Update - 10:00am ET 3/23 - from Okta CSO David Bradbury (source):
"After a thorough analysis of these claims, we have concluded that a small percentage of customers – approximately 2.5% – have potentially been impacted and whose data may have been viewed or acted upon. We have identified those customers and are contacting them directly. If you are an Okta customer and were impacted, we have already reached out directly by email. We are sharing this interim update, consistent with our values of customer success, integrity, and transparency."
Update - 6:00pm ET 3/22 - from Okta CSO David Bradbury (source):
"The Okta service has not been breached and remains fully operational. There are no corrective actions that need to be taken by our customers... The potential impact to Okta customers is limited to the access that support engineers have. These engineers are unable to create or delete users, or download customer databases. Support engineers do have access to limited data - for example, Jira tickets and lists of users - that were seen in the screenshots. Support engineers are also able to facilitate the resetting of passwords and multi-factor authentication factors for users, but are unable to obtain those passwords. We are actively continuing our investigation, including identifying and contacting those customers that may have been impacted. There is no impact to Auth0 customers, and there is no impact to HIPAA and FedRAMP customers."
-------------------------------------------------------------------------------------------------
Authentication platform Okta is reportedly investigating a potential breach after threat actors under the moniker Lapsus$ posted screenshots allegedly showing they had gained access to the company’s internal environment. If confirmed, the attack could put the security of Okta’s customers at risk.
While the attackers stated that they did not compromise any backend systems at Okta, just admin accounts, Cybereason advises users of Okta solutions to take extra precautions until more is understood about the attack.
Officials from Okta deny that the posted screenshots were from a recent compromise, stating that they believe they were from an isolated breach incident that was detected and mitigated back in January.
“In late January 2022, Okta detected an attempt to compromise the account of a third party customer support engineer working for one of our subprocessors. The matter was investigated and contained by the subprocessor,” Okta Chief Executive Officer Todd McKinnon stated.
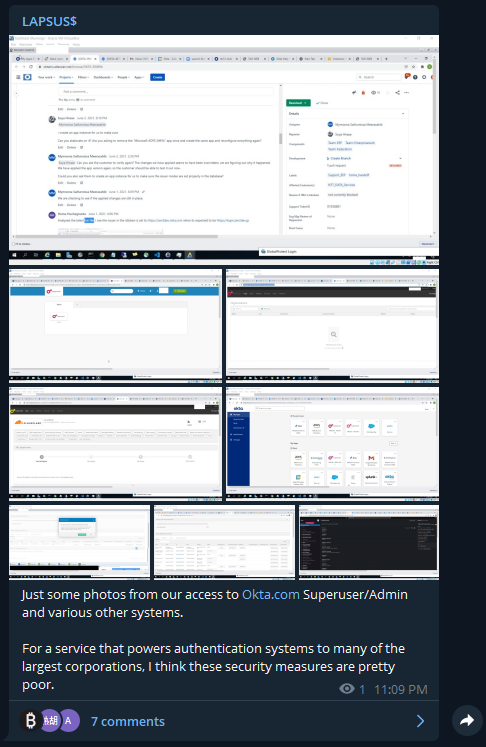 Sample screenshot from Lapsus$ group (source)
Sample screenshot from Lapsus$ group (source)
“We believe the screenshots shared online are connected to this January event. Based on our investigation to date, there is no evidence of ongoing malicious activity beyond the activity detected in January.”
Potential Risks
“We give credit for Okta that their passwords are hashed and properly salted, which limits the value of rainbow table-based attacks, and regular offline brute-forcing is still an issue with most passwords anyway,” said Cybereason Co-founder and CTO Yonatan Striem Amit.
“The real risk is from persistent administrative access, the disabling of 2FA, and theft of keys that allow token generation. If one steals Okta’s cryptographic keys, one could forge logon sessions and walk in as if already authenticated, as there’s no online verification when someone issues a valid JWT–this means the potential here is really as bad or worse than the RSA theft.”
News of the alleged compromise at Okta comes on the heels of President Biden’s announcement about cybersecurity threats, warning US companies that they should take extra care to protect their networks and “harden your cyber defenses immediately” in the face of increased risk stemming from the Russian invasion of Ukraine.
“If the breach is what the Lapsus$ group asserts, in terms of impact, this is potentially as big or bigger today as RSA was a decade ago, as it looks like they have hashes of passwords for certain accounts, and that means rainbow tabling (not replay) is a possibility to get passwords,” said Cybereason CSO Sam Curry.
“While 2FA helps mitigate this, the big problem is if superusers and admins are compromised–they can create accounts and override 2FA.”
Who are the Threat Actors from Lapsus$?
Lapsus$ is a more recently documented threat actor observed to be operating in Latin America, and is the threat actor alleged to have recently compromised graphics processing manufacturer nVidia and electronics giant Samsung, and there are reports that they may have also compromised Microsoft and stolen source code from the company.
“In most cases when dealing with a ransomware group, they follow a modus operandi with an established business model. Lapsus$ feels more like a startup with a team of talented offensive security folks who are looking at targets from a more opportunistic point of view, with their approach to monetization shifting depending on the specific target,” said Cybereason Director, Security Strategy Ken Westin.
“Lapsus$ is focused more on data exfiltration for extortion as opposed to both encryption and exfiltration like other ransomware threat actors, which may make evading common security controls easier for this group. There is no indication to date that they are affiliated with Russian actors. However, as their goal appears to be financial, it wouldn't be a leap to consider that Russian actors may buy access to organizations who they compromise, or data from the group in the future.”
Cybereason will continue to monitor the situation and provide our customers with updates as they become available.
Cybereason is dedicated to teaming with Defenders to end attacks on the endpoint, across enterprise, to everywhere the battle is taking place. Learn more about Cybereason AI-driven XDR here or schedule a demo today to learn how your organization can benefit from an operation-centric approach to security.






