Update: We've discovered a vaccination that disables the NotPetya ransomware.
Ransomware with functionality that’s similar to Petya ransomware has infected organizations across Europe, bringing business to a standstill. Ukraine businesses have so far beared the brunt of the attack. Supermarkets, gas stations and banks in the country along with its public transportation system and major telecommunications provider reported that their systems have been compromised. Like the WannaCry attack, this ransomware supposedly uses the EternalBlue exploit to spread.
Other affected organizations include British advertising agency WPP, Danish shipping company Maersk and Russian oil company Rosneft. The infection began Tuesday morning as European workers arrived at the office and turned on their computers and is believed to be spreading west as the day progresses.
After infecting systems, the ransomware demands $300 in bitcoin. As of 2:30 p.m. EST, blockchain records show that 27 transactions have been made to the target wallet, totaling $6,820.
The attack shares some of the functionality of the Petya ransomware family, but cannot be conclusively tied to that family or campaign as of yet.
Observed behaviors
- It kills itself prior to infection if the en_US keyboard layout is the only keyboard layout installed
- It overwrites the Master Boot Record of the System with a malicious payload
- It either forces a Hard Error within Windows which reboots the system, or creates a scheduled task to initiate a reboot after a set delay (eg, 2 hours)
- Upon reboot, code inserted into the Master Boot Record which executes and encrypts user files on the system
- It creates a scheduled task on the infected system prior to reboot that will re-encrypt the system if it is recovered through other means
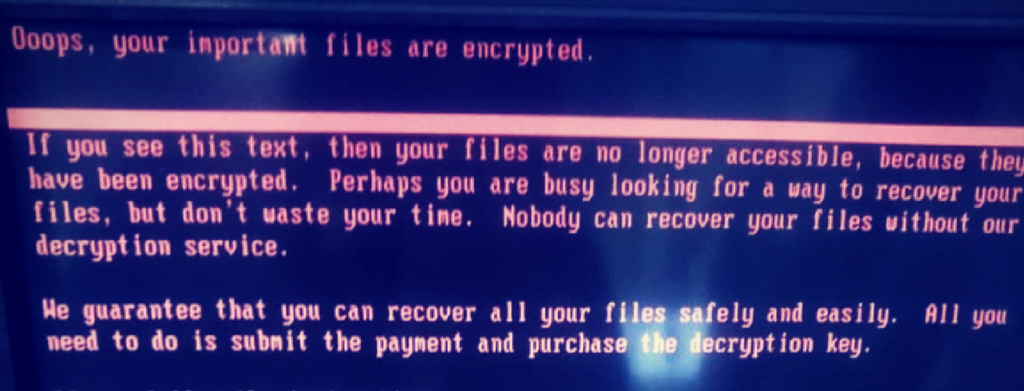
- The “ransom” message is displayed to the user telling them how to pay for a recovery key
Behavioral indicators & PREVENTION
Malware execution
- The parent process of the infection will be “wevtutil.exe” with a command line that contains the word “security”
- There will be a child process “cmd.exe” with a commandline that contains the word “deletejournal”
Below are action steps the Cybereason Intelligence Team recommends for prevention and mitigation:
Blacklist hashes
Add the following hashes to your blacklist, and if the prevention driver is installed, mark them for prevention.
06eff17186695d8f9ea466d159b3316d
82ed636b43a9739457b7460bc79bbd13
f7e6475366a65ac81740b539e1c58c1f
ccd721b4794a82167f94c9e6c54a7e09
3501a946998bbb35fca74e686591be41
5308e42d3978f5db730138ccdd0bd6dd
41787c17eb6e11018c31433a34c5e2f7
f22943e464da1294d732cdf688b0df21
c1232a57e1c929dfba38aea58b227598
bffabed92d5c9a6a5844bde6eccce651
674e86e29d34facd7a69bc5ccf626bc3
415FE69BF32634CA98FA07633F4118E1
0487382A4DAF8EB9660F1C67E30F8B25
A1D5895F85751DFE67D19CCCB51B051A
If you are not using SysInternals’ PSExec as an administrative tool in your environment, consider blacklisting the hash of the psexec version that is used in the attack:
aeee996fd3484f28e5cd85fe26b6bdcd
Block the Malware IPs at the Network Layer
Add the following IPs and domains to your firewalls and other network control measures (inbound and outbound):
95.141.115.108
84.200.16.242
111.90.139.247
185.165.29.78
Yadi[.]sk
Sundanders[.]online
Coffeinoffice[.]xyz
french-cooking[.]com
Block Lateral Movement at the Network Layer
Block SMBv1 across your organization to prevent lateral movement. Block SMB traffic from the internet to your internal network ranges.
Apply Windows Patches to Prevent Lateral Movement
Patch all Windows distributions against the EternalBlue exploit (Patch MS17-010).
Install MBR filtering
Install an MBR filter by TalosIntelligenceNote: this tool is not officially supported or endorsed by cybereason; liability remains with the user.
Warn users about unexpected restarts
Instruct users that if the machine suddenly and inexplicably restarts - shut it down immediately and don't restart it. IT Support Teams can restore the original MBR using a Windows boot disk to prevent encryption of files if the machine is powered off quickly enough.
Enable secure boot
Turn on secure boot when applicable (mostly laptops)