Global IT consultancy company Accenture announced that it has fully restored its systems after experiencing a LockBit ransomware attack. On August 11, Accenture shared details about an incident involving some of their IT assets.
“Through our security controls and protocols, we identified irregular activity in one of our environments. We immediately contained the matter and isolated the affected servers,” explained Stacey Jones, a spokesperson for the company, to CNN. “We fully restored our affected systems from backup, and there was no impact on Accenture's operations, or on our clients' systems.”
Accenture’s statement came shortly after a Twitter user shared a screenshot of an update posted by the LockBit ransomware gang to their data leaks website:
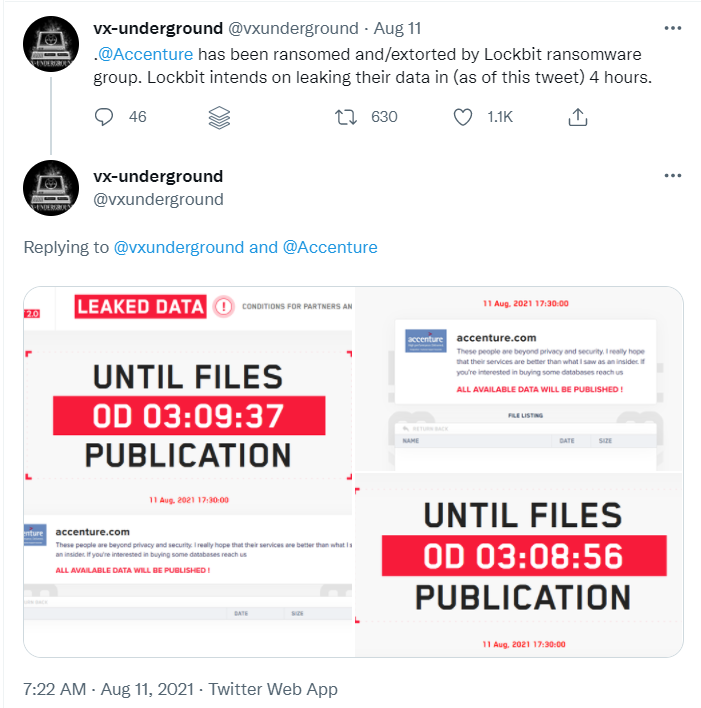
Source: https://twitter.com/vxunderground/status/1425462666408210433
The update displayed a countdown timer and a warning message that the LockBit gang would publish “all available data” from Accenture unless it paid the reported $50 million ransom, as reported by Bleeping Computer. That’s the same amount demanded by the REvil/Sodinokibi group from Acer, Apple, and later Kaseya.
Several hours after Jones released her statement, a CNBC reporter confirmed on Twitter that the LockBit ransomware gang had published approximately 2,400 files belonging to the company. The leaked information included PowerPoint presentations and case studies:
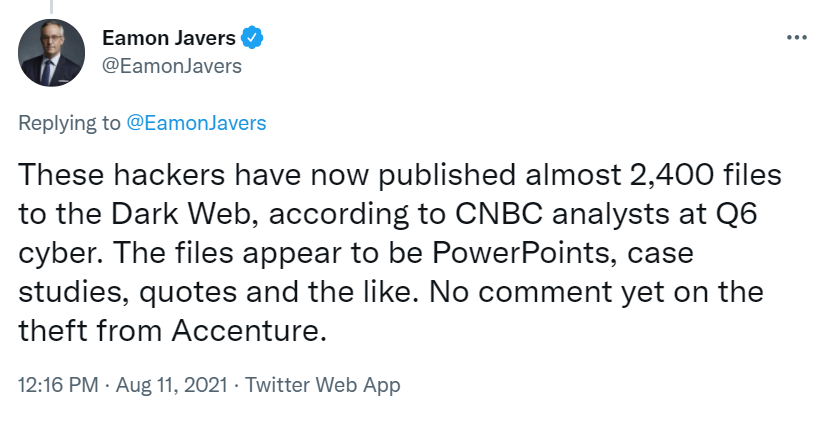 Source: https://twitter.com/EamonJavers/status/1425536526415548420
Source: https://twitter.com/EamonJavers/status/1425536526415548420
The CNBC reporter had not heard back from Accenture regarding the data theft and publication at the time of his tweet. It’s unclear when the attack occurred, how the LockBit crew entered Accenture’s network, and whether the company reached out to the attackers at some point.
Contextualizing the Accenture Ransomware Attack
To gain a better understanding of this attack, I sat down to chat with Cybereason CSO Sam Curry. Our conversation is replicated below:
David Bisson: Do you have any short-term advice for Accenture as it responds to the incident?
Sam Curry: From initial reports, kudos may be in order for Accenture, as it appears the company was prepared for ransomware. Accenture deployed backups and eliminated most, if not all, of the potential damage caused by the attack. My advice for SMEs is to safeguard their customers first and foremost.
Next, if possible, don’t pay. Not only does it fund a reprehensible group and parasites, but it also rarely gets you back to a good place operationally. And finally, focus on getting through this in an open, transparent, honest way. You can be a hero or villain in the public eye. Make sure you do the right thing because you will be judged after the fact based on how you handle this much more than you will on the fact that you were hit.
DB: Why do attackers target “big game” like Accenture, anyway?
SC: As Willie Sutton was (alleged) to have said on why he robbed banks, it’s where the money is. There is generally a correlation between brand and top-line revenue and, in turn, between top-line revenue and the ability to pay. Large companies are insured. They have massive environments that make hacking easier, and they are highly sensitive to goodwill and brand implications.
Simply put, the attackers are following the money to the biggest bank vaults and ability to pay. They have a lot of experience in knowing who pays. It’s also worth pointing out that they target a lot of people, but there’s a bias in what is visible because the media tends to report on the big brands more than the smaller ones.
DB: Is there a reason why double extortion attacks have grown in popularity in 2021?
SC: There’s an old business adage from pricing exercises: “Leave no money behind.” Put simply, there’s more money to be made from activities, and we’ve even seen other forms of monetization post-facto in these major RansomOps attacks, like selling IP to rivals even when a victim has paid or shorting stock prior to disclosure to make profits. There is no Stockholm Syndrome here. There is no scenario where these actors are on the victim’s side.
DB: Let’s talk about anti-ransomware efforts. More broadly, do you feel the government has been doing enough to help organizations combat the ransomware threat from foreign actors?
SC: We are the cavalry. Collectively. We must participate in our own rescue. The answer is not to just buy more insurance or to wait for foreign policy to catch up. Instead, all of us need to do more: the government, sure, but also the private sector, academia, practitioners, and more. The government has recently started to coordinate activities and response, as witnessed by the most recent Biden Administration cyber executive order.
And the United States, the United Kingdom, Germany, France, and other European Union countries admonishing China for carrying out the Microsoft Exchange Server attacks is important because coalition building is a critical step in turning the tables on adversaries. Overall, there is more we can do collectively in partnership to incrementally improve our common defense and make the Internet safer.
DB: Do you feel it is a good idea for ransomware victims to ever pay the ransom?
SC: It is rarely a good idea to pay ransom demands. Paying a ransomware normally just delays disclosure. Word is highly likely to get out. When the ransom arrives, you sometimes can’t pay as in the case of demonstrably terrorist-based ransoms. In other cases, it might be essential to save lives to pay, for example, as in the case of a nuclear power plant being targeted or a hospital with active surgeries happening.
However, the way to stop ransomware is ultimately financial. Make the cost too high, the revenue too small, and the initiative too risky. Those are the levers we must use, and the revenue part is a big one. Victims should deny the threat groups the funds even at a cost if they can. It’s easy to say that replacing systems for a price, say, of $1 million instead of paying a $5 million ransom makes sense, but a brave move is to not pay when those numbers are reversed.
DB: Finally, do you feel ransomware attacks are preventable? If so, how would you recommend organizations go about to prevent an infection?
SC: Nothing is 100% preventable, but RansomOps attacks can be managed and most often stopped. There are five things that companies should take into consideration to stop ransomware. These are as follows:
-
- Get ready on the business front, preparing in peace time for the unthinkable event.
- Have the right technical practices in place like closing vulnerabilities, augmenting security hygiene, creating and enforcing strong general policies, as well as maintaining backup and recovery practices. This is the “reducing the target” step.
- Deploy prevention that works like next-generation antivirus and explicit anti-ransomware technology.
- Have an EDR, MDR or XDR strategy. Ransomware is spread using the old APT toolkit. As such, the operations that penetrate networks and plant ransomware like explosives can be hamstrung and stopped as they spread.
- Finally, test a lot. Test backups. Tabletop disasters. Practice and use incident response muscle, tools, people, and processes.
Defenders United Against Ransomware
Cybereason is dedicated to teaming with defenders to end cyber attacks from endpoints to the enterprise to everywhere - including modern ransomware. Check out our recently published global research report, titled Ransomware: The True Cost to Business, learn more about ransomware defense, or schedule a demo today to learn how your organization can benefit from an operation-centric approach to security.





 Source: https://twitter.com/EamonJavers/status/1425536526415548420
Source: https://twitter.com/EamonJavers/status/1425536526415548420
