The Cybereason Global Security Operations Center (SOC) issues Cybereason Threat Alerts to inform customers of emerging impacting threats. The Alerts summarize these threats and provide practical recommendations for protecting against them.
What’s Happening?
The Cybereason GSOC Managed Detection and Response (MDR) Team is investigating a recent campaign, which is specifically targeting victims based in the EMEA region. The campaign is associated with the N3tw0rm threat actor, suspected to be based in Iran. The campaign involves ransomware and a disk space filler utility. This utility fills hard disk volumes with junk data until no free disk space is available.
Key Observations
-
- The Cybereason Defense Platform detects the ransomware associated with N3tw0rm.
- The ransomware campaign involves the use of a disk space filler utility, a scenario that is not typical for ransomware campaigns. The disk space filler utility continuously writes files on a victim’s computer hard disk volumes until no free disk space is left available. The utility then deletes the files it wrote, after which the utility shuts down the operating system.
- The activities of the disk space filler utility are a strong indicator that the ransomware campaign is associated with N3tw0rm.
- The ransomware leaves a ransom note, threatening to double the ransom price and to publish the victim’s data if the price is not paid before a given deadline.
Analysis
The disk space filler utility, observed as part of the recent ransomware campaign orchestrated by N3tw0rm, fills hard disk volumes with data, leaving no free disk space available. The utility then deletes the files it wrote, after which the utility shuts down the operating system. The overall activity of the disk space filler utility can be summarized as follows:
-
- When the disk space filler utility executes, the utility deletes all files in its current directory and creates a file named log.txt in this directory. The utility continuously records the progress of its operation in this file:
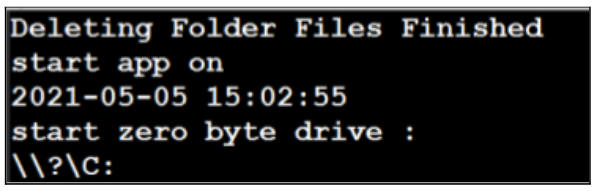 Contents of log.txt
Contents of log.txt
-
- The disk space filler utility then writes files on hard disk volumes until no free disk space is available. These files:
-
- are located in a directory created by the utility on each hard disk volume
- are filled with zeroes (0)
- have names that contain the temp.temp string:
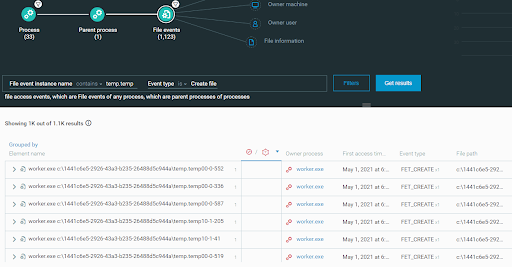 Files written by the disk filler utility
Files written by the disk filler utility
-
- When writing files, the disk space filler utility periodically displays the progress of its operation on the console screen. The utility refreshes the console screen by executing the cls command via spawned command-line interpreters - cmd.exe processes:
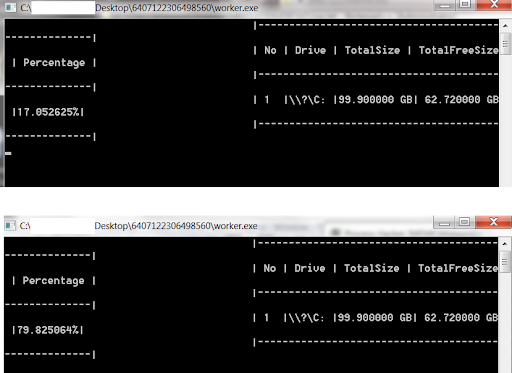 The disk space filler utility displaying operation progress on the console screen
The disk space filler utility displaying operation progress on the console screen
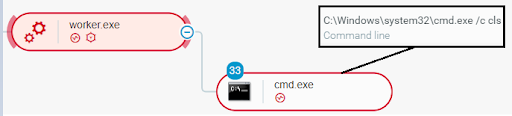 The disk space filler utility refreshing the console screen
The disk space filler utility refreshing the console screen
-
- When the capacities of the hard disk volumes are reached, the disk space filler utility deletes the files it has previously written. The utility then shuts down the operating system.
Cybereason Recommendations
By using the Cybereason Cross Machine Correlation (CMC) engine and collection abilities, you can detect the indicators of compromise (IOCs) that pertain to this attack. Cybereason recommends the following:
-
- Make sure that the Anti-ransomware feature of the Cybereason platform is set to Suspend and Prevent. The Cybereason platform detects the ransomware associated with N3tw0rm.
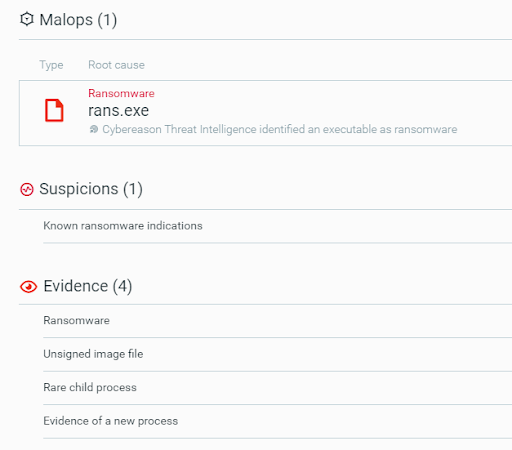 MalOp generated by the Cybereason Defense Platform for the ransomware associated with N3tw0rm
MalOp generated by the Cybereason Defense Platform for the ransomware associated with N3tw0rm
About the Researchers:
Aleksandar Milenkoski, Senior Threat and Malware Analyst, Cybereason Global SOC
 Aleksandar Milenkoski is a Senior Threat and Malware Analyst with the Cybereason Global SOC (GSOC) team. He is involved primarily in reverse engineering and threat research activities. Aleksandar has a PhD degree in the area of system security. Prior to Cybereason, his work was focusing on research in the area of intrusion detection and reverse engineering security mechanisms of the Windows 10 operating system.
Aleksandar Milenkoski is a Senior Threat and Malware Analyst with the Cybereason Global SOC (GSOC) team. He is involved primarily in reverse engineering and threat research activities. Aleksandar has a PhD degree in the area of system security. Prior to Cybereason, his work was focusing on research in the area of intrusion detection and reverse engineering security mechanisms of the Windows 10 operating system.
Eli Salem, Senior Security Analyst, Cybereason Global SOC
 Eli Salem is a lead threat hunter and malware reverse engineer at Cybereason. He has worked in the private sector of the cyber security industry for a couple of years now. In his free time he publishes articles about malware research and threat hunting.
Eli Salem is a lead threat hunter and malware reverse engineer at Cybereason. He has worked in the private sector of the cyber security industry for a couple of years now. In his free time he publishes articles about malware research and threat hunting.



 Contents of log.txt
Contents of log.txt


 The disk space filler utility refreshing the console screen
The disk space filler utility refreshing the console screen
 Aleksandar Milenkoski is a Senior Threat and Malware Analyst with the Cybereason Global SOC (GSOC) team. He is involved primarily in reverse engineering and threat research activities. Aleksandar has a PhD degree in the area of system security. Prior to Cybereason, his work was focusing on research in the area of intrusion detection and reverse engineering security mechanisms of the Windows 10 operating system.
Aleksandar Milenkoski is a Senior Threat and Malware Analyst with the Cybereason Global SOC (GSOC) team. He is involved primarily in reverse engineering and threat research activities. Aleksandar has a PhD degree in the area of system security. Prior to Cybereason, his work was focusing on research in the area of intrusion detection and reverse engineering security mechanisms of the Windows 10 operating system. Eli Salem is a lead threat hunter and malware reverse engineer at Cybereason. He has worked in the private sector of the cyber security industry for a couple of years now. In his free time he publishes articles about malware research and threat hunting.
Eli Salem is a lead threat hunter and malware reverse engineer at Cybereason. He has worked in the private sector of the cyber security industry for a couple of years now. In his free time he publishes articles about malware research and threat hunting.
