Molerats APT | Indicator's of Compromise
Hashes (SHA-256 + SHA-1)
553127cb586591cbfbae54dd4e28d4cd40fdddebaf4e0e7e1f3f23c446a621bb
0a2b7ac50f1467588b0e0b1b73fdfd270eaf86a0
URLs
https://www.dropbox[.]com/s/r81t6y7yr8w2ymc/MOM.zip?dl=1
https://drive.google[.]com/uc?export=download&id=1NnMlUPwkxK4_wAJwrqxqBAf
dKCPDxyeh
Archive Files:
Hashes (SHA-256 + SHA-1)
D7675b5c1a47b876b505bf6fd8dc9ea3b35520c13408450df8807a1a5c24da68
89e8c607f6fa6cebd0672a6147e23b8cbe26c972
58f926d9bd70c144f8697905bf81dfff046a12929639dfba3a6bd30a26367823
7f0e609cd49a51b1e0fcc08499a618136451f689
SharpStage Backdoor:
Hashes (SHA-256 + SHA-1)
782681add2e26a17f4ad415b5b30f280c93f954a40ec4f00e0e60f9ef3884ac9
0eb6fd1bbc58fff0d85fe01e6528939650f8965c
688f79ba03554bbaf2be513416360ce44757b2f69103e6043ab66508611fe01a
d59fccb2cfb79cf26b332e40b102aa35d67b44ff
69af17199ede144d1c743146d4a7b7709b765e57375d4a4200ea742dabef75ef
7f3d04f54ffff9751d037398752107856f563e73
Caab3635c747d037eff7d8597698636c9a597ff631840e551011011bd4608245
8ec4d30a3040e260174cabb4b0c3959233b53929
7da27c2020176fd2b6132d65bd4cbabf9c23a4cb96427f5f7c59c103e031c138
625c550256b9c042a2cb5ce77ce3134d3cad1a0e
8daab6b0c8a9d22085f66f7498f87467eefadbcd0118df007f1600c87b7a3839
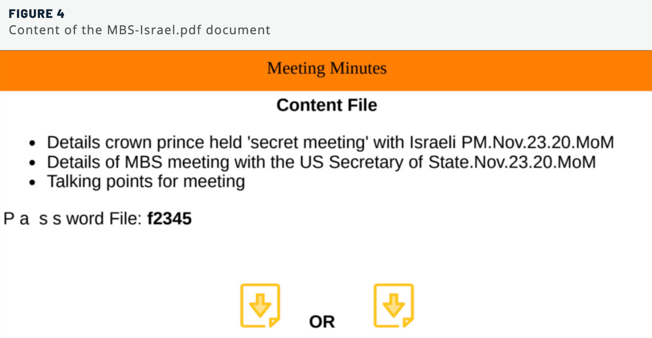
Decoy Document
20c74ccb8e56170fa3cdbf5f2e4dfe372bd88b9f1e78872691e37d868ccc3195
c7d2241c6a6ed2a079793fd2df17dd8582b24809
Domains
www.artlifelondon[.]com
www.forextradingtipsblog[.]com
Directoryswiss[.]com
URLs
https://www.artlifelondon[.]com/beta/medias[.]php
https://www.artlifelondon[.]com/Hamas.php - shortened URL https://bit[.]ly/3kE3QNb
http://artlifelondon[.]com/hamas_internal_elections.rar
https://www.artlifelondon[.]com/momnws.php
https://www.forextradingtipsblog[.]com/beta/mediasG.php?NamePC=<Machine_Name>&NameUser=<Username>&Mask=0
https://forextradingtipsblog[.]com/SaudiRecognitionofIsrael.php
https://forextradingtipsblog[.]com/AhmedMajdalani.php
https://forextradingtipsblog[.]com/momnws.php
hxxps://directoryswiss[.]com/gama/void.php
DropBook Backdoor:
Hashes (SHA-256 + SHA-1)
2578cbf4980569b372e06cf414c3da9e29226df4612e2fc6c56793f77f8429d8
2da78a9a8b3005fcf64028b035ab6f1a26ac290c
URLs
http://simp[.]ly/p/04T5bp
https://app.simplenote[.]com/p/04T5bp
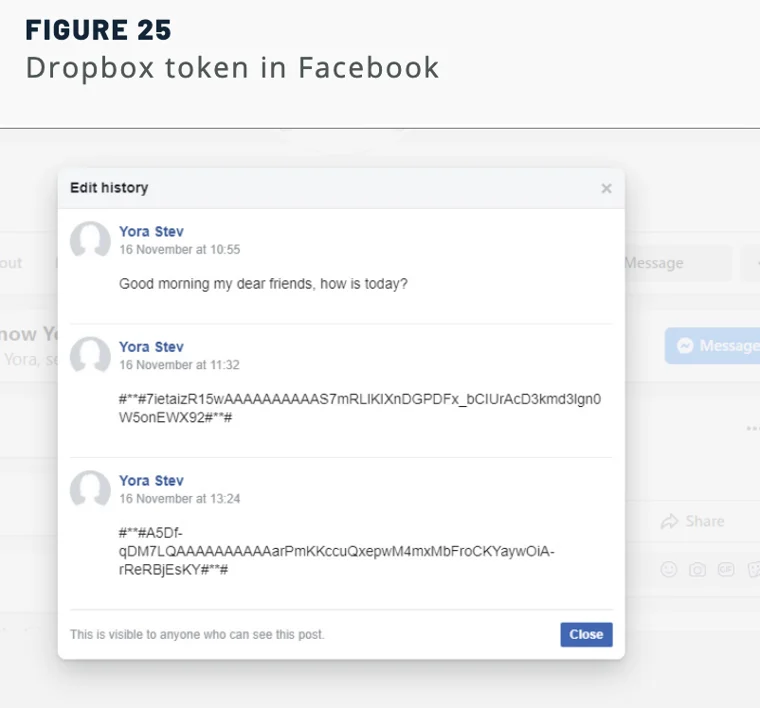
https://www.facebook.com/yora.stev.5
Spark Backdoor:
Hashes (SHA-256 + SHA-1)
54eadcd0b93f0708c8621d2d8d1fb4016f617680b3b0496343a9b3fed429aaf9
c3be6ad66b8de00741901ea9556621ef3515ee85
6afa011e2da6b009ab8e10a59c55c0f0c2161ca19f6305002f95dd532cf594bf
810ad432a3cec7b6ffca3268685d21f11b1b1688
5b0693731f100b960720d67bda6f3e6df1c25b7d5024d11cf61c13e7492f18cf
11c38b5c1bef14939410ebddcfec9c8a5e0e6aae
Domains
Brooksprofessional[.]com
IPs
168.119.82.89
93.115.10.142
Quasar RAT:
Hashes (SHA-256 + SHA-1)
e6f6615ccbfc1790fccaba78d11c79ecc47785245ad39fefd27bd74f9101c82e
bb7d1f60cbd7bf0508f2c8cc06e7ed907b0fa0aa
5b186548de81bc1d1ce92c042a6c488a647d80e570dd58c8d3f34910c12aba87
549d6a3123ea553d2bec5ef01029cd48fc50e0db
F5894e8c68aa2d3e34f7c967e6c4ad3cf35b399d452826148c2dd99958fa2af4
dde1e4ed199cca865a43f400646157cf3f42dd05
4e2bede5a455218844d18ff7086d9d35714499afb4d8d2c609274e1a05c67339
52693b5624d8ec23a5884653eecdf44502292109
49eb73f776e4e6d87d9701a135769c843847e7af6f5372fa99aba97b8c6af639
8b74574582a0adceb8b218399877c3f57daae57f
Domains
Lynsub[.]com
IPs
193.160.32.118
MoleNet Downloader:
Hashes (SHA-256 + SHA-1)
1ff12e9a7bc1047ad868d81bacd87ecffd18a0290d83c5e4e90783fe4249bc47
f7d2befa1db6214a45db819b14cc8d8afad3fb8b
F323a150d7597f46d29eb3a3c56f74e11d18caf164f9176c8c1b2fa0031cc729
d30810bdd1fe0e771c810659cabdb024985c4e7f
Domains
exchangeupdates[.]com
URLs
https://exchangeupdates[.]com/enterprise/Senterprise.php
https://exchangeupdates[.]com/enterprise/Wenterprise.php
New Pierogi Variant:
Hashes (SHA-256 + SHA-1)
B2ec6aeb55eb0acf12be51185e4d6b3e67e9f3931a0ce0ebbc5849f52c0d8fd3
487b56d0d7d2167fbd95804175ddffbca745be68
32eb4f92c8e82d3f401078725115d0604f9283ff8d9a088e7afbc150e08df295
4d1d67472886136ea280e262562c6033e3deeeea
0d65b9671e51baf64e1389649c94f2a9c33547bfe1f5411e12c16ae2f2f463dd
6ba65a22f189006f2d8007296688d407430682cb
82ad34384fd3b37f85e735a849b033326d8ce907155f5ff2d24318b1616b2950
e69c085587b985cb7b8ed868b6c455a218caa04a
3da95f33b6feb5dcc86d15e2a31e211e031efa2e96792ce9c459b6b769ffd6a4
891e252012f20a6df46e3bb031448e97ad954b70
Eda6d901c7d94cbd1c827dfa7c518685b611de85f4708a6701fcbf1a3f101768
27411054d9e0df9562e466abb0af07d951358783
078212fc6d69641e96ed04352fba4d028fd5eadc87c7a4169bfbcfc52b8ef8f2
825d67ec002469457e03817973c41d6614a569aa
D28ab0b04dc32f1924f1e50a5cf864325c901e11828200629687cca8ce6b2d5a
73bea795f6bd2d14887c966bdf281a5e6d7365d1
E869c7f981256ddb7aa1c187a081c46fed541722fa5668a7d90ff8d6b81c1db6
addbe1ef3cfd003a619c34d5be76cd628e172812
2115d02ead5e497ce5a52ab9b17f0e007a671b3cd95aa55554af17d9a30de37c
062f72e9ec84b1ceeceec58e9e8fb63b4d507ee9
B61fa79c6e8bfcb96f6e2ed4057f5a835a299e9e13e4c6893c3c3309e31cad44
fd193ca4c3aefe29a95d6077b438ea3b5568b5ec
B599b0327c4593a06a2e05a3373ee84c37faa6e4fd6f7e5c24544aa9192e0b43
ad6ab9659d4d07b0f4ecff7571b9a2f1ccf69069
9c1ebd6f1800194b29720f626d51bf8f67310c4c59e67cd12e398dde234872ca
7ac73d364e36bf1c181962094b7241bc48927f30
2b70045d4878a20b8fca568c0b3414f2d255f3b2a7dfed85c84cf88d1b2f4e74
8f3999352507eb2fa46f4a30d64b4ea2b6be2cd5
C7e74330440fcf8f6b112f5493769de6cdbdea5944ab78697ab115c927cbd0a1
ae29d19aa4e3f76aa8c7f42dbc3fe31340cfea0c
2d03ff4e5d4d72afffd9bde9225fe03d6dc941982d6f3a0bbd14076a6c890247
0d44e77fd514c261ef3ca168010ca93cf16f6519
B3e991914ca782b0b6f6a96d7df6d02e2388079a12e76dfacb47155fbff1084d
7f4bbae73f7f5fffdf1328e3391ad2af55932f10
42fa99e574b8ac5eddf084a37ef891ee4d16742ace9037cda3cdf037678e7512
d6b246959385362894ab96c724ea80add019869b
3884ac554dcd58c871a4e55900f8847c9e308a79c321ae46ced58daa00d82ab4
13f4d8cd1cc6fa121d4420e4694e8c151b916bbc
Decoy documents
Ec9e05daf725673e3614cd0be0279fe9261241a2be9b53885a5ab4a50f445763
c8eb145b24bd90595b2735399aa99a5855eb7023
b1ac14df66e1b10b3c744431add3d99a7eb39714b61253fb22dd3a00cba61e05
Domains
judystevenson[.]info
angeladeloney[.]info
ruthgreenrtg[.]live
escanor[.]live