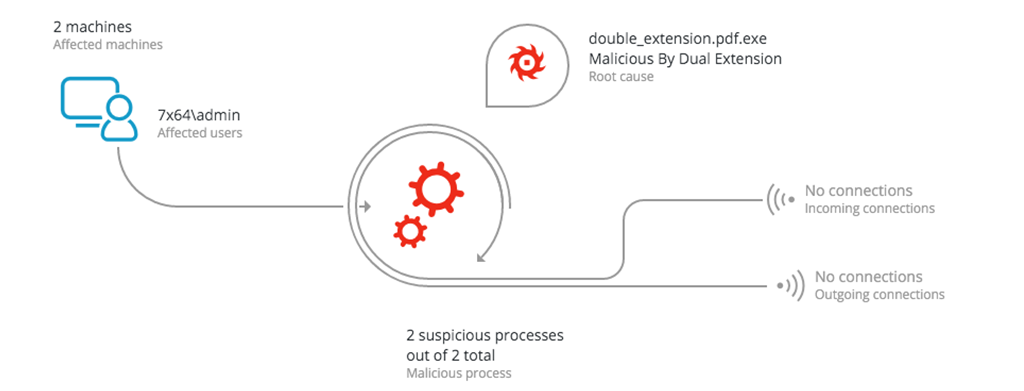
Data visualization may not be a key consideration in enterprise security, but poorly displayed threat information can lead to analysts missing critical details.
“Visualization is key to being able to draw things out you might not otherwise intuitively see or not be able to see at all,” said Forrester analyst Rick Holland, adding that better data visualization leads to the discovery of more threats and boosts a security team’s effectiveness.
The enterprise security space can learn a lot from consumer technology, especially when it comes to visualizing threat information in a way that’s useful for security analysts, he said.
Current security products are cumbersome to use and fall short in the display category, said Holland during a webinar on selecting a next-generation endpoint system Forrester co-hosted with Cybereason.
Android devices and iPhones, on the other hand, are “intuitive and easy to use. We need that kind of consumer experience to work its way up the enterprise security stacks,” Holland said
If threat information is displayed in a way that’s too complex to understand, analysts may overlook important information, he said.
“Visualization is key to being able to draw things out you might not otherwise intuitively see or not be able to see at all,” Holland said, adding that better visualization leads to the discovery of more threats and boosts a security team’s effectiveness.
The security tools security analysts are currently using fall short at presenting threat data, according to Holland.
Automated malware analysis reports, for instance, display information in a manner that’s “just painful to look at,” Holland said.
This proves particularly problematic for the people who are using these reports. Many of them aren’t “malware people” or reverse engineers who understand how to leverage the threat information presented in the report, he said.
Reports generated by sandboxes are another source of pain for security professionals. The information they display doesn’t offer a clear view on how the malware is operating in an IT environment.
“Is there a way to have a timeline that shows how the malware is executing instead of this ugly display that organizations have?” Holland said.
Not all analysts are well-versed in using administration tools
Weak visualization capabilities becomes an even greater issue when factoring in the security talent shortage, Holland said. Companies are hiring junior analysts who do not possess the skills to use common administration tools, like the command line interface.
“It’s important to have this capability for advanced users. But if you look at the resource staffing problems we have, there are people who just don’t have the skills. They can be intimidated by the command line,” Holland said.
This is the fifth and final blog post in a series that looks at the five points a company should consider when evaluating next-generation endpoint security products. Earlier posts gave an overview of each point, talked about the importance of using a product with a small footprint, how prevention must be done in tandem with detection and the rise the rise of behavioral analysis detection.