
How Cybereason Enables the U.K. to Defend Against Cyberattacks
The second installment of our five-part series outlining how Cybereason XDR maps to each of the objectives in the U.K. Government Cybersecurity Strategy...

Karishma Asthana
Although every organization’s journey to achieving Zero Trust will be different, there are two factors that will determine your ability to maintain a system of trust by verification on a continuous basis: Data and speed.
Reminiscent of our calculus courses, it’s important to be able to “show our work” behind our trust decisions. However, showing the work that went into your decision as to why you believe all users and activities in your environment are legitimate is quite a large undertaking.
It requires not only real-time information about the users and activities in your environment but also context around these large volumes of data to be able to determine if what you are seeing is legitimate or malicious. The longer these decisions take, the more vulnerable your organization becomes.
The Cybereason analytics and processing engine enables the fastest time to convict based on our ability to process 1.4 petabytes of data per day in real-time. The Cybereason XDR Platform Platform backend is powered by Google Cloud's Cloud, further supporting the speed and scale of our data-processing engines without filtering data like competing offerings . We know how important it is to show all your work.
The five pillars of Zero Trust that necessitate verification are device, identity, network, application workload and data. Historically, SOC teams have struggled to gain rapid insights and answers from the vast amount of telemetry data produced by the ever-increasing number of security tools deployed throughout their environment.
The correlation capabilities in the Cybereason MalOp™ (malicious operations) Detection Engine work to intelligently bridge telemetry among these five pillars, saving organizations from wasted time and resources spent on inefficient triage and investigations:
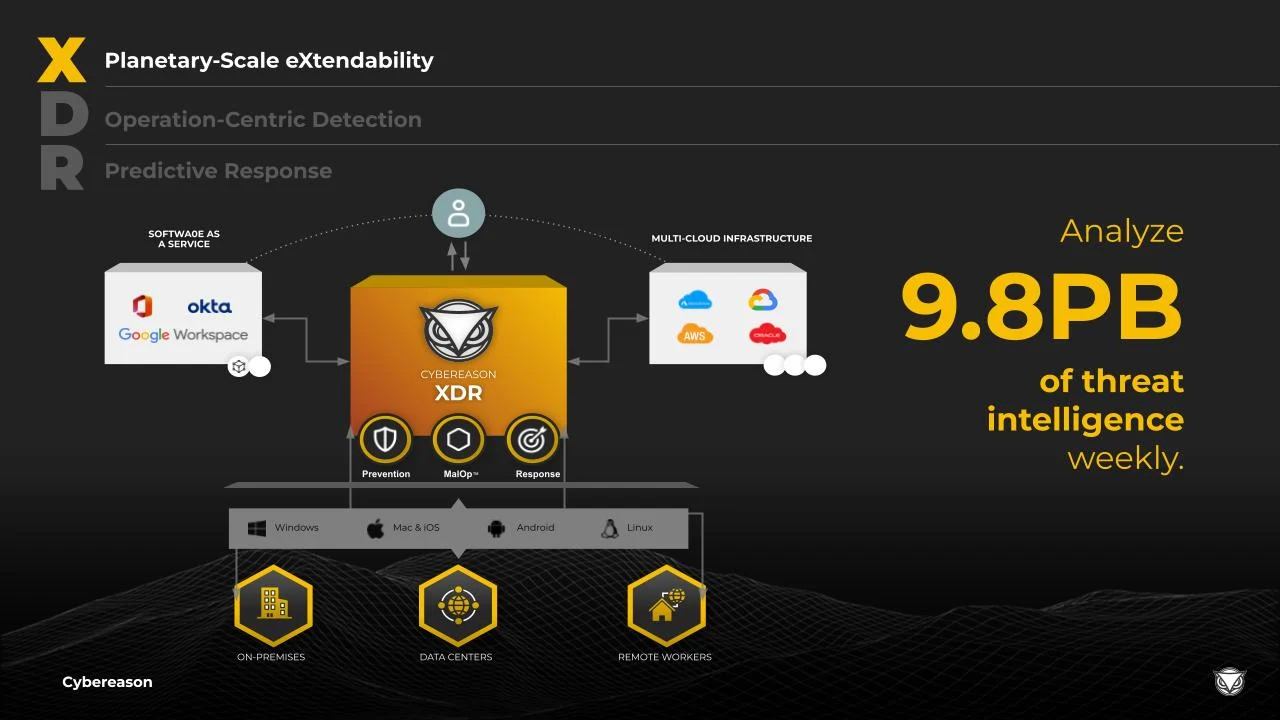 AI-driven Cybereason XDR combines the power of the MalOp™ analyzing more than 23 trillion security events per week with Google Cloud’s unrivaled ability to ingest and normalize petabytes of data
AI-driven Cybereason XDR combines the power of the MalOp™ analyzing more than 23 trillion security events per week with Google Cloud’s unrivaled ability to ingest and normalize petabytes of data
As can be seen from this graphic, there is a painstaking methodology to developing a MalOp detection, meaning that we do the work required to trust all legitimate entities within an environment. The Cybereason XDR Platform takes in raw data, or Facts, from endpoints and beyond and sends all of it over to the detection servers.
Facts include the properties of different activities on the machine on which a sensor is installed, including (but not limited to):
The MalOp Detection Engine correlates Facts across all machines and enriches the analysis with artificial intelligence, machine learning, behavioral analysis and information from threat intelligence sources.
These correlations are then mapped into Evidence or Suspicions, the next levels of the conviction pyramid, to explain patterns of behavior on the machines in your organization.
Evidence describes patterns of behaviors that the Cybereason XDR Platform detects on a machine. The MalOp Detection Engine generates a Suspicion when an individual activity is potentially malicious, or when several pieces of Evidence, taken together, might represent malicious activity.
When evidence and/or suspicions reflect a confirmed pattern of malicious behavior, the Cybereason platform deems the activity a MalOp.
Unlike less capable XDR platforms that work from limited data sets because of data filtering, Cybereason XDR supports Zero Trust by leveraging all of your security data. When you apply arbitrary, smart or statistical filtering of data, you will inevitably introduce blind spots into your system. For SOC teams, that means you are giving adversaries an avenue to exploit.
The truly smart approach to data filtering is to not filter data at all. Cybereason XDR collects every piece of data, processes every piece of data, and gives that data to analysts and threat hunters in real-time.
We do not duplicate activity with a SIEM; we are a primary recording mechanism designed to take in behavioral data. For Zero Trust to work, it’s important to show all of your work. And that means analyzing all of your data in time to detect and prevent an attack.
Cybereason is dedicated to teaming with defenders to end attacks on the endpoint, across the enterprise, and to everywhere the battle is taking place. Learn more about Cybereason Zero Trust here or schedule a demo today.

Karishma is a Product Marketing Manager at Cybereason. She was previously with Accenture Security where she worked as a penetration tester and was responsible for helping clients understand and manage their security vulnerabilities. Karishma is passionate about exploring large shifts in the cybersecurity industry from a technical and strategic point of view.
All Posts by Karishma Asthana
The second installment of our five-part series outlining how Cybereason XDR maps to each of the objectives in the U.K. Government Cybersecurity Strategy...

Robust protection mechanisms are not as binary as saying “good file” and “bad file” or “good user” and “bad user.” You must understand the interactions between malicious actors (or even suspicious actors) and your environment...

The second installment of our five-part series outlining how Cybereason XDR maps to each of the objectives in the U.K. Government Cybersecurity Strategy...

Robust protection mechanisms are not as binary as saying “good file” and “bad file” or “good user” and “bad user.” You must understand the interactions between malicious actors (or even suspicious actors) and your environment...
Get the latest research, expert insights, and security industry news.
Subscribe