The Cybereason Global Security Operations Center (SOC) issues Cybereason Threat Alerts to inform customers of emerging impacting threats. The Alerts summarize these threats and provide practical recommendations for protecting against them.
What’s Happening?
The Cybereason GSOC Managed Detection and Response (MDR) Team is investigating the PrintNightmare vulnerability (CVE-2021-34527), a critical vulnerability in the Windows Print Spooler service. This vulnerability enables attackers to execute arbitrary code on target systems with administrative privileges.
Key Observations
-
- PrintNightmare is a critical vulnerability in the Windows Print Spooler service that allows attackers to execute arbitrary code on target systems with administrative privileges.
- There is no patch for PrintNightmare at the time of writing of this Threat Alert. Cybereason recommends that you disable the Windows Print Spooler service if this service is not necessary on the machine. The Cybereason team provides further recommendations in the Cybereason Recommendations section. Update (July 6, 2021): Microsoft released an Out-of-Band Security Update for PrintNightmare. We recommend that you install this update immediately.
Analysis
PrintNightmare is a critical vulnerability in the Windows Print Spooler service, which executes as the spoolsv.exe process in Windows systems. An adversary who successfully exploits the PrintNightmare vulnerability could achieve full control over a target system by executing arbitrary code, such as a dynamic link library (DLL) or a Windows executable, with administrative privileges. The adversary must be authenticated to the Windows Print Spooler service to take advantage of PrintNightmare.
The RpcAddPrinterDriverEx Function
The RpcAddPrinterDriverEx function, implemented in the Windows Print Spooler service, allows authenticated users to deploy arbitrary DLLs or Windows executables on systems where the Windows Print Spooler service runs and execute them with administrative (SYSTEM) privileges. Adversaries can exploit this vulnerability.
According to the CERT Coordination Center at Carnegie Mellon University:
The RpcAddPrinterDriverEx() function is used to install a printer driver on a system. One of the parameters to this function is the DRIVER_CONTAINER object, which contains information about which driver is to be used by the added printer. The other argument, dwFileCopyFlags, specifies how replacement printer driver files are to be copied. An attacker can take advantage of the fact that any authenticated user can call RpcAddPrinterDriverEx() and specify a driver file that lives on a remote server. This results in the Print Spooler service spoolsv.exe executing code in an arbitrary DLL file with SYSTEM privileges.
Exploiting the Vulnerability
When an adversary exploits the PrintNightmare vulnerability, the Windows Print Spooler service writes two files, kernelbase.dll and UNIDRV.dll, as well as any attacker-provided DLL or Windows executable in the %SYSTEM%\System32\spool\drivers\ directory (for example, in C:\Windows\System32\spool\drivers\x64\3). The vulnerable Windows Print Spooler service (spoolsv.exe) then executes the attacker-provided DLL or Windows executable with administrative privileges. The spoolsv.exe process executes the executable as a child process.
For lateral movement, an attacker may deploy a command line interpreter utility, such as cmd.exe or powershell.exe, to execute arbitrary commands on the target system. An attacker may also load other executables that facilitate lateral movement, such as rundll32.exe, regsvr32.exe, msbuild.exe, or installutil.exe:
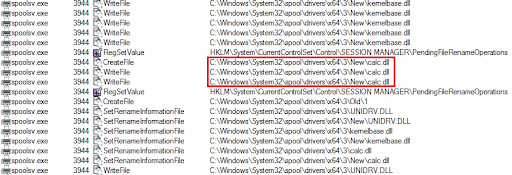 The Windows Print Spooler service writes and then executes the attacker-provided calc.dll
The Windows Print Spooler service writes and then executes the attacker-provided calc.dll
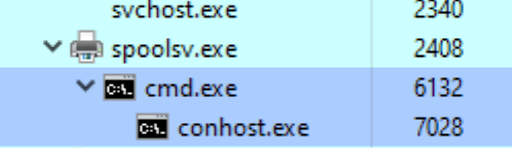 The Windows Print Spooler service executes the attacker-provided command line interpreter cmd.exe as a child process
The Windows Print Spooler service executes the attacker-provided command line interpreter cmd.exe as a child process
Cybereason Recommendations
Cybereason recommends the following:
-
- Disable the Windows Print Spooler service if this service is not necessary on the machine. To do this, use one of the following methods.
- Execute the following system command:
net stop spooler
- Execute the following PowerShell command:
Stop-Service -Name Spooler -Force & Set-Service -Name Spooler -StartupType Disabled
- If you do not want to disable the Windows Print Spooler service, modify the SYSTEM user privileges so that this user cannot write in the %SYSTEM%\System32\spool\drivers\ directory. This action effectively blocks the deployment of attacker-provided DLLs or Windows executables. To do this, execute the following PowerShell script:
$Path = "C:\Windows\System32\spool\drivers"
$Acl = Get-Acl $Path
$Ar = New-Object System.Security.AccessControl.FileSystemAccessRule("System", "Modify", "ContainerInherit, ObjectInherit", "None", "Deny")
$Acl.AddAccessRule($Ar)
Set-Acl $Path $Acl
-
- Check for potential PrintNightmare exploitation attempts by executing the following PowerShell command:
Get-WinEvent -LogName 'Microsoft-Windows-PrintService/Admin' | Select-String -InputObject {$_.message} -Pattern 'The print spooler failed to load a plug-in module'. The presence of the following log message indicates that the Windows Print Spooler service has attempted to execute a DLL or a Windows executable, which an attacker may have provided when exploiting PrintNightmare:
The print spooler failed to load a plug-in module
- Threat Hunting with Cybereason: The Cybereason MDR team provides its customers with custom hunting queries for detecting specific threats - to find out more about threat hunting and Managed Detection and Response with the Cybereason Defense Platform, contact a Cybereason Defender here.
- For Cybereason customers: More details available on the NEST including custom threat hunting queries for detecting this threat.
About the Researchers:
Aleksandar Milenkoski, Senior Threat and Malware Analyst, Cybereason Global SOC
 Aleksandar Milenkoski is a Senior Threat and Malware Analyst with the Cybereason Global SOC (GSOC) team. He is involved primarily in reverse engineering and threat research activities. Aleksandar has a PhD degree in the area of system security. Prior to Cybereason, his work was focusing on research in the area of intrusion detection and reverse engineering security mechanisms of the Windows 10 operating system.
Aleksandar Milenkoski is a Senior Threat and Malware Analyst with the Cybereason Global SOC (GSOC) team. He is involved primarily in reverse engineering and threat research activities. Aleksandar has a PhD degree in the area of system security. Prior to Cybereason, his work was focusing on research in the area of intrusion detection and reverse engineering security mechanisms of the Windows 10 operating system.
Eli Salem, Senior Security Analyst, Cybereason Global SOC
 Eli Salem is a lead threat hunter and malware reverse engineer at Cybereason. Eli has worked in the private sector of the cyber security industry for a couple of years now. In his free time he publishes articles about malware research and threat hunting.
Eli Salem is a lead threat hunter and malware reverse engineer at Cybereason. Eli has worked in the private sector of the cyber security industry for a couple of years now. In his free time he publishes articles about malware research and threat hunting.






 Aleksandar Milenkoski is a Senior Threat and Malware Analyst with the Cybereason Global SOC (GSOC) team. He is involved primarily in reverse engineering and threat research activities. Aleksandar has a PhD degree in the area of system security. Prior to Cybereason, his work was focusing on research in the area of intrusion detection and reverse engineering security mechanisms of the Windows 10 operating system.
Aleksandar Milenkoski is a Senior Threat and Malware Analyst with the Cybereason Global SOC (GSOC) team. He is involved primarily in reverse engineering and threat research activities. Aleksandar has a PhD degree in the area of system security. Prior to Cybereason, his work was focusing on research in the area of intrusion detection and reverse engineering security mechanisms of the Windows 10 operating system. Eli Salem is a lead threat hunter and malware reverse engineer at Cybereason. Eli has worked in the private sector of the cyber security industry for a couple of years now. In his free time he publishes articles about malware research and threat hunting.
Eli Salem is a lead threat hunter and malware reverse engineer at Cybereason. Eli has worked in the private sector of the cyber security industry for a couple of years now. In his free time he publishes articles about malware research and threat hunting.
