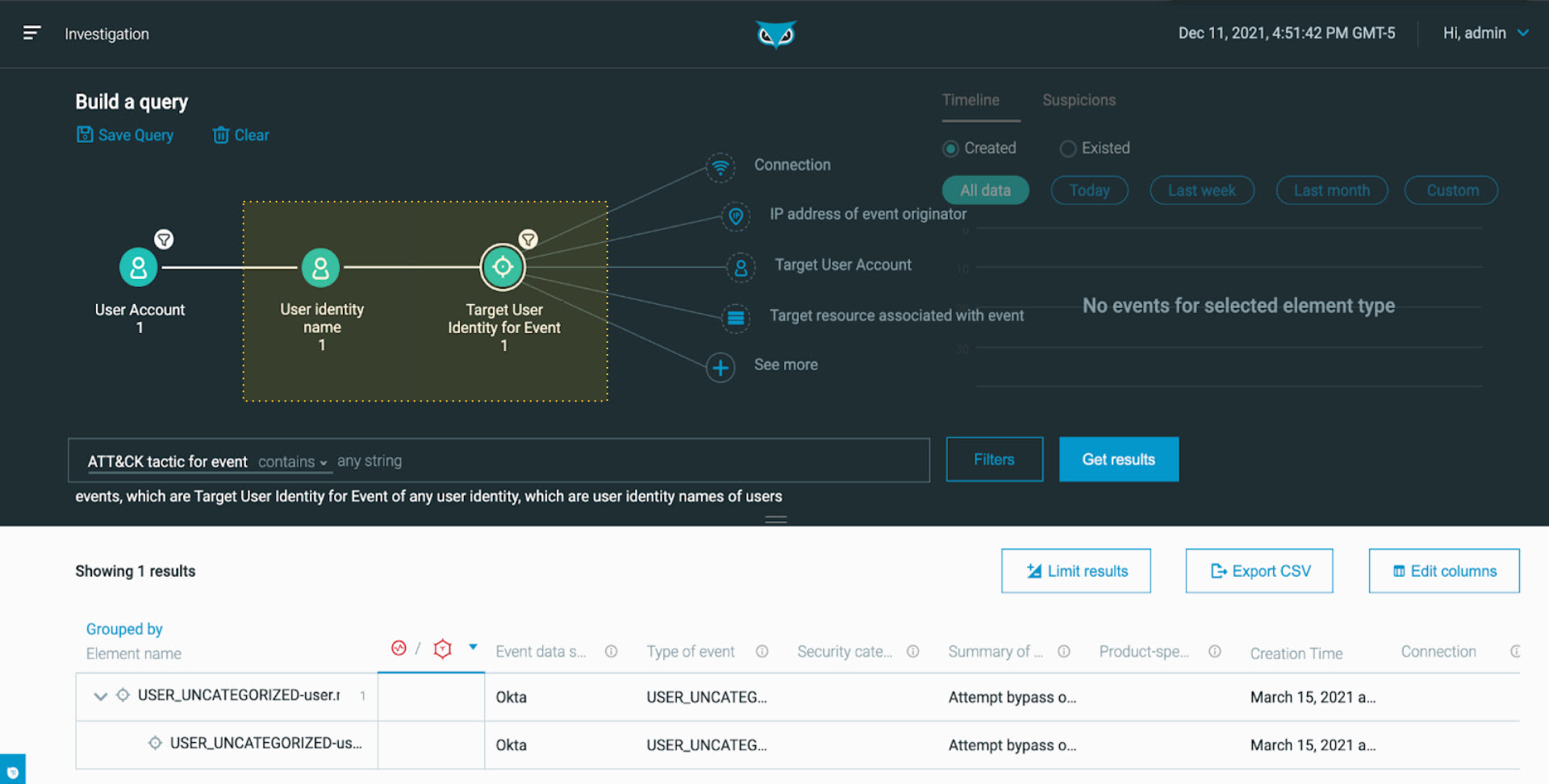 Searching for results related to the identity connected to the suspicious activity as seen in the Cybereason XDR Platform
Searching for results related to the identity connected to the suspicious activity as seen in the Cybereason XDR Platform
If we dig deeper into the events metadata (see below image), we can see the host vendor, the data source, method of authentication, source address, and the security result, including category, summary, and mapping to MITRE ATT&CK.
If we trace the target user account, we can determine the user to be Jacky Cooper, who works in Finance and is the owner of the endpoint and the SSO account:
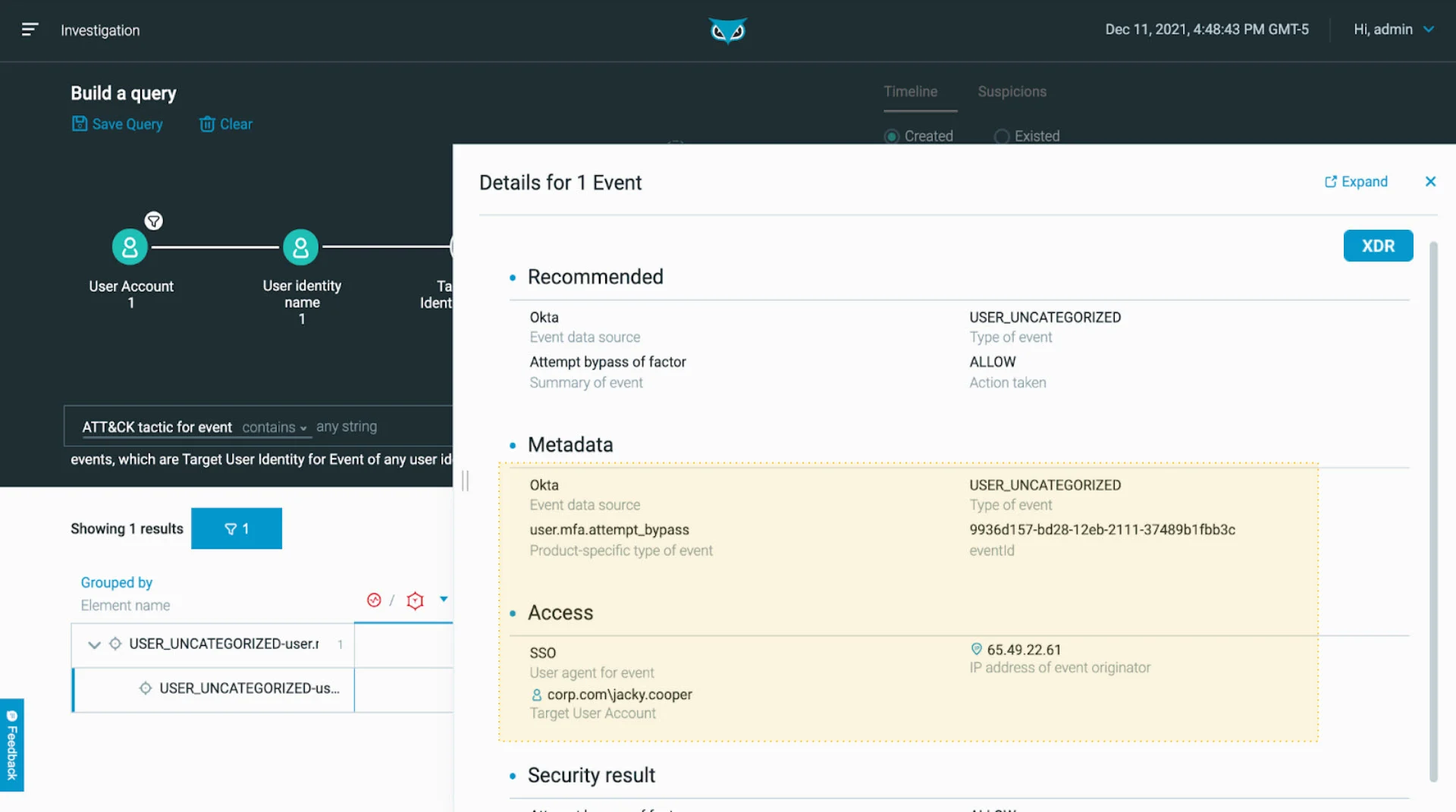
Events Metadata as seen in the Cybereason XDR Platform
From there, we can dig even deeper highlighting the recent login activities for all accounts belonging to the identity of Jacky Cooper to help better validate and quickly corroborate an identity theft.
In the below example, she has interacted with Office 365 and Microsoft Azure. Cybereason XDR produces a complete correlation map across the local/domain user, corporate identity, cloud access, and across networks, giving analysts actionable visibility and peace of mind:
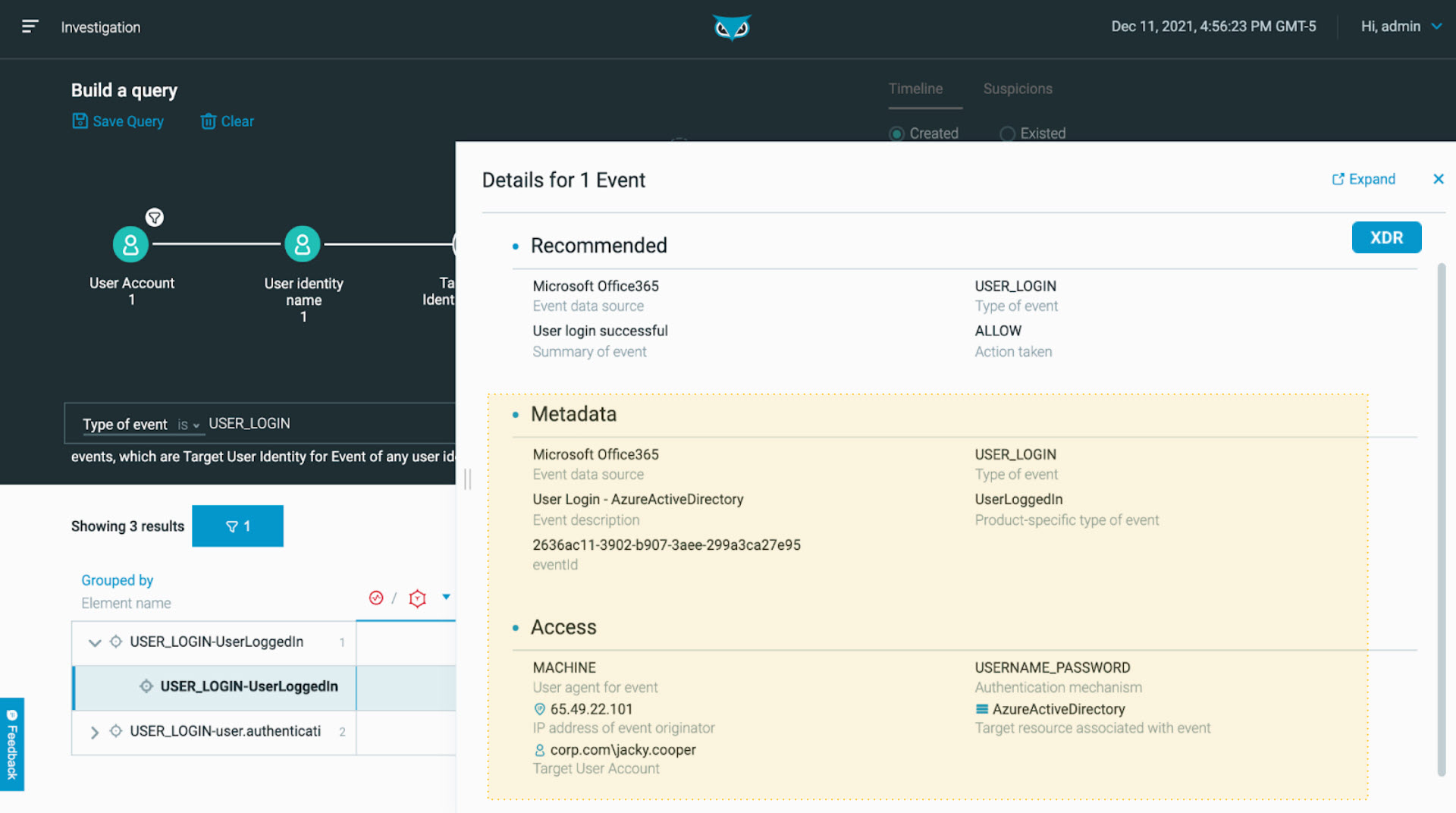
Telemetry correlations as seen in the Cybereason XDR Platform
“Imagine the world before XDR when you would think you have an endpoint problem and your team would be directed to go and respond to the endpoint problem, oftentimes completely missing the broader picture,” said Striem-Amit. “Now you have it in one cohesive experience. It's a single flow to see how an endpoint-based attack impacts your broader world.”
This common scenario starts with Cybereason identifying a malicious process running on the endpoint “desktop-21su9fn” under local user account niles.peterson:
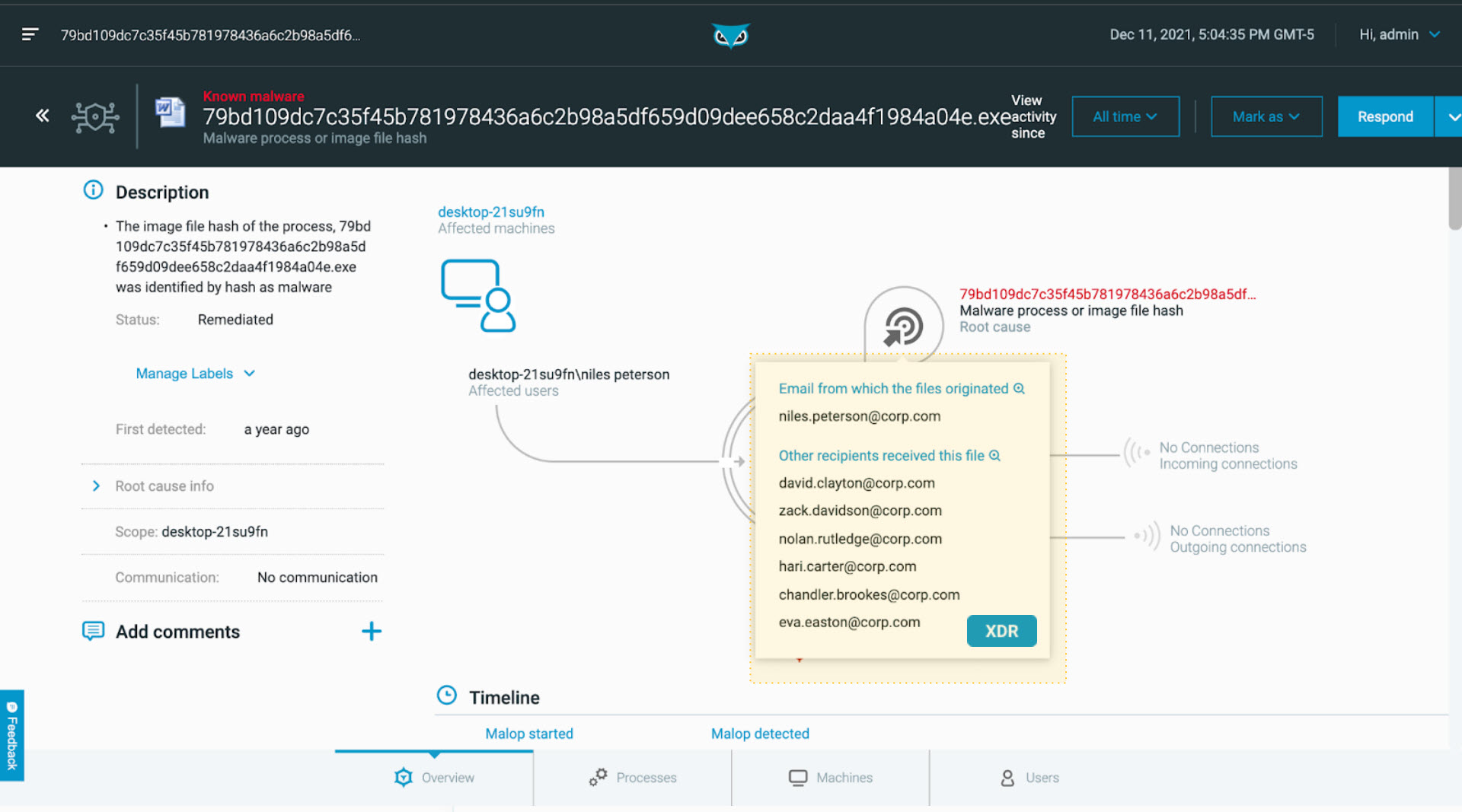
Malicious process detection as seen in the Cybereason XDR Platform
With the help of the identity management capabilities of Cybereason XDR, we automatically connect the local account and machine with its owner’s broader identities, including email. Combining this with Microsoft 365, Google Workspace, and other email data, XDR can proactively surface email activity containing attachments with the same detected file hash. This enables the security analyst to quickly conclude that the root cause for this malicious activity was a phishing email that included the malicious Word document.
By surfacing all of the other recipients that received the same malicious file, analysts can quickly understand the broader attack scope and expedite a fast and accurate response.
In Investigations, we can determine who it came from, the name of the attachment, subject line, and more:
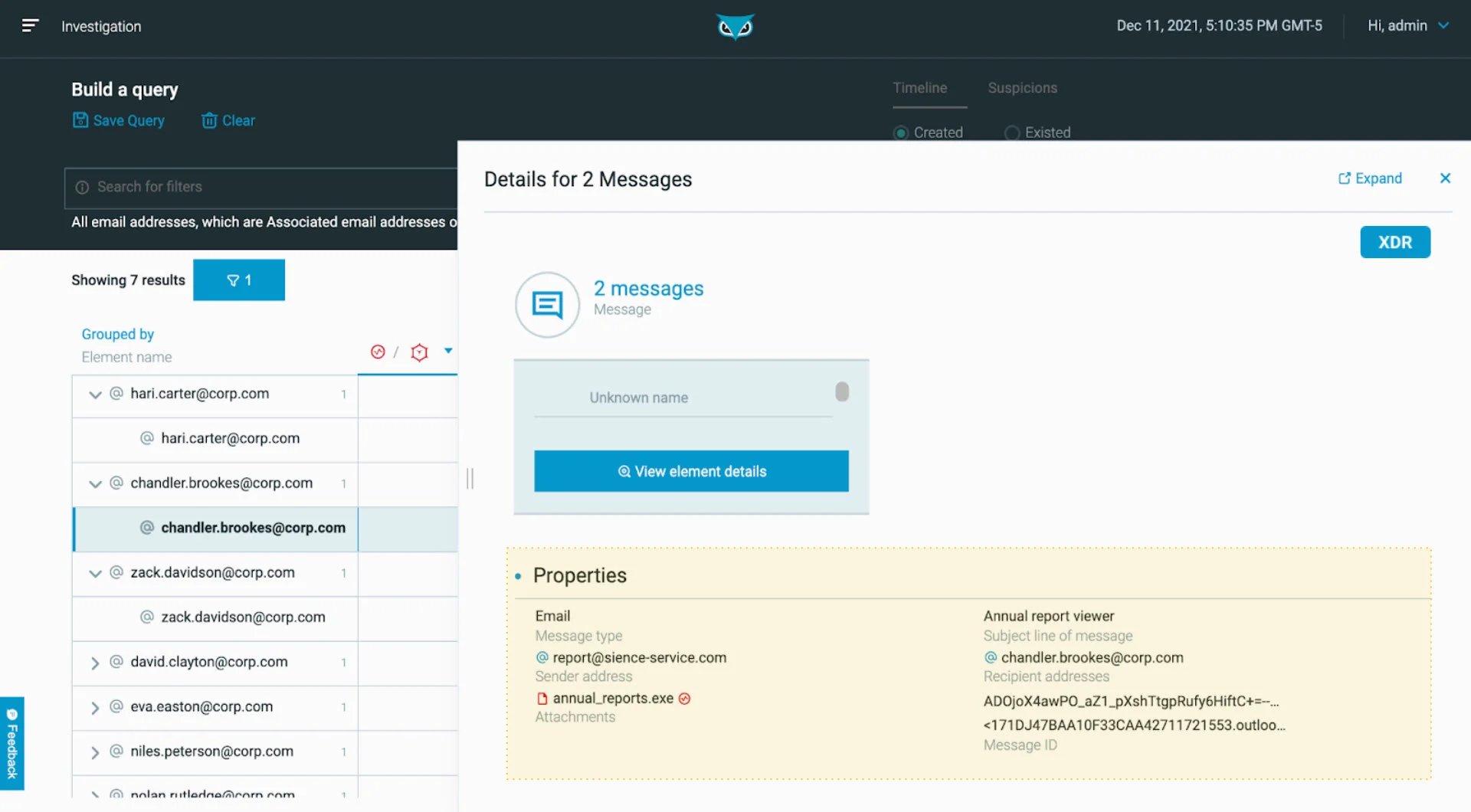
Identifying root cause as seen in the Cybereason XDR Platform
“The main thing here is now you understand that you don't have an endpoint attack, you have an enterprise attack going after you,” said Striem-Amit.

Dan Verton is Director of Content Marketing at Cybereason. Dan has 30 years of experience as a former intelligence officer and journalist. He is the 2003 first-place recipient of the Jesse H. Neal National Business Journalism Award for Best News Reporting – the nation’s highest award for tech trade journalism and is the author of the groundbreaking work, Black Ice: The Invisible Threat of Cyber-Terrorism (McGraw-Hill, 2003). He most recently served as an intelligence advisor and co-author of a nationwide TSA anti-terrorism awareness training program.
All Posts by Dan Verton
The Cybereason XDR Platform provides a unified view of your endpoints, allowing analysts to quickly remediate complex threats across multiple machines...

Cybereason XDR delivers an operation-centric approach to security that enables analysts of all skill levels to quickly understand an attack without crafting complicated queries...

The Cybereason XDR Platform provides a unified view of your endpoints, allowing analysts to quickly remediate complex threats across multiple machines...

Cybereason XDR delivers an operation-centric approach to security that enables analysts of all skill levels to quickly understand an attack without crafting complicated queries...
Get the latest research, expert insights, and security industry news.
Subscribe