The Cybereason Global Security Operations Center (SOC) issues Cybereason Threat Alerts to inform customers of emerging impacting threats. The Alerts summarize these threats and provide practical recommendations for protecting against them.
What’s Happening?
The Cybereason GSOC Managed Detection and Response (MDR) team is investigating CVE-2021-40444, a critical vulnerability in the Microsoft Hypertext Markup Language (MSHTML) web content rendering engine that Microsoft Office applications use. This vulnerability enables attackers to use malicious ActiveX controls to execute arbitrary code on target systems.
This Threat Alert focuses on the CVE-2021-40444 vulnerability as exploited via malicious Office documents. However, other applications that also use the MSHTML engine, such as Internet Explorer, can also be vectors for exploiting the vulnerability.
Key Observations
-
- Zero-day vulnerability: Adversaries have been exploiting CVE-2021-40444 as a zero-day vulnerability to execute malicious code on target systems.
- Social engineering: To exploit the CVE-2021-40444 vulnerability, the attacker tricks a user into opening a specifically crafted Office document and clicking Enable Content to disable the Microsoft Office Protected View feature. The Protected View feature is enabled by default and blocks the execution of potentially malicious code in the context of Office documents.
- No patch available: No patch for CVE-2021-40444 is available at the time of writing of this Threat Alert. Cybereason recommends that you disable ActiveX controls if these controls are not necessary on the machine. The Cybereason team provides further recommendations in the Cybereason Recommendations section below.
Analysis
CVE-2021-40444 is a critical vulnerability in the MSHTML rendering engine. Microsoft Office applications use the MSHTML engine to process and display web content. An adversary who successfully exploits CVE-2021-40444 could achieve full control over a target system by using malicious ActiveX controls to execute arbitrary code.
Malicious actors are exploiting CVE-2021-40444 by using specifically crafted Microsoft Office documents. A typical such document uses the MSHTML engine to open a malicious website hosted on an attacker-controlled endpoint. This website exists as a MIME HTML (MHTML) Object Linking and Embedding (OLE) object in the context of the document. The website executes JavaScript code and ActiveX controls that then execute malicious code on the system where the malicious Office document was opened. This code is hosted at the attacker-controlled endpoint in the form of a dynamic-link library (DLL).
To exploit the CVE-2021-40444 vulnerability, the attacker tricks a user into opening a specifically crafted Office document and clicking Enable Content to disable the Microsoft Office Protected View feature. The Protected View feature is enabled by default and blocks the execution of potentially malicious code in the context of Office documents.
A specific exploitation of CVE-2021-40444 observed in practice involves the following activities:
-
- A malicious actor tricks a user into opening a Microsoft Office document that contains an MHTML OLE object that is a website hosted on an attacker-controlled endpoint.
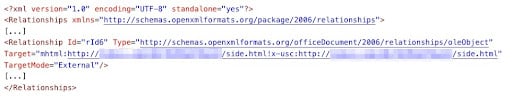 An MSHTML OLE object in a specifically crafted Microsoft Office document
An MSHTML OLE object in a specifically crafted Microsoft Office document
-
- The website executes obfuscated JavaScript code that instantiates ActiveX controls:
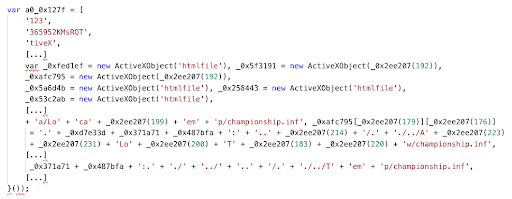 Obfuscated JavaScript code that instantiates ActiveX controls
Obfuscated JavaScript code that instantiates ActiveX controls
-
- The website code retrieves and opens a cabinet archive (.cab) file named ministry.cab from the attacker-controlled endpoint. This file contains a malicious DLL named championship.inf.
- The website code executes the championship.inf file as a Control Panel (.cpl) file using the Control Panel utility control.exe. For example, the website code might execute the following command:
control.exe .cpl:../../../AppData/Local/Temp/championship.inf.
- The control.exe utility executes as a child process of the process that hosts the Microsoft Office application that opened the Office document, such as winword.exe.
- The malicious DLL file championship.inf executes in the context of the rundll32.exe Windows utility.
Cybereason Recommendations
Cybereason recommends the following:
-
- Disable ActiveX controls if these controls are not necessary on the machine. To do this, configure the associated registry values by executing the following Windows Registry (.reg) file and rebooting the system:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\0]
"1001"=dword:00000003
"1004"=dword:00000003
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\1]
"1001"=dword:00000003
"1004"=dword:00000003
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\2]
"1001"=dword:00000003
"1004"=dword:00000003
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3]
"1001"=dword:00000003
"1004"=dword:00000003
-
- If you do not want to disable ActiveX controls, make sure that you do not click Enable Content when you view Office documents that originate from untrusted sources. Clicking Enable Content disables the Microsoft Office Protected View feature.
- Educate users so that they do not open Office documents that originate from untrusted sources, or do not click Enable Content when they open such documents.
- Threat Hunting with Cybereason: The Cybereason MDR team provides its customers with custom hunting queries for detecting specific threats - to find out more about threat hunting and Managed Detection and Response with the Cybereason Defense Platform, contact a Cybereason Defender here.
- For Cybereason customers: More details available on the NEST including custom threat hunting queries for detecting this threat and a list of indicators of compromise (IOCs) related to the threat.
About the Researcher:
Aleksandar Milenkoski, Senior Threat and Malware Analyst, Cybereason Global SOC 
Aleksandar Milenkoski is a Senior Threat and Malware Analyst with the Cybereason Global SOC (GSOC) team. He is involved primarily in reverse engineering and threat research activities. Aleksandar has a PhD degree in the area of system security. Prior to Cybereason, his work was focusing on research in the area of intrusion detection and reverse engineering security mechanisms of the Windows 10 operating system.







