The Round 2 MITRE ATT&CK evaluation was a product assessment focused on measuring EDR capabilities related to Cozy Bear, a hacker group believed to be linked to the Russian government. Within days of posting the results, many vendors claimed success. For those who have seen the raw results from MITRE, which never explicitly score vendor products as “good or bad”, they’re probably wondering, “How do I interpret the MITRE results for myself, and what information should I look for?”
We recommend taking a holistic approach with the MITRE ATT&CK results and look at solutions that help you detect and remediate attacks quickly. Ultimately, the goal of MITRE ATT&CK and other product evaluations is to identify which products can best contain attacks and provide you with actionable threat detection to reduce overall Mean Time To Respond (MTTR). To drive down MTTR, analysts must receive real-time alerts that provide enriched context to convey the complete story of an attack.
“People should take a holistic approach while using MITRE ATT&CK evaluation. SecOps should use the ATT&CK framework internally for purple teaming and red teaming and then look at which trade-off best fits their architecture.”
- Sam Curry, Chief Security Officer, Cybereason
In order to sift through the results, look at the following two metrics as you continue to secure your organization.
MTTR Reduction
Being able to reduce MTTR is the most relevant metric for evaluating the effectiveness of an EDR solution. The lower the ability of a solution to reduce MTTR, the greater the risk that the organization will experience material damage.
Cybereason reduced mean time to respond more than any of our key competitors across both round 1 and round 2 of the MITRE ATT&CK evaluations. The evaluations showcased Cybereason’s ability to reduce MTTR consistently across all tactics and techniques, spanning evaluations based on both APT3 and APT29.
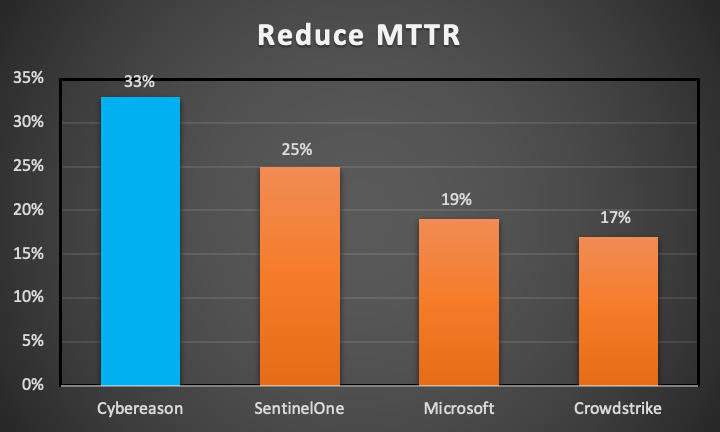
Figure 1: Ability to reduce MTTR
Correlation Efficacy
The ability to correlate data unaided and in real time provides an immense advantage to defenders. Using correlated data to create a full attack story within moments of initial detection can mean the difference between stopping an attacker and damage to an organization.
Cybereason delivered the highest efficacy rate out-of-the-box, correlating all attack activity for easy, fast investigations. Cybereason uses big data analytics to correlate the attack across all endpoints in a customer’s environment, giving a single and complete view of an attack in real time. This gives security analysts an intuitive understanding of the path an attacker takes, significantly shortening the time to respond and remediate. In addition, Cybereason’s Cross-machine Correlation Engine drives our impressive 1:150,000 endpoint to analyst ratio and low false positive rate, reducing the workload on security teams while raising their productivity.
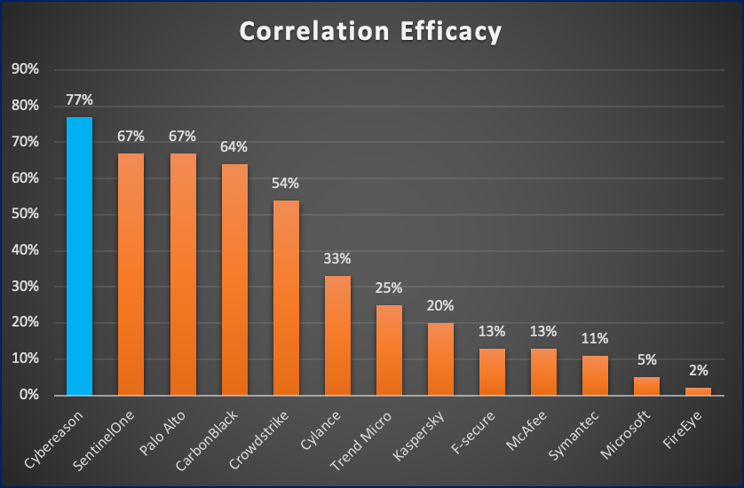
Figure 2: Correlation Efficacy
Closing thoughts
As prospects and customers explore the MITRE ATT&CK Round 2 evaluation, our recommendation is to take a holistic look at frameworks like MITRE ATT&CK. Use it to identify where your security operations has gaps in detection and then test products with real-world scenarios to find the optimal solution for your environment. To run your own evaluation of how Cybereason EDR can help your organization detect, investigate, and respond to advanced attacks, contact us.
For more information about how to use MITRE ATT&CK in your organization, sign up for the webinar:
3 Ways to Enhance Your Security Posture With The MITRE ATT&CK Framework.








