As we hurtle towards the end of 2020, the only constant we can come to expect is change itself. We’re pressed on two sides: our corporate IT environments continue to change, and attackers are more persistent and explosive than ever. While it is possible to secure a modern, distributed, multi-cloud environment, it feels out of reach for most security teams. Between data lake management, detection and rules tuning, and repetitive response actions, it’s challenging to architect, build, and maintain -- and of course prove that it’s making the business safer.
Extended detection and response, known as XDR, is a promising technology that directly supports finding and stopping threats. With a flexible data approach, XDR can (1) detect unknown threats that weave between data silos, and (2) accelerate investigation and response with automation workflows. This sounds great, but how real is this, and what does the security community think?
A new report from ESG, the Impact of XDR on the Modern SOC, surveyed 388 IT and cybersecurity professionals from organizations in the United States and Canada responsible for evaluating, purchasing, and managing detection and response strategies, processes, and technologies. The report focused on the perception and value of XDR, and certainly reveals a number of interesting insights around how teams are prioritizing investment against attacks.
Get your free copy of the report here:

3 Notable trends derived from the research
1) In the full report, we learn which tools are considered effective for threat detection and response across SIEM, EDR, NDR, and threat intelligence. For example, many security teams rate their SIEM as effective, but it’s too costly, maintenance is a challenge and is less effective against unknown threats.

ESG notes, “Security teams must aggregate and correlate signals from multiple security controls to investigate, understand, and respond before damage is done. With XDR promising to automate this process using a single solution, many think that XDR can become a new centralized management hub for security operations.”

2) Cloud and containers are high-impact technologies that require specialized protection, detection, and response strategies. Many teams are considering XDR for their ability to protect multi-cloud and user identities, a common gap in threat monitoring today. Ensure your XDR vendor aligns well with your longer term IT strategy.
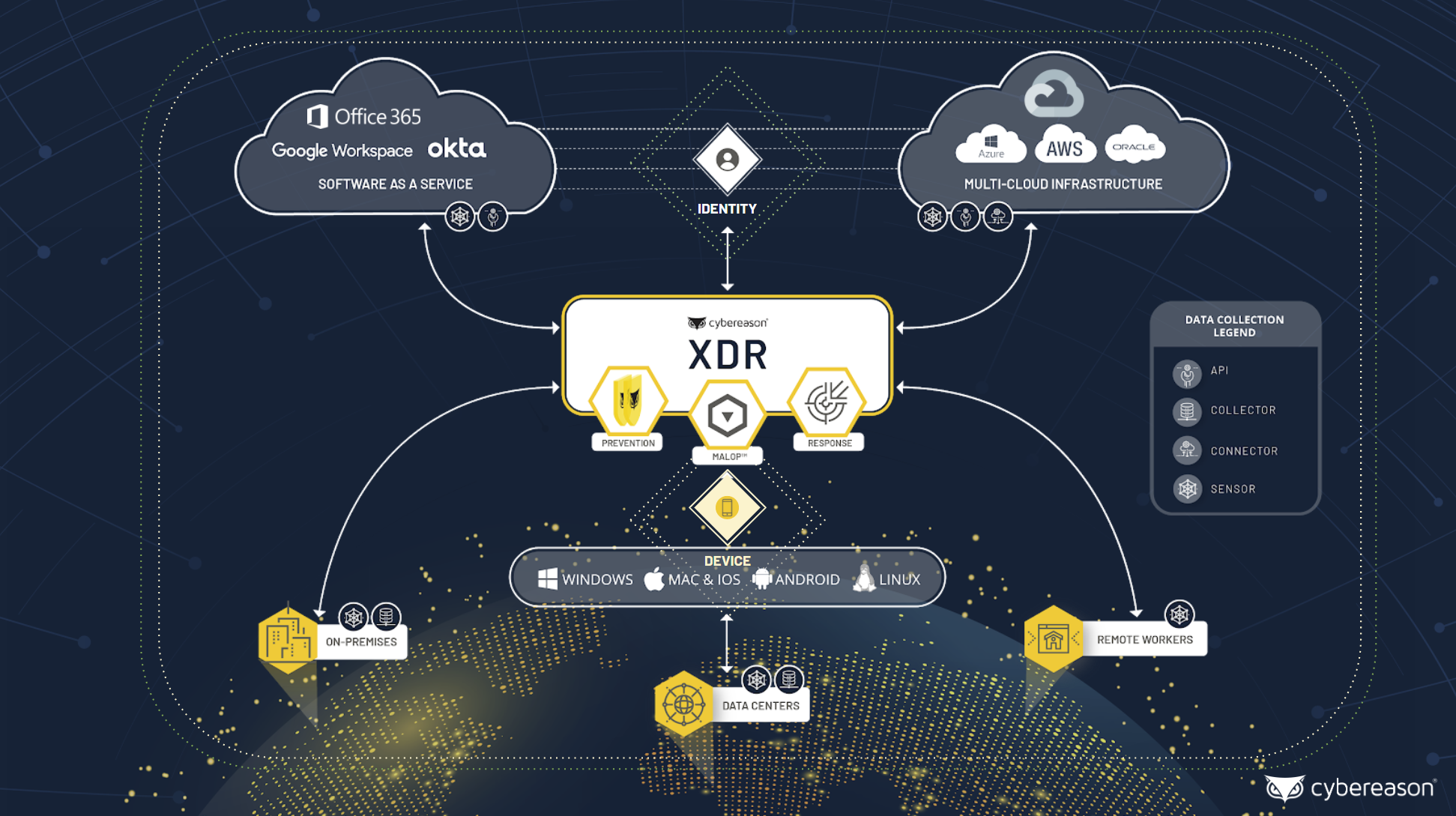
At Cybereason, we’ve focused on identity and cloud in order to support zero trust deployments and find credential-based attacks. As Cybereason supports both older operating systems and on-premises deployments, our XDR is well-suited for transitions while staying future-ready.

3) If you’ve been following our Nocturnus research on the Kimsuky KGH Spyware Suite, Molerats Espionage Malware, or simply the headlines with SolarWinds Orion SUNBURST, it’s clear that adversaries are investing in detection evasion, running multi-stage campaigns, and can almost assuredly break through a company’s prevention perimeter.
This is where user behavior analytics (UBA) and security orchestration and automation (SOAR) help, but those modules typically have been only accessible to mature teams with a heavy data lake investment.
At Cybereason, our focus is on finding and stopping the malicious operation. This is why we present Malops (malicious operations), not alerts:
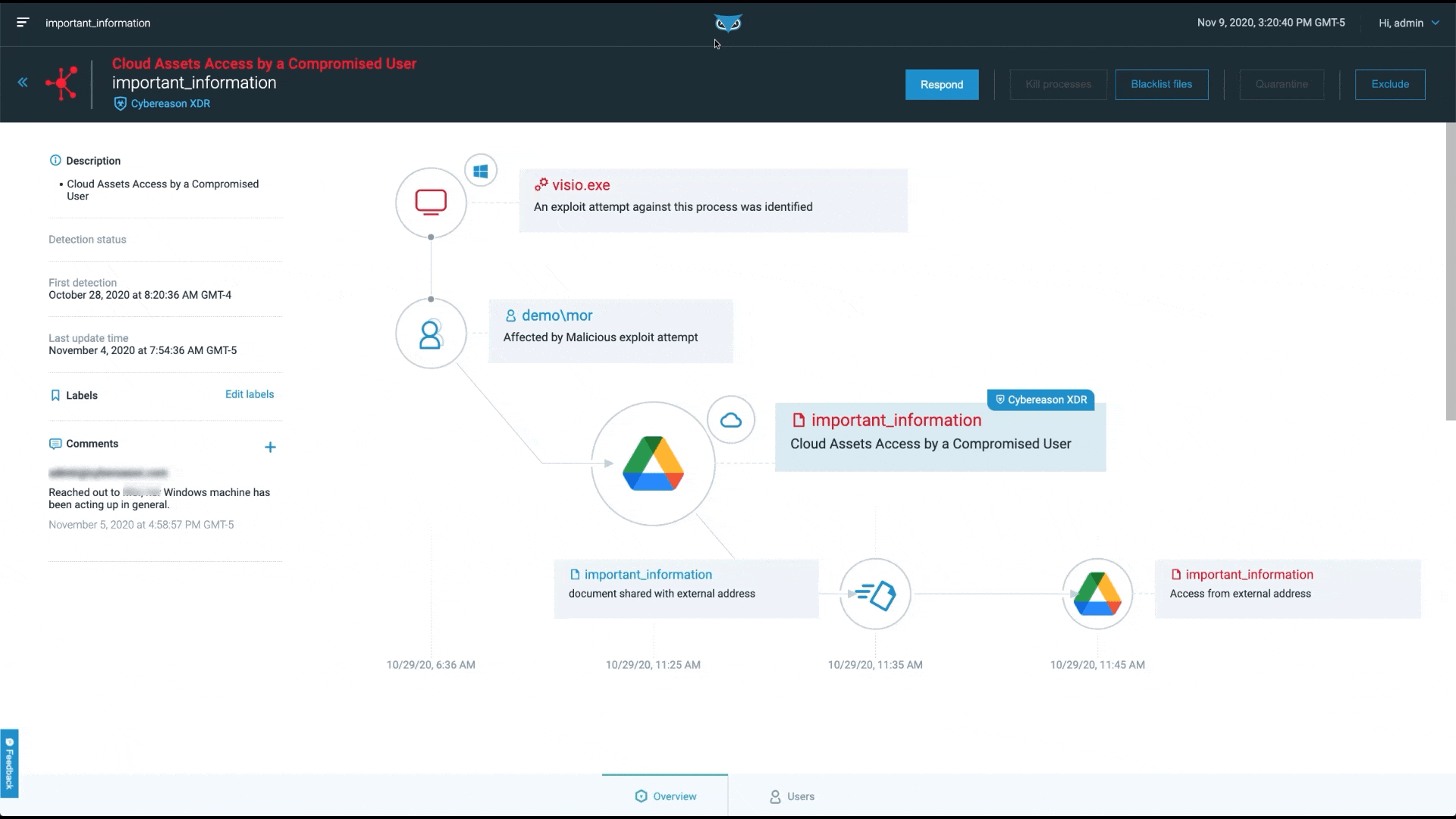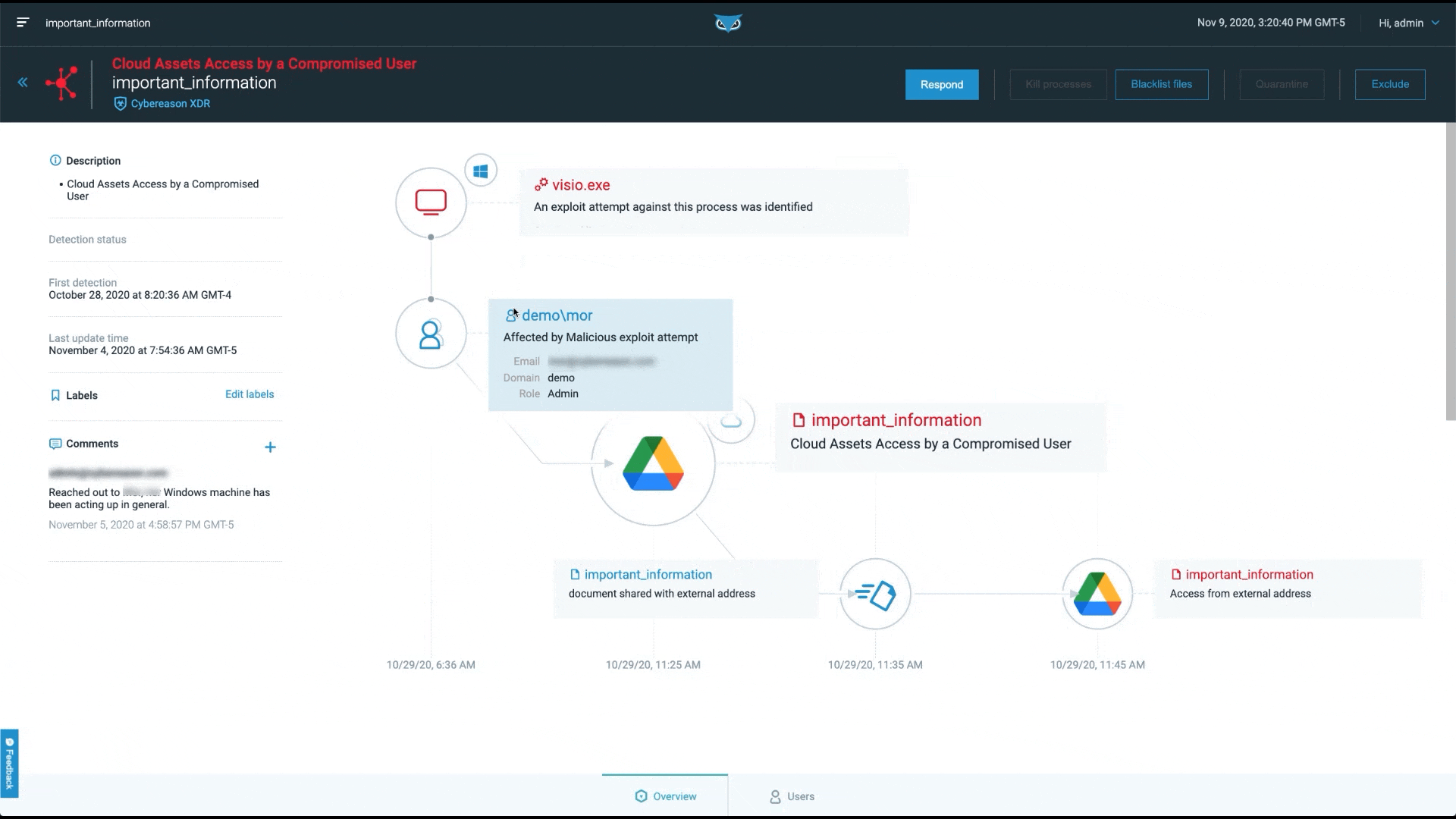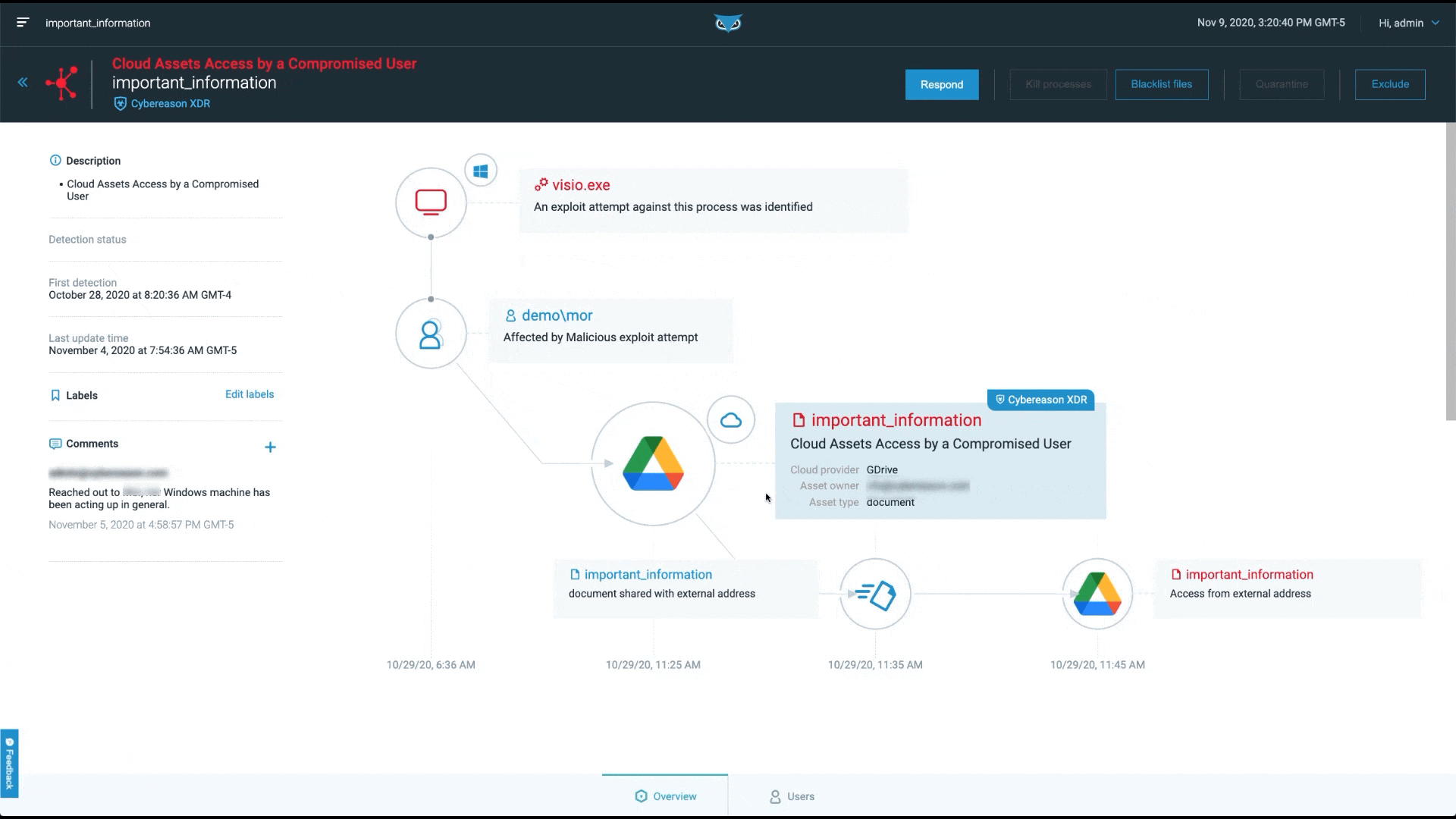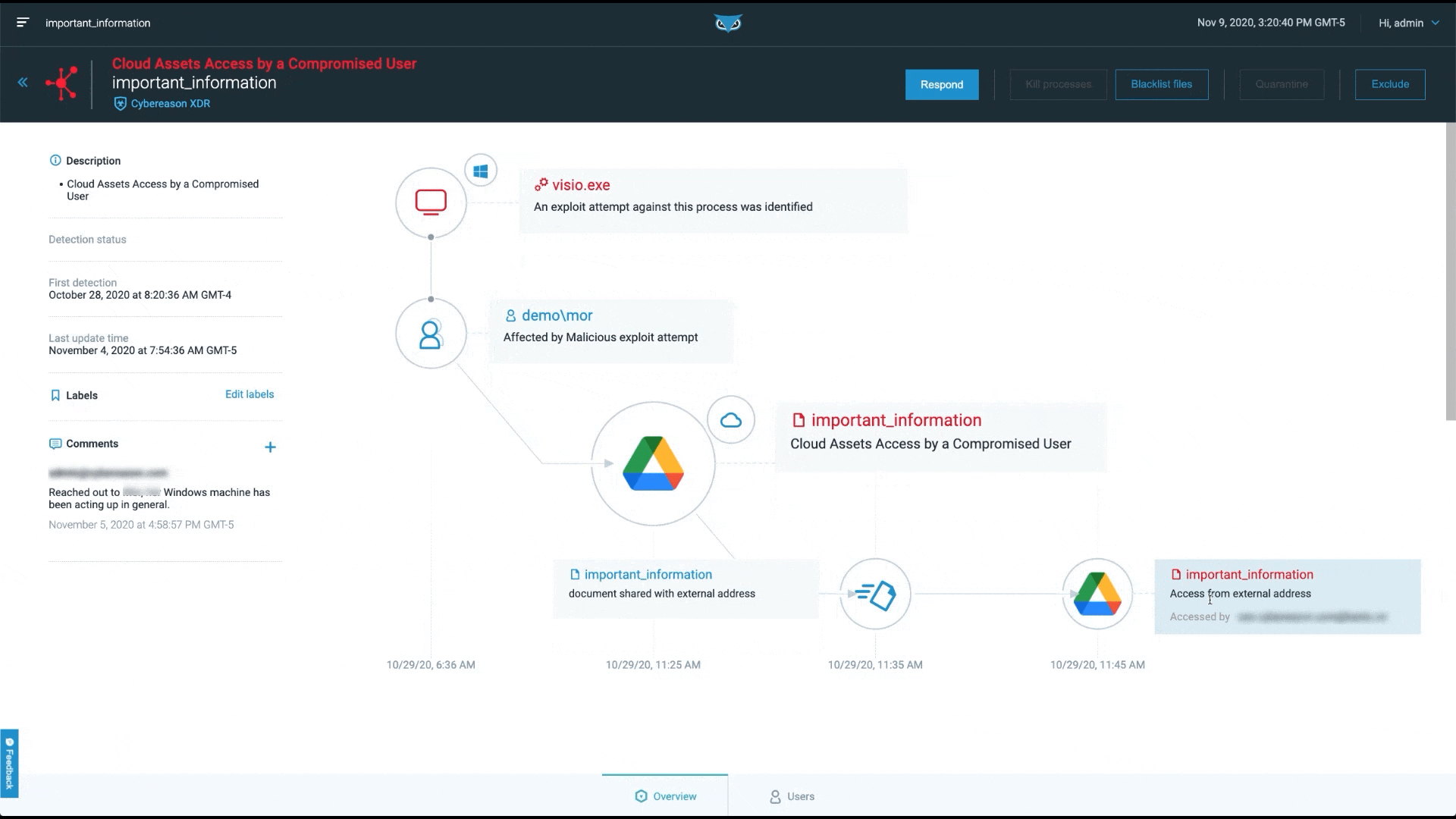
ESG notes, “In response, security teams must aggregate and correlate signals from multiple security controls to investigate, understand, and respond before damage is done. XDR promises to automate this process, exposing complex threats leading to improved response times.”
Getting Started with XDR
While there are a variety of expectations for XDR, the new ESG report suggests that teams are looking to simplify and streamline SOC and security team activities with an integrated XDR solution. Many implied that they would consider replacing core cybersecurity technologies, such as EDR, NDR, SIEM, and SOAR.
That transition will take time, though, as companies assess the efficacy of XDR and develop a threat detection and response strategy that takes business objectives and SOC best practices into consideration.











