
Cybereason Named Overall Leader in 2022 KuppingerCole Leadership Compass
Cybereason named an Overall Leader in the 2022 KuppingerCole Leadership Compass for vendors in the Endpoint Protection, Detection & Response (EPDR) market...

Dan Verton
New rules went into effect May 1 that require U.S. financial institutions to report cyber security incidents to regulators within 36 hours.
The rule, issued by the Federal Deposit Insurance Corp., the Board of Governors of the Federal Reserve System, and the Office of the Comptroller of the Currency, cuts the previous reporting deadline in half and has some industry analysts concerned that 36 hours is not enough time for large, complex financial institutions to detect and understand the scope of a cyber attack.
Joseph Carson, the chief security scientist at cybersecurity firm Delinea, told GovInfoSecurity that most organizations are still trying to determine the scale and impact of security incidents, even after 36 hours. "It will likely increase the burden on incident responders to try and find patient zero and the root cause along with the true scale and impact of security incidents as quickly as possible, indirectly increasing the resources they require for incident response," Carson said.
Security Operations Center (SOC) teams, regardless of size or sophistication, are at their breaking point. Alert overload and a “Fear of Missing Incidents” have led to unmanageable stress levels for SOC analysts. Making matters worse, more than half of those alerts are false positives — robbing analysts of time they could use on planning, training, and proactively improving their security program.
In most cases, an organization’s response time to a cybersecurity incident is a function of the quality of the alerts produced by the security tools deployed. The higher the quality and context of the initial alert, the faster the team can investigate and respond. To date, monitoring technologies have produced low-quality alert signals that lack supporting context, giving the adversary the advantage.
Cybereason has reversed the adversary’s advantage through the introduction of the MalOp, short for malicious operation. Rather than alert multiple times on different components for the same intrusion, the MalOp™ Detection Engine leverages industry-leading data analysis capabilities to tie together all of the components of an operation into a single attack story.
Through behavioral detection, the Cybereason Platform recognizes when multiple suspicious activities are likely part of a single security incident, and provides the security analyst with a single MalOp to investigate.
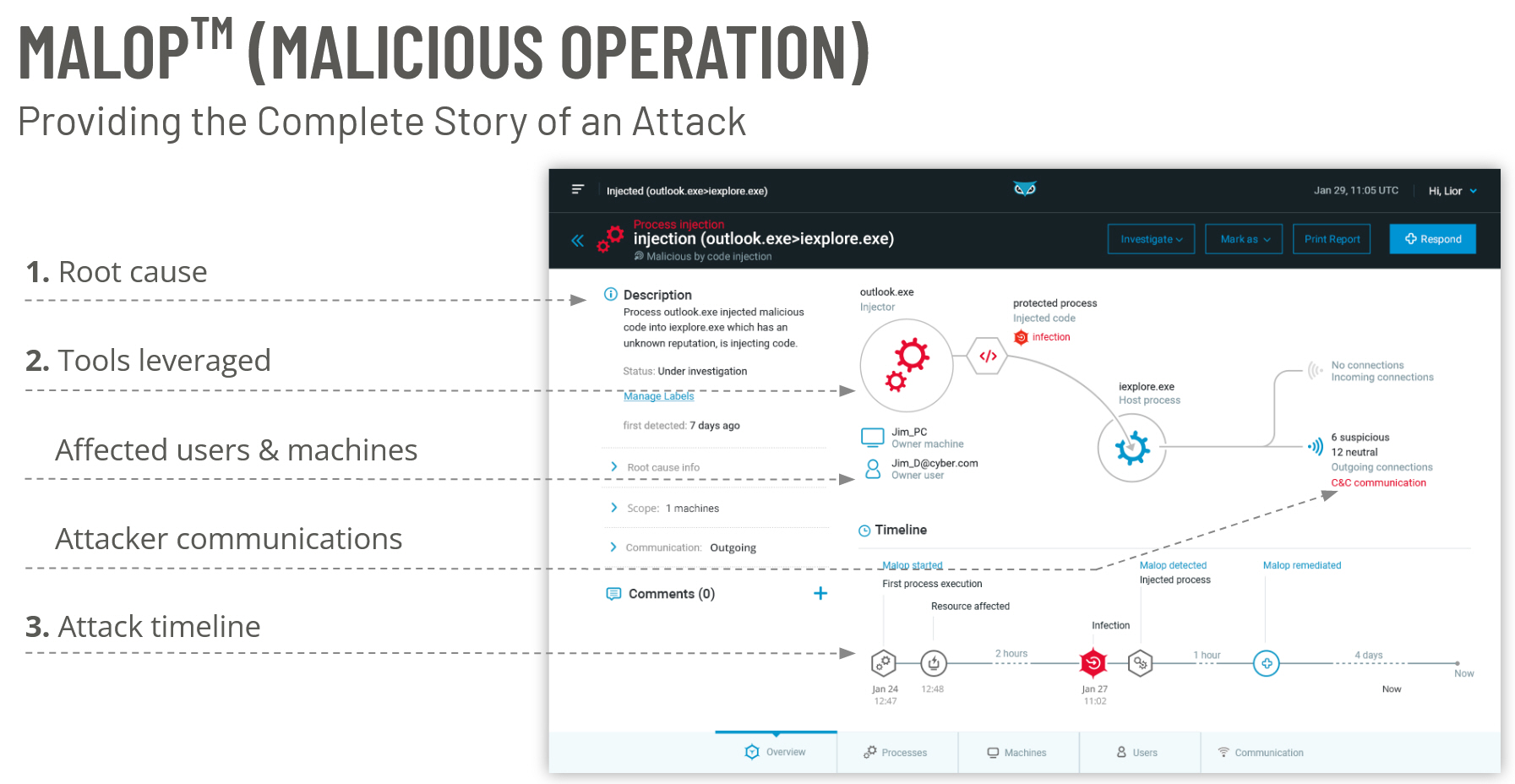
As seen in the image above, a MalOp contains the full narrative of a cyber attack, including:
The financial services sector deploys more tools, supports larger budgets, and is more likely to run an advanced cyber defense program than most other sectors of the economy. At the same time, financial services organizations are the most attacked vertical, and the attacks that they are facing are more sophisticated and damaging. Banking institutions, for example, saw a 1,318% increase in ransomware attacks in 2021.
Cybereason can support even the largest, most complex financial services environments, with the ability to accommodate hundreds of thousands of endpoints in nearly any configuration. For the first time, Cybereason XDR links together the many ways financial services firms work: on remote endpoints, mobile devices, cloud services, and email, and uses this data to expose a broader attack story.
AI-driven XDR from Cybereason is the only XDR platform capable of gathering telemetry across the planetary attack surface and delivering 10X performance improvements for defenders. AI-driven XDR from Cybereason breaks down the data silos that attackers rely on to remain undetected by unifying device and identity correlations for 10X faster and 10X more effective threat detection and response while unlocking new powers of prediction that enable defenders to anticipate and end future attacks before they begin.
For more information, download our free data sheet on Cybereason for Financial Services, or our Definitive Guide to XDR.
Cybereason is dedicated to teaming with Defenders to end attacks on the endpoint, across the enterprise, to everywhere the battle is taking place. Learn more about AI-driven Cybereason XDR here or schedule a demo today to learn how your organization can benefit from an operation-centric approach to security.

Dan Verton is Director of Content Marketing at Cybereason. Dan has 30 years of experience as a former intelligence officer and journalist. He is the 2003 first-place recipient of the Jesse H. Neal National Business Journalism Award for Best News Reporting – the nation’s highest award for tech trade journalism and is the author of the groundbreaking work, Black Ice: The Invisible Threat of Cyber-Terrorism (McGraw-Hill, 2003). He most recently served as an intelligence advisor and co-author of a nationwide TSA anti-terrorism awareness training program.
All Posts by Dan Verton
Cybereason named an Overall Leader in the 2022 KuppingerCole Leadership Compass for vendors in the Endpoint Protection, Detection & Response (EPDR) market...

To sustain the fight against a decentralized global enemy in cyberspace, the modern SOC must engage in a change management experiment to become more agile.

Cybereason named an Overall Leader in the 2022 KuppingerCole Leadership Compass for vendors in the Endpoint Protection, Detection & Response (EPDR) market...

To sustain the fight against a decentralized global enemy in cyberspace, the modern SOC must engage in a change management experiment to become more agile.
Get the latest research, expert insights, and security industry news.
Subscribe